
>
On August 23, CKB officially released the CKB -based lightning network solution -Fiber Network (optical fiber network),Once this news spread, it quickly caused heated discussion in the community, allowing the price of CKB to rise quickly by nearly 30%within a day.The reason why news causes strong response is that the Lightning Network has a strong narrative charm, andCKB’s Fiber has upgraded the traditional lightning network, and has made many improvements for the latter.
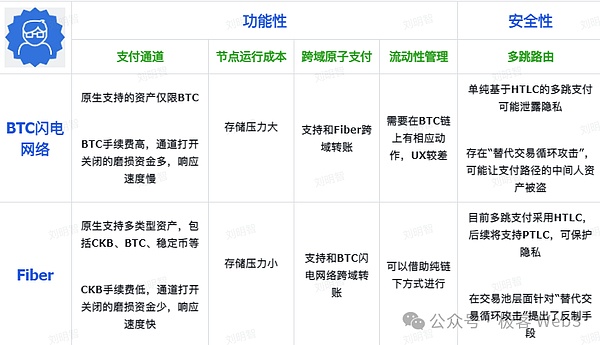
For example, FIBER can natively support multi -type assets, such as CKB, BTC, stablecoin, etc., and CKB’s handling fee is far lower than BTC and the response speed is faster. FIBER can make breakthroughs in UX.At the level of privacy and security, Fiber has also made a lot of optimization.
In addition, Fiber and BTC Lightning Networks can connect and form a larger P2P network. In previous offline activities,CKB officials even said that 100,000 physical nodes will be set up in the FIBER and Lightning Network to promote the improvement and progress of the P2P payment network.There is no doubt that this is an unprecedented story.
>
If the official vision of CKB is realized in the future, it will be huge for both the Lightning Network and the CKB and even the Bitcoin ecosystem.According to MEMPOOL data, the current BTC Lightning Network has more than 300 million US dollars of funds, with a number of nodes of about 12,000, and nearly 50,000 payment channels have been built between each other.
>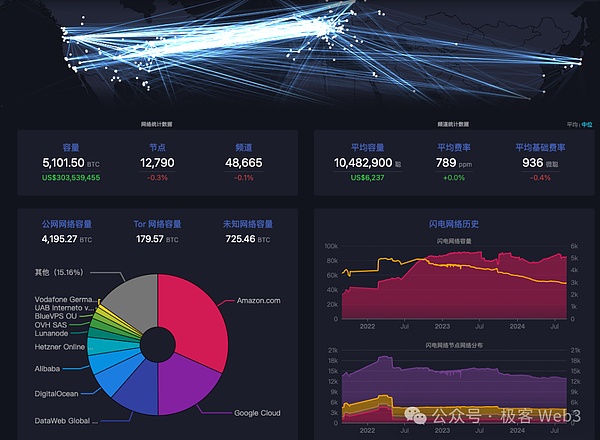
And on SpendMybtc.com, we can also see that more and more merchants are supporting the Lightning Network receipt. As long as the recognition of BTC is getting stronger and stronger, the rise of the Lightning Network and FIBER and other linksThe increasing day.
The purpose of systematic interpretation of Fiber’s technical solution,“Geek Web3” wrote this research report on the overall plan of the Fiber.As a CKB -based Lightning Network implementation plan, the principle of FIBER is consistent with the large surface of the Bitcoin Lightning Network, but it is optimized on many details.
The overall architecture of Fiber includes the following four core parts: payment channels, WatchTower, multi -jump route, cross -domain payment.Below we first explain the most important “payment channel”.
The cornerstone of Lightning Network and Fiber: Payment Channel
The essence of the payment channel is to move the transfer/transaction under the chain and deal with it, and then submit the final state to the chain for a period of time to “settle”.Since the transaction is completed in the chain, it can often get rid of the performance restrictions of the main chain such as BTC.
Assuming that Alice and BOB open a channel together, they first build a multi -signed account on the chain and save some money in it, such as Alice and BOB each store 100 yuan each, as their respective balances in the chain channel.Next, the two parties can make multiple transfers in the channel. When the passage exits the passage, the final balance is synchronized to the chain, and the multiple signed account will be paid to the two parties, that is, “settlement”.
>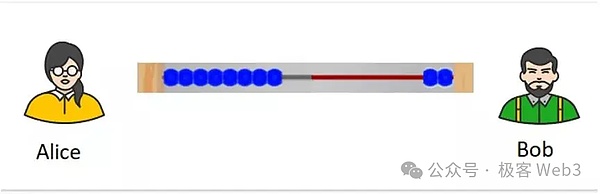
For example, the two sides started with 100 yuan at the beginning. After that, Alice transferred 50 to the BOB, and then Alice turned 10 yuan to the BOB, and then Bob turned 30 yuan to Alice.—130.It is not difficult for everyone to find that the balance of the two is unchanged. The cases of the abacus beads in the figure above can explain this well.
If one party exits the channel, the current balance Alice: 70/Bob: 130 synchronization to the chain, and the 200 yuan of the multiple accounts of the multiple account is transferred to the two to two people to complete the settlement.The above process looks simple, but many complex situations must be considered in practice.
First of all, you don’t actually know when the other party wants to quit the channel, whenTake the above example, BOB can withdraw after the second transfer is completed, or withdrawn after the first transfers, and the payment channel will not be compulsory to request, allowing participants to withdraw freely.To achieve this, assume that someone will exit at any time, and any party may submit the final balance to the chain for settlement.
So there is a setting of “commitment transaction”,The “commitment transaction” is used to declare the latest balance between the two parties in the channel, and the corresponding “commitment transaction” will be generated when each transfers occur.If you want to withdraw from the channel, you can submit the latest “commitment transaction” to the chain, and pull out the money you deserve from the multiple account.
>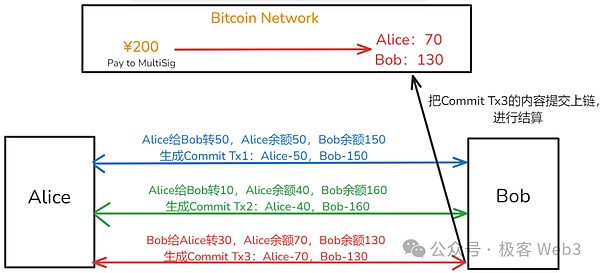
We can write down this conclusion:The promise transaction is used to settle the chain on the balance between the two parties in the channel. Any party can at any time on the chain of the latest commitment transactions and then exit the channel.
But there is an important evil scene here: BOB can submit the expired balance and commitment transaction to the chain,For example, after the COMMIT TX3 in the figure above, the balance of the BOB is 130, but in order to make a profit for yourself, the BOB submits the expired Commit TX2 to the chain and declare that the balance of its own is 160, and the balance of this balance is not real -time.Typical “double payment”.
In order to prevent such double -flower scenes, there must be corresponding punishment measures. The design of punishment measures is exactly the core of the entire 1 -to -1 payment channel. It is understood that this part can really understand the payment channel.In the design of the channel, if any party submits the expired status and the Commit TX to the chain, not only will it not be paid as expected, but will be pulled away by the other party.
Used hereThe two concepts are very important for “asymmetric commitment transactions” and “revoking key”.We first explain the “asymmetric commitment transaction”.Taking the previous Commit TX3 as an example, the figure below is a schematic diagram of promised transactions:
>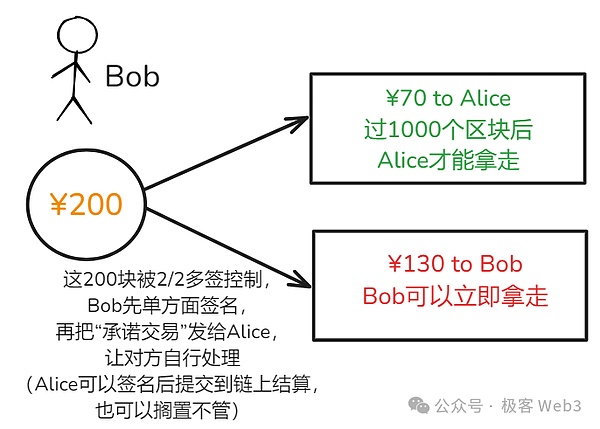
This commitment transaction is constructed by Bob, and then sent to Alice for the other party to handle it.As shown in the figure, this is a Bitcoin transfer, and declare that the 70 yuan of the multi -signed account is given to Alice, 130 yuan to BOB, but the unlocking conditions of the money are “asymmetric”.BOB is more favorable.
After receiving the promise transaction of the BOB structure, Alice can attach its own signature to satisfy more than 2/2 signatures. After that, Alice can submit the “commitment transaction” to the chain, so that you can exit the channel.If she doesn’t do this, she can continue to transfer in the channel.
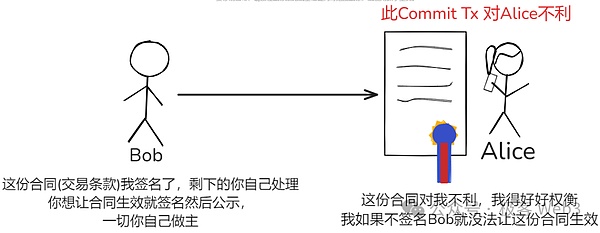
Here we should pay attention:This commitment transaction is actively constructed by Bob. The conditions are not good for Alice. Alice can only accept/reject. We must find ways to leave some autonomy to Alice.In the design of the payment channel, only Alice can put the promise transaction of “unfavorable to yourself” to trigger on the chain. This is because the promise transaction must be signed for more than 2/2.There is no Alice signature.
And Alice can “only receive the BOB signature, but not send his signature to him”, “This is like a contract that is not good for you. You need to sign a double sign with others. The other party signed the file first and then gives you the file. You can not let the other party get the signature.If you want the contract to take effect, sign it and then publicize it.Obviously, in the above case, Alice has a way to limit BOB.
>
Then the point is:After each transfer in the channel, there will be a pair of promised transactions. There are two mirror -like versions.Just like below.Alice and BOB can construct a promised transaction that is favorable to them, in which the amount they deserve when the balance/exit, and then send the content of the transaction to the other party for processing.
Interestingly,The “income amount” of these two commitments of the transaction statement is the same, but the withdrawal conditions are different. This is the origin of the “asymmetric commitment transaction” ahead.
>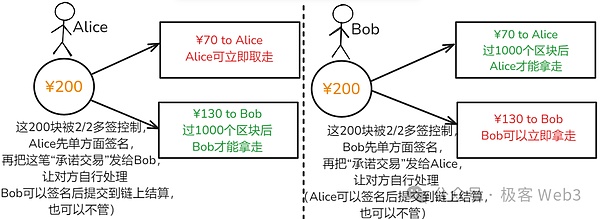
We explained earlier,Each promise transaction must be signed more than 2/2 to take effect.Bob’s local constructed and favorable commitment transactions are not satisfied with 2/2 signatures, but the commitment transaction that meets the 2/2 signing is on the hands of Alice.Balance.Conversely, similar truths.
So,Alice and BOB can only submit their unfavorable commitments to themselves. As long as one of the two parties submits the Commit TX to the chain and takes effect, the channel is closed.And when you return to the “double payment” scene, if someone submits the expired commitment transaction, what will happen?
Here is a thing called “revoking key”.If the BOB submits the expired commitment transaction, Alice can remove the money that the BOB deserves by revoking the key.
We look at the picture below. Assuming that the latest commitment transaction is Commit TX3, the Commit TX2 expires. If BOB submits the expired TX2 toAction within the scope of time lock).
>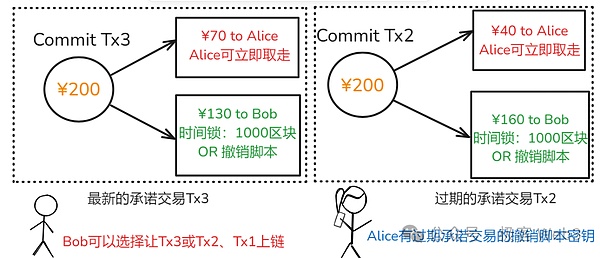
For the latest TX3, Alice does not revoke the key,Only after TX4 will appear in the future, Alice can obtain the TX3 withdrawal key.This is determined by the characteristics of public -private key passwords and UTXO. Due to space, this article will not thoroughly explain the implementation principle of revoking the key.
We can remember the conclusion: As long as the BOB dares to submit the expired commitment transaction, Alice can use the revoking key to take the BOB money as a punishment.In turn, if Alice is evil, BOB can punish her so.In this way,The 1 -to -1 payment channel can effectively avoid dual payment. As long as the participants are rational people, they dare not do evil.
Regarding the payment channel, CKB -based FIBER has a significant optimization compared to the Bitcoin Lightning Network, which can native transfer/transactions that support multi -type assets, such as CKB, BTC and RGB ++ stable coins, while the lightning network can only support Bitcoin natively Bitcoin.,,After Taproot Asset is launched, the Bitcoin Lightning Network cannot natively support non -BTC assets, and can only indirectly support stablecoins.
>
>
(Picture source: dapangdun)
also,Because the Layer1 main chain that Fiber relies on is CKB, the handling fee consumed by the operation of opening and closing the channel is much lower.This is its obvious advantage on UX.
Security of all -weather: WatchTower Watch Tower
There is a problem with the revocation key mentioned above:Channel participants should always monitor the other party to prevent the other party from sneaking the expired commitment transaction.But no one can guarantee 24 hours online,What should I do if the other party is evil when you are offline?
To this,Both Fiber and Bitcoin Lightning Network have the design of WatchTower Watching Tower, which will help users monitor the activities on the chain around the weather.Once someone in the channel submits an expired commitment transaction, WatchTower will deal with it in time to ensure the safety of the channel and funds.
The specific explanation is as follows: For each expired commitment transaction, Alice or BOB can build the corresponding punishment transaction in advance (use the withdrawal of the expired commitment transactions with the withdrawal key)Give WatchTower.Once WatchTower monitors someone to submit the expired commitment transaction, it will submit the punishment transaction and the chain for targeted punishment.
>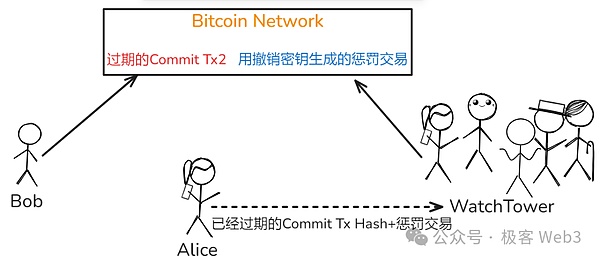
In order to protect the privacy of the channel participants, Fiber only allows users to send the “Hash+Punishment of the Expired Promise Trading” to WatchTower, so that WatchTower did not know the explicit text of the promise transaction at the beginning, but only knew its hash.Unless someone really submits the expired commitment transaction to the chain, WatchTower will see the bright text, and then submit the punishment transaction to submit the chain.In this way,Unless someone really does evil, Watchtower will not see the transaction records of the channel participants(Even if you see it, you can only see one of them).
Here we have to mention the optimization of Fiber compared to the Bitcoin Lightning Network.The above-mentioned punishment mechanism related to the cancellation key is called “LN-Penality”, andThe LN-Penalty of the Bitcoin Lightning Network has obvious disadvantages: WatchTower wants to preserve all expired commitment trading Hash and the corresponding cancellation key, which will cause a lot of storage pressure.
As early as 2018, the Bitcoin community proposed a solution called “ELTOO” to solve the above problems, but it requires Bitcoin fork to support SIGHASH_ANYPREVOUT operation code.The idea is that after the expired commitment transaction is on the chain, the latest commitment transaction can punish it, so that users can only save the latest commitment transactions.But the SIGHASH_ANYPREVOUT operating code has not yet been activated, and the solution cannot be landed.
andFiber implements the Daric protocol to modify the design of the revocation key, so that the same cancellation key is suitable for multiple expired commitments.This can greatly reduce the storage pressure of WatchTower and user clients.
Transportation system in the network: multi -jump route andHtlc/ptlc
The payment channel mentioned earlier is only applicable to 1 to 1 transaction scenario, and the lightning network supports multiple jump payment, that is, the route can be used through the intermediate node, so that the two parties that are not directly established can be transferred. For example, Alice and KEN have no channel. There is no channel.However, there are channels between Ken and BOB. There are channels between Bob and Alice. BOB can be used as intermediate nodes between Alice and Ken, so that transfer interaction between Alice and Ken can occur.and“Multi -jump route” refers to a transfer path through multiple intermediate people.
“Multi -jump routes” can enhance the flexibility and coverage of the network.However, the sender needs to understand the status of all public nodes and channels.In the FIBER, all open channels, that is, the network structure is fully disclosed,Any node can know the network information mastered by other nodes.Because the status of the entire network in the Lightning Network is constantly changing,FIBER will use Dijkstra’s shortest circuit diameter algorithm to find the shortest circuit path, so that the number of middlemen is as small as possible, and then set up a transfer path between the two parties.
>
But here to solve the credit problem of intermediate nodes:How do you guarantee that he is honest. For example, there is a middleman BOB between Alice and Ken mentioned earlier. Alice now has to transfer 100 yuan for Ken, BOB may hold the money at any time.There must be a way to prevent middlemen from doing evil,HTLC and PTLC are used to solve such problems.
Suppose Alice pays 100 yuan to Daniel, but there is no channel between them.And Alice found that they can pay Daniel through Bob and Carol.This is to introduce HTLC as the payment channel,First of all, Alice initiated a request to Daniel, and then Daniel sent an alice a hash R, but Alice did not know the Pingsh R corresponding to R.
>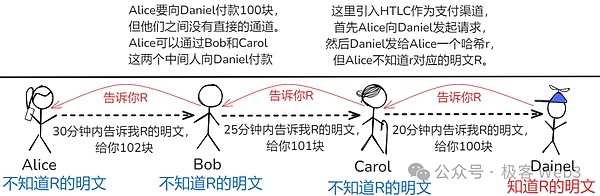
Later, in the channel with the BOB, Alice constructed the payment clause through HTLC: Alice is willing to pay 102 yuan, but the BOB will say a key R within 30 minutes, otherwise Alice will withdraw money.In the same way, BOB will create HTLC with Carol: BOB will pay 101 yuan to Carol, but Carol will say a key R in 25 minutes, otherwise BOB will withdraw money.
CAROL was made in the same way to create HTLC in the channel with Daniel: Carol is willing to pay 100 yuan, but Daniel will tell her about R’s bright text in 20 minutes, otherwise the money will be recovered by Carol.
Daniel understands that Carol’s request for key R is actually what Alice wants, because no one except Alice will care about R’s content.So Daniel will cooperate with Carol to tell her R’s content and get 100 yuan from Carol, so that Alice achieves the goal: 100 yuan for carol.
After that, it is not difficult to imagine: Carol told Bob to the key R and get 101 yuan; BOB told Alice again to get 102 yuan.We observe everyone’s gains and losses, we can see that Alice lost 102 yuan, Bob and Carol made a net profit of 1 yuan, and Daniel got 100 yuan.The one dollar earned by Bob and Carol is the handling fee they draw from Alice.
>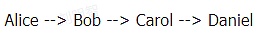
Even if someone is stuck in the payment path above, for example, Carol does not informed the downstream BOB of the key R, and it will not cause the BOB to lose: After the time, the BOB can withdraw the built HTLC.Alice is also the same.
However, there are problems with the Lightning Network: the path should not be too long. If there are too many paths in the middle, it will reduce the reliability of payment:Some middlemen may be offline, or the balance is not enough to build a specific HTLC (such as at least 100 yuan in each middle person in the previous case).Therefore, every intermediate node is added to the path, the possibility of errors will be increased.
also,HTLC may leak privacy.Although onion routing can properly protect privacy,For example, encrypted the route information of each jump, except for the initial initiator Alice, everyone only knows the adjacent up and down home, and does not know the complete path.But in fact, HTLC is still easy to be inferred.Our perspective of God looks at the following path
>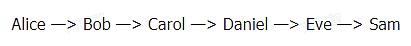
Suppose Bob and Daniel are two nodes controlled by the same entity, and many people receive HTLC from many people every day.They found that each time Alice and Carol sent HTLC, the keys to know are always the same, and the next family EVE connected to Daniel always knows the content of the key R.Therefore, Daniel and Bob can guess that there is a payment path between Alice and EVE, because they are always related to the same key,This can infer the relationship between Alice and EVE and submit monitoring.
To this,Fiber uses PTLC to improve privacy on the basis of HTLC. Each PTLC in the payment path is unlocked with different keys. Simply observing the keys required by PTLC cannot judge each other’s correlation.By combining PTLC with onion routing, FIBER can be an ideal solution for privacy payment.
also,The traditional lightning network has a “replacement cycling attack” scenario that allows the assets of the person in the payment path to be stolen.This discovery even allowed the developer Antoine R care to withdraw from the development of the Lightning Network.So far, the Bitcoin Lightning Network has not yet had fundamental measures to solve this problem, which has become a pain point.
At present, CKB officials can make FIBER solve the above attack scenarios at the level of the trading pool.Because the replacement trading cycle attack and solution are brain -burning, this article does not intend to continue to take advantage of the length to explain. If you are interested, you can read the following articles of BTCStudy and read the official information of CKB.
Overall,Whether at the privacy or safety, FIBER has greatly improved it than the traditional Lightning Network.
Cross -domain payments between FIBER and Bitcoin Lightning Network
Using HTLC and PTLC, FIBER can achieve cross -domain payment with the Bitcoin Lightning Network, and can ensure that “the atomicity of cross -domain behavior”, that is, all the steps related to cross -domain related steps are either fully successful or failed.Failure.
After the cross -domain atomic is guaranteed, it can ensure that the cross -domain itself will not cause property losses.It can make Fiber and Bitcoin Lightning Network interconnection,For example, a payment path can be set up in a hybrid network composed of FIBER and Lightning Networks, and the user transfer to the user directly to the BTC Lightning Network in the FIBER (only BTC) can be used in the BTC Lightning Network with CKB and RGB ++ assets in the FIBER.In exchange for equivalent Bitcoin.
We simply say the principle: Assuming that Alice runs nodes in the FIBER network, and BOB runs nodes in the Bitcoin Lightning Network,Alice wants to transfer some money to Bob, which can realize this transfer through cross -domain transit providers.Specifically, Ingrid runs nodes in FIBER and BTC Lightning Networks, respectively, acting as middlemen in the transfer path.
>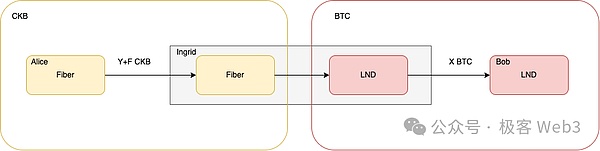
If BOB wants to receive a BTC, Alice can negotiate the exchange rate with Ingrid, such as using 1 CKB to change 1 BTC.Alice can send 1.1 CKB to Ingrid in Fiber, and then Ingrid sends a BOB BOB in the BTC Lightning Network, and Ingrid will leave 0.1 CKB as a handling fee.
The specific operation method in it is actually to establish a payment path between Alice and Bob and Ingrid, that is, Alice -& GT; Ingrid & GT; BOB, and then use HTLC.Similar truths have actually been mentioned earlier. In order to receive money, BOB must tell the content of the Ingrid key R.Once Ingrid gets the key R, you can unlock the money locking in HTLC.
It should be noted that these two cross -domain behavior that occurred in the BTC Lightning Network and FIBER is atomic, which means that either two HTLCs are unlocked and cross -domain payment is successfully implemented.Either do not unlock, cross -domain payment fails, without the situation that Alice gives money and BOB cannot receive money.
(In fact, the middleman Ingrid can unlock Alice’s HTLC after knowing the key R, but what is damaged is Ingrid, not user Alice, so the design of Fiber is safe for users))
This method does not need to trust third parties, you can achieve transfer behavior between different P2P networks, and almost no modification is required.
Fiber compared to other advantages of the BTC Lightning Network
We mentioned earlier,FIBER supports CKB native assets and RGB ++ assets (especially stablecoins), which makes it have great potential in the real -time payment scenario, and it is more suitable for daily small payment demand.
also,There is a main pain point of the Bitcoin Lightning Network, which is liquidity management.Everyone may remember what we first said, the overall balance in the payment channel is fixed,If the balance of one of them is exhausted, it will not be able to transfer the other party. Unless the other party transfer money to him first, at this time, it is necessary to re -inject funds or open a new channel.
>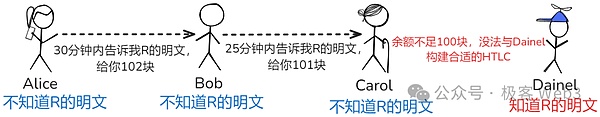
also,If it is in a complicated multi -jump network, the balance of some intermediate nodes cannot be transferred outward, which may cause the entire payment path to fail.This is one of the pain points of the lightning network. The solution to this provides an efficient liquidity injection solution to ensure that most nodes can inject funds at any time.
but,In the BTC Lightning Network, the steps to inject liquidity, open or off the channel are all carried out on the BTC chain. If the BTC network handling fee is extremely high, it will have an adverse effect on the UX of the payment channel.假设你想开启一个容量为100美元的通道,但建立通道的操作花掉10美元手续费,那这个通道在初始化时就磨了你10%的资金,这是让大多数人无法接受的;对于Lobricity injection and other work are also the same.
Fiber has a very significant advantage.First of all, CKB’s TPS is much higher than BTC, and the handling fee can reach the level of beauty. Secondly, in order to copeThe FIBER program has launched a new solution with Mercury Layer, so that liquidity injection work can get rid of the operation on the chain and solve UX and cost problems.
>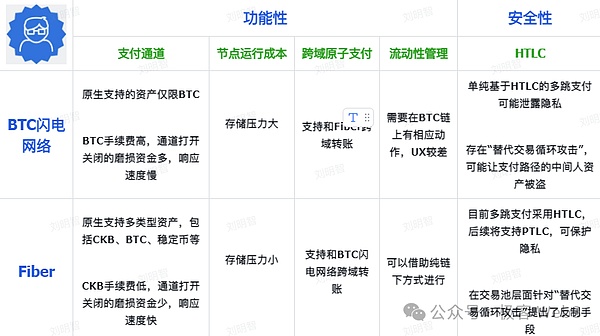
At this point, our system has combed the overall technical architecture of Fiber. The rough comparison summary of the Bitcoin Lightning Network is shown in the figure above.Since the knowledge points involved in the FIBER and Lightning Network itself are too much and too complicated, simply an article may not be able to cover all aspects.In the future, we will launch a series of articles on the topic of Lightning Network and Fiber. Please look forward to it.







