
Interviewer: Wuyue, Geek web3
Respondent: Jolestar, founder of Rooch Network & Faust, founder of Geek web3
Regarding Bitcoin Magazine’s previously ideological “Three Laws of Bitcoin Layer2”, Rooch Network’s teacher Jolestar posted his views on Bitcoin Layer2 on Twitter.
This situation is similar to the previous Nervos public chain Jan, who said on Twitter“Bitcoin Layer2 should not only consider security issues, but also consider functional expansion and empowering BTC currency attributes.”.These remarks are particularly thought-provoking.
With the attitude of “finding the root of the theory of Bitcoin Layer2”, Geek Web3 specially invited Mr. Jolestar to discuss the definition framework of Bitcoin Layer2 with Faust from different values.It aims to reveal a path to define Bitcoin Layer2 from the perspective of DA and function expansion.Although there is no consensus on how to define Bitcoin Layer2, the relevant discussion process is still of great reference value.
How to define Layer2 from a technical or DA perspective
Fog moon:Regarding the question of how to define Layer2, there are actually similar controversies in the Ethereum community.According to Mr. Jolestar on Twitter,Layer2 can be divided into “definition of technical or DA angle” and “definition of functional expansion angle”.So I would like to ask Mr. Jolestar first, what do you think of Layer2 defined from the perspective of “DA”?
Jolestar:In fact, the key is to let everyone clearly feel the difference between Layer2 and Layer1 and centralized solutions.I think there are two core points:
Layer2 does not create new block space.Technical solutions for creating new block spaces are essentially Layer1.
Layer2 needs to use Layer1 to achieve DA and security.
Fog moon:Teacher Jolestar explains here, what is “creating a new block space”?
Jolestar:This is a good question.What is said hereBlock space refers to the “data storage space” created through the blockchain consensus mechanism.The block space created by blockchain has many characteristics, such as: completely open, tamper-free, permanent storage/long-term storage, which contains great value.
As the most decentralized blockchain network, Bitcoin’s value has not been fully utilized.And this wave of Ordinals inscription fever can be understood as the value discovery of Bitcoin as a data availability layer (DA).
The Ordinals protocol defines extensible data format standards, allowing a unified solution to parse, display and exchange of data engraved on Bitcoin.And the extension protocol on Bitcoin and Layer2,How to make full use of Bitcoin’s block space is an important exploration direction.
Fog moon:Regarding what you said before, “Layer2 needs to use Layer1 to achieve DA and security”, I want to ask here,How to use Layer1 to implement DA?
For example, some Ethereum Layer2 (such as Redstone) only sends DA commit (datahash) to the chain, and the commit is associated with off-chain data.Although the DA data has not been published in full on Layer1,But it allows anyone to challenge the Commitment, requiring the sorter to put the full data on Chain.Is this considered creating block space outside Layer1?That is to say,Does not directly publish the complete DA data to Layer1, is it considered Layer2?
Jolestar:The meaning of “implementing DA” I mentioned here is actually very tolerant, not that the release of DA data depends entirely on Layer1.Even if the DA data is not completely chained, as long as the asset security of Layer2 can be associated with Layer1, it is fine.
Different Layer2 solutions have different application scenarios and different DA implementation paths. For example, the DA implementation method mentioned above by Wuyue is worth exploring.For example, when CEX submits the reserve certificate to the chain, it has already moved one step closer in this direction.So, the “using Layer1 to achieve DA” mentioned here is more broad than the way the Ethereum Foundation said.
Faust:actually,The purpose of completely chaining DA data is to enable anyone or node to trust to obtain new data, and furthermore, it is to ensure asset security.If DA data is not completely on chain, it may not be unsafe. For example, in the RGB protocol, only data Commitment is published on the Bitcoin chain, and the associated transaction data are stored off the chain. This solution can still ensure the security of assets.Because the user will personally verify the transaction behavior related to himself, if the verification fails, such transactions will not be allowed to take effect.Obviously this is very safe.
So in the RGB protocol scenario, even if the DA data is not published on the Bitcoin chain, the user’s assets are still safe. If the scenario where the user loses the data, I would think this way of client verification in person,It is reliable to entrust assets directly to any public chain.Even if the assets are directly entrusted to the Ethereum network or Bitcoin main network, there is no security that can be run by itself as Ethereum and Bitcoin are both third-party platforms.
So,Whether DA On Chain/On Layer1 is not a necessary condition for Layer2, but there should be a corresponding mechanism design to ensure that the release of DA data is reliable, at least it should not “seriously threaten” the security of user assets.
View Layer2 from the perspective of ecological and functional expansion
Jolestar:When defining L2 from an ecological and functional expansion perspective, we focus on how L2 utilizes or inherits the capabilities provided by L1.Taking Bitcoin as an example, all Layer2 is talking about how to empower BTC’s asset attributes and how to enable trillion-level BTC assets to generate additional usage scenarios. Whether it is transactions or pledges, there is a lot of room for imagination..
It takes a bridge to trade assets of one blockchain system into another system, and the key issue here is how to make users trust this bridge and ensure the security of assets.From this perspective, all solutions to create usage scenarios for BTC assets through bridges can be understood as broad Bitcoin L2.Even BTC ETFs can be understood as Bitcoin’s L2, which is a fully centralized hosting bridge that ensures security through legal supervision.
So what everyone is worried about is not the issue of decentralization, but the issue of trust.Decentralized solutions can reduce the trust costs of users and bring opportunities to new projects, but how to build a secure trustless bridge on Bitcoin is a key problem. Can L2 use other features of Bitcoin to improve this bridgeSecurity.In addition, with the development of expansion protocols on Bitcoin, whether it is Ordinals, as well as extension protocols on Ordinals (BRC20, etc.), Atomicals, RGB, Taprootassets, etc., there will be more and more new assets on Bitcoin. How to make this bridgeIt is a huge challenge to be scalable and able to quickly support new asset types.
Faust:Teacher Jolestar may be more optimistic about the broad Layer2 definition plan.But according to my personal opinion,Layer2 and even modular blockchain are popular in the Ethereum community. Westerners are more likely to stand on the Ethereum-style Layer2 definition standards.To judge the current Bitcoin ecosystem, this can be seen in many Western KOLs.
for exampleCEO of Oridnals trading platform Bioniq@BobBodily, it was pointed out that the Bitcoin ecosystem needs organizations like L2BEAT to judge Layer2;Citrea’s Lianchuang directly quotes some technical terms invented by L2BEAT, such as Optimium, to summarize certain special Bitcoin Layer2 solutions.The CEO of Bitcoin Magazine even threatened to directly hire L2BEAT people to review Bitcoin Layer2.[Note: Optimium refers to OP Rollup that does not publish full DA data on Layer1]
If you look at many “Bitcoin Layer2” from the perspective of Ethereum/Celestia, you will find that there is one important point in the current BTC ecosystem, that is, many project parties have not accurately identified their positioning.Self Position often has problems.For example, do you think Celestia is considered Ethereum Layer2?Of course not counting, but it is an important DA-layer module in the Layer2 ecological territory and the most influential one.
A similar truth,Many projects are not Layer2 itself, but the infrastructure or modules that Layer2 relies on, and are essentially the functional expansion layer that Jolestar calls it.This is like the relationship between B^2 Network and B^Hub network. The former is a typical Layer2 solution, while the latter is the facility on which the Layer2 solution relies.
The positioning of many projects in the Bitcoin ecosystem is a bit chaotic. In order to reduce communication costs and make it easier for everyone to understand, I directly position myself as Layer2.But in fact, there are quite a few projects that are similar to the core modules in the Layer2 component stack of Celestia and Avail, rather than the full Layer2 itself.
How to classify the specific categories? People in Western communities, especially those in modular blockchain-related communities, must be clear.I believe that the Western OG will“What are Layer2 itself and what are the functional expansion layers that Layer2 depends on”,By completely distinguishing it, everyone can see the entire Layer2 ecosystem more clearly and not be as chaotic as it is now.
Jolestar:Here I have some different opinions from Faust.If we put aside the concrete implementation method and abstractly understand Layer2 and other off-chain expansion solutions, we will find that it is a continuous spectrum.From the leftmost CEX to the rightmost Layer1, the middle zone solution can be included in this spectral range.
Both ends of this spectrum also represent two different growth patterns.CEX is basically a completely product-oriented and user-oriented growth method, while L1 has a relatively long construction cycle, which prioritizes narrative and blueprints, while L2 is in the middle, which will be a hybrid growth model.
Taking an inclusive perspective, we don’t need to worry too much about what is “real Layer2”.Various technologies and solutions created by the industry, such as Validium, Plasma, sovereign rollup, OP/ZkRollup, modular execution layer, decentralized computing, side chains, L2/L3, etc., should be regarded as part of this spectrum.Explore the infrastructure needed for new applications through various arrangements and combinations.
Different projects have different assumptions about new applications, which also determines its combination and growth mode. It may be that Layer1 is a little left or CEX is a little right.The future is uncertain. It is difficult to assert which model will grow at this stage, but one thing is certain. After so many years of exploration, the industry has a Layer1 and a CEX with a CEX with a Category, and aThe intermediate layer fills this gully.
How can we expand the Bitcoin network
Jolestar:Regarding this topic, I would like to briefly talk about the programmability of Bitcoin scripts.
BitcoinScript has limited programming capabilities, and its programming capabilities for assets are mainly manifested in three types of locks: time lock, Hash lock, and private key lock.Taproot allows BitcoinScript to be more complex, which creates possibilities for solutions like bitvm.But the more critical problem is that Bitcoin Script is stateless. As a programming language executed on-chain, it cannot read the state of Bitcoin, such as timestamps, nonce of past blocks, and parasitic asset information attached to UTXOwait.
Bitcoin script can only rely on the information included in the transaction input.Whether we can use Bitcoin scripts to arbitrate off-chain malicious behaviors is still a direction to be explored.
Another angle is innovation in cryptography, including protocols that construct game mechanisms based on key exchange to ensure security, such as Lightning Network, “extractable one-time signatures”, etc.
HereI want to talk about a concept called StackableL2 (stackableL2).If we implement the Indexer of Bitcoin’s extended protocol through smart contracts, we parse all UTXOs and additional states on Bitcoin in Indexer, allowing developers to deploy and apply to Indexer through smart contracts, which is equivalent to providing Bitcoin with a newSmart contract layer, this is our Rooch Network solution.
I used to call this model smart Indexer, but the concept of Indexer gives people the feeling that it is read-only, so I used a new word “Stackable L2”, which refers to all extension solutions that contain the full state of L1 in L2, which is completely inherited.All states of L1 are found.In this case, the application of L2 can read all states on L1 and create a new state. The assets of L1 and L2 can form new assets through stacking combination.The security of L2 can be guaranteed through a modular solution.

Fog moon:Can you give an example to illustrate that the assets of L1 and L2 can be combined to form new assets?
Jolestar:For example, there is an inscription on Bitcoin to express a piece of land.L2 can then stack a house on it, and they form an asset in its entirety, which is worth more than the original plot.Then someone built the house into an exhibition hall, and the value was different.In fact, this model is similar to the asset appreciation model in the real world.Assets in the real world are also value-added through synthesis, combination and stacking.
Fog moon:The concept of stacked L2 is interesting.How did this idea come about, Are there other similar projects doing this kind of thing now?
Jolestar:We think about how to inherit existing state on Bitcoin, whether it is UTXO or inscription.I started to want to use a Merkle proof method. The Layer2 node only saves the block headers of Bitcoin and does not save the “full state” of the Bitcoin network.However, when implementing this solution, it was found that the user and developer experience was relatively poor and could not support new assets such as inscriptions well.Therefore, it later evolved to preserve the “full state”.
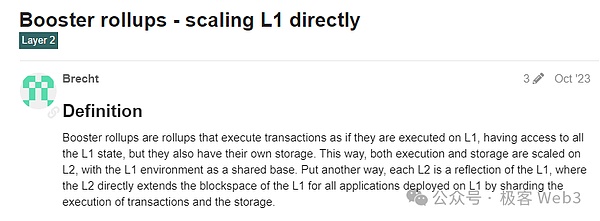
We see projects with similar ideas on the market, and the Ethereum community has a solution called Booster Rollup.Someone calledTaiko’s project saves the full state of Layer1 in Layer2., the smart contract in L2 can directly read all states of L1.Of course, we still have differences in specific implementations, such as it is an EVM virtual machine, Rooch is a Move smart contract, and there are also differences in DA and security mechanisms.
Fog moon:In the above scene, Rooch’sWhat are the advantages of Move languageIs it?
Jolestar:The assets in Move are expressed as resources or Objects, andBitcoin’s UTXO and Inscription can be mapped directly to Objects in Move.They belong to the Object of the user Owner.A key reason for the limited programming capabilities on Bitcoin is that it is difficult to express shared state, and Move has the concept of Shared Object, which can provide a good programming experience in Layer2.
The RGB++ protocol proposed by the CKB team andIsomorphic mapping, is a pioneer of this kind of thinking, but their cell is a more thorough and purer UTXO than the Object in the Move language, but the core concept is actually similar.
Another advantage of Move is its combination ability, which can nest another asset in one asset.For example, in the previous example, the house must be nested in the plot, otherwise it will be difficult to achieve atomic transfer of the plot and the house.
Faust:Here Jolestar mentioned RGB++. Indeed, RGB++ is a typical solution to expand Bitcoin UTXO from a functional perspective.RGB++ is not only suitable for CKB itself, but also for public chains such as Cardano, Fuel or Sui that are linked to UTXO or similar state storage models.
From this perspective,CKB, Cardano, Sui, and Rooch can all be used as functional expansion layers of Bitcoin.This is understandable.Now the Western community is too entangled in “security” and ignores the expansion of Bitcoin UTXO functions, which is something we should pay attention to.
Fog moon:What is the current state of Rooch Network?What are the technical challenges of the above solution?
Jolestar:We are preparing for the launch of RoochBTC pioneer network.and operational activities after launch.The RoochBTC pioneer network will include the full UTXO status and inscriptions on Bitcoin, and the final data verification and improvements in the upgrade mechanism are being made.
The full amount of data on Bitcoin is about a few hundred G. If UTXO and inscriptions are parsed out and expressed in Move language, the amount of data will increase several times.There are many kinds of inscription protocols now, and the standardization implementation of inscription protocols is not complete, so it is difficult to support them all at once. We need to provide a mechanism to dynamically support the new inscription protocol, and then gradually increase the support of the new agreement based on community feedback.
The test network is now online.Developers and users who are interested in Bitcoin and Move are welcome to experience it and try to develop applications.








