
Source: BitsLab
1. Preface
This report is jointly produced by TonBit, a subsidiary brand of blockchain security company BitsLab, and TonX.With the continuous development and widespread application of blockchain technology, the TON ecosystem continues to show strong growth momentum in 2024, attracting the attention of a large number of developers, investors and users.
In 2024, TON Ecosystem continued to make significant progress in technological innovation, application implementation and community construction, further consolidating its position in the blockchain field.However, with the rapid development of the ecosystem, security issues are becoming increasingly prominent.Faced with the ever-evolving security threats, how to effectively prevent and respond has become an important issue in the TON ecosystem.
TonBit is always committed to ensuring the stability and security of the TON ecosystem through professional audit services and security solutions.Since 2021, TonBit members have focused on the TON ecosystem and have launched projects such as TONX, TONX API, TonKey, Ton Research.This report reviews the development history of the TON ecosystem in detail, summarizes the major security incidents that have occurred in the past six months, analyzes their causes and impacts, and puts forward corresponding preventive measures and future improvement suggestions.
We hope that through this report, we can provide valuable references to participants in the TON ecosystem, promote the healthy development of the ecosystem, and enhance the importance of blockchain security by all parties.Thank you to all the partners who support and participate in the construction of the TON ecosystem, let us work together to strive to build a safer, transparent and prosperous blockchain ecosystem.
2. TON Ecology Overview
2.1 Introduction to TON Ecosystem
●Basic Introduction and Architecture
TON is the abbreviation of The Open Network, a blockchain and digital communication protocol designed by Telegram.It aims to build a fast, secure and scalable blockchain platform to provide users with decentralized applications and services.By combining blockchain technology and Telegram’s communication functions, TON achieves the characteristics of high performance, high security and high scalability.It supports developers to build various decentralized applications and provides distributed storage solutions.Compared with traditional blockchain platforms, TON has faster processing speed and throughput, and adopts the Proof-of-Stake consensus mechanism.As an innovative and potential blockchain platform, TON is driving the development of cryptocurrencies and decentralized applications.

2.2 Why choose TON
While competing with the strong liquidity and communities of Bitcoin and Ethereum, the challenges remain despite the many problems these blockchains still have in their early state.
The blockchain triad proposed by Vitalik Buterin describes the challenges faced by the Layer 1 network in balancing security, scalability, and efficiency simultaneously.Trade-offs must be made (at least in the initial stage).Taking Bitcoin as an example, we can see that Proof of Work (PoW) provides strong security and higher decentralization, but it has slower transactions and higher fees.Ethereum still faces high Gas fees during network congestion despite its recent migration to Proof of Stake (PoS) and supports more Layer 2 solutions such as Optimism and Arbitrum.
In short, there are few chains (whether Layer 1 or Layer 2) that compete with traditional banks and financial institutions under their status quo, not to mention gaining an advantage in balanced and pragmatic incentives such as privacy and security.

2.2.1 Flexible and shardable PoS architecture
Like Solana and Ethereum, TON adopts a proof-of-stake consensus mechanism.However, the key design and implementation of TON puts it ahead in performance and versatility.Its Turing-complete smart contract is an example, TON’s asynchronous blockchain introduces concepts such as Lamport time and unconventional sorting schemes.
TON’s lightning fast and low-cost transactions are powered by the flexible and shardable architecture of the chain.This architecture allows it to easily scale without losing performance.Dynamic sharding involves initially developed individual shards with their respective purposes that can run simultaneously and prevent large-scale backlogs.The block time of TON is 5 seconds, and the final determination time is less than 6 seconds.
The existing infrastructure is divided into two main parts:
Main chain (Masterchain)
Responsible for handling all important and critical data of the agreement, including parameters and current values.This includes the verifier’s address and the amount of coins verified.In addition, it also contains data for various work chains and shard chains.In multi-layer blockchain, the main chain is the most important; it is a single source of truth.
Workchain
The secondary chain connected to the main chain.It contains all transaction information and various smart contracts recorded.However, each work chain can have different rules.This means different virtual machines (VMs) with different formats of addresses, different transaction formats, and specific smart contracts.Because of this, the TON blockchain can be called a heterogeneous blockchain.
2.2.2 Extended use cases and advantages
The TON Foundation is a DAO run by the TON core community, providing various support for projects in the TON ecosystem.These support includes supporting developers through activities and hackathons, providing liquidity incentive programs for DeFi projects, and more.
According to recent developer reports, monthly active developers increased by 8%, while contributors for open source TON-related repositories on GitHub grew by 50% annually.This shows that the community is growing and fostering collaboration and innovation.
TON Connect 2.0 launch
The release of TON Connect 2.0 marks an important milestone, providing users with an intuitive way to connect their favorite wallets and applications.Powered by Tonkeeper Wallet and OpenMask, it has been adopted by more than 14 services, all of which have helped create a better user experience.
Improve trust and reliability with TON Verifier
TON Verifier, a smart contract checker created by the Orbs team, is now open to community members, allowing developers to check the integrity of their contracts before deployment.
Blueprint – Developer’s allies
TON has launched Blueprint, a simple environment designed to help developers write, test and deploy smart contracts.Blueprint simplifies the entire process and makes it easier for engineers to build on TON.
Sandbox Developer Toolkit
This latest toolkit extends the functionality of TON for a wide range of use cases from business to government.The Sandbox toolkit empowers mainstream smart contract development, paving the way for wider adoption.
Tact language beta version – embrace the future
The Tact programming language supported by Steve Korshakov and the Tact community successfully released the beta version.Concise documentation encourages community learning and feedback, promoting a stronger programming environment.
TON Society Internationalization
The TON community has also launched international centres in Lisbon, Bangkok, Hyderabad (India) and Barcelona to share ideas and accelerate project development.More centers are expected to appear around the world, inviting interested people to participate in this exciting cause.
DeFi liquidity incentive plan
This is a gradual, milestone-based approach that provides funding for projects.The program aims to achieve organic sustainability in the DeFi field within the TON ecosystem.
2.3 Overview of TON development direction and goals in 2024
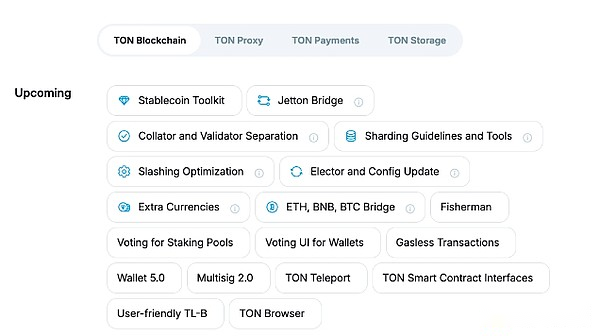
TON’s development roadmap contains many interesting plans such as stablecoin toolkits, sharding tools, and native bridging of BTC, ETH and BNB.
No Gas fee transaction
No other chains currently offer Gas-free transactions, so TON could revolutionize the blockchain space and attract more users from other ecosystems.TON may subsidize Gas fees in certain situations, such as Telegram wallets or USDT transfers, to attract more users to use TON for daily needs.
Separate verification node from packaging node
This is a major upgrade to TON’s scalability.Packaging means collecting transactions, verifying them, and putting them into a block.To this end, the node needs to store and continuously monitor the entire network status—all balances of all addresses in the TON blockchain.
TON plans to attract 500 million Telegram users by 2028 and use shards to provide sufficient transaction execution time and low transaction fees.Through sharding, the blockchain is divided into several sharding chains.2 shard chains provide 2x throughput, 4 shard chains provide 4x, and so on.
Each shard chain will have its own subset of verification nodes to package and verify blocks.These verification nodes must frequently rotate subsets to ensure security.The problem is: in case of random rotation, the verification nodes will have to store the state of each shard, not just their own shard state.Storing the status of 1 million accounts requires a powerful server, and storing the status of 500 million accounts in one place is impossible.
To solve this problem, the TON team proposed to divide verification and packaging into two roles: the packaging node only stores the status of its shard chain and packages the blocks, while the verification node assigned to the shard chain only verifies and signs within a certain period of timeBlock.This way the load and risk will be distributed evenly, and TON can be scaled to accommodate billions of users.
In the official documentation, no pledge rewards are mentioned.Although only verification nodes will create risks in block verification (verification nodes need to pledge a certain amount of cryptocurrency when participating in consensus and verifying blocks. If their behavior does not comply with the agreement, some or all of the pledged funds may be caused byPunitive cuts, called “punishment mechanisms” or “slashing”), which is called “risk”), but packaged nodes should also be rewarded for storing state and generating blocks.
Although the verification process becomes more complicated and the annual issuance rate of TON is fixed, the annual rate of return on pledge (APY) will change.As more people staking, the original APY was as high as 25% now, it is 3.4%.
Sharding Guide and Tools
TON became one of the first blockchains to efficiently utilize sharding technology, thanks to an outstanding team of developers.Centralized exchanges, payment systems, and even TON’s services and applications require dedicated tools and documents to implement sharding support because this is a technology they are not familiar with.That’s why TON developers hope to release these tools in the near future.
Optimization of punishment mechanism
The punishment mechanism is a punishment for verification nodes that fail to execute: miss blocks, frequently offline, and even attempts to push fraudulent transactions into blocks.
Currently, TON uses a complaint mechanism to punish verification nodes for misconduct.Any network participant can submit a complaint with evidence and hold the bad verification nodes accountable.
Punishment mechanism optimization will introduce better systems to detect and punish misconduct verification nodes, thereby improving the robustness of TON.This will be implemented in several steps: First, the mobile staking protocol will not be affected by the penalty of verification nodes, and the user’s reward will be guaranteed.The penalty will then be allocated to the TON provided by the liquid staking agreement, slightly reducing the average annual rate of return.
Electoral and configuration contract updates
TON staking, liquid staking and on-chain governance are all achieved through smart contracts.Tonstakers also use these contracts to pool TONs, provide TONs for verification nodes, and distribute rewards among users.
This election and configuration contract update will allow our users to vote on network proposals, making the network more open to everyone and increase the value of each user.
TON Stablecoin Toolkit
The stablecoin toolkit will allow anyone to issue algorithmic stablecoins pegged to local fiat currencies: GBP, EUR, New Zealand Dollar, etc.
Given TON’s integration with Telegram, built-in wallets, and the recent decision to share advertising profits with channel owners, we can speculate that Telegram may add local stablecoin payments to the built-in service.
Jetton Bridge
TON already has bridges for Ethereum and BNB chains to bridge $TON and popular coins such as ETH, BNB and USDC.The Jetton Bridge will allow users to send TON tokens (such as tsTON) to other chains.
ETH, BNB and BTC Bridge
Although there is a third-party bridge, it is reasonable to launch an official bridge to introduce major cryptocurrencies to TON.
Non-native tokens
In the TON blockchain ecosystem, $TON acts as a native token, and its specific uses include but are not limited to participating in the staking mechanism of the network and paying for Gas fees required for transaction execution.The interactive functions of $TON tokens, such as transactions and balance management, are implemented through smart contracts built into the TON protocol itself.In addition, the user’s $TON balance is properly recorded and stored in their on-chain accounts, ensuring the security of transactions and the consistency of data.
Jettons (such as USDT and ordinary tokens such as tsTON) are operated by third-party smart contracts and cannot pay fees and stakes instead of $TON.The user’s balance is stored in these contracts.
Extra Currencies will allow TON users to create native tokens that will also be stored in their accounts.The most obvious difference between extra currencies and Jettons is that trading of extra currencies should be 2-3 times cheaper, as they will not involve contract calls.
3. Ecological development situation
3.1 Ecological Overview

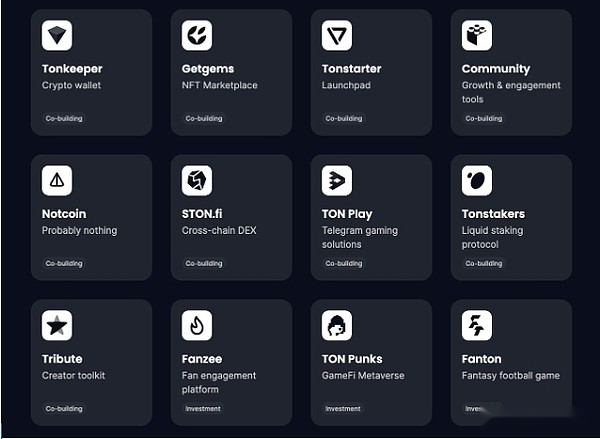
The TON Foundation official website currently displays nearly 1,000 applications, which cover a wide range of fields, from decentralized finance (DeFi) to gaming, social media and tool applications, showing the diversity and vitality of the TON ecosystem.Through these projects, the TON Foundation not only demonstrates its leadership in blockchain technology, but also demonstrates its commitment to drive innovation and promote ecosystem development.These projects have been supported by the TON Foundation’s financial support and technical guidance, providing developers with valuable resources and platforms to help them achieve their creative and business goals on the TON blockchain.This comprehensive support and investment strategy has enabled the TON ecosystem to continue to grow, attracting more and more developers and users to join, laying a solid foundation for future development.
3.2 TON Key Ecosystem Indicators
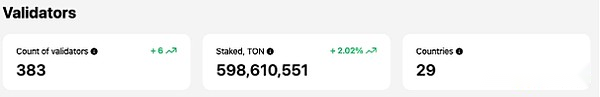
As of July 27, the number of verification nodes on the TON chain was 383, and the total number of $TON pledged under the PoS mechanism was more than 590 million, distributed in 29 countries.
As of mid-July, the number of daily active addresses on TON network has reached 373,000, an increase of 5360% year-on-year.This significant increase reflects the popularity of TON blockchain among users and the increasing adoption rate.
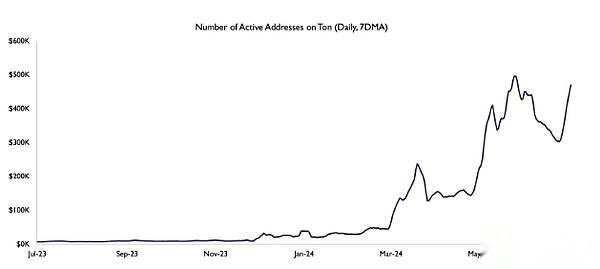
Image: TheBlock
TON Network’s DeFi ecosystem shows strong development momentum and a broad user base.Key metrics show that the number of independent users has reached 1,784,089, indicating that a large number of users are actively participating in and using DeFi services on the TON network.In addition, the total locked position (TVL) reached US$706,307,873, an amount that not only reflects users’ trust and recognition of the TON DeFi ecosystem, but also shows its significant position in the blockchain finance field.The number of liquidity providers also reached 26,297, further demonstrating the success of TON network in attracting investors and promoting liquidity.
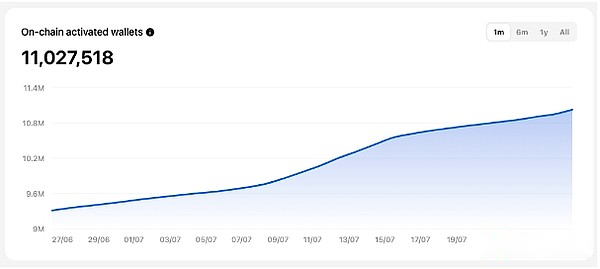
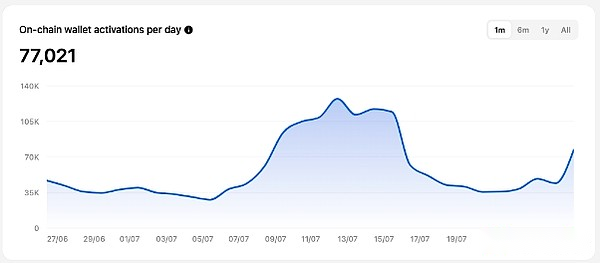
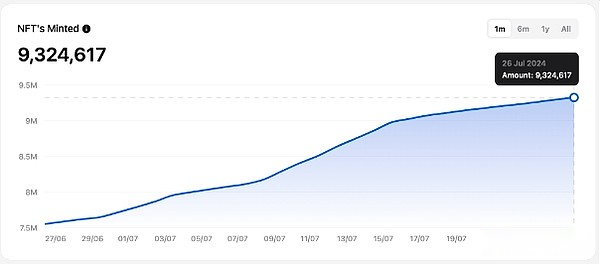
As of July 27, the number of active on-chain wallets on TON network reached 11,027,518, showing the network’s wide appeal and continued growth on a user-based basis.In addition, the daily on-chain wallet activations reached 77,021, indicating the continued activity and participation of new and existing users.Meanwhile, the number of NFT mintings reached 9,324,617, reflecting the prosperity and development of the TON ecosystem in digital asset creation and trading.Together, these data demonstrate the strong vitality of TON network in the blockchain industry and its ever-expanding ecosystem.
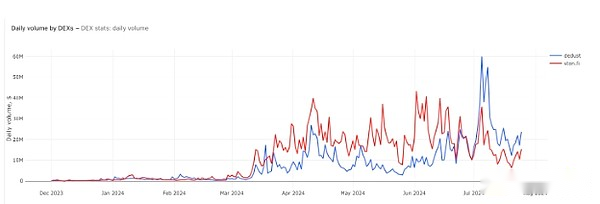
According to the Block’s mid-July statistics, more than half of the projects on TON were built as robots on Telegram, highlighting the close connection between TON and social platform Telegram.The integration of TON and Telegram provides developers with a convenient development environment and a broad user base, making it an ideal platform for project construction and promotion.
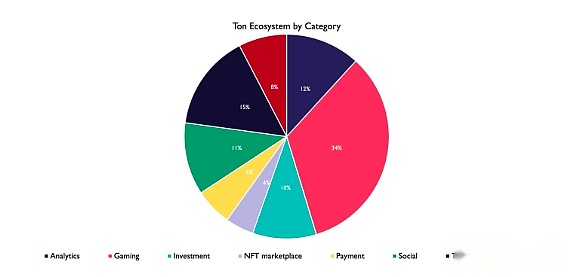
Image: TheBlock
The main project categories in the TON ecosystem include games and investments (specifically referring to some pan-financial applications), showing diversified community interests.Game projects utilize TON’s high-speed transaction processing and low fees to provide players with a smooth gaming experience and a rich in-game economy.Investment projects take advantage of TON’s decentralized features and security to attract many investors and developers of financial applications.
The continuous expansion of the TON ecosystem not only shows its technological advantages and platform potential, but also demonstrates its wide applicability in various application scenarios.With more developers and users joining, TON is expected to continue to promote the development of blockchain technology and play a more important role in the future digital economy.
3.3 How TON becomes a powerful decentralized gaming platform
3.3.1 The main reasons for building a TON-based decentralized game
Decentralized games based on TON blockchain provide a series of advantages for enterprises and developers, aiming to redefine the pattern of the game industry.
Let’s take a look at the key reasons why TON has become the preferred platform for decentralized gaming.
Integration with Telegram
The integration of TON and Telegram has provided developers with access to more than 900 million monthly active users, allowing games to be released quickly and easily directly on Telegram, which is in stark contrast to traditional app stores.
On operating systems such as iOS and Android, users often need to go through multiple steps, such as downloading and authorization.TON-based Telegram games allow users to start the game immediately by opening the robot directly or through the Telegram application center.
Powerful user acquisition and retention tools
With TON and Telegram, developers can get a comprehensive set of tools designed to improve user retention and improve user experience in the game.These tools include:
● Telegram Application Center, a one-stop destination for tools, utilities and games, all integrated into the Telegram ecosystem.
● Telegram Ads can perform advertising campaigns on almost any Telegram channel, delivering game ads to millions of users.
● You can send notifications directly within Telegram to ensure a higher opening rate than native push notifications in the game.
These tools are designed to keep players actively engaged in the gaming environment, helping developers maintain a dynamic user base.
Fast and efficient blockchain
TON blockchain is known for its high speeds.It is able to process over 100,000 transactions per second while keeping fees low.These features are critical to maintaining the performance and scalability of decentralized games, especially when dealing with high throughput player interactions.
Diversified monetization opportunities
TON provides developers with a variety of monetization strategies, from the integration of in-app advertising and tradable and sold non-fungible tokens to the creation of in-game economies that reflect real-world economic principles.This opens up a diverse revenue stream for developers and enhances the financial viability of game projects.
Simple and easy to access
TON is a user-friendly and accessible blockchain that is critical to widespread adoption in the gaming industry.
For GameFi Web3 developers and players, TON offers a complete set of tools that make it ideal for those who want to transition to the decentralized gaming world.
3.3.2 Application cases of TON in decentralized games
The TON blockchain has quickly become a vibrant decentralized gaming ecosystem, and here are some of the most popular examples that are defining the TON gaming experience.
● Notcoin: A click-to-earning game, players earn coins through clicks
●Catizen: An airdrop earning game where players earn $CATS tokens by raising cats
● Fanton Fantasy Football: A game that makes players form football teams and receive rewards
1. Notcoin
Notcoin is a simple and fun click-to-earning game that quickly became popular on Telegram due to its simple gameplay and interesting mechanics.
Players earn tokens by clicking, and their achievements are recorded in the league rankings.Players can also complete various tasks and climb the rankings by joining the Telegram channel and chatting.
2. Catizen
Catizen is an interesting airdrop earning game that combines elements of the metaverse, GameFi and AI.The gameplay involves breeding by dragging and dropping the cats together to increase their rank and earning $CATS tokens.Players can also earn fish coins through fishing, which are used for in-game promotion and upgrade.
In Catizen, players can purchase promotion props to accelerate cat breeding, acquire new cats, and enhance the overall gaming experience.The game store allows purchase of $CATS and fish tokens for TON.
As players mine more tokens, they continue to improve in the Bronze, Silver, Gold, Platinum and Diamond leagues, reflecting their achievements.
3. Fanton Fantasy Football
Fanton Fantasy Football is the first game-making game integrated with Telegram.In this game, players form a team of five football players: goalkeeper, defender, midfielder, forward and substitute.The player’s performance in actual football matches determines the points they earn in the game.
Players earn points through various on-field actions, such as goals, assists, saves and other important contributions.Users who earn the most points on the team have the chance to win valuable prizes, including cryptocurrencies and NFTs.This makes every game full of potential rewards.
Thanks to its seamless integration with Telegram, TON has greatly simplified game releases, making game releases easier than ever.Coupled with its advanced user acquisition and retention tools, it provides developers with the ability to create engaging and profitable decentralized gaming experiences.However, when developing such projects, security risks cannot be ignored.
4. Research on TON Ecological Security
4.1 How to do secure development on TON
In order to ensure the security of smart contracts, we need to take a series of security measures. Here are some key security practices in the TON ecosystem:
1. Access control
Description: When there are some important logic or sensitive operations in the contract that require specific authorized users to perform, we should do a good job of access control to avoid attackers performing sensitive operations, which will cause serious damage.
practice:
➢ Determine which operations require permission control.
➢ Restrict access to operations that require permissions by verifying the sender of the message.
➢ Regularly review and update access control policies to adapt to changes in contract requirements.
For specific proposals, please refer to:
https://github.com/ton-blockchain/TEPs/pull/180
https://github.com/ton-blockchain/TEPs/pull/181
2. Verify message input
Description: A lack of proper verification or filtering of external inputs in a smart contract can lead to malicious user or attacker input of malicious data, which may lead to unsafe behavior or vulnerabilities.
practice:
➢ Strict verification and filtering of all external inputs, including verifying data types, checking boundary conditions, and cleaning up user input
➢ Consider all possible input scenarios, including edge cases and unexpected inputs.
➢ Regular audits and test input verification logic.
3. Check the amount of Gas used
Description: When processing internal messages, the sender usually pays a Gas usage fee.When processing external messages, the contract pays for Gas usage.This means you need to be careful about the use of Gas in external messages.The Gas usage of the contract should always be tested to verify that everything works as expected and avoid loopholes that may drain the contract balance.
practice:
➢ Monitor and optimize Gas usage during development.
➢ Use Gas restrictions to prevent high consumption operations.
➢ Regularly test the gas consumption of contracts in different scenarios.
4. Timestamp dependency
Description: Some smart contracts rely on block timestamps, which may be manipulated by validators.For example, a verification node may selectively include or exclude certain transactions, or adjust the timestamp to serve certain purposes.This behavior may cause the contract logic to be manipulated and bring security risks.
practice:
➢ Avoid relying directly on block timestamps for key logical judgments.
➢ If you must use timestamps, make sure you use a more reliable and uncontrollable method.
➢ The time buffering mechanism is adopted to allow time to change within a certain range and reduce dependence on a single time point.
➢ Regularly review contract logic to ensure that it is not affected by timestamp manipulation.
5. Integer overflow
Description: Integer overflow and underflow are exponential operations that exceed the range of variable representation, resulting in incorrect calculation results.Integer overflow usually occurs in addition, subtraction, multiplication and other operations.If left uncontrolled, serious security issues can result, such as incorrect balance calculations or unexpected transfers of funds.
practice:
➢ Use a safe math library to handle integer operations.
➢ Add overflow checks before and after all mathematical operations.
➢ Regularly audit contract codes to ensure that all integer operations are protected.
6. Rounding Error
Description: Rounding error risk refers to errors in calculation results due to accuracy limitations in numerical operations or improper rounding methods.Especially when dealing with currency or high-precision values, rounding errors can lead to loss of funds or unfair allocation.
practice:
➢ Use high-precision numerical libraries or fixed-point numerical libraries to process currency operations.
➢ Regularly test and verify numerical operation logic to ensure that the accuracy meets expectations.
➢ Clearly mark the rounding method in the code to ensure consistency.
7. Denial of Service
Description: The risk of denial of service refers to consuming the computing resources of the smart contract or triggering an error condition, causing the contract to be unable to execute normally or fall into endless operations.This may prevent legitimate users from interacting with the contract and even prevent contract status from being updated.
practice:
➢ Limit the number of loops or recursion depth to avoid long-running operations.
➢ Check the remaining Gas before critical operations to avoid transaction failure due to insufficient Gas.
➢ Regularly review and optimize contract logic to ensure efficiency and reliability.
➢ Use event logs to record important operations to facilitate troubleshooting and recovery.
8. Business logic
Description: A business logic vulnerability refers to a design flaw or implementation error in a smart contract when implementing its business processes, causing the contract to perform abnormally in some cases.These vulnerabilities may be exploited by malicious users, resulting in serious consequences such as loss of funds, data tampering or contract function failure.Business logic vulnerabilities are usually not coding errors, but misunderstandings or imperfect implementations of business requirements and processes.
practice:
➢ Deeply understand and analyze business needs to ensure correct logic design.
➢ Regular code audits and logical verifications to promptly detect and fix vulnerabilities.
➢ Write comprehensive test cases to cover all possible business scenarios.
Through the above security practices, we can greatly improve the security of smart contracts, reduce risks, ensure the stable operation of contracts and the safety of users’ funds.
4.2 Review of TON Ecological Security Events
In 2024, multiple security incidents occurred in the TON ecosystem, revealing its security challenges.The following is a detailed description of some important events, analyzing the causes, impacts and solutions of events, and a inventory of some typical security vulnerabilities.
4.2.1 Common attack types
In 2024, many major security incidents occurred in the TON ecosystem, which had a certain impact on both project parties and users. These incidents revealed some of the vulnerabilities of blockchain technology in terms of security.Here are common attack types and their brief descriptions:
➢ The input verification is incorrect
Description: Input verification refers to verifying the integrity, accuracy and security of the input data.When smart contracts fail to adequately verify and clean user input, incorrect input verification occurs, leaving them vulnerable to various types of attacks.此类漏洞可被利用来操纵合约逻辑、注入恶意数据或导致意外行为。正确的输入验证可确保合约仅处理有效且预期的数据,从而降低被利用的风险。
➢ Calculation error
描述:计算错误是指系统在执行某些计算时出现错误,导致意外行为或漏洞。Such errors may stem from logical or programming errors in smart contract code that attackers can exploit to manipulate calculations or gain an advantage in the contract.
➢ Oracle/price manipulation
Description: Price manipulation refers to an attacker obtaining improper benefits by manipulating market prices.In the TON ecosystem, an attacker may make profits or trigger market panic by manipulating the volume or order book on a DEX (decentralized exchange).攻击者还可能通过干预预言机所报告的数字资产价格等外部信息,导致智能合约做出错误决策。
➢ Weak access control
描述:弱访问控制指系统未能有效限制用户对资源或操作的访问权限,导致未经授权的用户能够执行敏感操作。In the TON ecosystem, this may include unauthorized users being able to access management interfaces, change smart contract settings, or steal user assets.
➢ Denial of Service Attack
Description: Denial of Service (DoS) attack refers to consuming the computing resources of a smart contract or triggering an error condition, causing the contract to fail to execute normally or fall into endless operations.This may prevent legitimate users from interacting with the contract and even prevent contract status from being updated.In the TON ecosystem, an attacker may use DoS vulnerabilities to maliciously lock all assets, which will directly lead to the loss of funds of the project party and users.This will not only affect the normal operation of the project, but will also damage the trust of users.
➢ Phishing Attack
Description: A phishing attack is a social engineering attack where an attacker tricks users into providing sensitive information such as a username, password or private key by disguising as a trusted entity.In the TON ecosystem, phishing attackers may disguise themselves as official channels or partners, send fraudulent emails or messages, trick users into clicking malicious links or providing personal information.
These types of attacks not only reveal the security challenges of the TON ecosystem, but also emphasize the importance of strengthening security measures and increasing user vigilance.
Among them, the types of projects affected include Lanuchpad, Staking, Dex, Lending, and Gaming. These events not only expose the vulnerability of each project, but also pose serious challenges to the security of the entire ecosystem.The following is a inventory of specific security incidents and vulnerabilities.
4.2.2 Security vulnerability inventory
1. A pledge contract of a certain agreement was attacked, resulting in a large amount of token loss
Time: May 22, 2024
Loss amount: /
Root cause: Parameter configuration error
describe:
After staking activities to celebrate the prosperity of the TON ecosystem, due to the misconfiguration of protocol parameters, a certain protocol’s staking contract was hacked, resulting in a large number of tokens in the contract being stolen.After the incident, the project party immediately suspended the staking reward collection function and allocated a large amount of $USDT to repurchase the lost 307,264 tokens.
After the attack, the project party quickly contacted TonBit for audit.TonBit demonstrated its professionalism, responded quickly and mobilized a team of security experts to conduct a comprehensive and meticulous security audit of the core code of the project.TonBit’s security experts discovered six low-risk problems and immediately communicated in detail with the project team.With extensive experience and professional technical capabilities, TonBit not only provides specific solutions to the problem, but also assists the team in quickly completing the repair of all problems, ensuring the security and stability of the contract.
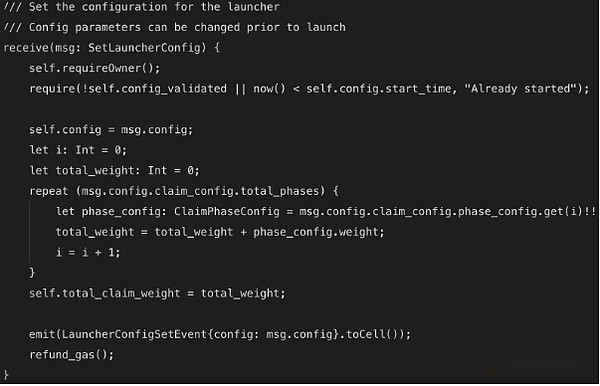
TonBit audit discovery and configuration related issues:
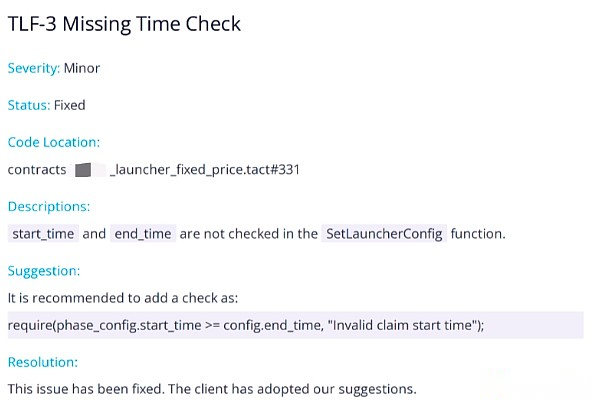
Solution: Modify the parameter configuration
2. Hackers use wallets to display controllable comment information to mislead users
Time: May 10, 2024
Loss amount: 22,000 TON
Root cause: The comment information displayed during transactions in the wallet may mislead users
describe:
While comments can be added when processing transfers messages in TON, the interface UI design of some wallets when displaying these comments poses a potential misleading risk.This design flaw is exploited by hackers. By manipulating the annotation content of transfers messages, hackers can display false information to users during the transaction process, thereby committing fraudulent behavior, resulting in user misoperation and causing capital losses.
Solution:
To solve this problem, wallet applications need to add prominent notes when displaying this information, reminding users that these contents are not trustworthy.In addition, the wallet development team should improve the UI design to ensure the transparency and reliability of transaction information display.At the same time, users also need to improve their discernment ability and be wary of suspicious transaction information.
Further measures:
TonBit recommends that the wallet development team introduce multi-layer verification mechanisms when displaying transaction annotation information, such as source verification of annotation information to ensure the reliability of the information.In addition, regular user education is conducted and security tips are issued to help users identify and prevent potential fraud.By combining technical means and user education, the occurrence of such security incidents can be effectively reduced.
3. BookPad uses a contract with a backdoor to defraud funds and run away with the money
Time: April 15, 2024
Loss amount: 74,424 TON
Root cause: BookPad uses backdoor contracts to absorb user funds and runs away
describe:
BookPad released a backdoor-free and non-open source smart contract and began pre-sale activities.After receiving enough funds, they use the backdoor in the contract to withdraw the funds and quickly run away with the money.
Solution:
To prevent similar incidents from happening again, users should collect as much information from project parties as possible before participating in investment activities of any project and select projects that are open source and have undergone strict security audits.
TonBit recommends that users pay special attention to the following points:
1.项目开源性: 确认智能合约代码是开源的,这样可以让独立的安全专家对其进行审查,确保没有隐藏的漏洞或恶意代码。
2. Security Audit: Select projects that have been reviewed by well-known security audit institutions.Security audits can detect and fix potential vulnerabilities in contracts, providing additional assurance.
3. Project background check: Investigate the background of the project party, the reputation and historical records of team members.Projects with high transparency and good reputation are more trustworthy.
4. Community feedback: Pay attention to the community’s feedback on the project, participate in discussions, and understand the reputation and potential risks of the project.
Further measures:
TonBit recommends introducing a stricter regulatory and audit mechanism into the TON ecosystem to review the qualifications of new projects to ensure that they comply with safety standards.In addition, a public contract code base can be set up, and only the approved contract can be used.This will greatly reduce the risk of user funds being stolen and improve the security and credibility of the entire TON ecosystem.
4. Hackers forged phishing links to defraud funds
Time: April 26, 2024
Loss amount: /
Root Cause: Hacker Phishing Attack
describe:
The hacker forged an NFT project and used it to forge an official website of Tether (USDT).When the user enters this forged Tether official website, he will be induced to fill in sensitive information and transfer all USDTs to the hacker’s account.In this way, hackers have successfully deceived many users and put their funds at risk.
Solution:
To avoid similar phishing attacks, users should take the following measures to verify the authenticity of the domain name when visiting unfamiliar websites:
1. Check the domain name: Confirm the accuracy of the spelling and characters of the domain name, pay attention to similar but different characters, especially those fake domain names that are maliciously used.
2. Get links from official channels: Always get the correct domain name link from official channels (such as official social media, applications, announcements, etc.) to avoid accessing the website through unreliable sources.
3. Check the security certificate: Confirm that the SSL/TLS certificate of the website is valid, and the browser address bar should display the security lock logo.Click the security lock logo to view details to ensure that the certificate is issued by a trusted certification authority and matches the domain name.
4. Tool Assistance: Use browser’s anti-phishing and security plugins to identify and block fake websites.Use online tools and services to detect the security and reputation of a website, such as verifying the legality of a website through services such as VirusTotal or PhishTank.
5. Education and awareness: Improve users’ security awareness, conduct regular network security education, and learn about the latest phishing methods and preventive measures.Especially for emerging NFT projects and cryptocurrency trading platforms, users should remain vigilant and avoid trusting unproven information.
Further measures:
TonBit recommends introducing more security education and prevention measures into the TON ecosystem, such as issuing security tips and guidelines through official channels to help users identify and avoid phishing attacks.At the same time, we will strengthen the review of new projects and websites to ensure their legality and security, and provide users with a safer usage environment.
5. Hackers pretend to be the project party to cheat on Telegram
Time: February 4, 2024
Loss amount: /
The root cause: The hacker impersonated the Ton_fish project party and posted false airdrop information on Telegram to defraud funds.
describe:
The hacker pretended to be the Ton_fish project team and posted fake airdrop information within the Telegram group to trick users into participating.They use social engineering methods and highly simulated accounts to gain the trust of users.Hackers will imitate the name, avatar and publishing style of the official account, making users mistakenly believe that the information is real.Once the victim interacts with it, he may be directed to a phishing website or requested to transfer money directly to a hacker-controlled account, which ultimately leads to a loss of funds.
Solution:
To prevent similar fraud, users should take the following measures when using social platforms such as Telegram to improve their identification capabilities and protect the security of funds:
1. Verify information through multiple channels: Before participating in any airdrop or other activities, users should verify the authenticity of the information through multiple official channels (such as official websites, official social media accounts, announcements, etc.) to avoid relying solely on a single source of information.
2. Check the authenticity of the account: Users should carefully check the authenticity of the account published information and pay attention to the time of the account creation, content of the posting and interaction.Official accounts usually have a long creation history and a large number of followers, while fake accounts may have characteristics such as short creation time and few interactions.
3. Avoid clicking on unfamiliar links: Users should be vigilant about unfamiliar or suspicious links and avoid clicking.You can use a secure browser plug-in or online tool to detect the security of the link.
4. Confirm with the official: When encountering any suspicious information, the user should confirm with the project party directly through the official contact information to avoid verification through unreliable third-party channels.
5. Improve security awareness: Users should conduct regular network security education to learn about the latest fraud methods and preventive measures.Especially when participating in cryptocurrency and blockchain-related activities, stay highly alert and avoid trusting unproven information.
6. Use two-factor authentication: To further ensure account security, users should enable the dual-factor authentication function provided by social platforms such as Telegram to increase the security protection layer of the account.
4.3 How to conduct security audits on TON ecological project parties
With the increasing number of projects in the TON ecosystem.However, there are also increasing safety issues.To ensure the security of the project, a comprehensive security audit is crucial.
General steps of security audit include:
1. Initial project evaluation
Understand project background and requirements, confirm audit scope and version, be familiar with the protocol architecture, and develop detailed audit strategies.
2. Automatic detection
Use static and dynamic analysis tools to conduct comprehensive inspection of project code and find issues that may disrupt contract functionality or security.
3. Manual audit
The security expert team will carefully check each line of code, identify potential errors and vulnerabilities, maintain close communication with the project party, and regularly feedback on issues.
4. Initial Review Report
The auditor drafts a preliminary review report, summarizing code defects and other problems, and feedbacks it to the project party.The project party confirms the audit problem, makes modifications to the effective problem, and notifies the auditor for review.
5. Final Review Report
Submit a detailed audit report containing discovered issues and repair suggestions.Communicate with the project team to ensure that all problems are effectively solved.
6. Continuous monitoring and support
Provide continuous security monitoring on the chain to promptly detect and respond to emerging security problems.Carry out regular safety reviews to maintain long-term safety of the project.
TonBit has a team of blockchain security experts and senior developers, with deep technical background and rich practical experience.Team members have many years of experience in the field of blockchain security and can accurately identify and solve potential security risks.The following is TonBit’s audit process in the TON ecosystem.
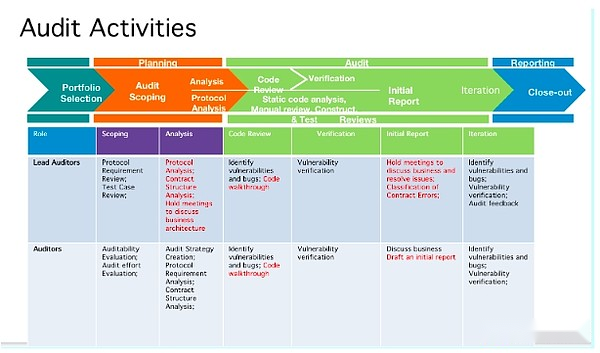
5 How users stay safe on TON and Telegram
With the rapid development of the TON and Telegram ecosystems, there are now more than 38 million active accounts, and the subsequent attention also brings greater risks.
Scammers and malicious actors are targeting the influx of novice users, and even in the safest ecosystem, it is still crucial to stay alert to the potential risks.You need to pay more attention to these most common scams.
5.1 Common fraud methods
1. Friends who need help: The scammer pretends to be friends or family members and requests funds urgently.Be sure to verify their identity.
2. 钓鱼网站:假冒网站模仿真实网站,窃取登录信息。核对网址,避免点击来历不明的链接。
3. 投资骗局:这些骗局在加密货币领域非常常见,承诺高回报但没有证明。深入研究;如果听起来好得不真实,可能就是骗局。
4. 假调查:提供参与调查的奖励以窃取个人信息。Avoid providing detailed information to unknown investigators.
5. 假工作机会:吸引人的招聘广告要求提供个人信息、下载应用或支付费用。Verification through official channels.
6. Classified Ad Scam: Fake ads lead you to fake Telegram bots to steal information.
7. Pull up shipments: Groups manipulate cryptocurrency prices to make profits, causing others to lose money.Always study and verify investment advice.
8. Romantic scam: In an online relationship, a scammer asks for money or personal information.Be alert to people you know online asking for money.
5.2 Beware of Toncoin pyramid scam
Telegram’s support for the TON blockchain unfortunately attracted some scammers who tried to exploit unsuspecting users.Here is a detailed analysis of the scam:
1. Setting up: The scammer sends a link to the “exclusive money-making plan”, which seems to be from a friend or contact person.They guided users to join an unofficial Telegram bot, lied to be used to store cryptocurrencies.
2. Investment: Users are instructed to purchase Toncoin through legal channels (such as wallets, P2P markets or cryptocurrency exchanges).This adds to false credibility.Once purchased, users must transfer their Toncoin to the scam bot.
3. Accelerator: The victim was forced to purchase the “accelerator” through a separate robot for a fee of between 5 and 500 Toncoin.At this stage, users lose their cryptocurrency.
4. Recruitment: Scammers promote recommendation plans, requiring users to create private Telegram groups and invite friends.They promise to receive a fixed payment of 25 TON per person recommended and a commission on the accelerator purchased by the referrer.
In fact, this is a typical pyramid scam.Scammers make money while others lose their investment.
5.3 How to Avoid Online Scam
To protect yourself from online scams and keep your Telegram account safe, follow these basic steps:
1. Enable Telegram’s two-step verification: Go to “Settings > Privacy & Security > Two-step Verification” to add additional security to your account.
2. Verify contact: Be vigilant about unsolicited messages, especially messages requiring personal information or funds.Confirm the sender’s identity through other means.
3. Check Telegram account activity regularly: Enter “Settings > Devices > Active Sessions” to check whether there are unknown devices or sessions in the account.
4. Report suspicious activities: If you encounter fraud, please report it to Telegram.
5. Avoid getting rich quickly: Be alert to these plans, even if recommended by friends or family members, they may be victims.
6. Don’t transfer cryptocurrency to unknown wallets: Always verify the recipient’s identity before transferring cryptocurrency to avoid being scammed.
Staying safe in TON and Telegram requires vigilance and awareness.By identifying common scams and following these security tips, you can protect your assets and personal information.Always verify the source, keep doubts about offers that are too good to be true, and trade only through official channels.Stay informed and cautious and you can enjoy the benefits of TON and Telegram without becoming a victim of fraud!
6. TON Ecological Development Summary
The reason for choosing TON is to recognize the ecosystem of Telegram itself.Deploying your Web3 project on TON can take advantage of Telegram’s huge user base with more than 700 million monthly active users.This integration provides a fertile environment for the prosperity of decentralized applications, similar to how Apple’s app store and Steam support developers.
To better understand its importance, the following analogy can be considered: Symbiosis is the basis in nature, whether it is the mutually beneficial relationship between clownfish and sea anemone, or the parasitic relationship of viruses.These relationships are crucial in shaping the planet’s biodiversity and are a key driver of evolution.Through networks and cooperation, species in symbiotic relationships can enhance their viability beyond what they can do by acting alone.The same applies to technology and Web3, especially in order to prosper, the Web3 ecosystem must achieve symbiotic relationships among different actors.
The symbiotic relationships in these technologies promote cooperation, bring synergies, ultimately benefiting all participants, and driving advancements and improvements in the Web3 field.
Overall, developers can benefit from user bases of major social networks such as Telegram without compromising incentives or value, building a strong future for their decentralized applications.This integration provides an ideal environment for the decentralized world to thrive, highlighting why TON is a strategic choice for developers to seek to deploy projects on an open network.
7. About TonBit
TonBit is a sub-brand of Web3 blockchain security auditing company BitsLab, focusing on security auditing and analysis of the TON ecosystem.As a professional and experienced team, TonBit is committed to ensuring the security and reliability of the TON ecosystem and providing high-level protection for developers and users.
1. Early participants in the TON ecosystem: Since 2021, TonBit members have focused on the TON ecosystem and have launched projects such as TONX, TONX API, Tonkey, TonResearch, etc.TonX Studio, TonFura, TonKey, Ton Research and other projects.
2. Comprehensive audit: TonBit provides a comprehensive range of security audit services, including smart contract audit, protocol security assessment and code vulnerability detection.Through comprehensive audits, ensure the security of the project at all levels and prevent possible attacks and risks.
TonBit advantages include
1. Efficient audit process: TonBit uses advanced audit tools to complete security audit tasks quickly and efficiently.While ensuring audit quality, it greatly shortens audit time and saves valuable development cycles for the project.
2. Customized solutions: TonBit provides customized security solutions according to the specific needs of each project.From initial design evaluation to security monitoring after launch, TonBit protects the entire life cycle of the project.
3. The industry’s highest security audit standard: In order to improve the security audit standards of smart contracts and ensure the security and reliability of audit project codes in all aspects, BitsLab’s three sub-brands (MoveBit, ScaleBit, TonBit) will launch specialized in smart contract security.The audit initiated activity “Secure+”.For audit projects participating in this activity, if the audit project (issuing the final audit report) is not changed, if other audit agencies or self-audit discover major problems (Major level and above) are found within one month after completing the audit (issuing the final audit report), TonBit promises30-50% audit fees will be refunded.
TonBit escorts the security of TON’s entire ecosystem through the following aspects
1. Preventive audit: Before the project is launched, TonBit will discover and fix potential security vulnerabilities in advance through a comprehensive security audit to ensure the security after the project is launched.
2. Real-time monitoring: TonBit provides 7×24-hour security monitoring services, monitors the operation status of the project in real time, promptly detects and responds to security threats, and ensures the smooth operation of the project.
3. Safety response: After discovering security problems, TonBit responds quickly, provides emergency response solutions, helping project parties solve problems quickly and reduce the impact of safety incidents.
4. Community collaboration: TonBit actively participates in the security construction of the TON community, shares security knowledge and best practices with community members, and jointly improves the security level of the entire ecosystem.
TonBit is committed to providing comprehensive security guarantees for the TON ecosystem, helping projects achieve higher security standards and user trust.As the security guardian of the TON ecosystem, TonBit will continue to work hard to contribute its own strength to the development of blockchain technology.
Disclaimer: This report is for information only and does not constitute any form of investment advice, recommendation or guarantee.Readers should conduct independent investigations and analysis before making investment decisions.
Data Accuracy: The data in this report is as accurate and up-to-date as possible, but due to rapid changes in the market, some data may change after the report is published.
Report limitations: Due to limitations on access to information, this report may not cover all security incidents and market changes.Readers should make comprehensive judgments based on other sources.
Copyright Statement: The content of this report is protected by copyright and may not be copied, reproduced or used for commercial purposes without permission.
Security Tips: Users should improve their own security awareness, regularly update security software and preventive measures to avoid becoming victims of cyber attacks and fraud.
References: In addition to the data from TON official foundation, this report also refers to multiple sources.
https://x.com/DegenonTON/status/1783738318850789494








