
Organization: Deng Tong, Bitchain Vision Realm
During the 2022 Hong Kong Web3 Carnival, Ethereum co -founder Vitalik Buterin delivered a keynote speech “Reaching the Limits of Protocol Design”.The Bitchain vision is sorted out as follows to readers.

Blockchain and ZK-Snarks
The type of technology we used to build an agreement has changed a lot in the past 10 years.Then, when Bitcoin was born in 2009, it actually used a very simple form of cryptography, right?The only encryption technology you see in the Bitcoin Agreement is -you have a beh, you have an ECDSA signature with an oval curve, you have a workload proof.The workload proof is only another way to use hash. If you look at the technology used in 2000 to build an agreement, you will see this more complicated technology, and these technologies actually just appeared 10 years ago.Essence

Many such things have already existed for a long time.Technically, since the birth of the PCP theorem, we already have ZK-SNARKS, and the theorem has a history of decades.So in theory, these technologies have existed for a long time, but in practice, there is huge efficiency obstacles between what you can do in academic papers and what you can do in practical applications.
Actually, I thinkThe blockchain itself has a lot of praise, because it actually helped the adoption of these technologies and really put them into practice.
Today’s situation has changed in the past ten years and made great progress.This includes many different things.The agreement we have today rely on all these technologies.Look at the agreement built in 2000, all these things have been regarded as key components from the first day.ZK-SNARKS is the first major thing here, right?ZK-SNARKS is a technology.You can verify the proof faster in this way, and then run the calculation yourself.You can also verify the proof without hiding a lot of information in the original input.Therefore, finding ZK-SNARKS is very useful in privacy and is also very useful in terms of scalability.
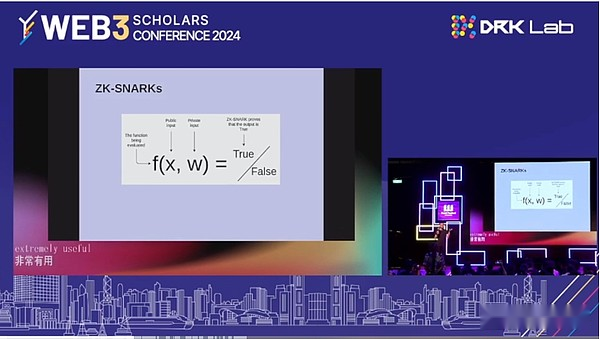
What is the role of blockchain now?Blockchain has brought you a lot of benefits. They provide you with openability, and they provide you with global verification.But all of this is at the expense of two very big things.One is privacy, and the other is security.ZK-SNARKS, you are privacy and you are safe.In 2016, we saw the Zcash protocol.Then we started seeing more and more things in the ecosystem theory.Today, almost everything has begun to be based on ZK, and starts to calculate and fully encrypted in various parties.But some things you can’t do with ZK-SNARKS.So privacy protection, computing, and running on people’s private data.Voting is actually an important case, you can get a certain degree of benefits in it.So vote with ZK-SNARKS, but if you want to get really the best attributes, then MPC and FHE are what you must use.
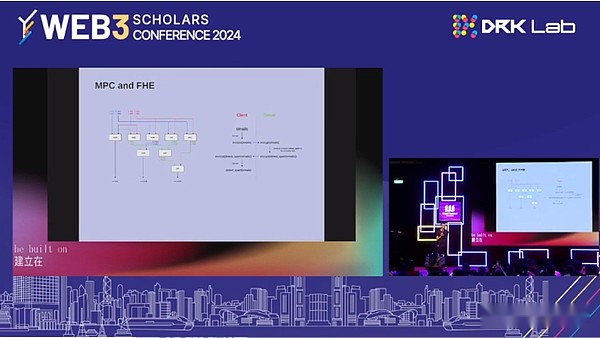
Many encryption and artificial intelligence applications will eventually use MPCs and FHE. These two primitives have been increasing rapidly in the past ten years.
The BLS key aggregation is an interesting technology. It basically allows you to obtain a lot of signatures from a lot of different participants (there may be tens of thousands of participants), and then verify the combination signature as soon as possible, just like the signature of the portfolio, just like the signature of the portfolio, just likeVerify the same signature.
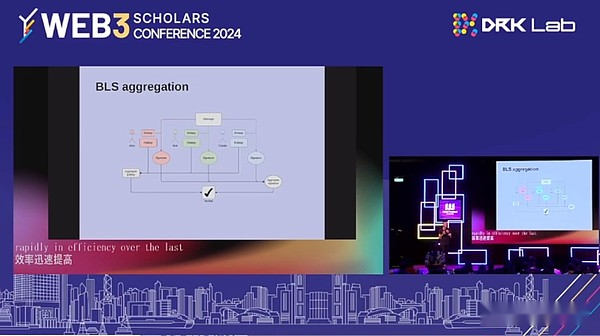
This is very powerful.The BLS key aggregation is actually a technology in modern state consensus to prove theoretical core.
If you look at the status consensus established before the BLS key aggregation, many times, algorithms usually only support hundreds of verifications, just like a theorem currently has about 30,000 verifications because they are submitting signatures every 12 seconds.The reason why this is possible is that this new form of cryptography has actually been optimized only in the past 5 to 10 years.
Efficiency, security and extension functions
So many things are brought by these new technologies.They soon became stronger.Today’s agreement uses a lot of these technologies.We have indeed experienced a major transformation from dedicated cryptography to general cryptography. Where to create a new agreement, you must understand how the cryptography works.You must create an algorithm for special use applications to achieve more common purposes.In this world, you need to create an application that uses the content I mentioned in the past 5 minutes, and you don’t even need to be a cryptist.You can write a piece of code and compile it into approval and verification device, and you have a application that seeks history.
So what are the challenges here?I think the two major problems now: one is efficiency and the other is security.Now there are third types, which can be said to be an extension function.I think,Improve the efficiency and safety of what we have todayMore important.

Let’s talk about efficiency.Let’s say a specific example is the theory of blockchain.Theoretically, if the block time is 12 seconds, the average interval between a block and the next block is 12 seconds.In normal block verification time.This is the time required for the verification block of the subordinates, about 400 milliseconds.Looking for traps, proof theory, and stopping the time required for about 20 minutes.But two years ago, this situation was rapidly improving.Previously, this equal was 5 hours.It now takes an average of 20 minutes.Compared with two years ago, we still made great progress.

What is our goal now?The goal is to perform real -time proof.The goal is that when you create a block, you can obtain proof before creating the next block. When we realize real -time proof, each user in the world can easily become a complete verification user of the agreement.If we can enter such a world: each Ethereum wallet, including browser wallet, including mobile wallets, and smart contract wallets, including other chains, are actually fully verifying the theory of consensus rules.
Therefore, they don’t even believe whether they prefer equity verification, because they actually directly verify the rules and directly ensure that the block is correct.How do we use history to do this?To make it really play a role, ZK-SNARKS proves that it needs to be carried out in real time, but there is a way to prove theory and block within 5 seconds.So the question is, can we achieve it?Now, MPC and FHE also have similar problems.As I mentioned earlier, a powerful case of MPC and FHE is voting, right?It has actually begun to appear.
The current problem of MPC is that some of its security attributes depend on a central server.Can we decentralize?We can, but it needs to be more efficient.The cost of these agreements is huge.
How do we realize such demands?For ZK-SNARKS, I think the efficiency improvement is divided into three categories.One of them is parallelization and aggregationTherefore, if you imagine in a theory about blocks, in a verification, the block needs up to about 10 million calculation steps.You execute each calculation step and prove it separately.Then you prove the aggregation.
 After about 20 above steps, you get an important proof of the correctness of the entire block.This is what you can do with existing technology today.And can prove inferior blocks within 5 seconds.It requires a lot of parallel computing, so can we optimize it?Can we optimize the aggregate proof?The answer is yes. There are many theoretical ideas about how to do this, but this really needs to be transformed into actual things.
After about 20 above steps, you get an important proof of the correctness of the entire block.This is what you can do with existing technology today.And can prove inferior blocks within 5 seconds.It requires a lot of parallel computing, so can we optimize it?Can we optimize the aggregate proof?The answer is yes. There are many theoretical ideas about how to do this, but this really needs to be transformed into actual things.
Under the same hardware costs and the same power cost, ASIC can handle the hash speed of about 100 times faster than the GPU.The question is, can we obtain exactly the same benefits through strict proof?I think the answer is that we should be able to.Many companies have begun to build products specifically used to prove ZK-SNARKS, but in fact, it should be very common.Can we shorten 20 minutes to 5 seconds, thereby increasing efficiency?
So we have the GKR protocol, we have 64-bit, we have various ideas such as ZK-SNARKS.Can we further improve the efficiency of the algorithm?Can we create more ZK-SNARKS, friendly hash functions, more ZK-SNARKS, friendly signature algorithms?There are many ideas here, and I strongly encourage people to do more for these ideas.We have all these amazing forms of cryptography, but will people trust them?If people worry about some kind of defects, whether it is ZK-Snarks or ZKEVM Circuits, they all have 7000 lines.If they do it very effective.In theory, there are 15 to 50 errors per thousand lines.We try hard.There are less than 15 lines, but it is also greater than zero.If you have these systems holding billions of dollars assets, then if one of them is wrong, no matter how advanced the encryption technology is, these money will be lost.
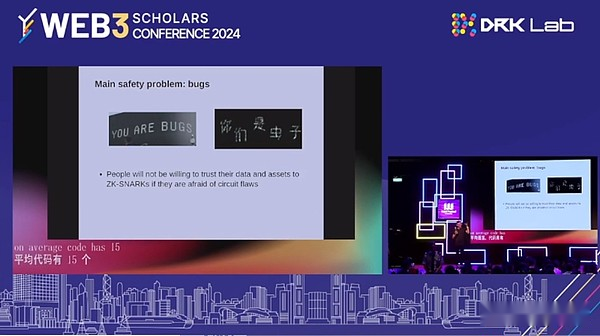
The question is, what can we do to really adopt existing cryptography and reduce the number of errors in it?
Now, I think that if there are 9 of the 12 people in a group, more than 75% of the people agree that there are mistakes, then they can overthrow any content in the proof system.So it is quite centralized.In the near future, we will have multiple proofs.In theory, you can reduce the risk of errors in any part of it.You have three proof systems.If one of them is wrong, I hope that the other two will not make errors in exactly the same position.
Perform formal verification with artificial intelligence tools
at last,I think an interesting thing worth studying in the future is to use artificial intelligence tools for formal verification.In fact, there is no error in mathematics that there are things like ZK-EVM.But can you truly prove this, for example, ZK-EVM implementation is fully the same function as the theorem in the GAS.For example, can you prove that they have only one output for any possible inputs?
In 2019, no one thinks artificial intelligence can make very beautiful photos today.We have made a lot of progress, and we have seen artificial intelligence.
The question is whether we can try to turn similar tools to similar tasks.For example, a complex statement in a program that spans thousands of lines automatically generate mathematical proof.I think this is an interesting open challenge that allows people to understand the efficiency of signature aggregation.So today Ethereum has 30,000 verification device, and the requirements for running a node are quite high?There is a node theory on my laptop, which can run, but it is not a cheap laptop computer.And I really have to upgrade the hard disk myself.The expected goal is theoretically, we hope to support as much verification as possible.We hope that the equity certificate is as democratic as possible so that people can directly participate in any size verification.We hope that the requirements in the node theory are very low and easy to use.We hope that theory and agreements are as simple as possible.

So what are the limits here?Limitation is that all the data of each participant each slot requires 1 bit, because you have to broadcast the information that who is involved in the signature and who has not participated.This is the most basic limit on this.If this is the case, there will be no other restrictions.Calculate, there is no lower limit.You can prove the aggregation.You can recuble in each tree or signature.You can make various signature aggregates.You can use SNARKS, you can use cryptography, just like you can use 32 -bit Snarks, various technologies.
Think about point -to -point network
The question is, to what extent can we optimize the signature aggregation -point -to -point safety?It is not enough people to think about the point network.This is what I really want to emphasize.I think that in the field of encryption, there are usually too many tendencies to create a peculiar structure above the point -to -point network, and then assume that the point -to -point network can work.There are many devils hidden here, right?I think these demons will become more complicated, just like the way of working in Bitcoin in Bitcoin.
There are various attacks, such as witch attacks, refusal service attacks, etc.But when you have a very simple network and the only task of the network is to ensure that everyone can get everything, the problem is still quite simple.The problem is that as a scale theory, the point -to -point network becomes more and more complicated.Today’s Ethereum dot -point network has 64 pieces -in order to make a signature aggregation, to handle 30,000 signatures.
First of all, as we do today, we have a point -to -point network. It is divided into 64 different shards. Each node is only part of one or more networks.Therefore, the cost of layering of the two items and allowing Rollup is very low, which is a talented scalability solution.This also depends on a more complicated point -to -point architecture.Do you download only 1/8 of all data in each node?Can you really make such network security?How can we save data?How do we improve the security of points to the network?
in conclusion
so,What we need to consider is an agreement that can implement cryptographic restrictions.Our cryptography is much stronger than decades ago, but it can be stronger. I think we really need to start considering what ceiling is now. How can we really reach the ceiling?
There are two equally important directions here:
One of them is to continue to improve efficiencyWe want to prove everything in real time.We want to see such a world: the default of each message transmitted in the decentralized protocol block is ZK-SNARKS default to prove that the message and all the contents that the message depend on follow the rules of the agreement.How can we improve efficiency to achieve this goal?The second is to improve security.The possibility of fundamentally reduced the possibility of problems, let us enter a world. In this world, the actual technology behind these protocols can be very powerful and very trustworthy.

But as we have seen many times, multiple signatures will be attacked by hackers.In many cases, the tokens in these Layer 2 projects are actually controlled by multiple signatures.If five -nine -people are attacked by hackers at the same time, they will lose a lot of money.If you want to avoid these issues, then we need to trust -we can use this technology, and to force the rules by encrypted, instead of believed in a small group of people to ensure system security.
But to truly realize this, the code must be trusted.The question is, can we make the code credible?Can we make the Internet trustworthy?Can we make the economics of these products trustworthy?I think these are the core challenges, and I hope everyone can continue to work together to improve.Thanks.








