
Source: Gryphsis Academy
The concept of DePIN was formally proposed by Messari in November 2022. In fact, this is not a novel concept. It has some similarities with the previous IoT (Internet of Things). The author believes that DePIN is a kind ofThe new “sharing economy”.
Unlike the previous DePIN craze, the DePIN hotspot projects in this cycle mainly revolve around the three elements of AI (data, algorithms, and computing power), especially“Computing Power”Projects are the most dazzling, such as io.net, Aethir, Heurist, etc., so this article focuses on analyzing related“Computing Power”project.
This article summarizes and extracts the basic framework of the DePIN project, and follows“WHAT-WHY-HOW”The structure of the DePIN track was to make an overview review and summary. Then, based on my own experience, the author clarified a basic idea for analyzing the DePIN project. At the same time, the specific idea was to be based on this idea.“Computing Power”The project was analyzed in detail.
1. What is DePIN
1.1 Definition of DePIN
The full name of DePIN is: Decentralized Physical Infrastructure Networks, which is “Decentralized Physical Infrastructure Network” in Chinese.DePIN is a network that uses blockchain technology to connect physical hardware infrastructure in a decentralized way, allowing users to access without permission and utilize network resources in an affordable way. DePIN projects usually use token reward systems to incentivize.Users actively participate in network construction and follow the principle of “the more contributions, the more profits”.
The application areas of DePIN projects are very wide, covering multiple fields such as data collection, computing and data storage. DePIN is usually present in the fields involved in CePIN.
Thinking about how the DePIN project operates and its economic model, the entire DePIN project is essentially a kind ofThe new “sharing economy”.So when conducting a preliminary analysis of a DePIN project, a concise approach can be taken: first identify what the core business of the project is.
If the project mainly involves computing power or storage services, the DePIN project can be simply defined as a platform that provides ‘shared computing power’ and ‘shared storage’ services.This classification helps to have a clearer understanding of the value proposition of a project and its positioning in the market.
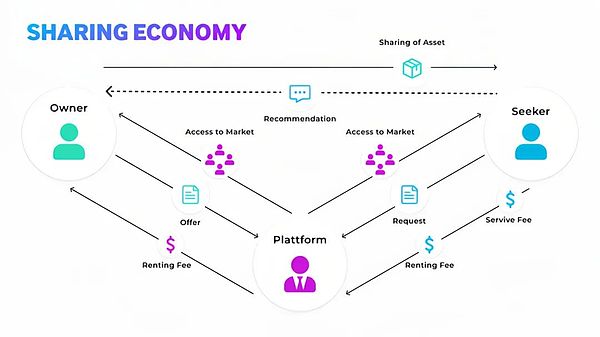
source: @IoTeX
In the above sharing economy model diagram, there are mainly three participants, the demand side, the supply side, and the platform side.In this model, first, the demand side will send demand to the platform, such as taxi, housing, etc.; then, the platform will pass on the demand to the supplier; finally, the supplier will provide corresponding services according to the demand to complete theThe entire business circulation process.
In this model, the flow of funds is first transferred from the demand side to the platform side, and then after the demand side confirms the order, the funds are then transferred from the platform side to the supply side. The platform provides a stable trading platform and a good order delivery experienceTo earn the handling fee and make profits.Thinking back on the process of your Didi, it is a reflection of this model.
In the traditional “sharing economy” model, the platform is usually a large centralized enterprise, and the control of its network, drivers and business is still in the hands of “Didi” itself, and some suppliers in the “sharing economy” modelIt is also a platform party, such as “shared power banks” and “shared electric vehicles”.This will lead to the following problems. Enterprises are prone to monopolisticism, the cost of enterprises doing evil is lower, and the charge of handling fees is too high to infringe on the interests of the supplier.In other words, the pricing power is in centralized enterprises, and those who control means of production do not have pricing power, which is not communism.
However, in the “sharing economy” model of Web3, the platform for matching transactions is a decentralized protocol. It eliminates the middlemen (Didi), making the pricing power in the hands of the “supply side”, which will provide passengers withMore economical rides, providing drivers with higher incomes and enabling drivers to have an impact on the network they help build every day, is a win-win model for all parties.
1.2 The development history of DePIN
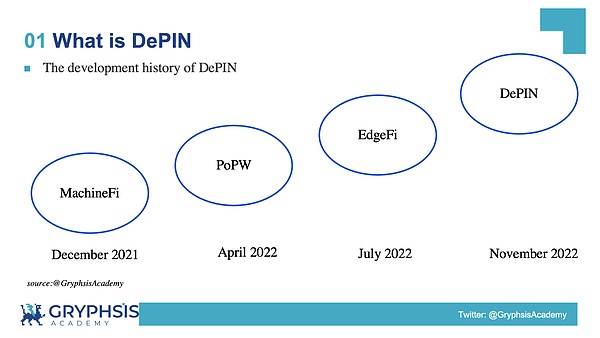
Since the rise of Bitcoin, people have begun to explore combining peer-to-peer networks with physical infrastructure, namely building an open, economically incentivized decentralized network between various devices.Influenced by nouns such as DeFi and GameFi in Web3, MachineFi is one of the earliest concepts proposed.
-
In December 2021, IoTeX was the first enterprise to name this emerging field, calling it “MachineFi.”The name combines “Machine” and “DeFi” to represent the concept of financialization of machines and the data they generate.
-
In April 2022, Multicoin proposed the concept of “Proof of Physical Work” (PoPW), which refers to an incentive structure that enables anyone to contribute to a set of shared goals without permission.Due to the introduction of this mechanism, the development speed of DePIN has been greatly promoted.
-
In September 2022, Borderless Capital proposed the concept of “EdgeFi”.
-
In November 2022, Messari conducted a Twitter vote to unify the abbreviation of the field, with options including PoPW, TIPIN, EdgeFi and DePIN.In the end, DePIN won with 31.6% of the vote, becoming the unified name in this field.
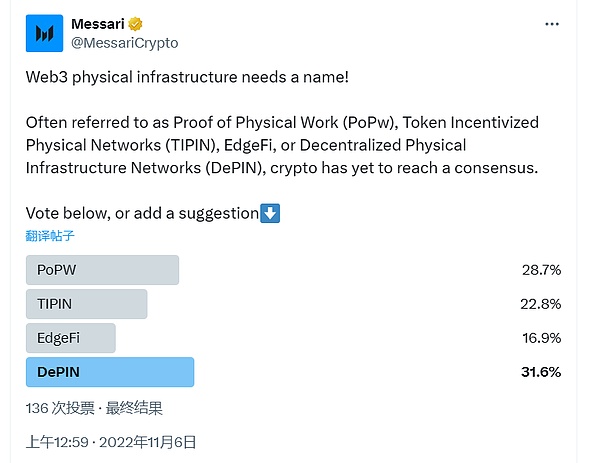
source: @MessariCrypto
2. Why DePIN is needed
In traditional physical infrastructure networks (such as communication networks, cloud services, energy networks, etc.), the market is often dominated by large companies or giant companies due to huge capital investment and operation and maintenance costs.This centralized industrial characteristics bring about the following major difficulties and challenges:
-
Government and enterprise interests are closely tied, and the threshold for new entrants is high:Taking the US communications industry as an example, the Federal Communications Commission (FCC) gives the highest bidder by auctioning wireless spectrum.This makes it easier for companies with strong capital to win and master the absolute advantageous resources of the market, resulting in a significant Matthew effect in the market and the strong become stronger.
-
The market competition pattern is stable, and there is insufficient innovation and vitality:A few licensed companies have market pricing rights. Due to their rich and stable cash returns, these companies often lack the motivation to further develop, resulting in slow network optimization speed, untimely equipment reinvestment and upgrades, and insufficient motivation to innovate and personnel updates.
-
Technical services are outsourcing, and service standards are uneven:Traditional industries are moving towards professional outsourcing, but the service concepts and technical levels of different outsourcing service providers vary greatly, which makes it difficult to control the delivery quality and lacks an effective outsourcing collaboration mechanism.
2.1 Disadvantages of CePIN
-
Centralized control:CePIN is controlled by a centralized organization and has the risk of a single point of failure, is vulnerable to attacks, and has low transparency, and users have no control over data and operations.
-
High entry threshold:New entrants need to overcome high capital investment and complex regulatory thresholds, limiting market competition and innovation.
-
Waste of resources:Due to centralized management, there are idle or waste of resources, and the resource utilization rate is low.
-
Reinvestment of inefficient equipment:Decisions are focused on a few institutions, with equipment renewal and investment inefficiency.
-
The service quality is uneven:The quality of outsourcing services is difficult to guarantee and the service standards are different.
-
Information asymmetry:The central organization has all data and operation records, so users cannot fully understand the operation of the system, which increases the risk of information asymmetry.
-
Inadequate incentive mechanism:CePIN lacks an effective incentive mechanism, and users are not very motivated to participate and contribute network resources.
2.2 Advantages of DePIN
-
Decentralization:No single point of failure enhances the reliability and flexibility of the system, reduces the risk of being attacked, and improves overall security.
-
Transparency:All transactions and operation records are publicly auditable, users have full control over the data, and users can participate in the decision-making process, increasing the transparency and democracy of the system.
-
Incentive mechanism:Through token economics, users can obtain token rewards by contributing network resources, and encourage users to actively participate in and maintain the network.
-
Resistance to censorship:Since there are no centralized control points, the network is more difficult to censor and control, and information flows freely.
-
Efficient resource utilization:The use of distributed networks to activate potential idle resources has improved resource utilization.
-
Open and global deployment:No license required, the agreement is open source and can be deployed globally, breaking the geographical and regulatory restrictions of traditional CePINs.
Through its advantages in decentralization, transparency, user autonomy, incentive mechanisms and censorship resistance, DePIN solves problems such as centralized control, data privacy issues, waste of resources and uneven service quality.It has promoted the transformation of production relations in the physical world and achieved a more efficient and sustainable physical infrastructure network.Therefore, DePIN is a better choice for physical infrastructure networks that require high security, high transparency and high user engagement.
3. How to implement a DePIN network
3.1 Comparison of different consensus mechanisms
Before discussing how to implement a DePIN network, we will first explain the PoPW mechanism commonly used in the DePIN network.
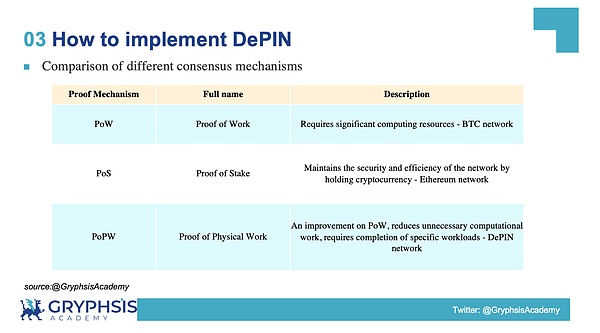
The demand for DePIN network is to be able to quickly expand the network, the cost of node participation in the network is low, the network supply nodes are many, and the degree of network decentralization is high.
PoW has to purchase high-priced mining machines in advance to participate in the operation of the network, which greatly increases the threshold for participating in the DePIN network, so it is not suitable for use as a consensus mechanism for the DePIN network; PoS also needs to pledge related tokens in advance, whichIt will reduce the user’s willingness to participate in the operation of network nodes, and it is also not suitable for use as a consensus mechanism for DePIN network; the emergence of PoPW just meets the characteristic needs of DePIN network. It is the emergence of PoPW mechanism that makes physical devices more convenientAccess to the network has greatly accelerated the development of the DePIN network.
At the same time, the economic model combined with PoPW fundamentally solves the dilemma of having chickens or eggs first.Using Token Rewards, protocols can inspire participants to build the providers of the network to a level that is attractive to users.
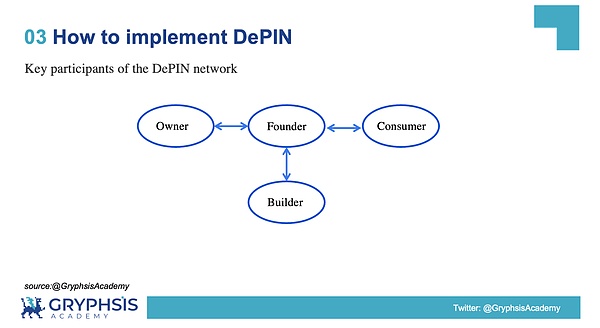
3.2 The main participants of the DePIN network
Generally speaking, a complete DePIN network includes the following parties.
-
Founder:It refers to the initiator of the DePIN network, which is what we usually call the “project party”.Founder was the most important participant in the early stages of the network, and it assumed important responsibilities for network construction and cold start.
-
Owner:Refers to the suppliers of DePIN network resources, such as computing power miners and storage miners.They earn protocol tokens by providing software and hardware resources to the network. In the cold start stage of the network, the supplier plays a very important role.
-
Consumer:Refers to the demanding party of DePIN network resources. Generally speaking, most of the requirements of DePIN projects come from B-end users, and most of them come from Web2. The entire Web3 demand for the DePIN network is relatively small, and relying solely on the needs of Wbe3 users is veryFor example, Filecoin, Bittensor is a typical project of this type that is difficult to support the operation of the entire network.
-
Builder:It refers to people who maintain the DePIN network and expand the ecosystem in the network. Usually, as the network grows, more and more Builders will join in the ecological construction. Of course, in the early stages of network development, Builders are mainly composed of Founders.
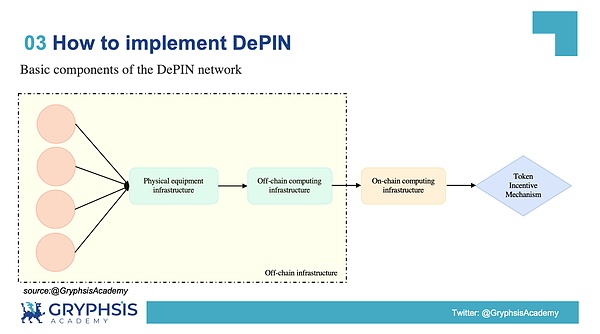
3.3 Basic components of the DePIN network
If a DePIN network wants to run successfully, it needs to interact with on-chain and off-chain data at the same time, which is inseparable from a stable and powerful infrastructure and communication protocols. In general, the DePIN network mainly includes the following parts.
-
Physical Equipment Infrastructure:The physical devices required for the network are usually provided by the Owner, such as GPUs, CPUs, etc.
-
Off-chain computing facilities:The data generated by physical devices needs to be uploaded to the chain through off-chain computing facilities. This is what we call the PoPW proof mechanism, which is usually used to upload the data to the chain.
-
On-chain computing facilities:After the data is verified, the on-chain account address of the device’s Owner needs to be checked and the token reward is sent to the on-chain address.
-
Token incentive mechanism:That is what we usually call the token economic model. The token economic model plays a very important role in the DePIN network and plays different roles in different development periods of the network. It will be explained in detail later.
3.4 Basic operating mode of DePIN network
The operating mode of the DePIN network is similar to the execution order of the above-mentioned architecture diagram. It is basically generated off-chain data and then confirmed on-chain data. Off-chain data follows the “bottom-to-top” rule, and on-chain data follows the “top-to-bottom”rules.
-
Devices provide services to obtain incentives: The hardware devices of the DePIN project receive rewards such as $HNT rewards by providing services such as providing signal overlays in Helium.
-
Present evidence: Before obtaining incentives, the device needs to present evidence to prove that it has put in some work as required.This evidence is called Physical Proof of Work (PoPW).
-
Identity verification using public and private keys: Similar to the public and private key system in traditional public chains, the identity verification process of DePIN devices also requires the use of public and private keys.Private keys are used to generate and sign physical proof of work, while public keys are used by the outside world to verify proofs or as an identity tag (Device ID) of the hardware device.
-
Reward distribution: DePIN project will deploy smart contracts.This contract records the on-chain account addresses of different device holders, realizing the function of directly transferring token rewards received by off-chain physical devices to the on-chain account of the device holder.
Use a simple example to further simplify this process, likening the operating mode of the DePIN network to an exam.
-
Teacher: The issuer of Token needs to verify the authenticity of “student scores”.
-
Student: The token’s acquisition party needs to complete the “Exam Paper” to receive the Token reward.
First, the teacher will send the test paper to the students, and the students need to complete the test according to the requirements of the test paper; then the students hand over the completed test paper to the teacher, and the teacher will mark the paper and give the top students a big red according to the principle of descending order.Flower reward.
Among them, the “issued test paper” is the “demand order” on the DePIN network demand side. The solution to the test questions must follow certain rules (PoPW). If the teacher wants to confirm that the test paper is completed by Student A, he must check the A on the test paper.The teacher will then score the completion status of the test paper. After the score is completed, the teacher will use a red pen to sort the descending order principle, and the descending order principle also meets the token distribution principle of the DePIN project.- “The more contribution, the more profits.”
The basic operating mechanism of the DePIN network is similar to the examination system in our daily lives.In the cryptocurrency space, many projects are actually mapping real-life patterns on the blockchain.In the face of difficult-to-understand projects, we recommend an analogy approach that compares them with familiar situations in daily life to promote understanding and mastery of the project concept.This analogy method helps to reveal the operating logic and principles behind the project.
4. DePIN track classification
We followWHAT-WHY-HOWThe logical order of the DePIN track has been overviewed. Next, let’s sort out the specific tracks of the DePIN section.The disassembly method of sectors is divided intoPhysical Resource Network-Digital Resource NetworkTwo parts.
-
Physical Resource Network: Incentives participants to use or deploy position-based hardware facilities and deliver real-world non-standard goods and services.Specifically, it can be further subdivided into: wireless network, geospatial data network, mobile data network, and energy network.
-
Digital Resource Network: Incentives participants to use or deploy hardware facilities and provide standardized digital resources.Specifically, it can be further subdivided into: storage network, computing power network and bandwidth network.
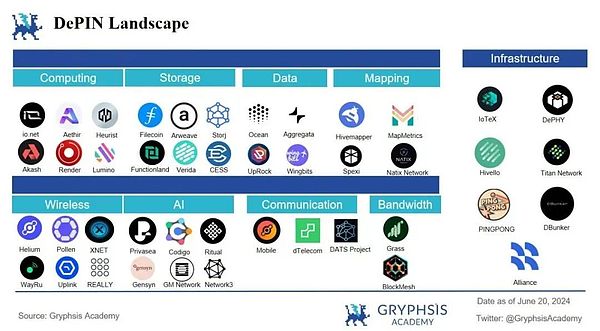
Among them, the representative items of some sections are as follows:
4.1 Decentralized storage network-Filecoin
Filecoin is the world’s largest distributed storage network, with more than 3,800 storage providers worldwide contributing more than 17M TB of storage capacity.Filecoin can be said to be the most well-known DePIN project, and its $FIl coin price peaked on April 1, 2021.Filecoin’s vision is to bring open, publicly verifiable features to the three core pillars that support the data economy, storage, computing, and content distribution.
Filecoin files are stored based on IPFS (InterPlanetary File System), and IPFS can be used to achieve secure and efficient storage of files.
Another unique feature of Filecoin is its economic model. Before becoming a storage node of Filecoin, a certain amount of $FIl tokens will be pledged, which will form “staking tokens->Total storage space increases->MoreMore nodes participate ->More pledged token demand ->Coin price soars” such a flywheel; but it is also easy to experience a spiral decline in the price of the currency in a bear market, and this economic model is more suitable for showing off its skills in a bull market.
4.2 Decentralized GPU rendering platform-Render Network
Render Network is a decentralized GPU rendering network platform under OTOY. It is composed of artists and GPU computing power providers, and can provide users around the world with powerful rendering capabilities available to users.Its $RNDR coin price reached its peak on March 17, 2024. Since Render Network ($RNDR) also belongs to the AI sector, its price peak is at its peak in the AI sector.
The working mode of Render Network is: First, the creator submits work that requires GPU rendering, such as 3D scenes, high-resolution images/videos, etc., and distributes these work to GPU nodes in the network for processing; then, the node owner (Node Operators) contributes idle GPU computing power to Render Network and receives $RNDR token rewards.
Render Network’s pricing mechanism is also unique, using a dynamic pricing model to determine the price of rendering services based on factors such as work complexity, urgency and available resources, providing creators with competitive prices while also compensating fairly.GPU computing power provider.
The recent benefit of Render Network is “Octane on iPad (a professional rendering app) is powered by the Render network.”
4.3 Decentralized data market-Ocean
Ocean Protocol is a decentralized data exchange protocol, mainly for secure sharing between data and commercial application of data. Like common DePIN projects, it also has several major project participants.
-
Data provider: Share data on the protocol
-
Data Consumer: Access to purchase data using OCEAN tokens
-
Node operator: Maintain network infrastructure and receive OCEAN token rewards
For data providers, the security and privacy of data are crucial. Ocean Protoco uses the following mechanisms to realize the flow of data and the security protection of data:
-
Data Security and Control: Ocean Protocol ensures the security and transparency of data transactions through blockchain technology, and data owners have complete control over their data.
-
Data Tokenization: Data tokenization allows data to be bought, sold and exchanged like other cryptocurrencies, which improves the liquidity of the data market.
-
Privacy protection: Compute-to-Data function allows data to be calculated and analyzed without exposing the original data. Data owners can approve AI algorithms to run on their data, while the calculation process is only local to the data owner.Perform in the environment to ensure that the data does not leave its control range.
-
Fine-grained permission control: Ocean Protocol provides fine-grained permission control, and data providers can set detailed access control policies to specify which users or user groups can access specific data parts and under what conditions.This permission control mechanism ensures secure sharing between data while maintaining data privacy.
4.4 An EVM-compatible L1-Lotex
Founded in 2017, IoTeX is an open source, privacy-centric platform that combines blockchain, secure hardware and data service innovations to support the Internet of trustworthy things.
Unlike other DePIN projects, IoTeX is positioned as a development platform designed for DePIN builders, such as Google’s Colab.The most important technology of IoTeX is the off-chain computing protocol W3bStream. The function of W3bStream is to connect IoT devices to the blockchain.Some well-known IoTeX DePIN projects are Envirobloq, Drop Wireless, and HealthBlocks.
4.5 Decentralized hotspot network-Helium
Founded in 2013, Helium is a veteran DePIN project. It is the first to create a large-scale user-contribute new hardware network. Users can purchase Helium hardware hotspots (Hotspots) made by third-party manufacturers to provide accessories for the Internet of Things.The device provides hotspot signals; at the same time, Helium will give hardware hotspot $HNT tokens as a reward for maintaining network stability.In fact, it is just a mining model, but the mining equipment is specified by the project party.
There are two main equipment modes in the DePIN track. One is customized dedicated hardware specified by the project party, such as Helium; the other is to incorporate universal hardware commonly used in life into the networkIn this article, such as Render Network, io.net incorporates the user’s idle GPU into the network.
The most important technology of Helium is its LoRaWAN protocol, a low-power, long-distance wireless communication protocol that is especially suitable for IoT devices. These Helium hardware hotspots provide network wireless coverage through the LoRaWAN protocol.
Although Helium has built the world’s largest LoRaWAN network, demand has not emerged as expected, and now Helium is more focused on launching 5G cellular networks.
On April 20, 2023, Helium has moved to the Solana network and subsequently launched the Helium Mobile project on Solana, which focuses on a 5G unlimited traffic package of $20 per month, due to its affordable price.The project quickly became popular in North America.
From the 5-year global “DePIN” search index, it can be seen that a small peak was ushered in from December 23 to January 24. At this time, it was the top range of the $MOBILE coin price, and the subsequent “DePIN” popularity continuedUp.It can be said that Helium Mobile has ushered in a new era of sailing for the DePIN project.
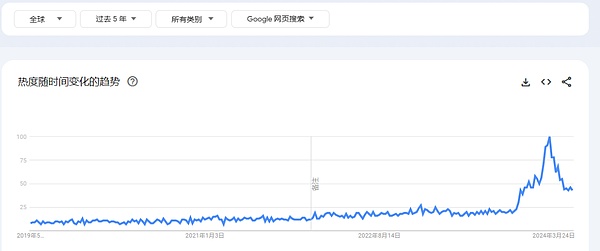
source: @Google Trendes
5. DePIN Economic Model
The economic model of the DePIN project is crucial to the development of the project and has different roles at different stages of the project. For example, at the initial stage of the project, it mainly attracts users to contribute their own hardware and software through token incentive mechanisms.Resources to complete the construction of the project supply side.
5.1 BME model
Before exploring the economic model, we will briefly sort out the BME model, because most of the economic models of DePIN are related to the BME model.
BME (Burn-and-Mint Equivalent, burning coin balance model), is used to manage the supply and demand of tokens. Specifically, it refers to the demand side purchasing goods or services through burning tokens, while the agreement platform rewards supply by minting new tokens.Contributors to the link.
If the newly cast token exceeds the amount of burning, the total supply will increase, resulting in a price drop; conversely, if the burning exceeds the amount of casting, deflation will occur, resulting in price increases.The rising Token prices will attract more supply-side users and form a virtuous cycle.
Supply>Demand=> Price drops
Supply <Demand => Prices rise
We can use Fisher Equation to further elaborate on the BME model.Fisher Equation is an economic model that describes the relationship between money supply, currency circulation speed, price level and transaction quantity, in its specific form:
MV = PT
-
M= Money Supply
-
V = Currency circulation speed
-
P = Price level
-
T = Number of transactions
When the Token circulation velocity V rises, when other conditions remain unchanged, the balance of the equation can only be maintained by reducing the Token circulation (M) through the combustion mechanism.Therefore, as the network usage increases, the amount of combustion will also accelerate.When the inflation rate and the combustion rate can achieve dynamic equilibrium, the BME model can maintain a stable equilibrium state.
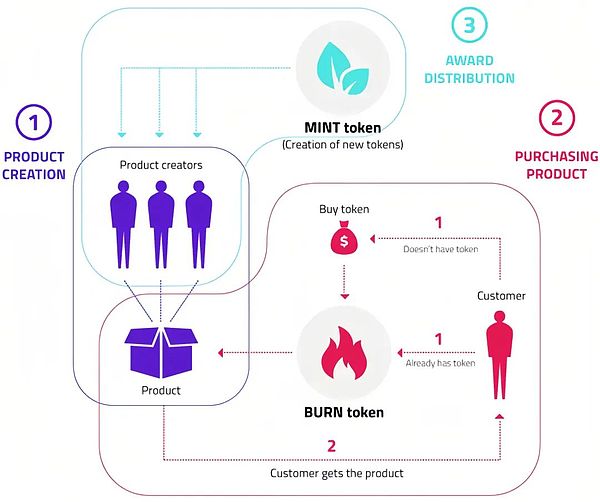
source: @Medium
Taking real-life purchases as specific examples to illustrate this process.First, the manufacturer will make the goods, and then the consumer will buy them.
During the purchase process, you do not hand over the money to the manufacturer, but burn the given amount as a public voucher for you to receive the goods you purchased.At the same time, the agreement platform will mint new currencies every once in a while.In addition, this money is distributed transparently and fairly to various contributors responsible for the supply chain links such as production, distribution, and sales.
5.2 Comparison of advantages and disadvantages of BME model
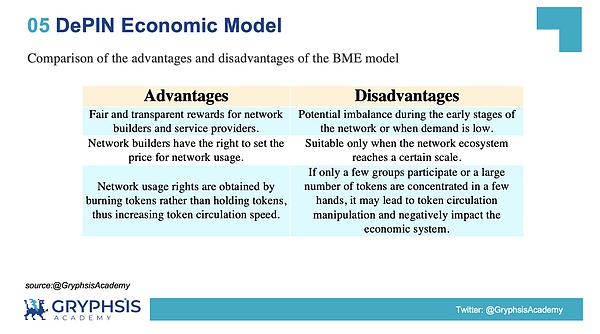
source:@GryphsisAcademy
5.3 Economic model development stage
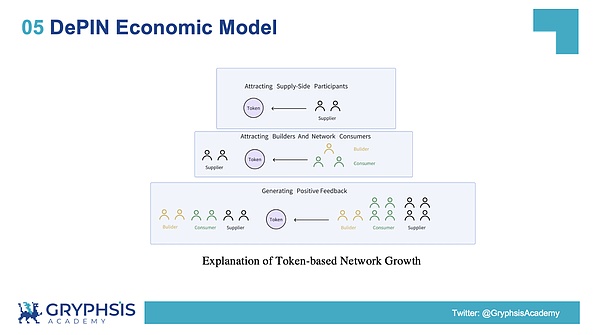
With a simple understanding of the BME model, we can understand the common economic models of the DePIN track more clearly.
Overall, the DePIN economic model is roughly divided into the following three stages:
Phase 1: Cold start-up period and network construction phase
-
This is the initial stage of the DePIN project, focusing on building a physical infrastructure network
-
Through token incentive mechanisms, individuals and enterprises can contribute software and hardware resources (such as computing power, storage space, bandwidth, etc.) to promote network deployment and expansion, and
-
Projects usually rely on core teams to deploy nodes and promotion networks in a more centralized manner until they reach a certain critical scale.
-
Tokens are mainly used to reward contributors to provide hardware resources rather than paying for network usage
Phase 2: The network development phase and the value capture phase
-
Once the network reaches a critical scale, the project will gradually transition to a decentralized community governance model
-
The network has begun to attract end users. In addition to rewarding contributors, tokens can also be used to pay for network usage.
-
Projects capture economic value generated within the network through tokenization and allocate it to contributors and participants
-
Token economic model usually uses the BME model to balance supply and real demand to avoid inflation or deflation.
Stage 3: Maturity and value maximization stage
-
The network has a large number of active users and contributors, forming a virtuous cycle
-
The token economic model focuses more on long-term value creation and improves the value of tokens through carefully designed deflation mechanisms.
-
Projects may introduce new token models to optimize token supply and promote positive externalities in bilateral markets
-
Community autonomy becomes the dominant model of network governance
A good economic model will have an economic flywheel effect on the DePIN project.Because the DePIN project adopts a token incentive mechanism, it will bring a lot of supply-side attention during the cold start period of the project, so it can achieve rapid scale expansion with the help of the flywheel effect.
The token incentive mechanism is the key to the rapid growth of DePIN projects.The project first needs to formulate appropriate reward standards for the scalability development of physical infrastructure based on the type of physical infrastructure.For example, to expand the coverage area of the network, Helium rewards higher in areas with lower network coverage density than in areas with higher density.
As shown in the figure below, investors will invest real money into the project in the early stages of the project, so that the token will have initial economic value. In order to obtain the token reward, the supply side will actively participate in the project construction, and as the network begins to developThe scale and its low price compared to CePIN, more and more demanding ends have begun to adopt the services of DePIN projects, which brings revenue to the entire network protocol and forms a good path from the supply end to the demand end.
As demand on the demand side rises, the price of tokens rises through destruction or repurchase (BME model), which provides additional incentives for the supply side to continue to expand the network, because it means that the value of tokens they receive will also beIncreased with it.
As the network continues to expand, investors’ interest in the project gradually increases and they are beginning to provide more financial support for it.
If the project is open source, or the contributor/user data is open to the public, developers can build dApps based on this data to create additional value within the ecosystem, thereby attracting more users and contributors.
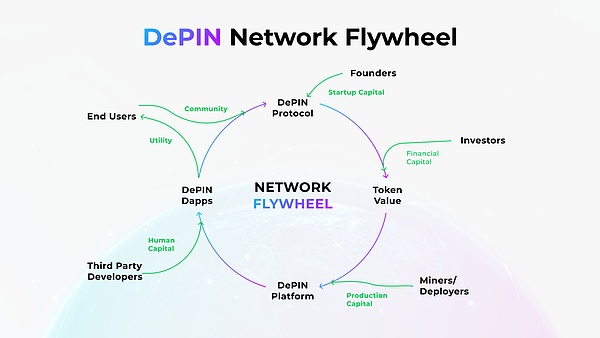
source: @IoTeX
6. Current status of the DePIN track
The current popularity of DePIN projects is mainly concentrated inSolanaNetwork and “DePIN x AI“This track, as can be seen from the Google Index, in network infrastructure, DePIN and Solana have the strongest correlation, and the areas of high attention are mainly concentrated in Asia, including China, India, etc., which also shows the main participation in the DePIN project.The user is still from Asia.
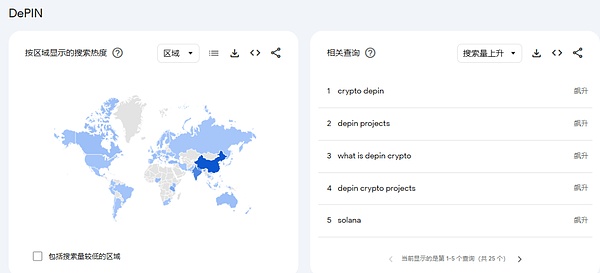
source: @Google Trendes
The total market value of the entire DePIN track is “$32B”, compared with traditional CePIN projects, such as China Mobile’s market value is “$210B”, AT&T (the largest operator in the United States) market value is “$130B”, there is still a lot of room for growth when analyzing the entire DePIN track from the perspective of market value only.
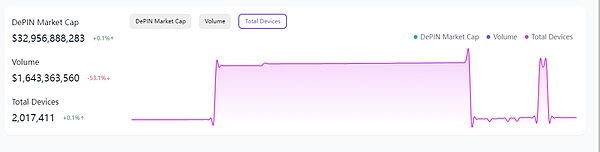
source: @DePINscan
At the same time, it can be seen from the change curve of the total number of equipment in the DePIN track that the turning point occurred in December 2023, and this time period is also the time when Helium Mobile is the most popular and the highest coin price. It can be said that the DePIN craze in 2024 was made by HeliumMobile is open.
As shown in the figure below, the global distribution map is shown. From the figure, it can be seen that DePIN equipment is mainly distributed in North America, East Asia, Western Europe and other regions.These regions are relatively economically developed because if users want to become nodes in the DePIN network, they need to provide software and hardware equipment, and these devices need to be purchased for money. For high-end consumer GPUs, a RTX-4090 pieceThe price is $2,000, which is a considerable fee for users in economically underdeveloped areas.
Since the token reward mechanism of the DePIN project follows the principle of “the more contributions, the more profits”, if users want to get more token rewards, they need to contribute more resources and higher-end equipment. For the project party, thisOf course it is a good thing, but for users, this undoubtedly raises the threshold for participation.A good DePIN project is backward compatible and is inclusive. The threshold for participation will not be particularly high. It will give low-end devices an opportunity to participate, which is in line with the spirit of blockchain “fairness, justice and transparency”..
Judging from the global equipment distribution map, there are still many areas that have not been developed. We believe that through continuous technological innovation and market expansion, the DePIN track is expected to achieve global growth, touching every corner, and connecting people around the world, jointly promote technological progress and social development.
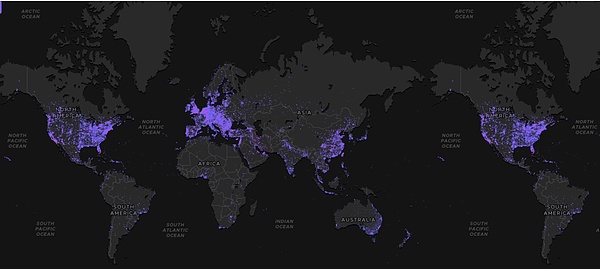
source: @DePINscan
7. Basic steps for DePIN project analysis
After my brief review of the DePIN track, the author summarized the basic steps of analyzing a DePIN project.
Most importantly, the operational model of the DePIN project is analyzed as the sharing economy in Web2.

8. io.net
8.1 Project basic information
Project Introduction
io.net is a decentralized computing network that supports the development, execution and scaling of machine learning applications on the Solana blockchain.Their vision is to “group a million GPUs together to form the largest cluster of GPUs in the world.” Enable engineers to gain a lot of computing power in accessible, customizable, cost-effective, and easy to implement systems.
Team background
-
Founder and CEO: Ahmed Shaidid, who worked in quantitative finance and financial engineering before founding io.net and was also a volunteer at the Ethereum Foundation.
-
Chief Marketing Officer and Chief Strategy Officer: Garrison Yang, Yang Xudong.Prior to that, he was Vice President of Strategy and Growth at Avalanche and an alumnus of the University of California, Santa Barbara.
It can be seen that the technical background of the project is relatively solid, and many founders have Crypto experience.
Narrative:AI, DePIN, Solana Ecology.
Financing situation

source: @RootDataLabs
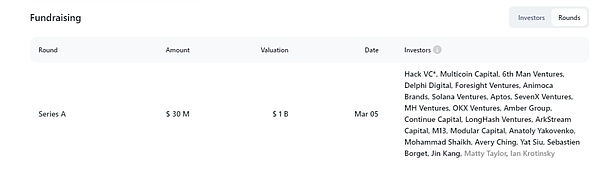
source: @RootDataLabs
io.net received a US$30 million Series A financing on March 5, 2024, with a valuation of US$1 billion. The benchmark is Render Network. In addition to well-known top investment institutions such as Hack VC, OKX Ventures, and Multicoin Capital, the participating investors are not only in the world.There are also the heads of projects such as Anatoly Yakovenko (Solana CEO), Yat Siu (Animoca co-founder), etc. It can be said that io.net has been favored and supported by top capital since its birth. This is why we call io.netThe reasons for celebrity projects – have funds, background, technology, and airdrop expectations.
8.2 Product Architecture
io.net’s products are mainly divided into the following major parts:
-
IO Cloud: Deploy and manage on-demand GPU clusters, which are computing power equipment management interfaces for demand-side users.
-
IO Worker: Provides a comprehensive and user-friendly interface that effectively manages users’ GPU node operations through intuitive web applications, which is a computing power device management interface for supply-side users.
-
IO Explorer: provides users with a window to understand the internal functioning of the network, providing comprehensive statistics and a bird’s-eye view of all aspects of the GPU cloud.Just like Solscan or blockchain browsers provide visibility for blockchain transactions.
-
BC8.AI: is an advanced AI-driven image generator that uses deep neural networks to create highly detailed and accurate images based on text descriptions or seed images.This is an AI application on io.net. You can easily use the AI biographic application by simply using the user IO ID of io.net.
As shown below is a Van Gogh-style cat image generated on BC8.AI.
source: @ionet
Product features and advantages
Compared with traditional cloud service providers Google Cloud and AWS, io.net has the following features and advantages:
-
There are many GPUs and high computing power;
-
Cheap and cost-effective;
-
Response to review – Quickly use cutting-edge GPUs like the A100 H100 without auditing;
-
Antitrust;
-
High degree of user customization.
Let’s compare in detail using AWS as an example:
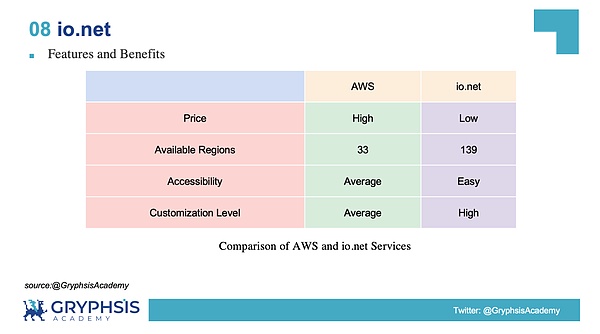
Accessibility refers to the convenience of users accessing computing power. When accessing traditional cloud service providers, you need to present your bank card, contact information and other key identity information in advance. When accessing io.net, you only need toA Solana wallet can quickly and conveniently obtain network computing power licenses.
The degree of customization refers to the degree of customization of the computing power cluster by users. When visiting traditional cloud service providers, you can only choose the machine model of the computing power cluster and the area where the machine is located. When visiting io.net, in addition to choosing the aboveIn addition to the options, you can also choose bandwidth speed, cluster type, data encryption method, billing method, etc.
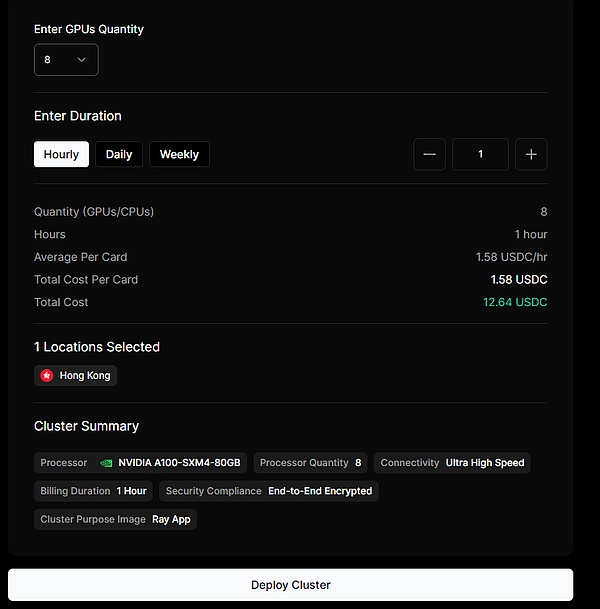
source: @ionet
As shown in the figure above, when the user selects the NVIDIA A100-SXM4-80GB model GPU, Hong Kong server, ultra-high speed bandwidth speed, hourly billing method, end-to-end encryption and encryption method, the price of its single GPU is$1.58Every hour, it can be seen from here that the user customization level of io.net is very high, and there are many options for users to choose from, putting the user’s experience first, and this is also an expansion for the DePIN project.The way to promote the healthy development of the network on the demand side.
The following figure shows the price of the NVIDIA A100-SXM4-80GB model GPU of traditional cloud service providers. With the same computing power required, the price of io.net is at least higher than that of traditional cloud service providers.Half cheaper, this is very attractive to users.
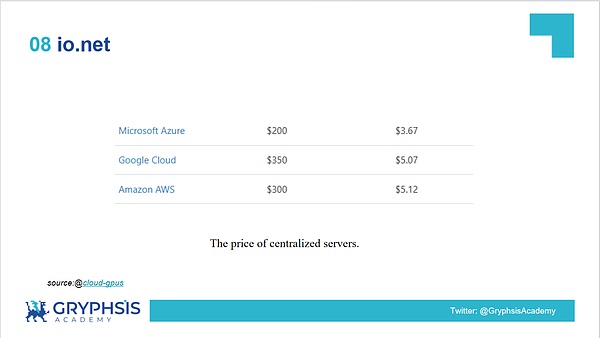
8.3 Overall network situation
We can use IO Explorer to comprehensively view the computing power situation of the entire network, including the number of devices, available service areas, computing power prices, etc.
Computing equipment status
Currently, io.net has a total of 101,545 verified GPUs and 31,154 verified CPUs.io.net will verify whether the computing power device is online every 6 hours to ensure the stability of io.net’s network.
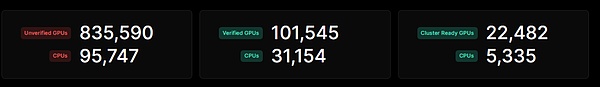
source: @ionet
The second picture shows the current available computing power devices that have been proven by PoS and are easily deployed. Compared with Render Network and Filecoin, the number is one order of magnitude. From here, we can see that the number of computing power devices of io.net isThere are many, and io.net also integrates Render Network and Filecoin computing power devices. Users can choose computing power device providers when deploying computing power clusters, and always meet users’ customized needs with user experience.
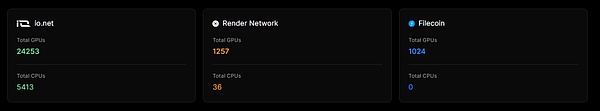
source: @ionet
Another feature of io.net’s computing power equipment is that it has a large number of high-end computing power equipment. Take the United States as an example. High-end GPUs such as H100 and A100 have hundreds of yuan. In the case of US sanctions and AI explosion, high-end graphics cards have become very precious computing power assets.
In io.net, whether you are a US citizen or not, you can use the high-end computing power equipment provided by these supply side without auditing, which is why we say io.net has the advantages of antitrust.
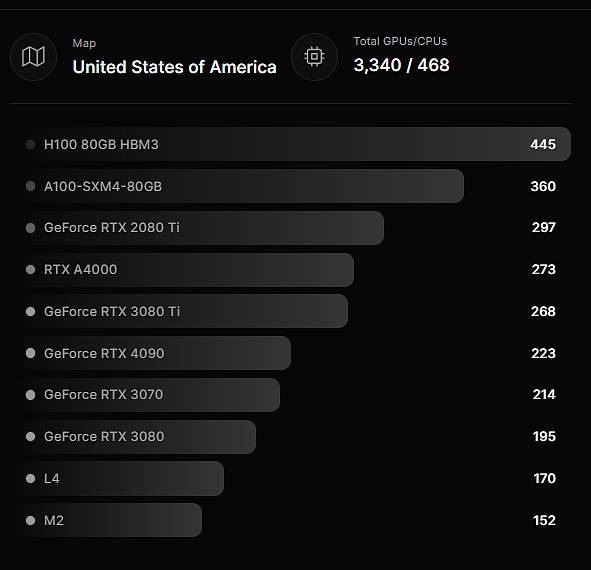
source:@ionet
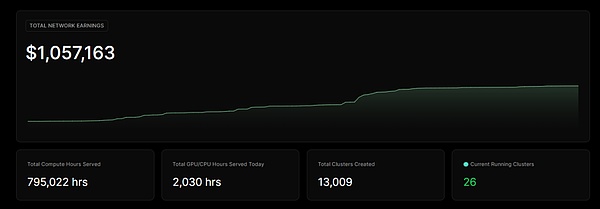
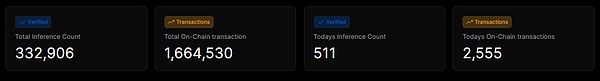
Business revenue status
From the revenue board of io.net, it can be seen that io.net has stable returns every day, and the total returns have reached the level of one million US dollars. From this, it can be seen that io.net has completed the supply side construction and the entire projectIt has gradually passed the cold start period and has begun to move towards the development period of the Internet.
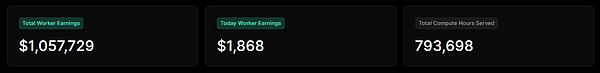
source: @ionet
source: @ionet
source: @ionet
From the supply side of io.net
-
The validity of network nodes has been verified
-
Computing power equipment is stable online and sufficient
-
Having a certain number of high-end computing power equipment can fill some market demand
But from the demand side
-
There are still many devices in idle state
-
Most computing power tasks require from BC8.AI
-
The demands on the enterprise and personal ends have not been stimulated yet
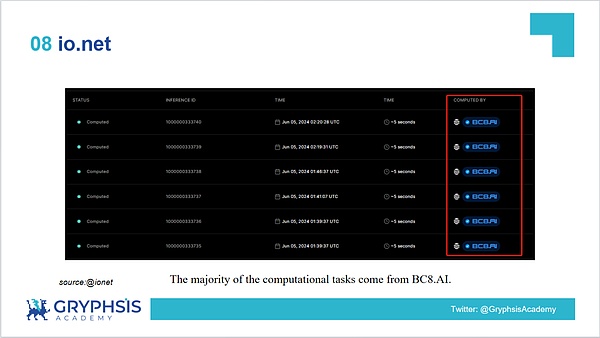
8.4 Economic Model
The network native tokens of io.net are $IO, with a fixed total of 800 million and an initial supply of 500 million. The remaining 300 million points will be issued as rewards every hour and paid to suppliers and token stakers.
$IO adopts a deflation mechanism: The revenue generated by the network is used to purchase and destroy $IO, and the amount of token burning is adjusted according to the price of $IO.
Token empowerment
-
Payment means: A 2% handling fee is required to pay USDC payments to users and suppliers, and there is no charge for payments to $IO.
-
Staking: A minimum of 100 $IO tokens can be pledged to enable nodes to obtain $IO free rewards from the network.
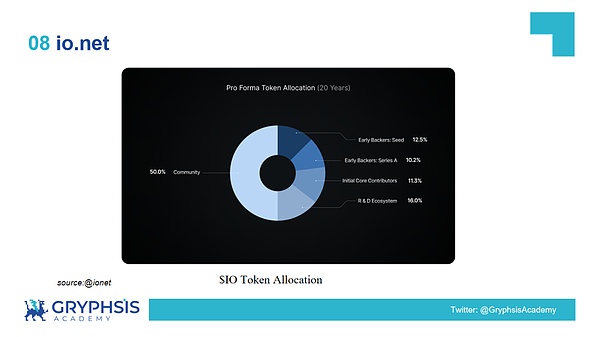
Token allocation ratio
As can be seen from the allocation scale chart, the project community members account for half of the tokens, which shows that the project hopes to promote the development of the project by incentivizing the community members.The R&D ecosystem accounts for 16%, ensuring that the project’s technology and product development can be continuously supported.
It can be seen from the token release chart that the $IO token is released step by step linearly. This release mechanism helps stabilize the price of the $IO token and avoids the sudden appearance of a large number of $IO tokens in the market causing price fluctuations.At the same time, the reward mechanism of $IO tokens can also incentivize long-term holders and stakeholders, enhancing project stability and user stickiness.
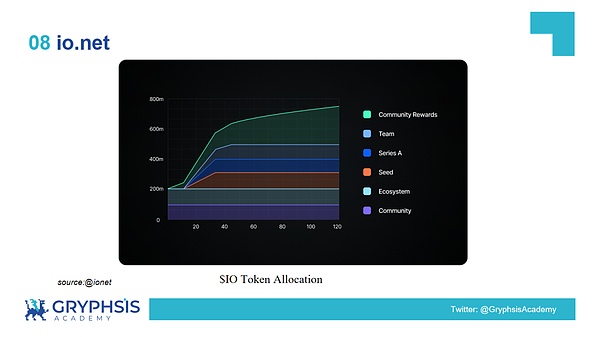
Overall, io.net token economics is a well-designed token solution.It can be seen from the token allocation ratio that allocating half of the tokens to the community shows the project’s emphasis on community-driven and decentralized governance, which will help the long-term development of the project and the establishment of credibility.
In the third stage of the three stages of the DePIN economic development, “community autonomy becomes the dominant model of network governance” has been elaborated, and io.net has created a good foundation for future community autonomy.At the same time, the gradual release mechanism and destruction mechanism of $IO tokens have also effectively dispersed market selling pressure and reduced the risk of price fluctuations.
From this we can see that the various mechanisms of io.net illustrate that it is a planned long-term development project.
8.5 Project Participation Methods
Currently, the “ignition reward” of io.net has arrived in season 3, with a duration of June 1 to June 30. The main way to participate is to incorporate your computing power equipment into the computing power main network to participate in mining..The mining reward of $IO tokens is related to various factors such as the computing power of the device, network bandwidth and speed.
In the “Ignition Reward” in Season 1, the starting threshold for user equipment to connect to the grid is “GeForce RTX 1080 Ti”, which also reflects what we said in the previous article – giving low-end devices an opportunity to participate, which is in line with the blockThe spirit of chain “fairness, justice and transparency”.Then, the starting threshold for Season 2 and Season 3 “Ignition Rewards” is “GeForce RTX 3050”.
The reason for this is that from the perspective of the project, when the project develops to a certain stage, low-end computing power equipment contributes less to the overall network, and better and stronger computing power equipment can better maintain network stability;For end users, most users need high-end computing power equipment more. They need high-end computing power equipment to train and infer AI models, while low-end computing power equipment cannot meet their needs.
Therefore, with the good development of the project, raising the threshold for participation is the right route. Just like the Bitcoin network, better, stronger and more computing power equipment is the goal pursued by the project party.
8..6 Project Summary and Prospect
io.net has performed well in the cold start period of the project and the network construction stage. It has completed the construction of the entire network and verified the effectiveness of computing power nodes and generated continuous revenue.
The main goal of the project’s next step is to further expand the network ecosystem and improve the incremental growth of the network demand side. The computing power demand market is a large market. How to promote the project in the market requires the efforts of the marketing team of the project party.
In fact, what we usually call AI algorithm model development mainly includes two parts, one is training (train) and the other is inference (Inference).We use a simple example to illustrate these two concepts, and there is a quadratic equation:
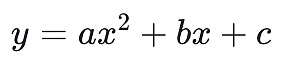
The process of solving unknown coefficients (a, b, c) using (x, y) data pairs (training sets) is the training (Train) process of AI algorithms; after obtaining unknown coefficients (a, b, c), according toThe process of solving y given by x is the inference process of AI algorithms.
From this calculation process, we can clearly see that the calculation amount of the training process is much greater than the inference process. Training an LLM (Large Language Model) requires a large number of computing power clusters.Support, while also requiring a lot of money.Take the GPT-3 175B as an example, thousands of Nvidia V100 GPUs were used for training, which took about a few months and had a training cost of tens of millions of dollars.
It is difficult to do AI big model training on a decentralized computing platform, because the model training involves transfer and transfer between large-scale data. This process has a very high demand for network bandwidth, and the decentralized computing platformIt is difficult to meet this need.The reason why NVIDIA is the king of the AI industry is that in addition to its high-end computing chips and underlying AI computing acceleration library (cuDNN), it also has its unique communication bridge “NVLink”. “NVLink” greatly accelerates the model training process.flows between large-scale data.
In the AI industry, training of large models not only requires a large amount of computing resources, but also involves the collection, processing and conversion of data.These processes often require large-scale infrastructure and centralized data processing capabilities.Because of this, we can see that the AI industry is essentially a large-scale and centralized industry that relies on strong technology platforms and data processing capabilities to promote innovation and development.
Therefore, decentralized computing platforms such as io.net are most suitable for AI algorithm inference. Their potential customer objects should be students and those task requirements for fine-tuning downstream tasks based on big models, because it is cheap and accessibleSimple and sufficient computing power.
9. Aethir
9.1 Project Background
Artificial intelligence is regarded as the most important technology humans have ever seen, and with the advent of general artificial intelligence (AGI), lifestyles will undergo earth-shaking changes.However, the AI wealth gap between GPU rich and GPU poor is led by a few companies leading AI technology development.Through its distributed physical infrastructure network (DePINs), Aethir aims to increase the availability of on-demand computing resources, thereby balancing the distribution of outcomes of AI development.
Aethir is an innovative distributed cloud computing infrastructure network designed specifically to meet the high demand for on-demand cloud computing resources in the fields of artificial intelligence (AI), gaming and virtual computing.Its core philosophy is to form a single global network by aggregating enterprise-class GPU chips from all over the world, thereby significantly increasing the supply of on-demand cloud computing resources.
Aethir’s main goal is to solve the current shortage of computing resources facing the AI and cloud computing sectors.With the development of artificial intelligence and the popularization of cloud games, the demand for high-performance computing resources is increasing.However, small and medium-sized enterprises and startups often have difficulty obtaining sufficient computing power, as a few large companies monopolize most of GPU resources.Through its distributed network, Aethir provides a viable solution that can help resource owners (such as data centers, tech companies, telecom companies, top game studios and cryptocurrency mining companies) to make the most of their underutilization.GPU resources can also provide end users with efficient and low-cost computing resources.
Advantages of distributed cloud computing
-
Enterprise-level computing resources:Aethir aggregates high-quality GPU resources, such as NVIDIA’s H100 chips, from a variety of enterprises and data centers, ensuring high quality and reliability of computing resources.
-
Low latency:Aethir’s network design can support low-latency real-time rendering and AI inference applications, which is difficult to achieve in current centralized cloud computing infrastructure.Especially in the world of cloud gaming, low latency is crucial to providing a seamless gaming experience.
-
Quickly expand:Thanks to the distributed model, Aethir is able to scale its network faster to meet the rapidly growing market demand for AI and cloud gaming.Compared with traditional centralized models, distributed networks can increase the supply of computing resources more flexibly.
-
Excellent unit economy:Aethir’s distributed network reduces the high operating costs of traditional cloud computing providers and is able to provide computing resources at a lower price.This is especially important for small and medium-sized businesses and startups.
-
Decentralized ownership:Aethir ensures that resource owners always retain control over their resources, and resource providers can flexibly adjust their resource utilization according to their needs while obtaining corresponding benefits.
Through these core strengths, Aethir is not only technologically leading, but also economically and socially.It makes the supply of computing resources more fair through distributed physical infrastructure networks (DePINs), and promotes the popularization and innovation of AI technology.This innovative model not only changes the way computing resources are supplied, but also provides new possibilities for the future development of AI and cloud computing.
9.2 Technical Architecture
Aethir’s technical architecture consists of multiple core roles and components to ensure that its distributed cloud computing network can operate efficiently and securely.Here is a detailed description of each key role and component:
Core roles and components
Node Operators:
-
Node operators provide actual computing resources, and they connect their own GPU resources to the Aethir network for use.
-
Node operators need to register their computing resources first and then undergo specification evaluation and confirmation of the Aethir network before they can start providing services.
Aethir Network
Containers
-
Containers are the place to perform computing tasks, ensuring an instantly responsive cloud computing experience.
-
Selection: AI customers select containers based on performance needs, and gaming customers select containers based on service quality and cost.
-
Staking: New node operators need to pledge $ATH tokens before providing resources.If quality control standards are violated or network services are interrupted, the tokens pledged will be cut.
-
Reward: The container receives rewards in two ways: one is the reward for maintaining a high readiness state (PoC), and the other is the service reward for actually using computing resources (PoD and service fees).
Checkers
-
The inspector’s main responsibility is to ensure the integrity and performance of containers in the network, performing critical testing in registration, standby and rendering states.
-
Inspection method: including direct reading of container performance data and simulation tests.
Indexers
-
The indexer matches it to the right container according to user needs, ensuring fast and high-quality service delivery.
-
Select: Randomly select the indexer to maintain decentralization and reduce signal latency.
-
Matching criteria: Select containers based on service costs, experience quality and network evaluation index.
End Users:
The end user is a consumer of Aethir network computing resources, whether it is used for AI training and reasoning, or gaming.The end user submits a request, and the network matches appropriate high-performance resources to meet the needs.
Treasury:
The treasury holds all pledged $ATH tokens and pays all $ATH rewards and fees.
Settlement layer:
Aethir uses blockchain technology as its settlement layer to record transactions, support scalability and efficiency, and uses $ATH for incentives.Blockchain ensures transparency in resource consumption tracking and enables near-real-time payments.
For specific relationships, please refer to the following chart:
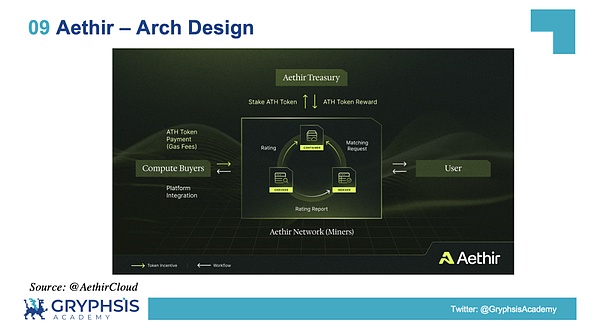
Source: @AethirCloud
9.3 Consensus mechanism
The Aethir network operates with unique mechanisms at its core are two main proofs of work:
Rendering capacity proof
(Proof of Rendering Capacity):
-
A random set of nodes is selected every 15 minutes to verify the transaction.
-
The probability of selecting a node is based on the number of tokens it invests, the quality of service, and the frequency of previous selection.The more investment, the better the quality, and the fewer times you have been selected before, the greater the possibility that the node will be selected.
Proof of Rendering Work:
-
The performance of the node will be closely monitored to ensure high-quality service.
-
The network will adjust resource allocation according to user needs and geographical location to ensure the best service quality.
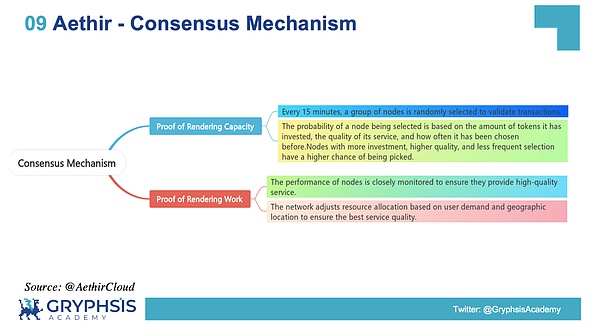
Source: @AethirCloud
9.4 Token Economics Model
ATH tokens play a variety of roles in the Aethir ecosystem, including transaction medium, governance tools, incentives and platform development support.Specific uses include:
-
Trading tools:ATH is a standard trading medium within the Aethir platform, used to purchase computing power, covering business models such as AI applications, cloud computing and virtualized computing.
-
Diversified applications:ATH is not only used for current business, but also plans to continue to play a role in the future merger mining and integration markets as the ecosystem grows.
-
Governance and participation: ATH token holders can participate in Aethir’s decentralized autonomous organization (DAO) to influence platform decision-making through proposals, discussions and voting.
-
Pledge: New node operators need to pledge ATH tokens to ensure that they are consistent with the platform’s goals and act as a precaution against potential misconduct.
Specific allocation strategy: The token of the Aethir project is $ATH, and the total issuance is 42 billion.The largest share is given to GPU providers, such as data centers and individual retail investors. 17.5% of tokens are given to teams and consultants, and the node inspection and sales teams are given to 15% and 11.75% of tokens respectively..As shown in the figure below:
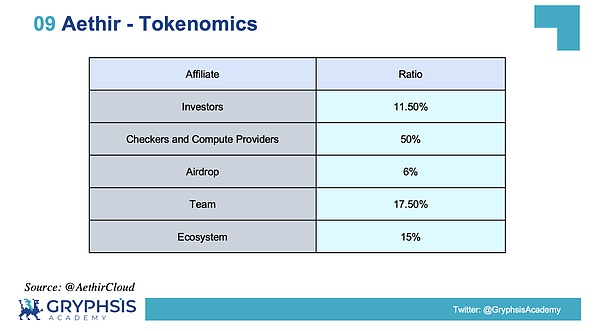
Source: @AethirCloud
Reward emissions
The emission strategies of mining rewards are designed to balance the participation of resource providers and the sustainability of long-term rewards.Through the decay function of the early reward, ensure that the participants who join later are still motivated.
9.5 How to participate in Aethir mining
The Aethir platform chooses to use most of the Total Token Supply (TTS) for mining rewards, an allocation that is crucial to strengthening the ecosystem.The purpose of this allocation method is to support node operators and adhere to container standards.Node operators are the core of Aethir, providing the necessary computing power, while containers are key to providing computing resources.
Mining rewards are divided into two forms: rendering proof of work and capacity proof.Rendering proof of work encourages node operators to complete computing tasks and distribute them specifically to containers.Proof of capacity is to motivate computing providers to prepare for services. Proof of capacity is to provide GPUs to Aethir to get rewards; Proof of work is to use your GPUs and there will be additional token rewards when a customer uses your GPUs.Rewards will be issued in $ATH tokens.These rewards are not only distributions, but also investments in the future sustainability of the Aethir community.
10. Heurist
10.1 Project Background
Heurist is a Layer 2 network based on ZK Stack, focusing on AI model hosting and inference.Its positioning is similar to the Web3 version of HuggingFace, providing users with serverless open source AI model access.These models are hosted on a decentralized network of computing resources.
Heurist’s vision is to use blockchain technology to decentralize AI, thereby achieving popularization and fair innovation in technology.Its goal is to ensure accessibility and unbiased innovation of AI technology through blockchain technology and promote the convergence and development of AI and cryptocurrencies.
The term Heurist comes from heuristics, and refers to the process by which the human brain quickly reaches reasonable conclusions or solutions when solving complex problems.The name embodies Heurist’s vision to quickly and efficiently solve AI model hosting and inference problems through decentralized technologies.
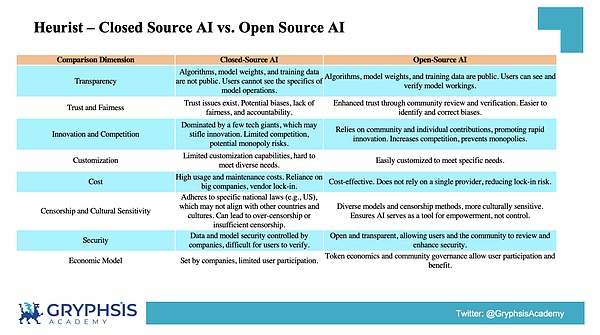
Problems with closed source AI
Closed source AI is often reviewed in accordance with U.S. law, but this may not be consistent with the needs of other countries and cultures, resulting in over-censorship or under-sufficiency.This not only affects the performance of the AI model, but may also infringe on the user’s right to express himself freely.
The Rise of Open Source AI
Open source AI models outperform closed source models in many fields, such as the Stable Diffusion Model (Stable Diffusion) outperforms OpenAI’s DALL-E 2 in image generation and is cheaper.The weights of the open source model are public, allowing developers and artists to fine-tune according to specific needs.
Community-driven innovation of open source AI is also a highlight. Open source AI projects benefit from the collective contribution and review of diverse communities, promoting rapid innovation and improvement.Open source AI models provide unprecedented transparency, and users can review training data and model weights, thereby enhancing trust and security.
A detailed comparison between open source AI and closed source AI is shown in the figure below:
Source: @heurist_ai
10.2 Data Privacy
When dealing with AI model inference, the Heurist project integrates Lit Protocol to implement the encryption of data during transmission, including the input and output of AI inference.For miners, Heurist has two major categories, divided into public miners and privacy miners:
-
Public miners:Anyone with a GPU that meets the minimum requirements can become a public miner, and the data processed by such miners is not encrypted.
-
Privacy Miner:Trusted node operators can become privacy miners, processing sensitive information such as confidential files, health records and user identity data.Such miners need to comply with the off-chain privacy policy.The data is encrypted during transmission, and the router and sorter of the Heurist protocol cannot decrypt this data. Only miners that match the user access control condition (ACC) can decrypt the data.
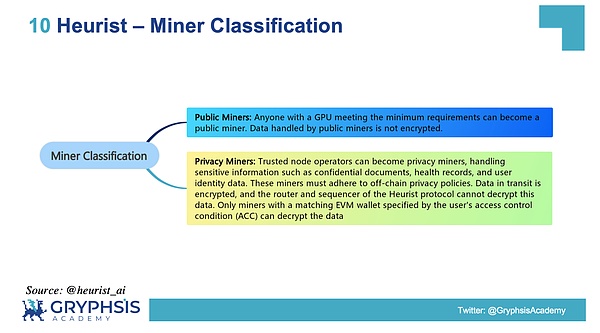
Source: @heurist_ai
How to build trust in Privacy – enabled miners?The following two methods are mainly used
-
Off-chain consensus: Off-chain consensus established through real-life laws or agreements, which is technically easy to achieve.
-
Trusted Execution Environment (TEE): Utilize TEE to ensure the security and confidentiality of sensitive data.While there are currently no mature TEE solutions for large AI models, the latest chips from companies such as Nvidia show potential in supporting TEE to handle AI workloads.
10.3 Token Economics Model
The token of the Heurist project is called HUE. As a practical token, its supply is dynamic and regulated through issuance and destruction mechanisms.The maximum supply of HUE tokens is limited to 1 billion.
Token allocation and issuance mechanisms can be roughly divided into two types, namely mining and staking:
-
Mining:Users can mine HUE tokens by hosting AI models on their GPUs.Mining nodes need to pledge at least 10,000 HUE or esHUE tokens to be activated, and no reward will be obtained below this threshold.The reward for mining is esHUE tokens, which will be automatically compounded to the stake of the miner node.The reward rate depends on GPU efficiency, availability (uptime), type of AI model running, and the total amount of pledged in the node.
-
Pledge:Users can pledge HUE or esHUE tokens in miner nodes.The staking income is issued in the form of HUE or esHUE, and the yield of staking esHUE tokens is higher than that of HUE tokens.Unstaking HUE tokens requires a 30-day lock-up period, while unstaking esHUE does not have a lock-up period.The esHUE reward can be converted to HUE tokens through a one-year linear release period.Users can instantly transfer their pledged HUE or esHUE from one miner node to another, thereby promoting flexibility and competition among miners.
Token destruction mechanism
Similar to Ethereum’s EIP-1559 model, the Heurist project implements a token destruction mechanism.When a user pays for AI reasoning fees, some HUE payments are permanently removed from circulation.The balance of issuance and destruction of tokens is closely related to network activities. During periods of high usage, the token destruction rate may exceed the issuance rate of new tokens, thus bringing the Heurist network into a deflation phase.This mechanism helps regulate the supply of tokens and aligns the value of tokens with actual needs within the network.
Bribery mechanism for tokens (Bribes)
The bribery mechanism was first proposed by Curve Finance users as a gamified incentive mechanism to help guide the rewards of liquidity pools.The Heurist project borrows this mechanism and applies it to improving mining efficiency.Miners can choose to set a percentage of their mining rewards as bribes to attract pledges.The staker may choose the miner who offers the highest bribe, but also considers factors such as the miner’s hardware performance and uptime.Miners are encouraged to provide bribes because higher stakes will lead to higher mining efficiency, thus creating an environment where competition and cooperation coexist, and miners and stakeholders jointly provide better services to the network.
Through these mechanisms, the Heurist project aims to create a dynamic and efficient token economy system to support its decentralized AI model hosting and inference network.
10.4 Incentive Test Network
The Heurist project allocated 5% of the total supply of HUE tokens to mining rewards during the Incentivized Testnet phase.These rewards are calculated in the form of points, which can be redeemed into fully flowing HUE tokens after the mainnet token generation event (TGE).Testnet rewards are divided into two categories: one is used for the Stable Diffusion model and the other is used for large language models (LLMs).
Points mechanism
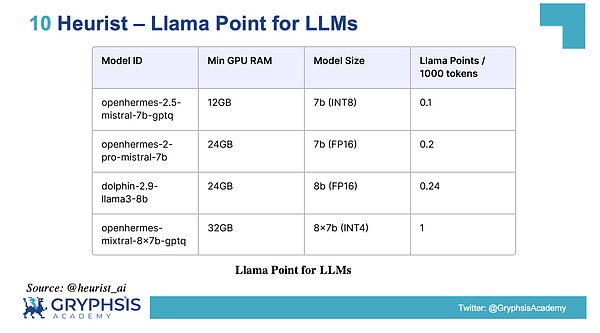
Llama Point: For LLM miners, one Llama Point is obtained for every 1000 input/output tokens processed by the Mixtral 8-7b model.The specific calculations are shown in the figure below:
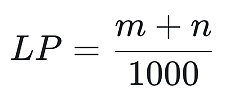
Waifu Point: For Stable Diffusion miners, a Waifu Point is obtained for each 512×512 pixel image generated (using the Stable Diffusion 1.5 model, after 20 steps iteration).The specific calculations are shown in the figure below:
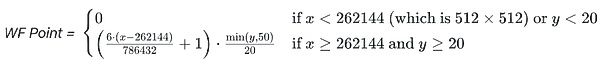
After each calculation task is completed, the system will evaluate the complexity of the task based on the results of the GPU performance benchmark and give corresponding points.The allocation ratios for Llama Points and Waifu Points will be determined as they approach TGE, taking into account the demand and usage of both model categories over the coming months.
Source: @heurist_ai
There are two main ways to participate in the test network:
-
Bring your own GPU: Whether you are a gamer with high-end configuration, a former Ethereum miner with idle GPUs, an AI researcher with occasionally idle GPUs, or a data center owner with extra capacity, you can download miner programs and set up miner nodes.For detailed hardware specifications and setup guides, please visit the Miner’s Guide page.
-
Rent a hosting node: For those who do not have the required GPU hardware, Heurist provides managed mining node services at competitive prices.The professional engineering team will be responsible for setting up the mining machine and software, you just need to observe your rewards daily growth.
The recommended GPUs involved in Heurist mining are shown in the figure below:
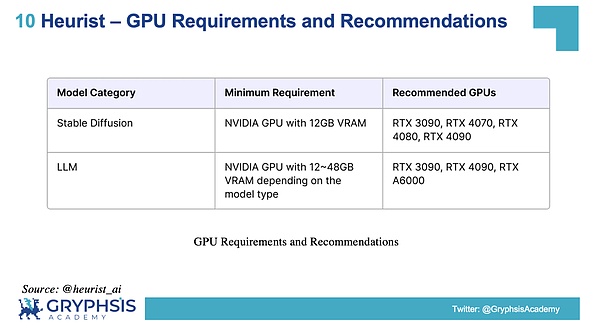
Source: @heurist_ai
Note that the Heurist testnet has anti-cheating measures, and the input and output of each computing task are stored and tracked by an asynchronous monitoring system.If miners engage in malicious behavior to manipulate reward systems (such as submitting incorrect or low-quality results, tampering with downloaded model files, tampering with equipment and delay metric data), the Heurist team has the right to cut their testnet points.
10.5 Heurist Mining
The Heurist testnet offers two points: Waifu Point and Llama Point.Waifu Point is obtained by running the Stable Diffusion model that generates images, while Llama Point is obtained by running a large language model (LLM).When running these models, there are no restrictions on graphics card models, but the requirements for video memory are rigid regulations.The higher the memory requirement, the higher the integral coefficient of the model.
The following figure lists the currently supported LLM models.For Stable Diffusion models, there are two modes: Enable SDXL mode and exclude SDXL mode.Enable SDXL mode requires 12GB of video memory, while excluding SDXL mode found in my tests that it only takes 8GB of video memory to run.
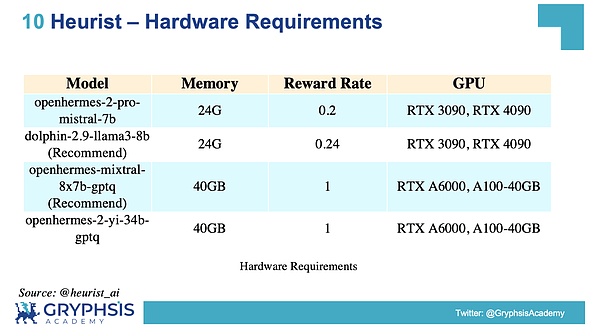
Source: @heurist_ai
10.6 Application
The Heurist project demonstrates its powerful AI capabilities and broad application prospects through three application directions: image generation, chatbots and AI search engines.In terms of image generation, Heurist uses the Stable Diffusion model to provide efficient and flexible image generation services; in terms of chatbots, it realizes intelligent dialogue and content generation through large language models; in terms of AI search engines, it combines pre-trained language models to provide accurate information retrieval.and detailed answers.
These applications not only improve the user experience, but also demonstrate Heurist’s innovation and technical advantages in the field of decentralized AI. The application effect is shown in the figure below:
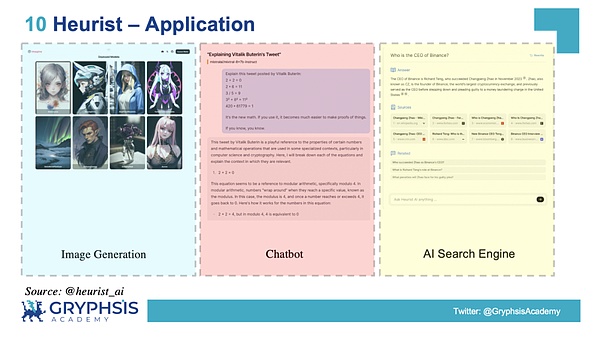
Source: @heurist_ai
Image generation
The image generation application of the Heurist project mainly relies on the Stable Diffusion model to generate high-quality images through text prompts.Users can interact with the Stable Diffusion model through the REST API and submit text descriptions to generate images.The cost of each generation task depends on the resolution of the image and the number of iterations.For example, using the SD 1.5 model to generate a 1024×1024 pixel, 40 iteration image, requires 8 standard credit units.Through this mechanism, Heurist implements efficient and flexible image generation services.
Chatbot
The chatbot application of the Heurist project implements intelligent dialogue through large language models (LLM).Heurist Gateway is an OpenAI-compatible LLM API endpoint built using LiteLLM, allowing developers to call the Heurist API in OpenAI format.For example, using the Mistral 8x7b model, developers can replace existing LLM providers with just a few lines of code and get performance similar to ChatGPT 3.5 or Claude 2 at a lower cost.
Heurist’s LLM model supports a variety of applications, including automatic customer service, content generation and complex question answering.Users can interact with these models through API requests, submit text input and obtain the response generated by the model, thereby achieving a diverse conversation and interactive experience.
AI Search Engine
The AI search engine of the Heurist project provides powerful search and information retrieval capabilities by integrating large-scale pre-trained language models such as Mistral 8x7b.Users can obtain accurate and detailed answers through simple natural language queries.For example, on the question of “Who is Binance’s CEO?”, the Heurist search engine not only provides the current CEO’s name (Richard Teng), but also explains his background and the situation of his former CEO in detail.
The Heurist search engine combines text generation and information retrieval technology to handle complex queries and provide high-quality search results and related information.Users can submit queries through the API interface and obtain structured answers and reference materials, which makes Heurist’s search engine not only suitable for general users, but also meets the needs of professional fields.
Summarize
DePIN is aThe new “sharing economy”, is the bridge connecting the physical world and the physical world.From the perspective of market value valuation and application area scope, there is still a lot of room for growth.Compared with CePIN, DePIN has advantages in decentralization, transparency, user autonomy, incentive mechanisms and censorship resistance, which further promote the development of DePIN.Due to DePIN’s unique economic model, it is easier to form a “flywheel effect”.At present, many DePIN projects have completed the construction of the “supply side”. How to stimulate the needs of real users and expand the number of “demand side” is the direction that these DePIN projects need to focus on next.
Although DePIN has shown great development potential, it still faces challenges in technology maturity, service stability, market acceptance and regulatory environment.However, with the advancement of technology and the development of the market, these challenges are expected to be gradually solved.It can be foreseen that once these challenges are effectively solved, DePIN will usher in large-scale applications (Mass Adoption), bringing massive new users and attention to the encryption field, and is likely to become a new round of bull market engine.Let us witness this day together!








