background
In the previous issue of Web3 security introduction to avoid pits, we mainly explained the relevant knowledge of multi-signing fishing, including the multi-signing mechanism, the reasons for multi-signing, and how to avoid malicious multi-signing of wallets.What we are going to explain in this issue is a marketing method that is regarded as an effective marketing method in both traditional industries and crypto fields – airdrop.
Airdrops can push the project from obscurity to the public’s vision in a short period of time, quickly accumulate user base, and enhance market influence.When users participate in Web3 projects, they need to click on relevant links and interact with project parties to obtain airdrop tokens. However, from high-quality imitation websites to tools with backdoors, hackers have long been full of traps upstream and downstream of user airdrop process.Therefore, in this issue, we will explain the relevant risks by analyzing some typical airdrop scams to help everyone avoid pitfalls.
What is airdrop
In order to increase the popularity of the project and realize the accumulation of early users, Web3 project parties often distribute tokens to specific wallet addresses for free. This behavior is called “airdrop”.For the project party, this is the most direct way to get users.Depending on how to obtain airdrops, airdrops can usually be divided into the following categories:
-
Task type: Complete tasks specified by the project party, such as forwarding, like, etc.
-
Interactive type: Complete operations such as token exchange, token issuance and collection, and cross-chain.
-
Holding type: Hold tokens specified by the project party to obtain airdrop tokens.
-
Pledge type: Obtain airdrop tokens through single or dual currency pledge, providing liquidity or long-term lockout.
Risks when dropping airspace
Fake airdrop scam
Such scams can be subdivided into the following types:
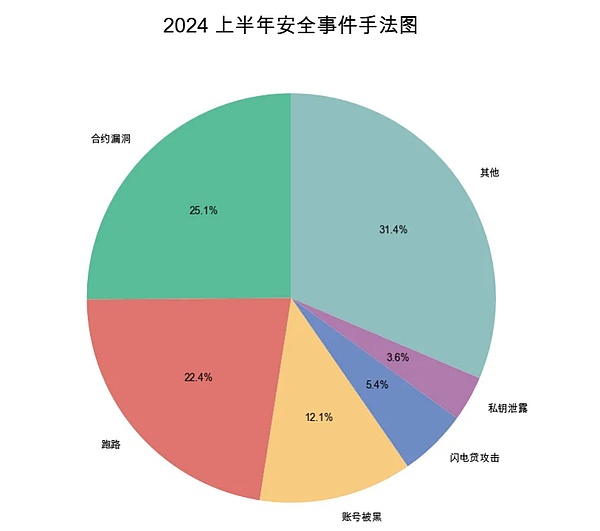
1. Hackers stole the project party’s official account and posted a message of fake airdrops.We can often see security reminder on the information platform that “the X account or Discord account of a certain project has been hacked, please do not click on the phishing link posted by the hacker.”According to the data from the Blockchain Security and Anti-Money Laundering Report in the first half of 2024, in the first half of 2024 alone, there were 27 incidents of the project party’s account being hacked.Users click on these links based on their trust in their official accounts, and are then directed to a phishing website disguised as airdrops.Once a private key/mnemonic is entered on the phishing website or the relevant permissions are authorized, the hacker can steal the user’s assets.
2. Hackers use high-quality project party accounts to swipe messages in the comment area of the project party’s official real account, post messages about receiving airdrops, and induce users to click on the phishing link.Previously, the Slow Fog Security Team analyzed this method and put forward response suggestions, to see the real and fake project parties | Beware of high imitation number fishing in the comment area; in addition, after the real project parties release the airdrop news, hackers will follow closely,Use high-quality imitation accounts on social platforms to publish large quantities of dynamics containing phishing links. Many users have installed fake APPs or opened phishing websites for signature authorization because they did not carefully identify them.
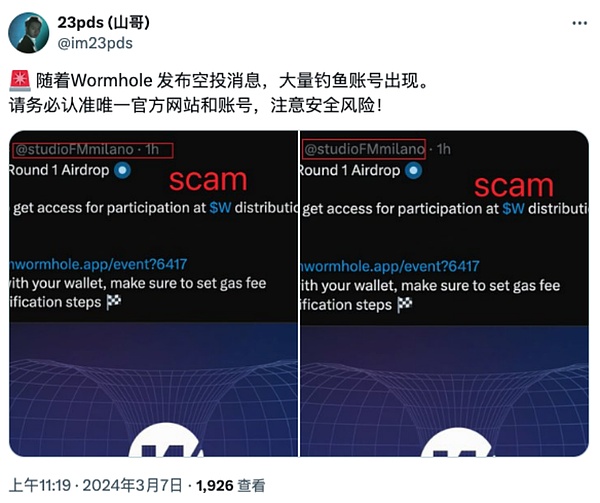
(https://x.com/im23pds/status/1765577919819362702)
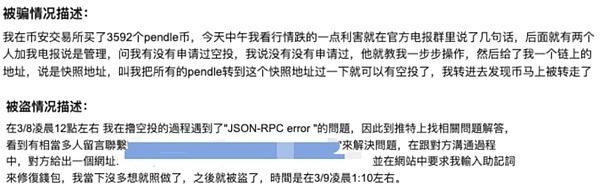
3. The third fraud routine is even more abominable. They are definitely scammers. They lurk in the group of Web3 projects, select target users to conduct social engineering attacks, and sometimes use airdrops as bait to “teach” users to transfer tokens as required to obtainairdrop.Please be vigilant and don’t easily believe netizens who actively contact your “official customer service” or “teach” you how to operate. These people are most likely to be scammers. You just want to get an airdrop, but you suffer heavy losses.
“Free” airdrop tokens
The beginning mentioned that users often need to complete some kind of task to obtain airdrops. Let’s take a look at the situation of “free” user tokens.Hackers will airdrop tokens that have no actual value to the user’s wallet, and users see these tokens and may try to interact with them, such as transferring, viewing, or trading on a decentralized exchange.However, we reversely analyze a Scam NFT smart contract and found that it will fail when trying to pledge an order or transfer this Scam NFT, and then an error message “Visit website to unlock your item” is displayed, inducing users to visit the phishing website.
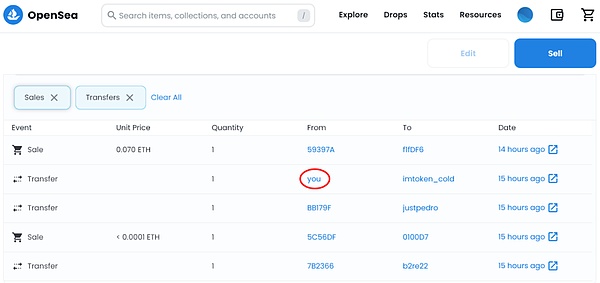
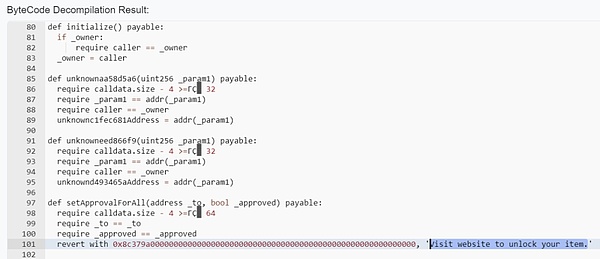
If a user visits a Scam NFT-booted phishing website, the hacker may do the following:
-
Bulk “zero yuan purchase” valuable NFT, see “zero yuan purchase” NFT phishing analysis
-
Take away Approve authorization or Permit signature from a high-value Token
-
Take away the native assets
Next, let’s see how hackers steal users’ Gas fees through a well-designed malicious contract.
First, the hacker created a malicious contract called GPT on BSC (0x513C285CD76884acC377a63DC63A4e83D7D21fb5) to attract users to interact by airdropping tokens.
When the user interacts with the malicious contract, a request appears to require approval of the contract to use the tokens in the wallet.If the user approves this request, the malicious contract will automatically increase the Gas limit based on the balance in the user’s wallet, which will cause subsequent transactions to consume more Gas fees.
Malicious contracts use excess Gas tokens (CHI tokens can be used for Gas compensation) using high Gas provided by users.After a malicious contract accumulates a large number of CHI tokens, hackers can obtain Gas compensation returned when the contract is destroyed by burning CHI tokens.
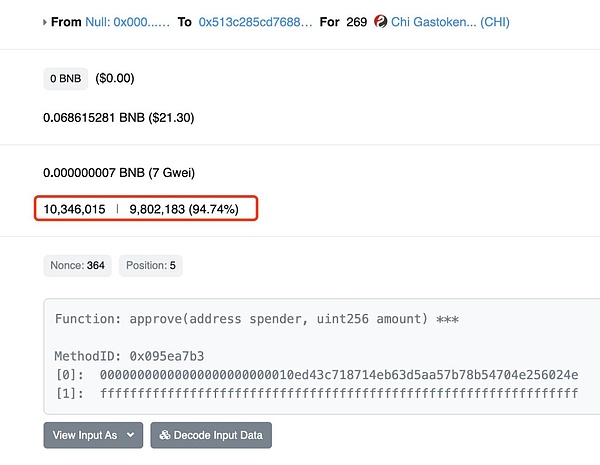
(https://x.com/SlowMist_Team/status/1640614440294035456)
In this way, hackers skillfully use users’ Gas fees to make a profit for themselves, and users may not realize they have paid the additional Gas fees.Users thought they could make profits by selling airdrop tokens, but their native assets were stolen.
Tools with backdoors
(https://x.com/evilcos/status/1593525621992599552)
During the airdrop process, some users need to download plug-ins such as translation or query token rarity. The security of these plug-ins is questionable, and some users do not download them from the official channel when downloading the plug-in, which makes it possible to download it with a backdoor.The possibility of plugins is greatly increased.
In addition, we have also noticed that there are services for selling airspace drop scripts online, claiming that automatic batch interaction can be completed by running scripts, which sounds quite efficient, but please note that downloading uncensored and verified scripts is extremely risky becauseYou can’t determine the source of the script and its real functionality.Scripts may contain malicious code, potential threats include stealing private keys/mnemonics or performing other unauthorized operations.Moreover, some users did not install or close antivirus software when performing related types of risk operations, resulting in failure to find that the device was caught in a Trojan, which was damaged.

Summarize
In this guide, we mainly explain to you what risks will be when airspace is encountered by analyzing scams. Many projects now use airdrops as marketing methods. Users can use the following measures to reduce the possibility of assets being damaged during airspace.:
-
Verification by multiple parties. When visiting the airdrop website, please check the URL carefully. You can confirm it through the project’s official account or announcement channel. You can also install a phishing risk blocking plug-in (such as Scam Sniffer) to assist in identifying the phishing website.
-
Wallet hierarchical, used by airspace wallets to store small amounts of funds, and put large amounts of funds in cold wallets.
-
Be vigilant about airdrop tokens received from unknown sources and do not easily perform authorization/signature operations.
-
Pay attention to check whether the Gas limit of the transaction is abnormally high.
-
Use well-known antivirus software, such as Kaspersky, AVG, etc., to keep real-time protection on and update the latest virus database at any time.