author:0xtodd Source: X,@BESSJOYCE16
Many friends will still confuse FHE, ZK, MPC, etc., so this article compares these three technologies in detail.
Last time we analyzed how FHOMOMOMOMOMOMOMOMOMOMOMOMORPTION technology was operated.
However, many friends still confuse FHE, ZK, MPC, etc., so the second Thread plans to compare these three technologies in detail: a wave:
Fhe vs zk vs MPC
First of all, let’s start with the most basic problems: -What is these three technologies?-How to work?-How to do the application of blockchain?
1. Zero Knowledge Proof (ZK): Emphasize “proof but not leaked”
The proposition of zero -knowledge proof (ZK) technical discussion is to verify the authenticity of information without leaking any specific content.
ZK is based on the actual basis of cryptography. Through zero knowledge proof, Alice can prove to the other party: she knows a secret, but there is no need to reveal any information about the secret itself.
Imagine a scene, Alice hopes to prove her credit to the car rental employee Bob, but she does not want to go to the bank to make a flow.At this time, for example, the “credit score” of bank/payment software is comparable to her “zero knowledge certificate”.
Under the condition of Bob’s “zero -knowledge”, Alice proves that her credit score is good without showing her account flow. This is zero -knowledge proof.
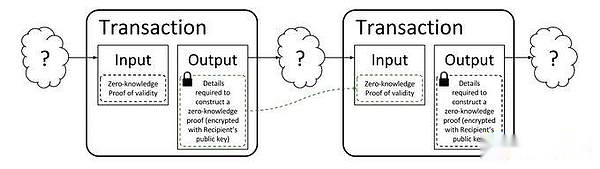
If you apply it to the blockchain, you can refer to the previous anonymous coin Zcash:
When Alice is transferred to others, she has to be anonymous, but also proves that she has the power to transfer these coins (otherwise it will lead to double flowers), so she needs to generate a ZK proof.
Therefore, after seeing this proof, the miner BOB can still go up the transaction without knowing who she is (that is, zero knowledge for Alice).
>
2. Multi -party security calculation (MPC): Emphasize “how to calculate but not leak”
Multi -party security calculation (MPC) technology is mainly used for: how to allow multi -party participants to calculate safely without leaking sensitive information.
This technology allows multiple participants (such as Alice, BOB, and Carol) to complete a computing task, but no party needs to disclose their input data.
For example, if Alice, Bob, and Carol want to calculate their average salary, they do not leak their specific wages.So how to operate?
Everyone can divide their salary into three parts and exchange two of them to the other two.Everyone adds and harmonize the number of numbers they receive, and then share this sum of sum.
In the end, the three of them had a summary of these three results, and then got the average value, but they could not determine the exact salary of others except themselves.
If you apply it to the encryption industry, the MPC wallet uses this technology.
Taking the simplest MPC wallet launched by Binance or Bybit as an example, users no longer need to save 12 aid words, but are a bit similar to change the private keys to more than 2/2.A portal of the exchange.
If the user accidentally lost his mobile phone, at least the cloud+exchange can be restored.
>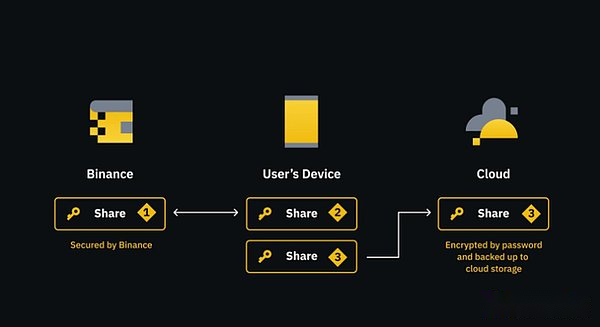
Of course, if the security is required, some MPC wallets can support the introduction of more third parties to protect private key fragments.
Therefore, based on the MPC cryptographic technology, many parties can use private keys safely without mutual trust.
3. Full -minded encryption (FHE): Emphasize “how to encrypt to find out outsourcing”
As I said in the previous THREAD, the same -state encryption (FHE) is applied: how we encrypted, so that after the sensitive data is encrypted, it can be handed over to a third party for auxiliary calculations. As a result, we can still be decrypted by us.The last part of the portal:https: //x.com/0x_todd/status/1810989860620226900Mowing
>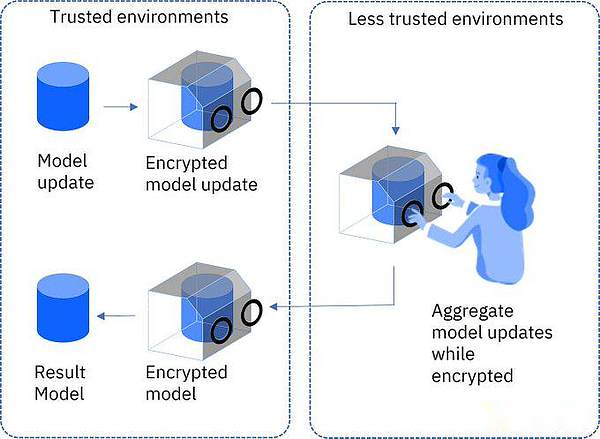
For example, Alice has no computing power and needs to rely on BOB to calculate, but does not want to tell the truth of the BOB, so you can only introduce the original data into noise (the addition of any additional method/multiplication), and then use the strong computing power of the BOB.These data are processed, and finally the Alice decrypted it to get the real results, and BOB knows nothing about the content.
Imagine that if you need to process sensitive data in the cloud computing environment, such as medical records or personal financial information, FHE is particularly important.It allows data to maintain an encryption state throughout the processing process, which not only protects data security, but also meets privacy regulations.
The last time I analyzed why the AI industry needs FHE, so what applications can the FHE technology bring in the encryption industry?For example, a project is called Mind Network. It is also a project of the Ethereum Grant and is also a project of the Binance Incubator.It pays attention to the native issue of a POS mechanism:
POS protocols like Ethereum, with 100W+verifications, are naturally fine.But many small projects, the problem comes, miners are born lazy.
Why do you say that?Theoretically, node work is to verify whether each transaction is legal.But some small POS protocols have not enough nodes, and include many “big nodes”.
Therefore, many small POS nodes discover that instead of waste time to calculate and verify in person, it is better to follow the results of the ready -made node.
There is no doubt that it will bring a very exaggerated centralization.
In addition, the scene of voting also shows this “follow”.
For example, the previous MakerDAO protocol voting, because A16Z had too many MKR ticket warehouses in that year, many times its attitude played a decisive role in certain protocols.After the A16Z votes, many small ticket warehouses can only be forced to follow the votes or abstain, which cannot reflect true public opinion at all.
Therefore, Mind Network used FHE technology:
Let the POS node be mutually*without knowing the answer of the other party, and can still use the machine computing power to complete the verification work of the block to prevent POS nodes from plagiarizing each other.
ordered
After allowing the voters to have the intention of the voting of each other, the voting platform can still be used to calculate the voting results with the help of the voting platform to prevent the voting.
>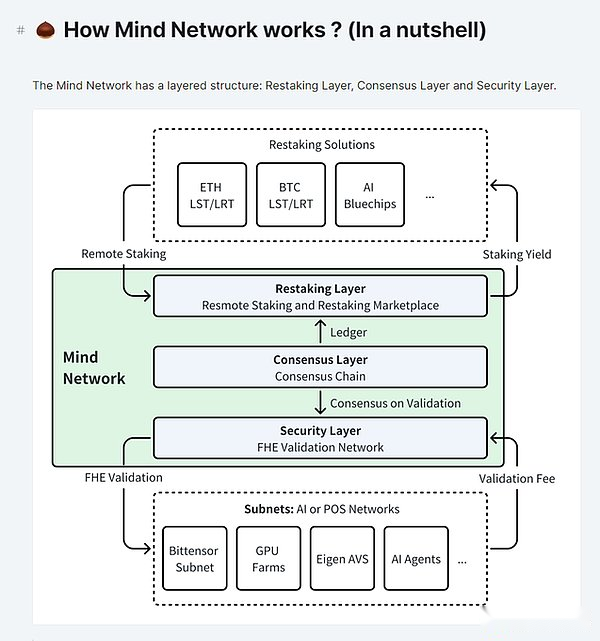
This is one of the important applications of FHE in the blockchain.
Therefore, in order to achieve such functions, Mind also needs to rebuild a RE-Staking package agreement.Because EigenLayer itself will provide “outsourcing nodes” services for some small blockchain in the future. If you cooperate with FHE, you can greatly improve security.
In the inappropriate metaphor, the small blockchain introduced EIGEN+MIND, which was a bit like the small country itself could not accurately internal affairs, so it was introduced to a foreign garrison.
This is also one of the differences between Mind and Renzo and Puffer on the POS/RESTAKING branch. Mind Network has started late than Renzo and Puffer than Renzo and Puffer. Recently, the main network has just started. Relatively speakingIt’s right.
Of course, Mind Network also provides services on AI branches, such as encrypted data to AI with FHE technology, and then allows AI to learn and process these data without knowing*original data. Typical cases include Bittensor sub -ZisiNetwork cooperation.
Finally, summarize again:
Although ZK (zero knowledge proof), MPC (multi -party calculation), and FHE (full -state encryption) are advanced encryption technologies to protect data privacy and security design, there is a difference in application scenarios/technical complexity:
Application scenario: ZK emphasizes “how to prove”.It provides a way that one party can prove the correctness of a certain information to the other without disclosing any additional information.This technology is very useful when requiring verification permissions or identity.
MPC emphasizes “how to calculate”.It allows multiple participants to calculate together without having to disclose their inputs.This is in the case of data cooperation but also protects the privacy of all parties, such as the data analysis and financial audit of cross -institutions.
FHE emphasizes “how to encrypt”.It makes it possible to commission complex calculations when the data is always encrypted.This is particularly important for cloud computing/AI services, and users can securely process sensitive data in the cloud environment.
Technical complexity: Although ZK is theoretically strong, the design is effective and easy to implement zero -knowledge certification protocol may be very complicated, and deep mathematics and programming skills are required, such as various “circuits” that you don’t understand.
MPC needs to solve the problem of synchronization and communication efficiency when implementing, especially when there are many participants, coordinated costs and calculation overheads can be very high.
FHE is facing huge challenges in terms of computing efficiency, and the encryption algorithm is complicated, and it will only be formed in 2009.Although it is theoretically attractive, its high computing complexity and time cost in practical applications are still the main obstacles.
To be honest, the data security and personal privacy protection we depend on are facing unprecedented challenges.Imagine that if there is no encryption technology, the information in our text messages, takeaway, and online shopping has been exposed.It’s like no lock -up house, anyone can enter at will.
It is hoped that friends who are confused about these three concepts can completely distinguish the pearls on the three -door encrypted holy grails.







