Author: Hannes Huitula Source: Equilibrium Labs Research Translation: Good Ouba, Bit Chain Vision Realm
What is the blockchain and how do they expand the current calculation paradigm?
Blockchain (noun): A coordination machine that enables participants from all over the world to cooperate along a set of rules that jointly agreed, without any third party assistance.
The design purpose of the computer is to do three things: store data, calculations, and communication between each other and humans.The blockchain increases the fourth dimension: the additional three things (storage, computing and communication) occur in an agreed way.These guarantees make cooperation between strangers not need to be promoted (decentralized) without trusted.
>
These additional guarantees can beEconomical(Trust game theory and incentive/suppression) orEncrypted(Trust mathematics), but most applications use the combination of the two-Encryption economyEssenceThis is in stark contrast to the current status of the main reputation -based system.
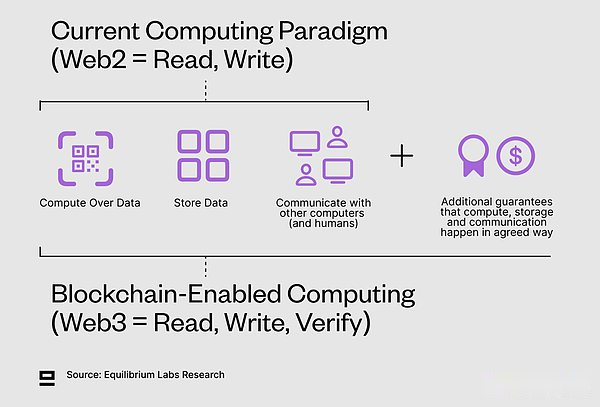
Although web3 is usually described as “reading, writing, writing, writing, writing, writing, writing, writing, writing, writing, writing, writing, writing, writing,have“But we believe that the better concept of the third iteration of the Internet is” reading, writingAs well asverify“,,Because the main benefit of public blockchain is to ensure computing and easily verifying that these guarantees are fulfilled.If we build digital workpieces that can be purchased, sold, and controlled, then ownership can become a subset with guaranteed calculations.However, many cases of blockchain benefit from guarantee calculations, but do not directly involve ownership.For example, if your health in the game is 77/100 -Do you have the health, or it is only forced to execute on the chain based on the rules that jointly agreed?We will argue the latter, but Chris Dixon may disagree.
Web3 = reading, writing, verification
ZK and modular -two trend of accelerated development
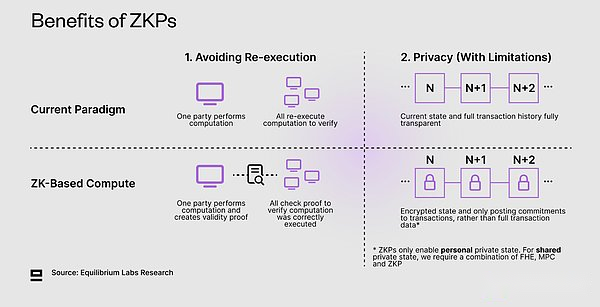
The blockchain provides a lot of exciting things, but the decentralized model also increases the overhead and low efficiency through additional functions such as P2P message transmission and consensus.In addition, most blockchains still verify the correct state conversion by re -execution, which means that each node on the network must re -execute transactions to verify the correctness of the state conversion.This is a waste, which is in sharp contrast to a centralized model that has only one entity execution.Although the decentralized system always contains some expenses and replication, the goal should be gradually approaching the centralized benchmark in terms of efficiency.
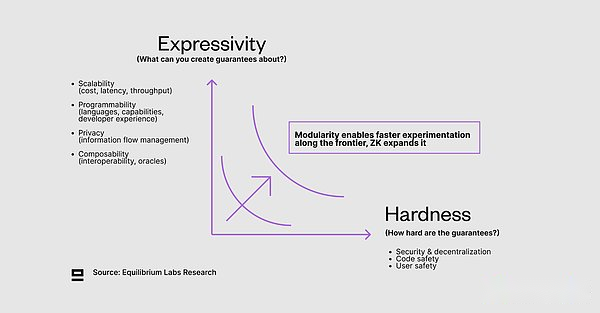
Although the underlying infrastructure has been significantly improved in the past ten years, before the blockchain can handle the scale of the Internet level, there are still many jobs to do.We see the trade -offs along the two main axes (expressiveness and hardness), and believe that modularization can be used to expand it at the ZK, and conduct faster experiments along the front edge of weighing:
-
Expression-What can you guarantee?Including scalability (cost, delay, throughput, etc.), privacy (orInformation flow management), Programmatic and combined.
-
Hardness -How difficult is these guarantees?Including security, decentralization, and user and code security.
>
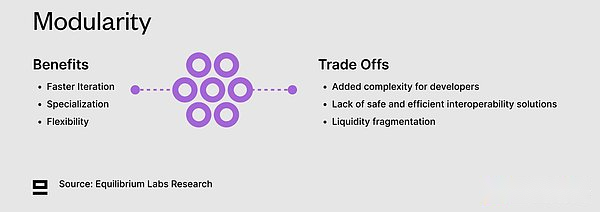
ModularIt refers to the system component that can be separated and re -combineddegree.Through faster feedback cycle and lower entry barriers, and less capital demand (economy and human resources) -modularization can achieve faster experiments and professionalism.The problem of modularity and integration is not binary, but a series of experiments to find out which parts are suitable for decoupling and which parts are not.
on the other hand,Zero Knowledge Proof (ZKP) to make one party(Proofer)Able to another(Verification)It proves that they know that something is real, and there is no need to disclose any additional information beyond its effectiveness.This can be re -executed (from all of the executionTo verifyThe model of the model is transformed intoOne execution, all verificationModel)To improve scalability and efficiency, and enable privacy (restrictions) to improve expressiveness.ZKP also improves the hardness of guarantee by using a stronger encryption economy to replace the weak encrypted economy guarantee, which is manifested to push the border outward (refer to the figure above).
>
We believe that modular and “all things ZK” will continue to accelerate.Although both provide interesting perspectives to explore the space alone, we are particularly interested in the cross of the two.The two key issues we are interested in are:
-
Which parts of the modular stack have been included in ZKP, and which parts have to be explored?
-
What problems can ZKP alleviate?
-
Account abstract (AA) enables smart contracts to be traded without a user signature (“programmable encryption account”) without each operation.It can be used to define who can sign (key management), what (transaction load), how to sign (signature algorithm), and when to sign (transaction approval conditions).These functions are combined to realize functions such as social login and DAPP interaction, 2FA, account recovery and automation (automatic signing).Although the discussion is usually revolved around Ethereum (ERC-4337 passed in the spring of 2023), many other chains already have built-in account account abstraction (APTOS, SUI, NEAR, ICP, StarkNet, and ZKSYNC).
-
The chain drawing allows users to sign a transaction on different chains, and at the same time interact with one account(One interface, multiple chains)EssenceMultiple teams are committed to this, including Near, ICP and DWALLET.These solutions use MPC and chain signed nicknames, and the private keys of another network are divided into several small parts, and signed a cross -chain transaction authentication to share on the source chain.When the user wants to interact with another chain, a sufficient number of verifications need to sign the transaction to meet the threshold encryption.This retains security, because the private key will never be completely shared anywhere.However, it does face the risk of the verifier’s collusion, which is why the encrypted economic security of the bottom chain is still highly related to the decentralization of the decentralization.
-
From a high level, intention can connect user needs with operations that blockchain can perform.This needIntention solution——The special chain proxy, the task is to find the best solution for the user’s intention.Some applications have already used special intentions, such as DEX polymer(“Best Price”)Hexiaxiaxin polymer (“the cheapest/fastest bridge connection”).General intent for settlement networks (ANOMA, Essential, Suave) aims to make it easier for users to express more complicated intentions and make developers easier to build an application -centric application.However, there are still many suspicious problems, including how to form the process, what the language is centered, and whether the optimal solution always exists and whether it can be found.
-
Use AA X ZK for authentication: One of the examples is SUI’s zklogin. It can log in with familiar credentials (such as email address).It uses ZKP to prevent third parties from linking the SUI address to its corresponding OAUTH logo.
-
AA wallet more efficient signature verification: Verify that transactions in AA contracts may be much more expensive than trading initiated by traditional accounts (EOA).ORBITER tries to solve this problem by binding services. The service uses ZKP to verify the correctness of the transaction signature and maintain the random value and GAS balance of the AA account (through the Merkle World Tree).It can be proved to be awarded the cost of verification on the average distribution chain between all users, which can significantly save costs.
-
The best execution or intentional proof: Although intention and AA can abstract complexity from users, they can also act as concentrated power and ask us to rely on specialized participants (resolved) to find the best execution path.ZKP can prove that the best path of the user is selected from the path sample of the solution device, instead of simply trusting the goodwill of seeking solving device.
-
Privacy of intention settlement: Agreement like TAIGA aims to achieve completely shielded intentions to protect users’ privacy -this is part of adding privacy (or at least confidential) to the blockchain network.It uses ZKP (HALO2) to hide sensitive information (application types, recipients, etc.) on state conversion.
-
AA wallet password recovery: The idea behind the proposal is to allow users to restore the wallet when they lose their private keys.By storing hash values (passwords, random numbers) on the contract wallet, users can generate ZKP with the help of a password to verify that this is their account and request to change the private key.The confirmation period (3 days or longer) can prevent unauthorized interviews.
-
Verifying the correct encryption of memory pool: Radius is a shared sorting network with a practical encryption memory pool with a practical can be delayed.The user generates a ZKP to prove that solving the problem of time locking will lead to the correct decryption of effective transactions, that is, the transaction contains effective signatures and random numbers, and the sender has sufficient balance to pay transaction fees.
-
Verifying sorting rules (VSR): Make proposals/sorters abide by a set of rules related to execution order, and additional guarantees to comply with these rules.Verification can be proof of ZKP or fraud, and the latter needs sufficient economic bonds. If the proposal/sorter has improper behavior, economic bonds will be cut.
-
ZKEVM Rollups: A special type of ZKVM, which is optimized compatible with Ethereum and proves the EVM execution environment.However, the closer the compatibility of Ethereum, the greater the trade -offs.In 2023, multiple ZKEVM was launched, including Polygon ZKEVM, ZKSYNC Era, Scroll and Linea.Polygon recently released their type 1 ZKEVM proofer, which can prove that the main network of Ethereum is proved at a price of $ 0.20-0.50 each (to be optimized to further reduce costs).Risczero also has another solution that proves the Ethereum block, but due to the limited benchmark test available, the cost is high.
-
Alternative ZKVM: Some protocols are taking alternative paths and optimizing the friendship of performance/provenability (zorp) or developers, instead of trying to maximize compatibility with Ethereum.Examples of the latter include the ZKWASM protocol (FLUENT, Delphinus Labs) and Zkmove (M2 and ZKMOVE).
-
ZKVM, which focuses on privacy: In this case, ZKP is used for two things: avoid re -execution and realization of privacy.Although the use of ZKP alone is limited (only limitedPersonal private state) But the upcoming agreement adds a lot of expression and programming to the existing solution.Examples include Aleo’s snarkvm, AVM of Aztec, and Midenvm of Polygon.
-
ZK-Synthetic processor: Enable the chain calculation of the data on the chain (but no state).ZKP is used to prove the correct execution and provides faster settlement speed than the Optimized Association processor, but needs to be weighing in cost.Considering the cost and/or difficulty of generating ZKP, we have seen some hybrid versions, such as Brevis Cochain, which allows developers to choose between ZK or optimistic mode (weighing between cost and guarantee hardness).
-
Important ZKVM: Most basic layers (L1) still use re -execution to verify the correct state conversion.Turn ZKVM into the basic layer to avoid this, because verificationrs can verify proof.This will improve operating efficiency.Most people’s eyes are concentrated on Ethereum with ZKEVM, but many other ecosystems also depend on re -execution.
-
ZKSVM: Although SVM is currently used in Solana L1, teams like Eclipse are trying to use SVM to summarize Ethereum.Eclipse also plans to use RISC ZERO for ZK fraud to deal with the potential challenges of status conversion in SVM.However, mature ZKSVM has not been explored -it may be due to the complexity of the problem and the fact that SVM has optimized other aspects other than provenability.
-
Storage certificate: You can inquire history and current data from the blockchain without using a trusted third party.ZKP is used to compress and proves the correct data.Project examples built in this field include Axiom, Brevis, Herodotus, and Lagrange.
-
Efficient query in the state of privacy: Privacy items usually use variants of the UTXO model. It can provide better privacy functions than account models, but the price is the friendship of sacrifice developers.The private UTXO model may also cause synchronization problems -since 2022, Zcash has been working hard to solve this problem after experiencing a significant increase in transaction volume.Wallets must be synchronized to the chain before using funds, so this is a fairly fundamental challenge for the operation of the network.Considering this problem, Aztec recently released an RFP about the foundation of banknotes, but has not found a clear solution.
-
Stark with a Snark box: Stark proof is fast and does not require credible settings, but the disadvantage is that they will generate a large number of proofs, and the cost of verifying these proofs on Ethereum L1 is too high.The last step is encapsulated in Snark, which greatly reduces the cost of verification on Ethereum.The unfavorable side is that this has increased complexity, and the security of these “composite proof systems” has not been thoroughly studied.Existing existing examples include Boojum and RISC ZERO in Polygon Zkevm, ZKSYNC Era.
-
GM decentralization certificate network: Integrate more applications into the decentralized certification network to make the proofer more efficient (higher hardware utilization), which is cheaper for users (no need to pay for hardware redundancy).Projects in this field include Gevulot and Succinct.
-
ZK fraud certificate: In an optimistic solution, anyone can challenge the state conversion and create a fraud certificate during the challenge.However, the verification of verification of proves that it is still quite cumbersome because it is completed by re -execution.The ZK fraud certificate aims to solve this problem by creating a challenging state conversion certificate, thereby achieving more effective verification (no need to re -execute) and may be faster.At least Optimism (collaboration with O1 Labs and Risczero) and Altlayer X Risczero are committed to this.
-
More efficient proof aggregation: An important feature of ZKP is that you can aggregate multiple proofs as a proof without significantly increased verification costs.This enables the verification costs of multiple proofs or applications.Proved aggregation is also a proof, but the input is two proofs rather than executing tracking.Project examples in this field include Nebra and Gevulot.
-
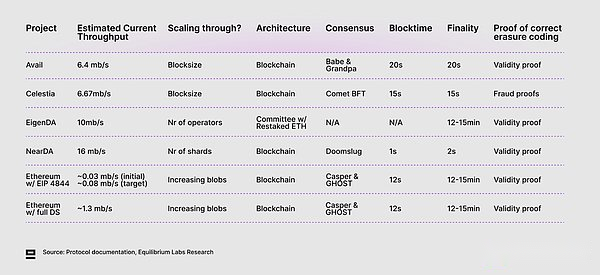
Prove the correctness of the default code: The deletion code brings a certain degree of redundancy. Even if part of the coding data is not available, the original data can be restored.This is also a prerequisite for DAS. Among them, the light node only samples a small part of the block to ensure that the data exists.If the malicious proposal has an error encoding of the data, even if the light node samples enough only one piece, the original data may not be recovered.It can prove the correct deletion code to use effective proof (ZKP) or fraud -the latter will be affected by delays related to the challenge period.All other solutions except Celestia are committed to using validity proof.
-
ZK light client supports the data bridge: Rollups using external data release layers still need to be released correctly with the settlement layer communication data.This is the purpose of the data proved bridge.Using ZKP can make the verification of Ethereum Shangyuan Chain Consensus signature more efficient.Avail (Vectorx) and Celestia (BlobstreamX) data proof bridges are supported by the ZK light client built with SUCCINCT.
-
Celestia combines the validity proof of correct erase encoding: Celestia is currently a heterogeneous in the data release network, because it uses fraud proof to achieve the correct erase code.If the malicious block proposal has an error encoding the data, any other node can generate a scam proof and question it.Although this method is relatively simple to implement, it also introduces delays (this block is the ultimate after the fraud certificate), and it is necessary to trust a honest all node to generate a fraud certificate (unable to verify it).However, Celestia is exploring the combination of its current Reed-Solomon encoding with ZKP to prove that the encoding is correct, which will significantly reduce the finality.You can find the latest discussion around this theme. Here are the records of the previous working group (except to add ZKP to more ordinary attempts to the basic layer of Celestia).
-
ZK proves that DAS: The availability of ZK proof has been explored. Among them, light nodes will simply verify the Merkle root and ZKP without having to use the download of small pieces of data for usual sampling.This will further reduce the requirements for light nodes, but development seems to have stagnated.
-
Storage certificate: Long -term storage providers need to generate ZKP regularly to prove that they have stored all the data they claim.An example of this aspect is Filecoin’s Time and Space Certificate (POST), where the storage provider successfully answered the POST challenge each time it will get block rewards.
-
Prove the source of data sources and view of sensitive data: For two unbelievable recipes who want to exchange sensitive data, ZKP can be used to prove that one party has the credentials required for viewing data without uploading actual documents or leaking passwords and logs.Details.
-
Pledge in ZK -based privacy networks: POS -based privacy networks have challenged, because the holders of the pledged token must make choices between privacy and participation in consensus (and get pledge rewards).Penumbra aims to solve this problem by eliminating pledge rewards. Instead, non -mortgage and mortgage shares are regarded as separate assets.This method keeps privacy of each commission, and the total amount bound to each verificationr is still public.
-
Private governance: Realizing anonymous voting for a long time has been a challenge in the encryption field. Noun private voting and other projects try to promote this process.This is also applicable to governance, at least Penumbra is conducting anonymous voting on the proposal.In this case, ZKP can be used to prove that a person has the right to vote (such as via token ownership) and meet certain voting standards (such as not voting).
-
Private leaders election: Ethereum currently elected the next 32 block proposals at the beginning of each EPOCH, and the results of this election are public.This will bring a malicious party to launch a DOS attack on each proposal in order to try to disable the risk of Taifang.To solve this problem, WHISK proposed a proposal for a privacy protection agreement for the election proposal on Ethereum.The verified by ZKP to prove that shuffle and randomization are honest.There are other methods that can achieve similar ultimate goals. This blog post from A16Z introduces some of them.
-
Signature aggregation: The use of ZKP aggregation signature can significantly reduce the communication and calculation overhead of the signature verification (verify a polymerization evidence instead of each separate signature).This has been used in the ZK light client, but it may also expand to consensus.
-
Accelerate the settlement through effectiveness summary: Compared with optimism summary, the effectiveness of effectiveness does not require a challenge period, because they depend on ZKP to prove the correct state conversion, whether anyone challenges (whether anyone challenges (whether anyone challenges it (Pessimistic summaryTo.This makes the basic layer setting faster (the settlement time on Ethereum is 12 minutes, and the settlement time on Ethereum is 7 days), and avoid re -execution.
-
Eigenlayer’s goal is to use existing Ethereum security to protect extensive applications.The white paper was released in early 2023. Eigenlayer is currently in the main network Alpha stage. The complete main network is expected to be launched later this year.
-
COSMOS launched the chain security (ICS) in May 2023, which enables COSMOS Hub (one of the largest chains on COSMOS, supported by about $ 2.4 billion pledged ATOM) to rent its safety to the consumer chain.By using the same authentication set provided for COSMOS HUB to verify the block on the consumer chain, its purpose is to reduce the obstacles to launch the new chain at the top of the cosmos stack.However, only two consumer chains are currently in activities.
-
BABYLON also tries to make BTCs use for sharing security.In order to solve the problems related to merging mining (difficult to punish bad behaviors), it is building a virtual POS layer, and users can lock BTC to Bitcoin’s pledge contract (no bridge connection).Because Bitcoin does not have a smart contract layer, the reduction of the pledge contract is expressed in UTXO transactions written in the Bitcoin script.
-
The re -mortgage on other networks includes Octopus on Near and Picasso on Solana.Polkadot parallel chain also uses the concept of shared security.
-
The mix of ZK and economic security: Although the security guarantee based on ZK may be stronger, for some applications, the cost of proof is still too high, and it takes a long time to generate proof.Brevis Cochain is an example. It is a collaborator that obtains economic security from ETH re -pledges and optimizes calculations (proves through ZK fraud).DAPP can choose a pure ZK or Cochain mode according to its specific needs in terms of security and cost trade.
-
ZK Light Client (Consensus Verification): At present, most light clients can verify the consensus of other chains-either a complete authentication set (if it is small enough), or the subset of all the verification device (such as the synchronization of Ethereum, synchronization of Ethereum.Committee).ZKP is used to make verification faster and cheaper, because the signature scheme used on the source chain may not be supported by the target chain.Although the importance of the ZK light client in the bridge is expected to increase, the current widely used friction includes the cost of proof and verification and the cost of the ZK light client implemented by each new chain.Examples in this field include data proof bridges of PolyHedra, Avail, and Celestia, as well as ZKIBC.
-
Storage certificate: As mentioned earlier, the storage certificate can inquire history and current data from the blockchain without using a trusted third party.This is also related to interoperability because they can be used for cross -chain communication.For example, users can prove that they have tokens on one chain and use it for governance on another chain (no bridge).There are also trials to use storage certification for bridge, such as a solution developed by Lambdaclass.
-
ZK Oracles: Oracles acts as an intermediary and connects the real -world data to the blockchain.The ZK prophecy machine has improved the current reputation -based prophet model through the source of the data and the integrity of the data and any calculation of the data.
-
Complete light client: The complete light client also verifies the correct execution and DA instead of blindly trusting the authentication set of other chains.This reduces trust assumptions and is closer to complete nodes, while still maintaining lower hardware requirements (allow more people to run light clients).However, on most chains, especially on Ethereum, any other content except consensus is still expensive.In addition, the light client only enables information verification (half of the problem), that is, they can recognize the information that is fake, but still requires additional mechanisms for them to take measures.
-
Polymer layer: Polygon’s Agglayer aims to achieve smooth interoperability between L2 between L2 in the ecosystem by using polymerization proof and unified bridge contracts.The aggregation proof can achieve more effective verification and security -compulsory dependencies chain status and bundle bags are consistent, and ensure that if the summary status depends on the invalid state of another chain, it cannot be solved in Ethereum.ZKSYNC’s Hyperchains and Avail Nexus also adopted a similar method.
-
All unnecessary reorganizations are eliminated: By turning to 1/N execution model (instead of re -execution of N/N), we significantly reduce the overall redundancy of the network and can use the underlying hardware more effectively.Although there are still some expenses, this will help the blockchain gradually approach the centralized system in terms of computing efficiency.
-
Most applications rely on the encryption guarantee supported by ZK, not economic security: When the cost and time of generating proof are no longer related factors, we believe that most applications will rely on ZKP to obtain stronger guarantees.This also requires some improvements in availability and development personnel to build ZK applications, but these are issues that many teams are working hard to solve.
However, before discussing these issues, we need to understand the latest situation of the module stack in 2024.
Module stack in 2024
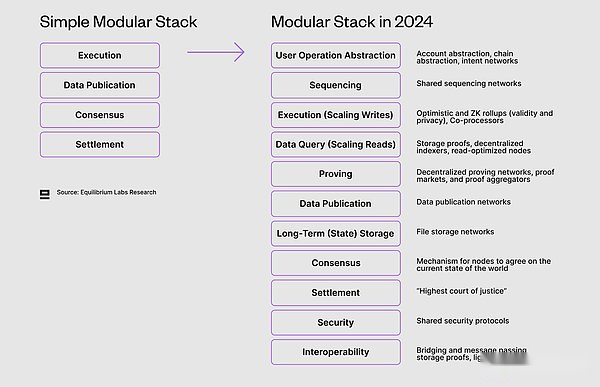
With four components (execution, data release, consensus, settlement)Common images of modular stacks are useful as simple psychological models, but considering how much modular space has developed, we think it is no longer a sufficient representation.Further spin -off has led to a new component that was previously considered a larger part, and at the same time, it also created new dependencies and the safe and interoperability needs between different components (the detailed introduction will be introduced later).Considering the development speed of this field, it is difficult to understand all innovations at different levels of stacks in time.
Early attempts to explore the WEB3 stack include the attempts of Kyle Samani (Multicoin)-were first released in 2018 and updated in 2019.It covers everything from the decentralized last mile Internet visit (such as Helium) to end user key management.Although the principles behind it can be reused, some parts, such as proof and verification, are completely missing.
Considering this, we tried to create a 2024 module stack update, which expanded the existing four -part modular stack.It is divided according to components rather than functions, which means that P2P networks, etc. are included in consensus, rather than split it into separate components -mainly because it is difficult to build protocols around it.
>
ZK in the modular stack
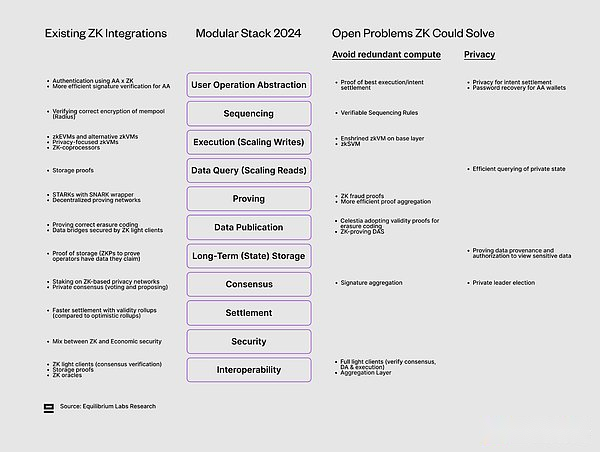
Now we have a modular stack update view. We can start studying the real problems, that is, what parts of ZK have penetrated the stack and which open problems that can be solved by introducing ZK (avoid re -execution or privacy -characteristics).Before studying each component separately, the following is the summary of our discovery.
>
1 -The user operation abstraction
The current blockchain users need to browse multiple chains, wallets and interfaces, which is troublesome and will hinder more widely adopted.User operation abstraction is a general name that refers to any attempt to abstract such complexity and allows users to interact with only one interface (such as a specific application or wallet), and all complexity occurs at the back end.Some examples of bottom -level abstraction include:
Existing ZK Integration
The open problem that ZKP can solve
2 -Sequence
Before the transaction is added to the block, it needs to be sorted, which can be completed in various ways: sorted according to the profitability of the proposal (first paid the maximum payment transaction), according to the sequence of submittingTransactions of private memory pools.
Another problem iswhoYou can order transactions.In the modular world, multiple different parties can perform this operation, including summary sorters (centralized or decentralized), L1 sorting (based on summary) and shared sorting networksTo.All these have different trust assumptions and extensions.In practice, the actual sorting of the transaction and bundling them into a block can also be completed outside the protocol by special participants (block builders).
Existing ZK Integration
The open problem that ZKP can solve
3 -Execution (scaling writing)
The execution layer contains the logic of status update and is also the place where smart contract executions.In addition to returning calculated outputs, ZKVM can also prove whether the status conversion is completed correctly.This allows other network participants to verify the correct execution without verifying proof without having to re -execute transactions.
In addition to faster and more efficient verifications, another benefit that proves that it can be implemented is that more complicated calculations can be achieved, because you will not encounter typical GAS problems and limited chain resource issues calculated outside the chain.This opens the door for the new application. These applications have a greater calculation intensity and can run on the blockchain and use guaranteed calculations.
Existing ZK Integration
The open problem that ZKP can solve
4 -Data query (scaling read)
Data query, or reading data from the blockchain is an important part of most applications.Although most of the discussions and efforts in recent years are concentrated on extension (execution), it is more important to expand reading due to the imbalance between the two (especially in a decentralized environment).The reading/writing ratio between blockchain is different, but a data point estimated by SIG is that 96% of all calls of nodes on Solana are readings (based on 2 -year experience data) -Reading/The writing ratio is 24: 1. 1.
Extended reading includes higher performance (such as SIG on Solana) through the dedicated verification device client (such as SIG on Solana) (more read per second) and enable more complicated queries (combine reading and calculation)With the help of the processor.
Another angle is the decentralization of the data query method.Today, most of the data query requests in the blockchain are promoted by trusted third parties (based on reputation), such as the RPC node (Infura) and indexes (DUNE).Examples of more decentralized options include The Graph and memory storage components (also verified).There are also some attempts to create decentralized RPC networks, such as Infura Din or LAVA Network (except for decentralized RPC, LAVA’s goal is to provide additional data access services later).
Existing ZK Integration
The open problem that ZKP can solve
5 -proof
As more and more applications are included in ZKP, proof and verification are rapidly becoming an important part of the modular stack.However, most of the proof of infrastructure is still permitted and concentrated, and many applications depend on a single proof.
Although the centralized solutions are not complicated, the decentralized proof architecture and splitting it into a modular stack separately component will bring a variety of benefits.One key is the form of activity guarantee, which is essential for applications generated by frequent proofs.Users also benefit from higher censorship resistance and lower cost driven by competition and multiple proofers.
We believe that the GM Certificate Network(Many applications, many proofers)Better than the single application proof network(A application, many proofers),Because the existing hardware utilization rate is higher, the complexity of provers is lower.Higher utilization is also conducive to users to reduce costs, because proofers do not need to compensate redundancy through higher costs (still need to pay for fixed costs).
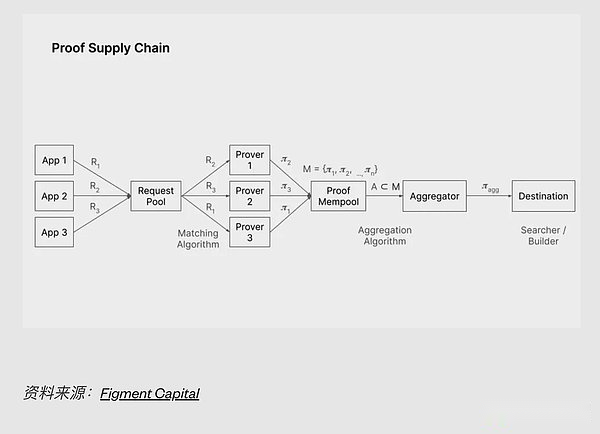
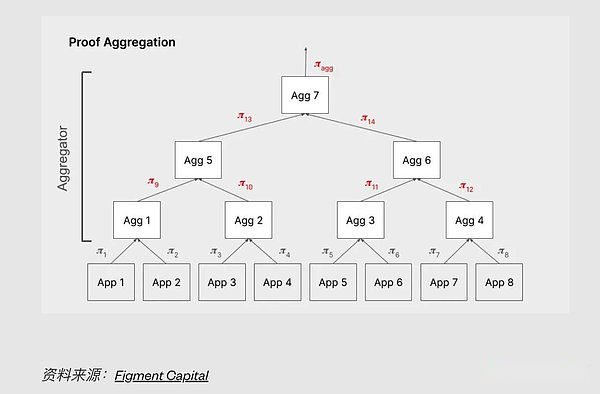
Figment Capital has well summarized the current state of the supply chain, which includes proved generation and proof aggregation(It is proved to be generated, but only two proofs are used as inputs rather than executing tracking).
>
Existing ZK Integration
The open problem that ZKP can solve
>
6 -Data release (available)
Data release (DP)Make sure that data can be available in a short time (1-2 weeks).This is for security (optimistic summary requires input data to verify the correct execution by re-execution within the challenge period (1-2 weeks)) and active (even if the system uses validity proof, data may be proved to asset ownership) to be related)important.Escape cabin or compulsory transaction).Users (such as ZK-Bridges and Rollups) are facing one-time payment, which covers the cost of storing transactions and status within a short time before being trimmed.Data release network is not designed for long -term data storage(On the contrary, please refer to the next section to understand the possible solutions)Essence
Celestia is the first alternative DP layer for launching the main network (October 31), but there will be many alternatives to choose from soon, because Avail, EIGENDA, and Near DA are expected to be launched during 2024.In addition, Ethereum’s EIP 4844 upgrade has also expanded to publish data on Ethereum (except for creating a separate expense market for BLOB storage), and laid the foundation for complete DANK shards.DP is also expanding to other ecosystems -Nubit is an example, which aims to build Native DP on Bitcoin.
>
Many DP solutions also provide services other than pure data release, including sharing security (such as CELESTIA and Avail), or more smooth interoperability (such as Avail’s NEXUS).There are also some projects (Domicon and Zero Gravity) both provide data release and long -term state storage, which is a striking proposal.This is also an example of two components in the modular stack. We may see more progress (further spin -off and re -bundled experiments).
Existing ZK Integration
The open problem that ZKP can solve
7 -Long -term (status) storage
Storage of historical data is important, mainly for synchronous purpose and service data requests.However, all data is not feasible for each full node, and most of the whole node will trim the old data to keep the hardware demand reasonable.On the contrary, we rely on specialized agencies (archive nodes and indexes) to store all historical data and provide these data according to user requests.
There are also decentralized storage providers, such as Filecoin or Arweave, which provides long -term decentralized storage solutions at reasonable prices.Although most blockchains do not have a formal archive storage procedure (only depend onSomeoneStorage), but decentralized storage protocol is a good candidate who stores the built -in storage historical data and add some redundant (at least X -node storage data).In the incentives.
Existing ZK Integration
The open problem that ZKP can solve
8 -Consensus
Given that the blockchain is a distributed P2P system, there is no credible third parties with the truth of the global truth.Instead, the network node reached an agreement on the current truth (which block is correct) through a mechanism called consensus.POS -based consensus methods can be divided into BFT -based (where the verifications of Byzantine determine the final state) or the chain -based (final state is determined by the division selection rules traceable).Although most existing POS consensus is based on BFT, Cardano is an example of the longest chain implementation.People are becoming more and more interested in DAG-based consensus mechanisms, such as Narwhal-Bullshark, which are implemented with certain variants in Aleo, Aptos, and SUI.
Consensus is an important part of many different components of the modular stack, including shared sorters, decentralized certifications, and blockchain -based data release networks (not based on committees, such as EIGENDA).
Existing ZK Integration
The open problem that ZKP can solve
9 -Settlement
Lise is similar to the correctness of the Supreme Court -verifying the correctness of the state conversion and the final truth source of the dispute.When a transaction is irreversible (or when the probability ultimateness -when it is difficult to reverse), the transaction is considered the final.The final determined time depends on the underlying settlement layer used, and this depends on the specific final determination rules and block time.
The slow ultimateness is especially a problem in cross -rollup communication. Among them, Rollup needs to wait for the confirmation of Ethereum to approve the transaction (optimistic Rollups takes 7 days, and the effective RollUps takes 12 minutes and the certificate time).This leads to poor user experience.There are many ways to use a pre -confirmation of a certain security level to solve this problem.Examples include solution -specific solutions (POLYGON AGGLAYER or ZKSYNC Hyperbridge) and universal solutions (eg, Fast Finality Layer).EssenceYou can also choose to use EIGENLAYER’s summary bridge for soft confirmation to avoid waiting for being completely determined.
Existing ZK Integration
10 -security
Safety is related to the hardness of guarantee, and it is also an important part of blockchain value claim.However, it is difficult to guide the security of encrypted economic security -increasing the innovation friction of applications (various middleware and alternative L1) that requires it.
The idea of sharing security is to use the existing economic security of the POS network and to withstand additional reduction of risks (punishment conditions), rather than trying to guide their own security.In the early days, some attempts to do the same thing on the POW network (merged mining), but inconsistent incentives make it easier for miners to collude and use the agreement (because work occurs in the physical world, it is more difficult to punish bad behaviors, even if you use it, even if you use it, even if you use it, even if you use it, even if you use it, even if you use it, even if you use it.Computing power).POS is more flexible and can be used by other protocols because it has positive (pledge income) and negative (reduced) incentives.
Agreement built around shared security prerequisites includes:
Existing ZK Integration
11 -Mutual operation
Safe and efficient interoperability is still a major problem in the multi -chain world. The loss of $ 2.8 billion caused by bridge hackers is an example.In the modular system, interoperability becomes more important -not only communicating between other chains, but also the modular blockchain also requires different components to communicate with each other (such as DA and settlement layers).Therefore, it is no longer feasible to run a complete node or verify a single consensus certificate as integrated blockchain.This adds more mobile factors to the equation.
Interoperability includes token bridges and more ordinary message transmission across blockchain.There are several different options that they have made different signs in terms of security, delay and cost.It is very difficult to optimize these three, and it usually needs to sacrifice at least one.In addition, the different standards of cross -chain make the implementation of the new chain more difficult.
>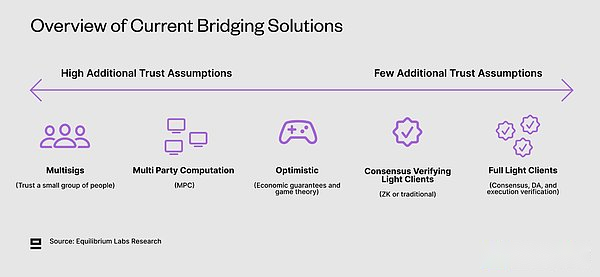
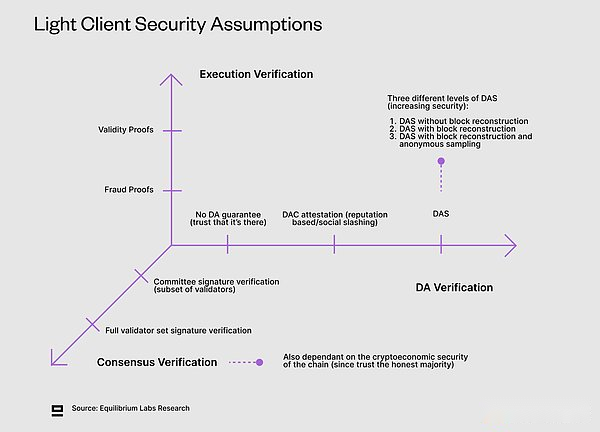
Although we still lack the clear definition of different types of light clients (or nodes), this article by Dino (Fluent & Amp; Modular Media co -founder) gives a good introduction.Today, most light clients only verify consensus, but ideal, we should have light clients that can verify and execute and DA to reduce the assumptions of trust.This will allow the security of the whole node without high hardware requirements.
>
Existing ZK Integration
The open problem that ZKP can solve
When did ZK eat the modular stack?
Suppose we can reach such a state: the generation of ZKP becomes very fast (At a speed of light) And very cheap(Almost free)So what will the final situation look like?In other words -zkwhenEat the modular stackIntersection
In a broad sense, we believe that there are two things in this case that are correct:
The third condition is privacy (or orInformation flow management), But it is more complicated.ZKP can be used for some privacy applications with client proof. This is the goal of platforms such as Aleo, Aztec or Polygon Miden, but to achieve large-scale privacy for all potential cases, it also depends on the progress of MPC and FHE-Future Blog ArticlesPotential theme.
The risk of our paper
If we are wrong, what should we do if it is neither modular nor ZK in the future?Some potential risks of our papers include:
Modularization increases complexity
Both users and developers are facing the growth of the number of chains.Users need to manage funds across multiple chains (and multiple wallets).On the other hand, considering that space is still developing, the stability and predictability of application developers are poor, which makes it more difficult to determine which chain to build.They also need to consider the fragmentation of status and liquidity.This is especially true, because which components are still decoupled by which components are meaningful and which components will be tested at the frontier of coupling.We believe that users operate abstract and safe and efficient interoperability solutions are the key part of this problem.
>
Is ZK’s performance good enough?
The unavoidable fact is that the proof of generation is too long, and the cost of proof and verification is still too high today.For many applications today, competitive solutions such as trusted execution environment/Tee or optimistic/encrypted economic security solutions (cost) are still more meaningful.
However, we are doing a lot of work on Software optimization and hardware acceleration of ZKP.Prove that aggregation will help further reduce verification cost by splitting costs to multiple different parties (lower/user costs).You can also adjust the basic layer to optimize ZKP verification.A challenge facing ZKP hardware acceleration is to prove the rapid development of the system.This makes it difficult to create a special hardware (ASIC), because when/when the standards of the underlying proof system are developed, they may be outdated soon.
Ingonyama attempts to create some benchmarks as proof of the provenor by comparable indicators called ZK scores.It is based on the cost of running computing and tracks MMOPS/WATT, where MMOPS represents the calculation per second.To read the theme further, we recommend Cysic and Ingonyama blogs, as well as WEI DAI speeches.
Is ZKP a limited hidden private use?
ZKP can only be used to realize the privacy of personal status, and cannot be used for sharing status that needs to be calculated by multi -parties (such as private Uniswap).FHE and MPCs also need to be completely privacy, but before they become more widely used, they need to increase many orders of magnitude in terms of cost and performance.In other words, ZKP is still useful for some use cases that do not need private sharing, such as identity solutions or payment.Not all problems need to be solved by the same tool.
Sum up
So what impact does this bring to us?Although we are progressing every day, there are still a lot of work to do.The most urgent need to solve is how values and information flow safely between different modular components without sacrificing speed or cost, and abstract all of them from the final consumers so that they do not need to care about care, so that they do not need to care about care, they do not need to care about care, so they do not need to care about care.The bridge connects different chains, switch wallets, etc.
Although we are still in the experimental stage, over time, when we find out the best trade -offs of each use case, the situation should be stable.In turn, it will provide space for standards (informal or formal), and provide more stability for builders above these chains.
Today, due to the cost and complexity of ZKP, there are still many use cases that use encrypted economic security by default, and some use cases require the combination of the two.However, as we design more efficient proof systems and special hardware to reduce the cost and delay of proof and verification, this share should be reduced over time.With each index level of cost and speed, new use cases will be unlocked.
Although this article pays special attention to ZKP, we are also increasingly interested in how the modern cryptographic solution (ZKP, MPC, FHE, and Tee) will eventually play a role -we have seen this.







