
introduction
OKX Web3 wallet specially planned the “Safety Special issue” column to make special answers on different types of chain security questions.Through the most real cases around the user, it is jointly shared and answered with experts or institutions in the field of security.Users have learned to protect their private keys and wallet asset safety from themselves.
The biggest charm of the world is that everyone has the potential to become a “giant whale”
But even “giant whale” can not be stubborn. Although eating meat, there are also when there is “beating”.
So, playing on the chain, safety first
Otherwise, you have to “start a job” ~
This issue is the 05th issue of Safety Special Issue. Special Blockchain Security Pioneer BlockSec and OKX Web3 Wallet Security Team, from the perspective of practical guidelines, will be given to all users and project parties who are about to become “giant whales”.A DEFI hedging strategy.For example, how to look at audit reports, preliminary assessment of indicators and parameters, project parties or giant whale users, how to build monitoring perception ability, DEFI security protection codes, etc., do not miss it!

BlocksecSecurity team:Blocksec is the world’s leading “full stack” blockchain security service provider. At present, the company has served more than 300 customers, including Metamask, Compound, Uniswap Foundation, FORTA, Pancakeswap, PUFFER and other well -known project parties.$ 20 million in funds.
Blocksec’s CEO & AMP; Co-Founder Zhou Yajin is a professor of computer at Zhejiang University. AMINER selected the world’s most influential scholars. He published more than 50 top papers and obtained more than 10,000 citations.CTO & amp; CO-Founder Wu Lei is a professor of computer at Zhejiang University. The former Shield co-founder led the team to discover dozens of zero vulnerabilities of many well-known projects.Product Director Raymond has been responsible for safe products in Tencent and 360.
Okx web3Wallet safety team:Hello everyone, I am very happy to make this sharing.The OKX Web3 Security team is mainly responsible for the construction of various types of security capabilities in the field of web3, such as smart contract security audit, wallet security capacity building, and the safety monitoring of the project on the chain.Protective services contribute to the security ecology of the entire blockchain.
Q1: Share a few users’ real encountersDefiRisk case
BlocksecSecurity team:DEFI has attracted many large households because it brings relatively stable high returns to assets.In order to improve liquidity, many project parties will also actively invite large households to settle in.For example, we can often see news reports that some large households are stored in huge assets into DEFI.Of course, when participating in the DEFI project, these giant whales will also face some risks in addition to stable benefits.Next, we share some disclosure of Defi risk cases:
Case 1: In the Polynetwork security incident in 2022, a total of more than $ 600 million in assets were attacked.According to rumors, Shenyu also has 100 million US dollars in it. Although the attackers have repaid the money and the incident has been successfully resolved. Shenyu also announced that it would build a monument on the chain to commemorate the matter, but the process must be very suffering.Although a small part of the current security incident is good, most of the safety events are not so lucky.
Case 2: The well -known Dex Sushiswap was attacked in 2023. The large number of large households lost more than $ 3.3 million in losses, and his loss alone reached about 90%of the total loss.
Case 3: In the PRISMA security incident in March this year, the total loss was 14 million US dollars. These losses came from 17 wallet addresses, and the average loss per wallet lost 820,000 US dollars, but the losses of 4 users accounted for 80%.Most of these stolen assets have not been recovered.
In the final analysis, DEFI, especially the main network, is not ignored because the GAS Fee cannot be ignored. Only assets reaches a certain scale can they really get income (except for airdrop rewards).In some projects, 2% of the giant whales contributed 80% of TVL.When the security incident occurs, these giant whales will inevitably bear most of the losses.”You can’t see the giant whales eating meat, and they are also beaten.”
Okx web3Wallet safety team:With the prosperity of the world on the chain, the DEFI risk cases encountered by users are also increasing day by day. The security on the chain is always the most basic and important needs of users.
Case 1: PlayDapp privilege account private key leakage incident.From February 9th to 12th, 2024, the PlayDapp game platform based on Ethereum was attacked due to private key leaks. The attacker was cast and stole 1.79 billion PLA tokens without authorization, losing about $ 32.35 million.The attacker added new coinkers to the PLA token, cast a large number of PLA, and scattered to multiple chain addresses and exchanges.
Case 2: Hedgey Finance attack event.On April 19, 2024, Hedgey Finance encountered major security vulnerabilities on Ethereum and Arbitrum, resulting in a loss of about 44.7 million US dollars.The attacker uses the contract to lack the vulnerability of the user’s input verification to obtain the authorization of the attack on the attack on the attack, so as to steal assets from the contract.
Q2: Can you summarize the currentDefiThe main risk type exist in the field
Okx web3Wallet safety team:Combined with real cases, we sort out the current 4 types of risk types common in the current DEFI field
The first category: fishing attack.Fishing attacks are a common type in cyber attacks. By disguised as legal entities or individuals, they trick victims to provide sensitive information, such as private keys, passwords, or other personal data.In the field of DEFI, fishing attacks are usually performed in the following ways:
1) Fake websites: The attacker creates a fishing website similar to the real DEFI project to seduce users to sign authorities or transfer transactions.
2) Social engineering attack: On Twitter, the attacker uses high imitation accounts or hijacking the project party Twitter or Discord account to release false promotional activities or airdrop information (actually fishing links) to perform fishing attacks on users.
3) Malicious smart contracts: The attacker posted a seemingly attractive smart contract or DEFI project to seduce users to authorize their access rights to steal funds.
The second category: Rugpull.Rugpull is a unique scam in the field of DEFI. It means that the project developers suddenly withdraw the funds and disappear after attracting a large amount of investment, resulting in all investors’ funds.Rugpull usually occurs in the decentralized exchange (DEX) and liquidity mining projects.The main manifestations include:
1) Liquidity evacuation: Developers provide a large amount of liquidity to attract user investment in the liquidity pool, and then suddenly withdraw all liquidity, resulting in the token prices plummeted, and investors have suffered heavy losses.
2) Forge project: Developers create a seemingly legal Defi project, which seduce users to invest through false commitments and high income, but there is actually no actual product or service.
3) Change contract permissions: developers use the back door or permissions in smart contracts to change the rules of the contract or withdraw funds at any time.
Third category: Smart contract vulnerability.Smart contract is an automatic execution code. It is running on the blockchain, and once deployed, it cannot be changed.If there is a loophole in a smart contract, it will lead to serious security issues.Common smart contract vulnerabilities include:
1) Re -entered vulnerability: The attacker repeatedly called the vulnerability contract before the last call was completed, causing problems in the internal state of the contract.
2) Logic error: Logical errors in contract design or implementation lead to unexpected behaviors or loopholes.
3) Our integer overflow: The contract does not properly handle the integer operation, resulting in overflow or overflow.
4) Price manipulation: The attacker is attacked by manipulating the price of the prophecy machine.
5) Precision loss: Due to the problem of floating point or integer accuracy, calculation errors are caused.
6) Lack of input verification: Failure to verify the user input, leading to potential security issues.
The fourth category: governance risk.The governance risk involves the core decision -making and control mechanism of the project. If it is maliciously utilized, it may cause the project to deviate from the expected goal, and even cause serious economic losses and trust crisis.Common types of risk include:
1) Private key leakage
The privilege account of some DEFI projects is controlled by EOA (Externally Owned Accounts) or signing more wallets. If these private keys are leaked or stolen, the attacker can manipulate contracts or funds at will.
2) Governance attack
Although some DEFI projects use decentralized governance solutions, the following risks still exist:
· Borrowing to tokens: The attacker can manipulate the results of the voting in a short period of time by borrowing a large amount of tokens.
· Control the right to voting: If the token is highly concentrated in the hands of a few people, these people can control the decision -making of the entire project through centralized voting rights.
Q3: What dimensions or parameters can be preliminarily evaluatedDefiThe safety and risk level of the project?
BlocksecSecurity team:Before participating in a DEFI project, it is necessary to conduct a overall security assessment of the project.Especially for participants with relatively large capital volume, necessary safety due diligence surveys can ensure the security of funds to the greatest extent.
First, it is recommended to comprehensively evaluate the code security of the project, including whether the project party is audited and whether the audit company with a good security reputation, whether there are many audit companies involved, and whether the latest code has been audited.Generally speaking, if the code running online is audited by a number of security companies with a good security reputation, it will greatly reduce the risk of being attacked by security.
Second, it depends on whether the project party deploys a real -time safety monitoring system.The safety of security audit guarantees is static and does not solve the dynamic safety problem caused by the project after the project.For example, the project party has inappropriately adjusted the key operation parameters of the project and added new POOL.If the project party uses some real -time safety monitoring systems, the safety factor at runtime is higher than that of the agreement that does not adopt such a solution.
Third, it depends on whether the project party has an automatic response ability in emergency situations.This ability has long been ignored by the community.We found that in multiple security incidents, the project party did not achieve automatic function melting (or the melting of fund -sensitive operations).Most of the project parties use manual ways to handle safety events in emergency situations, and this method is proven to be inefficient or even invalid.
Fourth, it depends on the external dependence of the project and the robustness of external dependence.A DEFI project will rely on the information provided by third -party projects, such as price and liquidity.Therefore, it is necessary to evaluate the security of projects from external dependence quantity, external dependent project security, whether there is monitoring of external -dependent data and real -time processing angle to evaluate projects.Generally speaking, the project party of the external dependencies is the project party of the head project and the fault tolerance and real -time processing of the abnormal data of external projects will be safer.
Fifth, whether the project party has a relatively good community governance structure.This includes whether the project party has a community voting mechanism for major events, whether the sensitive operation is completed, and whether the more wallet has introduced the community neutral participation and whether it has the community security committee.These governance structures can improve project transparency and reduce the possibility of users’ funds in the project by Rugpull.
Finally, the historical history of the project party is also very important.The background investigation of the project team and the core members of the project needs to be conducted.If the core member of the project party has been attacked many times in the past or bad historical records such as Rugpull, the security risks of such projects will be relatively high.
In short, before participating in the DEFI project, users, especially large funding participants, should do a good job of research, from the code security audit before the project to the real -time security monitoring and automatic response capabilities after the project goes online, and inspect the security of the project party’s securityInvestment and security, we must do a good job of being transferred from the perspective of external dependence, governance structure, and the past history of the project to ensure the security of funds invested in the project.
Okx web3Wallet safety team:Although it is impossible to ensure the security of the DEFI project 100%, users can initially evaluate the safety and risk level of the DEFI project through the cross -combination of the following dimensions.
1. Project technical security
1. Smart contract audit:
1) Check whether the project has been audited by multiple audit companies, and whether the audit company has a good reputation and experience.
2) Check the number and severity of the reports in the audit report to ensure that all problems have been repaired.
3) Check whether the code of the project deployment is consistent with the code version of the audit.
2. Code open source:
1) View whether the code of the project is open source. The open source code allows communities and security experts to review, which helps to discover potential security issues.
2) The background of the development team: Understand the background and experience of the project development team, especially their experience in blockchain and security, as well as the team’s transparency and public information level.
3) Vulnerability Bounty Plan: Whether the project has a vulnerability bounty plan to motivate security researchers to report the loopholes.
3. Finance and economic security
1) Fund lock quantity: Check the amount of funds locked in smart contracts, and a higher locking may mean a high degree of trust in the project.
2) Transaction volume and liquidity: Evaluate the volume and liquidity of the project, low liquidity may increase the risk of price manipulation.
3) Tokens Economic Model: Evaluate the token economic model of the project, including token distribution, incentive mechanism and inflation model.For example, there are excessive concentrated tokens holding, and so on.
4. Operation and management safety
1) Governance mechanism: Understand the governance mechanism of the project, whether there is a centralized governance mechanism, and whether the community can vote for important decisions, and analyze the distribution of tokens and the concentration of voting rights.
2) Risk management measures: Whether the project has risk management measures and emergency plans, how to deal with potential security threats and economic attacks.In addition, in terms of project transparency and community communication, you can see that the project party can not regularly release project progress reports and security updates, and whether to actively communicate with the community and solve user problems.
5. Market and community evaluation
1) Community activity: Evaluate the community activity and user foundation of the project. Active community usually means that the project has extensive support.
2) Media and social media evaluation: Analyze the evaluation of projects in the media and social media, and understand the views of users and industry experts on projects.
3) Partners and investors: View whether the project has well -known partners and investors support. The reputable partner and investors can increase the credibility of the project, but this can become the decisive factor in judging its safety.
Q4: How should users look at the audit report, open source status and so on?
BlocksecSecurity team:For projects that have been audited, the project party usually actively announces the audit report to the community on official channels.These audit reports are usually in the project party’s documents, GitHub code libraries and other channels.In addition, the authenticity and identification of the audit report is needed. The method of identifying includes the digital signatures of the inspection audit report and the second confirmation of the audit company.
So how do investors study such audit reports when they get such audit reports?
First, it depends on whether the audit report has been audited by some security companies with high security reputation, such as Open Zeppelin, Trail of Bits, BlockSec and other head audit companies.
Second, it depends on whether the problems mentioned in the audit report have been repaired. If it is not repaired, it depends on whether the reason for the project party is not fixed.Here we also need to distinguish the valid vulnerability reports and invalid vulnerabilities in the audit report.Because the audit report has no unified industry standards, the security audit company will conduct project vulnerabilities risk rating and reports based on their own safety cognition.Therefore, the loopholes found in the audit report must focus on the effective vulnerability report.This process is best to have its own security consulting team introduced to conduct third -party independent evaluation.
Third, it depends on whether the audit time in the audit report published by the project party is consistent with the upgrade and update time of the recent project (or close). In addition, it is necessary to pay attention to whether the project party code in the audit report covers all the code of the project party’s current online code.EssenceFor the consideration of economic and time costs, the project party usually conducts some code audit.Therefore, in this case, it is necessary to determine whether the audited code is the core protocol code.
Fourth, it depends on whether the code running on the line of the project has been verified (open source) and the verified code is consistent with the audit report.Generally, audit will be based on the project party’s github (rather than the code that has been deployed online).If the project’s final deployment on the chain is not open source, or it is largely different from the audited code, it is a point that needs to be paid attention to.
In short, reading the audit report itself is a very professional thing. It is recommended to introduce independent third -party security experts in the process to provide consulting opinions.
Okx web3Wallet safety team:Users can use the official website of the DEFI project or third -party website, such as OKLINK to view the audit report and open source status of smart contracts. The steps of commonly viewing project audit reports and open source status are introduced below:
First, find the official announcement or website.Most credible DEFI projects will display their related document information on their official website. On the project document page, there will usually be a “security”, “audit” or “contract address” and other pages to the audit report and the project party deploymentThe contract address.In addition to the official website of the project party, it usually shows the audit report and deployment of contract address information on official social media such as Medium and Twitter.
Second, after reading the official website of the project party, you can check the contract address information given by the project party through the OKLINK browser, and check the open source code information of the contract in the “contract” column.
Third, after getting the audit report and the open source code information of the project party, you can start reading the audit report of the project party. When reading the audit report, there is the following attention:
1) Understand the structure of the audit report and have a general concept for the content of the audit report. The audit report is roughly divided into profiles, problems, solutions, suggestions and audit results.
2) When reading the relevant content of the introduction, we need to pay attention to the scope and goals of the audit report audit. Generally, the audit report will marked the GitHub Commit ID submitted by the audit file.Essence
3) When reading the problems, solutions and suggestions and audit results found in reading, we need to focus on whether the project team has fixed the vulnerabilities found in accordance with the suggestion, and whether the project party has conducted follow -up auditThe problems are properly handled.
4) Compare multiple reports.If the project has been audited multiple times, check the differences between each audit report to understand the safety improvement of the project.
Q5: Hacker attack history and bounty plan, rightDefiReference value of project safety?
Okx web3Wallet safety team: Hacker attack history and bounty plan provides a certain reference value for the security assessment of the DEFI project, which is mainly reflected in the following aspects:
First, hacker attack history
1) Reveal historical vulnerability: Attacking history can show the specific security vulnerabilities of the project, allowing users to understand which security issues have been used in the past, and whether these problems have been completely repaired.
2) Evaluate risk management capabilities: How the project responds to the security incidents in history, which can reflect its ability to manage and deal with crisis.A project that actively responds, timely repair vulnerability and compensate users is usually considered as more reliable and mature investment options.
3) Project reputation: Frequent security issues may reduce users’ trust in the project, but if the project can show the ability to learn and strengthen security measures from errors, this can also build its long -term reputation.
Second, bounty plan
The implementation of the bounty plan in DEFI and other software projects is an important strategy to improve security and excavate potential loopholes.These plans bring multiple reference value for the safety assessment of the project:
1) Strengthen external audit: The bounty plan encourages global security researchers to participate in the project’s security audit.This “crowdsourcing” security test can expose problems that may be ignored internal audit, thereby increasing the opportunity to discover and solve potential vulnerabilities.
2) Validity of verifying safety measures: Through actual bounty plans, the project can test the effectiveness of its safety measures in actual combat.If the bounty plan of a project is longer, but the report is less serious, this may be an indicator that indicates that the project is relatively mature and safe.
3) Continuous security improvement: The bounty plan provides a continuous improvement mechanism.With the emergence of new technologies and new attack methods, the bounty plan helps the project team to update and strengthen its security measures in a timely manner to ensure that the project can cope with the latest security challenges.
4) Establish a security culture: whether the project sets up a bounty plan, and the seriousness and activity of the plan can reflect the project team’s attitude towards security.A positive bounty plan shows the project’s commitment to establish a solid security culture.
5) Improve the confidence of community and investor: The existence and effect of the bounty plan can prove to the community and potential investors that the project attaches importance to security.This can not only enhance user trust, but also attract more investment, because investors tend to choose projects that show high security responsibility.
Q6:participateDefiAt the time, how can users build monitoring perception capabilities
BlocksecSecurity team:Taking giant whale users as an example, giant whales mainly refer to the investment institutions of individual investors or small teams. These users have a large scale, but usually do not have a very strong security team and the ability to develop their own safety tools.Therefore, so far, most giant whales have not enough risk perception, otherwise they will not suffer such huge losses.
Due to the risk of huge losses, some giant whale users have begun to consciously rely on some open security tools to monitor and perceive risks.Now, many teams are doing monitoring products, but how to choose is very important.Here are a few key points:
First, the cost of use.Although many tools are very powerful, they need programming and the cost of use is not low.For users, it is not easy to understand the structure of the contract, and even collecting addresses.
Second, it is accuracy.No one hopes to receive a few alarms in a row while sleeping at night, and finds that it is a mistake, which will make people burst.Therefore, accuracy is also critical.
Finally, it is security.Especially under this scale of funds, we cannot ignore tool development and various security risks of its team.The recent Gala Game was attacked, which is said to have introduced unsafe third -party service providers.Therefore, reliable teams and credible products are essential.
As of now, many giant whales have found us. We will recommend a professional asset management plan for it, so that giant whale users can ensure the security of funds, but also take into account daily capital management such as “digging and selling” and perceive risks.Even funds retreating in emergency state.
Q7:participateDefiSafety suggestions and how to deal with safety risks
BlocksecSecurity team:For large -scale participants, participating in the DEFI agreement is to ensure the principal security, and invest in a comprehensive research on possible security risks.Fund safety can usually be guaranteed from the following aspects.
First of all, we must judge the security and investment of the project party in multiple aspects.Including whether the above is a thorough security audit, whether the project party has project safety risk monitoring and automatic response capabilities, whether it has a good community governance mechanism, etc.These can reflect whether the project party has a highly responsible attitude towards the security of user funds in a relatively important aspect and whether the user’s funding security is highly responsible.
Secondly, participants with large funds also need to build their own safety monitoring and automatic response system.After a security incident in the investment agreement, investors with large funds should be able to perceive and retreat funds as soon as possible to recover the losses as much as possible instead of pinning all hope on the project party.In 2023, we can see that many well -known projects have been attacked, including CURVE, Kyberswap, Euler Finance, etc.Unfortunately, we found that when the attack occurred, large investors often lacked time and effective intelligence, nor did their own safety monitoring and emergency retreat system.
In addition, investors need to choose better security partners to continue to pay attention to the safety of investment project standards.Whether it is the upgrade of the project party code, important parameter changes, etc., you need to be able to perceive and evaluate the risk in time.And such things are difficult to complete without the participation of professional security teams and tools.
Finally, you need to protect the security of the private key.For accounts that need to be traded frequently, it is best to use the combination of online signing and offline private key security solutions to prevent the single -point risk after the loss of a single address and a single private key.
What should I do if the project is facing security risks?
It is believed that for any giant whale and investors, the first reaction to encounter a security incident must be the first to protect the capital.However, the speed of attackers is usually very fast, and manual operation is often too late, so it is best to automatically withdraw the capital according to risks.At present, we provide related tools that can automatically withdraw capital after discovering attacks and help users prioritize evacuation.
Secondly, if you really encounter losses, in addition to learning, you should also actively promote the project party to seek the help of a security company and trace back and monitor damage funds.As the entire Crypto industry attaches great importance to security, the proportion of recovery of funds is gradually increasing.
Finally, if it is a large household, you can also ask the security company to take stock of other projects to invest in similar problems.Many attacks of ROOT CAUSE are consistent. For example, the accuracy loss of Compound V2 has similar problems last year and was continuously attacked.Therefore, you can ask the security company to analyze the risks of other projects in the investment portfolio. If the risk is found, you should communicate or withdraw from the project party as soon as possible.
Okx web3Wallet safety team:When participating in the DEFI project, users can take multiple measures to participate more securely to participate in the DEFI project, reduce the risk of capital loss, and enjoy the benefits brought by decentralized finance.We are expanded from the user level and the OKX Web3 wallet.
First, for users:
1) Choose audit projects: Preferentially selects projects that have been audited by well -known third -party audit companies (such as Consensys Diligence, Trail of Bits, OpenZeppelin, QuantstamP, ABDK audit projects, review their public audit reports to understand potential risks and vulnerability repair.
2) Understand the project background and team: By researching the white paper, official website and development team background of the project, ensure that the project is transparent and credible.Pay attention to the activities of the team in social media and development communities, and understand their technical strength and community support.
3) Disposal investment: Do not invest all funds into a single DEFI project or assets, decentralized investment can reduce risk.Select multiple DEFI projects of different types, such as borrowing, DEX, Farming, etc. to decentralized risk exposure.
4) Small tests: Before a large amount of transactions, make a small test transaction to ensure the safety of operations and platforms.
5) Regular monitoring accounts and emergency treatment: regularly check your own DEFI account and assets, and timely discover abnormal transactions or activities.Use tools (such as EtherScan) monitoring chain trading records to ensure asset safety.After detecting abnormalities, take emergency measures in time, such as revoking all the authorization of the account, contacting the wallet safety team to obtain support.
6) Use new projects with caution: Keep cautiously for new projects that are just online or unbelievable.You can invest a small amount of funds for testing to observe its operation and safety.
7) Use mainstream Web3 wallets for transactions: Only the mainstream Web3 wallet interacts with the DEFI project. The mainstream Web3 wallet provides better security protection.
8) Prevent fishing attacks: Carefully click on strange links and emails that are unknown. Do not enter private key or notes on unbelievable websites to ensure that the access to access is the official website.Use official channels to download wallets and applications to ensure the authenticity of the software.
Second, from the level of OKX Web3 wallet:
We provide a lot of security mechanisms to protect user funds:
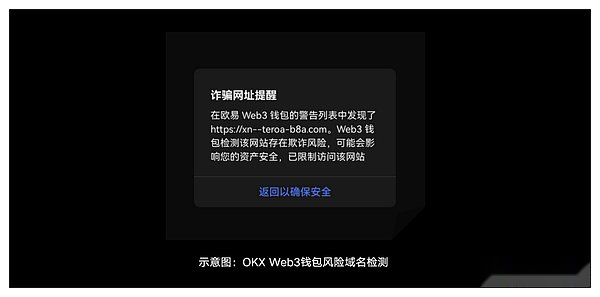
1) Risk domain name detection: When users access DAPP, OKX Web3 wallets will be detected and analyzed at the domain name. If the user accesses malicious DAPP, it will intercept or remind users to prevent users from being deceived.
2) 貔貅 plate tokens test: OKX Web3 wallet supports a complete puppet token detection ability, actively shield the 貔貅 plate to the coin in the wallet, and avoid users trying to interact with the 貔貅 plate tokens.
3) Address label library: OKX Web3 wallet provides a rich and perfect address label library. When the user interacts with suspicious address, the OKX Web3 wallet will be alarm in time.
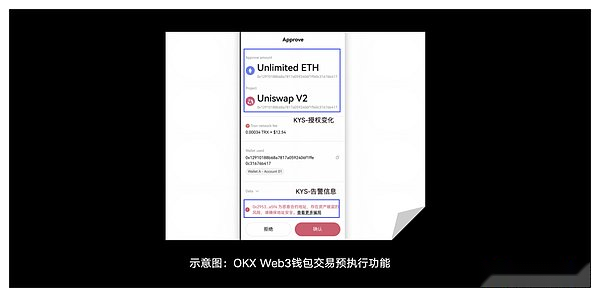
4) Trading pre -execution: Before the user submits any transaction, the OKX Web3 wallet will simulate the transaction and display the results of the assets and authorization to the user for reference.Users can judge whether they meet the expectations based on the results so that they can decide whether to continue to submit the transaction.
5) Integrated DEFI application: OKX Web3 wallet has integrated services for various mainstream Defi projects. Users can associate interact with integrated DEFI projects through the OKX Web3 wallet.In addition, OKX Web3 wallets also recommend paths for DEX, cross -chain bridge and other DEFI services to provide users with optimal DEFI services and optimal GAS solutions.
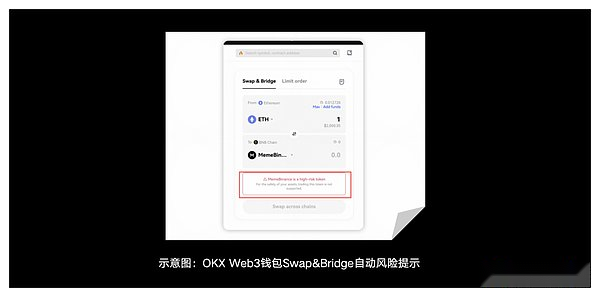
6) More security services: OKX Web3 wallets are gradually increasing more security functions, building more advanced security protection services, and better and more efficiently to ensure the safety of OKX wallet users.
Q8: Not only users,DefiHow to protect the risk of the project and how to protect it?
BlocksecSecurity team:The types of risks faced by the DEFI project include: code security risk, operating security risk, and external dependence risks.
First, code security risk.That is, the security hazards that may exist at the code level at the code level.For the DEFI project, smart contracts are its core business logic (front -end and back -end processing logic, etc. belong to traditional software development business, which is relatively mature). It is also the focus of our attention and discussion, including:
1) First of all, from the perspective of development, we need to follow the industry-recognized intelligent contract security development practice, such as for the CHCKS-EFFECTS-Interactions model for preventing the loopholes of the loopholes.The three -party library is realized to avoid unknown risks caused by repetitive invention wheels.
2) Followed by internal testing, testing is an important part of software development, which can help discover many problems.However, for the DEFI project, only local testing is not enough to expose the problem, but also requires further testing in the deployment environment close to the actual online. In this regard, it can be achieved by using tools like Phalcon Fork.
3) Finally, after the test is completed, it connects to a well -known third -party audit service.Although the audit cannot ensure that 100%do not have any problems, the systemic audit work can largely help the project party positioning various common safety issues, which are often unfamiliar with developers or because of different thinking methods.The part that is difficult to touch.Of course, due to the differences in professionalism and direction, if the budget permits, two or more audit companies are recommended to participate in practice.
Second, operate safety risks.That is, the safety risk of the project after the project is launched.On the one hand, the code may still have unknown loopholes.Even though the code has undergone good development, testing and auditing, there may still be unlimited security risks, which has been widely proven in the security practice of software development for decades; on the other hand, in addition to the problem of code levelAfter the project is launched, facing more challenges, such as private key leaks, system important parameter error settings, etc., can cause serious consequences and huge losses.Cope of operating safety risks include::
1) Establish and improve private key management: adopt reliable private key management methods, such as reliable hardware wallets or MPC -based wallet solutions.
2) Do a good job of running status monitoring: The monitoring system perceives the operation of special rights and the safety status of the project operation in real time.
3) Construct a automated response mechanism for risks: For example, the use of BlockSec Phalcon can automatically obtain blocking and avoid (further) losses when encountering attacks.
4) Avoid single -point risks for privileges operation: If you use SAFE to sign more wallets to perform privileges.
Third, external dependence risks refer to the risks caused by external dependencies existing in the project. For example, the price prophecy machine depends on other DEFI protocols, but the problem with the problem of the prophecy machine causes the error result of the price calculation.Suggestions for external dependence risks include:
1) Choose reliable external partners, such as the industry -recognized reliable head protocol.
2) Do a good job of operating status: Similar to operational safety risks, but the monitoring object here is external dependencies.
3) Construct a automated response mechanism for risks: similar to operating safety risks, but the disposal method may be different, such as switching spare dependencies instead of directly PAUSE’s entire protocol.
In addition, for the project party who wants to build a monitoring ability, we also give some monitoring suggestions
1) Accurately set monitoring points: Determine which key states (variables) and which locations need to be monitored. This is the first step in building monitoring capabilities.However, the setting of the monitoring point is difficult to cover comprehensive, especially in attack monitoring, it is recommended to use an external professional third party and actual inspection attack detection engine.
2) Ensure the accuracy and timelyness of monitoring: the accuracy of monitoring means that there must be not too many misunderstandings (FP) and omissions (FN).The prerequisite for response (for example, whether it can be detected before the suspicious contract deployment and the attack transaction is detected), otherwise it can only be used for post -post analysis, which has extremely high requirements for the performance and stability of the monitoring system.
3) Need to automate response capabilities: Based on precise and real -time monitoring, it can build automated responses, including the PAUSE protocol blocking attacks, and so on.Here is a customized and reliable automation response framework support. You can flexibly customize the response strategy according to the needs of the project party and automatically trigger the execution.
In general, the construction of monitoring capabilities requires professional external security suppliers to participate in the construction.
Okx web3Wallet safety team:There are many risks in the DEFI project, which mainly include the following categories:
1) Technical risk: It mainly includes smart contract vulnerabilities and network attacks.Protective measures include a third -party audit company with security development and hiring professional audits to conduct comprehensive audit of smart contracts, set up vulnerability bounty plans to motivate white hats and hackers to discover vulnerabilities, and to improve the security of assets to improve funds.
2) Market risk: mainly include price fluctuations, liquidity risks, market manipulation and combined risk.Protective measures include the use of stable currency and risk hedging to prevent price fluctuations, use liquidity mining and dynamic cost mechanism to deal with liquidity risks, strictly review the types of assets supported by the DEFI protocol and use decentralized prophecy machines to prevent market manipulation.Innovate and optimize protocol functions to deal with competitive risks.
3) Operating risk: It mainly includes human errors and governance mechanism risks.Protective measures include establishing strict internal control and operating processes to reduce the occurrence of artificial errors, use automated tools to improve operating efficiency, and reasonable design governance mechanisms to ensure decentralization and security balance, such as introducing voting delay and multiple signing mechanisms.And make a good monitoring and emergency plan for the online projects. Once abnormalities occur, you can immediately take measures to minimize the loss.
4) Regulatory risk: Law compliance requirements and anti -money laundering (AML)/understand your customer (KYC) obligation.Protection measures include hiring legal advisers to ensure that the project meets the requirements of law and regulatory, establish a transparent compliance policy, and actively implement AML and KYC measures to enhance the trust of users and regulators.
Q9TheDefiHow to judge and choose a good audit company?
BlocksecSecurity team:How does the DEFI project party judge and choose a good audit company. There are some simple standards for reference here:
1) Whether to audit well -known projects: This indicates that the audit company is recognized by these well -known projects.
2) Whether the audit items have been attacked: Although theoretically, audit does not guarantee 100%of the security, but most of the projects audited by the audited company with good reputation have not been attacked.
3) Through the quality of auditing through past audit reports: Audit report is an important symbol to measure the professionalism of the audit company. Especially when the same audit items and the same audit scope can be compared, they can focus on the quality of vulnerability (harmfulness (harmful harmAccording to the degree), quantity, etc., the vulnerability found whether it was usually adapted by the project party.
4) Professional practitioners: The composition of the audit company, including academic qualifications and employment backgrounds. Systemic education and experience experience are greatly helpful to ensure the quality of audit.
Finally, thank you for watching the 05th issue of the OKX Web3 Wallet “Safety Special issue” column. At present, we are preparing the content of the 06th issue. Not only are there real cases, risk identification, but also safe operation dry goods, so stay tuned!
Disclaimer:
This article is for reference only. This article has no intention to provide (i) investment recommendations or investment recommendations; (ii) the request or recruitment of digital assets to purchase, sell or hold digital assets;Holding digital assets (including stable currency and NFTS) involves high risk, and may fluctuate sharply, even as worthless.You should carefully consider whether transactions or holding digital assets are suitable for you according to your financial situation.Please be responsible for understanding and obeying relevant local application laws and regulations.








