
Source: ArkStream Capital
Preface
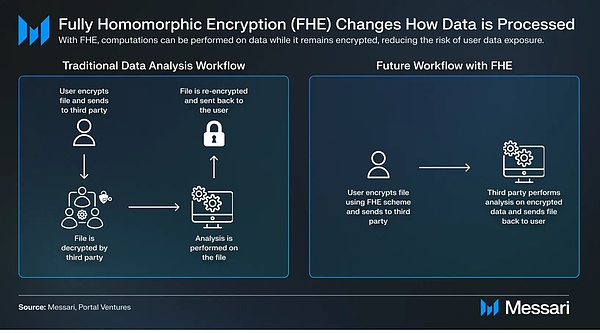
In the past, cryptography technology has played an important role in the progress of human civilization, and has played an irreplaceable role in the fields of information security and privacy protection.It not only provides solid protection for data transmission and storage in various fields, but also its asymmetric encryption public-private key system and hash function were creatively integrated by Satoshi Nakamoto in 2008 to design a solution to the problem of double flowers.The proof-of-work mechanism of the problem has promoted the birth of Bitcoin, a revolutionary digital currency, and opened a new era in the blockchain industry.
With the continuous evolution and rapid development of the blockchain industry, a series of cutting-edge cryptography technologies have emerged continuously, among which Zero Knowledge Proof (ZKP), Multi-party Computing (MPC) and Fully Homomorphic Encryption (FHE) are the most prominent.These technologies have been widely used in many scenarios, such as ZKP combined with Rollup solution to solve the “impossible triangle” problem of blockchain, and MPC combined with public-private key system to promote large-scale application of user portals (Mass Adoption).As for the fully homomorphic encryption FHE, considered one of the holy grails of cryptography, its unique characteristics allow third parties to calculate and operate encrypted data at any number of times without decryption, thereby achieving composable on-chain privacy.Computing brings new possibilities to multiple fields and scenarios.
Quick overview of FHE
When we mention FHE (full homomorphic encryption), we can first understand the meaning behind its name.First of all, HE represents homomorphic encryption technology, and its core feature is that it allows calculations and operations to be performed on ciphertexts, and these operations can be mapped directly to plaintexts, that is, keeping the mathematical properties of encrypted data unchanged.The “F” in FHE means that this homomorphism has reached a whole new level, allowing infinite calculations and operations on encrypted data.
To help understand, we chose the simplest linear function as the encryption algorithm, and combined with the single operation instructions for addition and multiplication homomorphism.Of course, actual FHE uses a series of more complex mathematical algorithms, and these algorithms require extremely high computing resources (CPU and memory).
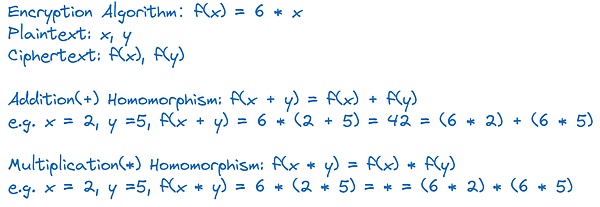
Although the mathematical principles of FHE are profound and complex, we will not expand on them too much here.It is worth mentioning that in the field of homomorphic encryption, in addition to FHE, there are two forms: some homomorphic encryption and some homomorphic encryption.The main difference is that the types of operations supported and the number of operations allowed are different, but also provides the possibility for implementing the calculation and operation of encrypted data.However, in order to keep the content simple, we will not discuss it in depth here.
In the FHE industry, although many well-known companies are involved in research and development, Microsoft and Zama have highlighted their unparalleled availability and influence with their outstanding open source products (code library).They provide developers with stable and efficient FHE implementation, and these contributions have greatly promoted the sustainable development and wide application of FHE technology.
Microsoft’s SEAL: A FHE library carefully created by Microsoft Research Institute, not only supports full homomorphic encryption, but is also compatible with partial homomorphic encryption.SEAL provides an efficient C++ interface and significantly improves computing performance and efficiency by integrating numerous optimization algorithms and technologies.
Zama’s TFHE: is an open source library focusing on high-performance fully homomorphic encryption.TFHE provides services through the C language interface and uses a series of advanced optimization technologies and algorithms to achieve faster computing speed and lower resource consumption.
According to the simplified idea, the operation process of experiencing FHE is roughly as follows:
-
Generate keys: Use the FHE library/framework to generate a pair of public and private keys.
-
Encrypted data: Use a public key to encrypt data that needs to be processed for FHE.
-
Perform homomorphic calculation: Use the homomorphic calculation function provided by the FHE library to perform various calculation operations on the encrypted data, such as addition, multiplication, etc.
-
Decryption result: When you need to view the calculation result, a legitimate user uses the private key to decrypt the calculation result.
In FHE’s practice, the management scheme of decryption keys (generation, circulation and use, etc.) is particularly critical.Since the calculation and operation results of encrypted data need to be decrypted for use in certain moments and scenarios, the decryption key becomes the core of ensuring the security and integrity of the original data and processed data.Regarding the management of decryption keys, the solution actually has many similarities with traditional key management, but given the particularity of FHE, it is also possible to design and adopt more rigorous and meticulous strategies.
For blockchain, due to its decentralization, transparency and immutability, the introduction of a threshold multi-party security computing solution (TMPC) is a promising choice.This scheme allows multiple participants to jointly manage and control the decryption key, and the data can be successfully decrypted only when the preset threshold number (i.e., number of participants) is reached.This not only improves the security of key management, but also reduces the risk of a single node being compromised, providing a strong guarantee for the application of FHE in the blockchain environment.
Lay the foundation fhEVM
From the perspective of minimal intrusion, the ideal way to implement FHE application on blockchain is to encapsulate it into a universal smart contract code base to ensure lightness and flexibility.However, this solution is premised on the fact that the smart contract virtual machine must pre-support a specific set of instructions for complex mathematical operations and encryption operations required by FHE.If the virtual machine cannot meet these requirements, it must be customized and modified in the core architecture of the virtual machine to meet the needs of the FHE algorithm, thereby achieving its seamless integration.
As a widely adopted and long-term validated virtual machine, EVM naturally becomes the first choice for implementing FHE.However, there are few practitioners in this field, among which we once again noticed the open source TFHE Zama.It turns out that Zama not only provides a basic TFHE library, but also launches two important open source products: Concrete ML and fhEVM as a technology company focusing on applying FHE technology to the fields of artificial intelligence and blockchain.Concrete ML focuses on machine learning privacy computing.Through Concrete ML, data scientists and ML practitioners can train and infer machine learning models on sensitive data while protecting privacy, thereby making full use of data resources without worrying about privacy leakage.Another product, fhEVM, is a fully homomorphic EVM that supports Solidity to implement privacy computing.fhEVM allows developers to use fully homomorphic encryption technology in Ethereum smart contracts to achieve privacy protection and secure computing.
By reading fhEVM’s information, we learned that the core features of fhEVM are:
-
fhEVM: At the non-EVM bytecode level, in the form of inline functions, FHE operation support is provided by integrating multiple precompiled contracts in different states of the Zama open source FHE library.In addition, a specific EVM memory and storage area is specially created for FHE to store, read, write and verify FHE’s ciphertext;
-
Decryption mechanism based on distributed threshold protocol: Supports the global FHE key that mixes encrypted data between multiple users and multiple contracts and stores encryption keys on the chain, and multi-party security computing solution with thresholds between multiple validatorsShare the asynchronous encryption mechanism of decryption keys;
-
Solidity contract library that lowers the threshold for developers to use: designed FHE’s encrypted data types, operation types, decrypted calls and encrypted outputs;
Zama’s fhEVM provides a solid starting point for FHE technology in blockchain applications, but considering that Zama mainly focuses on technology research and development, its solutions are more technical, and there are relatively few thoughts on engineering implementation and commercial applications..Therefore, fhEVM may encounter various unexpected challenges in its promotion to practical applications, including but not limited to technical thresholds and performance optimization problems.
Building an ecosystem FHE-Rollups
A simple fhEVM itself cannot form a project or a complete ecosystem alone, it is more like one of the diverse clients in the Ethereum ecosystem.To be a stand-alone project, fhEVM must rely on public chain-level architecture or adopt Layer2/Layer3 solutions.The development direction of FHE public chain is inevitably to solve how to reduce the redundancy and waste of FHE computing resources among distributed validator nodes.On the contrary, the Layer2/Layer3 scheme that exists as the public chain execution layer itself can allocate computing work to a few nodes, greatly reducing the order of magnitude of computing overhead.Because of this, Fhenix, as a pioneer, actively explores the combination of fhEVM and Rollup technology and proposes to build an advanced FHE-Rolups-type Layer2 solution.
Considering that the ZK Rollups technology involves complex ZKP mechanisms and requires huge computing resources to generate the proofs required for verification, combining the characteristics of the entire FHE itself, directly implementing the FHE-Rollups-based FHE-Rollups solution will face many challenges.Therefore, at the current stage, it will be more practical and efficient to adopt the Optimistic Rollups solution as Fhenix’s technology choice compared to ZK Rollups.
Fhenix’s technology stack mainly includes the following key components: a variant of Arbitrum Nitro’s fraud prover, which can perform fraud proof in WebAssembly. Therefore, FHE logic can be compiled into WebAssembly for safe operation.The core library fheOS provides all the features needed to integrate FHE logic into smart contracts.Threshold Service Network (TSN) is another important component that hosts secretly shared network keys, splits them into multiple copies using secret sharing technology of a specific algorithm to ensure security, and, if necessary, is responsible for tasks such as decrypting data..
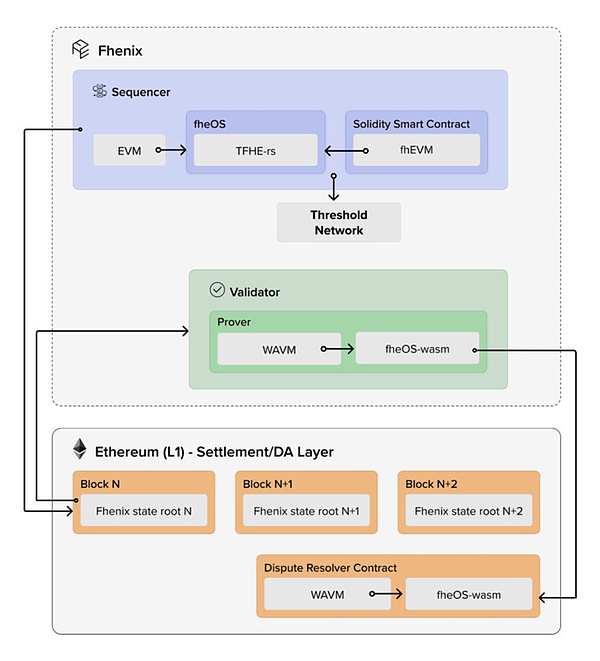
Based on the above-mentioned technology stack, Fhenix released its first public version, Fhenix Frontier.Although this is an early version with many limitations and missing features, it has provided instructions for using smart contract code bases, Solidity APIs, contract development toolchains (such as Hardhat/Remix), front-end interactive JavaScript library, etc.Developers and ecological projects interested in this can refer to the official documents to explore.
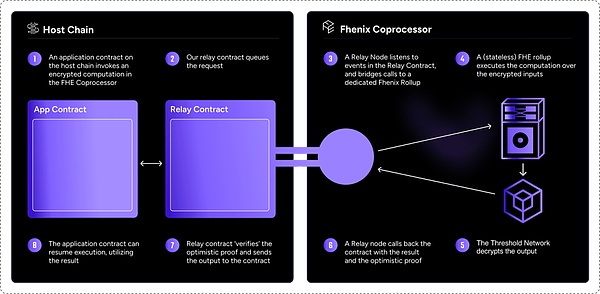
Chain-Agnostic’s FHE Coprocessors
Based on FHE-Rollups, Fhenix cleverly introduced the Relay module, aiming to empower various public chains, L2 and L3 networks, so that they can access FHE Coprocessors to use FHE functions.This means that even if the original Host Chain did not support FHE, it can now indirectly enjoy the powerful functions of FHE.However, since the proof challenge period of FHE-Rollups is usually as long as 7 days, this limits the widespread use of FHE to some extent.In order to overcome this challenge, Fhenix teamed up with EigenLayer to provide FHE Coprocessors’ services with faster and more convenient channels through EigenLayer’s Restaking mechanism, greatly improving the efficiency and flexibility of the entire FHE Coprocessors.
The use process of FHE Coprocessors is simple and clear:
-
Application contract calls FHE Coprocessor on Host Chain to perform encryption calculation operations
-
Relay contract queue request
-
The Relay node listens to the Relay contract and forwards the call to a dedicated Fhenix Rollup
-
FHE Rollup performs FHE calculation operations
-
Threshold network decryption output
-
Relay node returns results and optimistic proofs to the contract
-
Contract validates optimistic proof and sends the result to the caller
-
The application contract will continue to execute the contract according to the call result
Fhenix Participation Guide
If you are a developer, you can delve into Fhenix’s documentary and develop your own FHE-type applications based on these documents to explore their potential in practical applications.
If you are a user, you might as well try to experience the dApps provided by Fhenix’s FHE-Rollups to experience the data security and privacy protection brought by FHE.
If you are a researcher, it is highly recommended that you read Fhenix’s data and documents carefully to gain insight into the principles, technical details and application prospects of FHE in order to make more valuable contributions in your research field.
Best application scenarios for FHE
FHE technology has shown a wide range of application prospects, especially in the fields of full-chain gaming, DeFi and AI. We firmly believe that it has huge development potential and broad application space in these fields:
-
Full-chain game with privacy protection: FHE technology provides strong encryption guarantees for financial transactions and player operations in game economies, effectively preventing real-time manipulation and ensuring the fairness and impartiality of the game.At the same time, FHE can also anonymize players’ activities, significantly reducing the risk of player financial assets and personal information leakage, thereby protecting players’ privacy and security in all aspects.
-
DeFi/MEV: With the vigorous development of DeFi activities, many DeFi operations have become the target of MEV attacks in the dark forest.In order to solve this challenge, FHE can effectively protect sensitive data in DeFi that is unwilling to be leaked, such as the number of positions, clearing lines, trading slippages, etc. while ensuring business logic computing processing.By applying FHE, the health of on-chain DeFi can be significantly improved, thereby significantly reducing the frequency of adverse MEV behavior.
-
AI: Training of AI models depends on data sets. When it comes to training with individual data, ensuring the safety of individually sensitive data becomes the primary prerequisite.To this end, FHE technology has become an ideal solution for AI models to train individual private data, which allows AI to process on encrypted data, so as to complete the training process without revealing any personal sensitive information.
FHE’s Community Recognition
The development of technology cannot be achieved by its hard-core characteristics alone.To achieve technological maturity and continuous progress, we must rely on continuous and perfect academic research and development and active community strength.In this regard, FHE has become the holy grail of the cryptocurrency community, and its potential and value have long been widely recognized.In 2020, Vitalik Buterin highly recognized and supported FHE technology in the article “Exploring Fully Homomorphic Encryption”.Recently, he has spoken out again on social media, undoubtedly strengthening this position again and calling for more resources and strength for the development of FHE technology.Correspondingly, the emerging new projects, non-profit research and education organizations, and the continuous injection of market funds, all seem to indicate that a technological explosion is about to be played.
The potential FHE early ecology
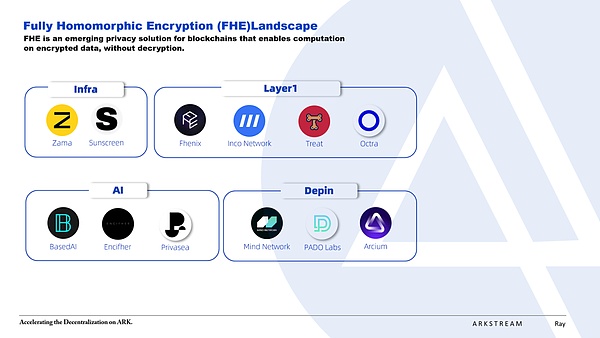
In the early stages of the development of the FHE ecosystem, in addition to the core basic technology service company Zama and the highly anticipated Fhenix, there are also a series of equally excellent projects that deserve our in-depth understanding and attention:
-
Sunscreen: The FHE compiler built through self-developed research and development supports FHE conversion in traditional programming languages, designs corresponding to FHE ciphertext decentralized storage, and finally outputs FHE features for Web3 applications in the form of SDK.
-
Mind Network: FHE network that combines EigenLayer’s Restaking mechanism to extend security for AI and DePIN networks
-
PADO Labs: Launches a decentralized computing network that integrates ZKP and FHE and builds on it
-
**Arcium: **Solana’s privacy protocol Elusiv has recently transformed into a parallel confidential computing network that combines FHE
-
Inco Network: Layer1, which is based on Zama’s fhEVM, focuses on optimizing the computing cost and efficiency of FHE, and then develops a complete ecosystem.
-
Treat: FHE Layer3, which is jointly created by Shiba team and Zama, is committed to extending Shiba ecosystem.
-
octra: FHE network that supports isolated execution environment based on OCaml, AST, ReasonML and C++ development
-
BasedAI: Supports distributed networks that introduce FHE functions to LLM models
-
Encifher: The former is BananaHQ, now renamed Rize Labs, and is doing FHEML around FHE
-
Privasea: The FHE network created by NuLink’s core team adopts Zama’s Concrete ML framework, aiming to achieve data privacy protection in the ML inference process in the AI field.
For non-profit research and educational institutions, we strongly recommend FHE.org and FHE Onchain, which provide valuable resources for academic research and educational popularity throughout the ecosystem.
Due to limited space, we have failed to list all the excellent projects in the FHE ecosystem one by one.But please believe that this ecosystem contains unlimited potential and opportunities, which is worthy of our continuous in-depth exploration and exploration.
Summarize
We are optimistic about the prospects of FHE technology and have high expectations for the Fhenix project.Once the Fhenix main network is released and officially launched, we expect applications in different fields to be improved due to FHE technology.We firmly believe that this future full of innovation and vitality is within reach.
References
https://zama.ai/
https://github.com/microsoft/SEAL
https://www.fhenix.io/
https://mindnetwork.xyz/
https://www.inco.org/
https://x.com/treatsforShib
https://docs.octra.org/
https://x.com/encifherio
https://www.getbased.ai/
https://www.privasea.ai/
https://x.com/fhe_org
https://x.com/FHEOnchain
https://vitalik.eth.limo/general/2020/07/20/homomorphic.html
https://x.com/MessariCrypto/status/1720134959875457352
https://foresightnews.pro/article/detail/59947






