
Thank you: Thank you Momir, XINSHU’s precious modification of the article
>
TL; DR:
-
The changes in Bitcoin cores are usually resisted. The reasons include: A) Compared to a currency, people prefer Bitcoin as value storage.b) Attach importance to stability and predictability, rather than fast innovation.c) It is difficult to reach consensus in a diversified community.
-
Many items claim that there are methods to solve the scalability of Bitcoin and do not need to change the Bitcoin chain itself.Recently, we witnessed the super inflation of Bitcoin “L2S”.
-
Although many claims are only misleading marketing, we also recognize a new computing paradigm that can bring programming to Bitcoin -BITVM.
-
The best expansion solution that BITVM can support is close to the security assumptions of the OP-Rollup type (although there are some additional precautions).
-
The success of Bitvm and similar initiatives depends on the feasibility of technology, the support of the community, and the distinction between other “excessive marketing” projects.
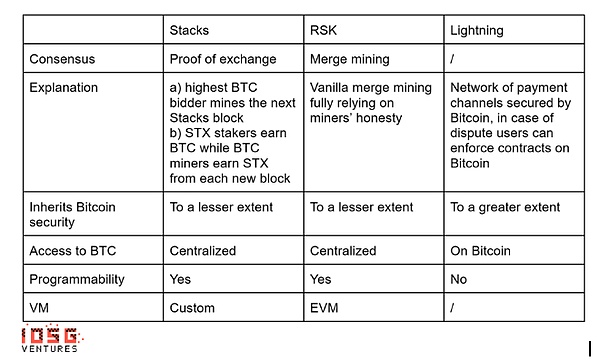
Bitcoin is built as a trading blockchain, and its script language intentionally limits as stateless to minimize the attack surface and ensure network security.Due to the lack of Turing-Completeness, it is impossible to introduce smart contracts directly on the blockchain unless the core of Bitcoin is upgraded by a bimedia.
The traditional Bitcoin community is resistant to changes. The reason is as follows:
-
The narrative pays more attention to value storage instead of inacular currency: the Bitcoin community intends to focus on maintaining the network as a point -to -point payment system, and puts security and decentralization on rapid development.As the famous Bitcoin holder Michael Saylor said: “No one tries to use a small part of them to buy a cup of coffee on one part of a building on the fifth avenue.”Tools rather than daily currency use preferences.
-
The stability of the system is better than innovation: For assets that are regarded as excellent value storage, predictability is essential.For example, even if the network has only 10 major upgrades, and the success rate of each upgrade is 90%, the probability of one failure is about 65%!According to the theory of normal accidents: “In complex systems, we should expect small factor that can often be ignored occasionally cause major events. Therefore, the goal of the Bitcoin community has always been a way to reduce potential errors.
-
Diversified communities: Many Bitcoin holders understand Bitcoin from different angles and cherish it for different reasons.Reaching a consensus in a diversified and decentralized community is full of challenges, which further slows the pace of innovation.To explain the diversity of the Bitcoin community, you can observe the response of the community to the inscription and Ordinals.When a part of the Bitcoin community celebrates the success of the order, it is regarded as the time of Bitcoin’s Cryptokitties, and the other person thinks that this is a loophole that should be repaired.
>
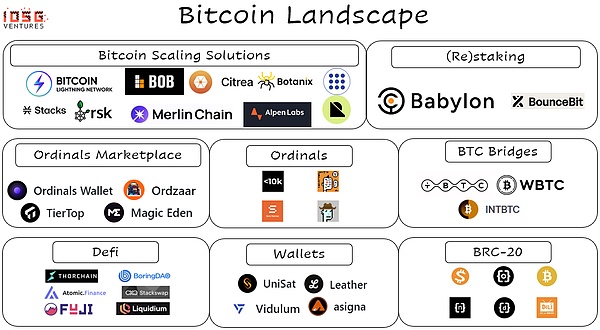
1. The rapid expansion of the Bitcoin capacity expansion scheme
In view of the above situation, why suddenly appear a large number of new Bitcoin “L2” solutions?
Recent
-
Side chains like Stacks provide smart contract capabilities and extensive application scope. Although they have an independent consensus mechanism, these mechanisms are difficult to obtain extensive acceptance.
-
Clients such as RGB verification projects use the UTXO model of the main network to make more complex transactions under the link, but their interaction with Bitcoin’s main network lacks stability.
-
The state channel like Lightning Network is closely related to the core Bitcoin developers and is considered a more orthodox tolerance method.
-
BITVM does not require a change of fork or any Bitcoin protocol.
-
Bitvm does not make Bitcoin blockchain blockage, because calculations are not performed on Bitcoin, but only use the Bitcoin network to verify when there are disputes.
-
>
-
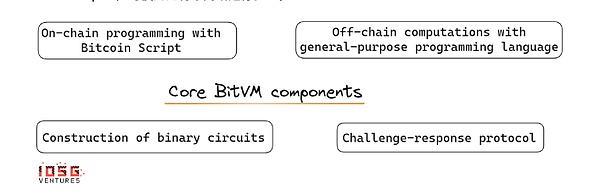
If Vicky stops challenge, it shows that Paul has received Paul, and Paul finally gets funds after a certain period of time.
-
If Vicky proves that Paul is inconsistent in execution (vaguely), she can ask for these funds.
-
If Vicky suspects the other part of the execution is wrong, she can initiate another challenge to move the funds to the next response address.To this end, she must reveal a image of a specific tableaf. Paul then needs to use it to unlock the funds and prove his correctness within a limited time.
-
Although BITVM can theoretically perform complex chain programs, in fact, with the increase of the complexity of the programming programs under these links, the relevant cost of performing fraud proves on Bitcoin has increased rapidly.Excessive programs may require multiple blocks to perform, further complicated this process.
-
Mining pools with computing power can be stolen from BITVM (similar to the Lightning Network), because they can conspire to review the certification of challengers, or malicious actors can bribe them to ignore the challengers.
-
Due to the interactive nature of BITVM, malicious proofs may manipulate the system and steal it from the verification.Attack can be constructed according to the following assumptions:
-
The proofer starts to verify the sequence through starting the transaction
-
Verification of suspicion proofer’s behavioral validity starts a challenge, which contains the response fee that pays the proofer in the challenge
-
Provers choose to collect costs, at the same time ignore the challenges, and do not fulfill some of their responsibilities in the verification process
-
In the end, Bitvm is currently a conceptual framework and a virtual computer concept that is almost impossible to perform any operation.The “convolution” of Bitvm is far from the application level. Optimism is estimated to see some Bitvm programs in 2025 in 2025.The technical risk of performing BITVM cannot be underestimated.
-
“Bitcoin Audible.”
-
“Bitvm.”
-
“Bitvm: Uma Ferramenta Para Contratos AINDA MAIS Inteligentes -Super Testnet -Satsconf 2023 -YouTube.” /watch? v = IEM_TXMJYXA.
-
Linus, robin. “Bitvm: Compute Anything on Bitcoin,” N.D.
-
“What is bitvm? With robin linus and super testnet (SLP520) -Youtube.”
-
DEEP DIVE Into Bitvm -Computing Paradigm to Express Turing- Complete Bitcoin. NG-PARADIGM-TO-EXPRESS-TRING-COMPLETE-BITCOIN-Contracts-1c6cb05edfca
-
Coinex Institution: Bitvm, The Potential of Smart Contracts on the Bitcoin Mainnet https://www.busines-standard.com/Content/Press-ani/Coinex-institu Tion-Bitvm-the-Potential-OF-Smart-Contracts-On-the-Bitcoin-Mainnet-123122500619_1.html
>
The first generation of BTC expansion solution
Compared with the existing solutions, what are the novels of the recent expansion method?In our opinion, the most exciting innovation comes from the encoding program on Bitcoin (via BITVM) and no need to trust BTC (such as Babylon).This article will focus on the former.
>
>
2. BITVM -Overview
To explain what Bitvm is, we should first introduce empowerment and stimulate its Primitive -Bitcoin Taproot upgrade.
Taproot is a major upgrade of the Bitcoin agreement and activated in November 2021.Through Taproot, the hash of the script must be submitted on the chain by default.When performing a path of the script, you only need to submit the script on the path to the chain.This not only improves efficiency (the size of the transaction will not increase with the size of the script), but also enhances privacy (it will only expose the path of the transaction, not the entire script).
With a huge opportunity for Taproot to upgrade, Robin Linus took the lead in launching Bitvm, which is a breakthrough innovation in the Bitcoin ecosystem.
BITVM is a computing paradigm. It uses Taproot to upgrade without changing the network consensus rules, and promote the realization of Turing -ling contracts on Bitcoin.It allows verification (instead of executing), similar to Optimistic Rollups.
Bitvm is minimized on the chain by enabling the complicated chain by enabling the complicated chain (only when the dispute is only required when there is a dispute only when there is a dispute).
This process involves the binary circuit that submits the program in the Taproot address and uses the challenge-response mechanism to verify.In summary, BITVM implements the complete Bitcoin contract of Turing, the most important thing is:
Construct a binary circuit on Bitcoin
The construction of binary circuits is a method that uses binary logic doors (such as AND, OR, not, not) to perform calculations or programs, which can perform any calculated functions.
BITVM is like the logical door of the current through the computer chip (these tiny structures are based on the existence of the current, determine whether the signal passes, that is, the complex simulation of opening or turning, or closed), and converts into the language of Bitcoin.
In essence, any computer program, from games to complete Linux operating systems, is the result of the complex arrangement of these logical doors. All digital things are basically based on binary numbers -0 and 1.By combining these binary numbers with logic doors (such as AND and NOT doors), we have created various circuits, including arithmetic logic units (Alus) and memory systems.This basic technology enables us to write and perform procedures to perform extensive tasks.
>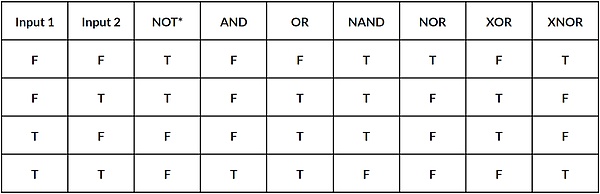
Source: Stepping Through Logic Gates; Basic Logic Gate (F represents 0, T represents 1)
The premise of Bitvm is to use Bitcoin Script to make a promise to calculate under the chain (submit a calculated hash to the Taproot address), and to form a combination of binary circuits by solving any program and enable execution verification.The process includes Bitcoin script, butThe script itself does not perform the entire calculation logicEssence
Bitcoin script can achieve Bit-Value Commitments, which can be displayed and punishedEquivocationThe behavior is very important.It realizes uncomfortable because it allows individuals to submit the value that others cannot modify.
This method involves the use of two hash to represent each input position: one hash for digital 0 and the other for numbers 1.When someone wants to execute the program, they reveal an original image (Pre-Images) to indicate the input.The value will be converted to 0 or 1, which is determined by comparing the hash values of the original image with the two hash values of representatives 0 and 1.
If the input and output are not matched, the verifications have the right to punish the provider by confiscating the funds of the provider.
Challenge-response mechanism
Verification is usually inUnder the chainPerforming, optimistic assumes that the proof of the proof is honest.In the case of controversy, the process is transferred to the chain, andStart a round of challenge-responseEssenceThis mechanism ensures that in most cases, calculation and verification can be carried out efficiently and at low cost, and only when there is differences, the unspeakable and transparency of the blockchain needs to be used for final ruling.
The dynamic of the challenge-response mechanism in Bitvm involves a system that verify the execution of the program on the blockchain (such as Vicky and Paul).When there is a dispute, Vicky challenges Paul to prove the correctness of his program execution.
Vicky selects a logical door from a binary circuit, and Paul opens this door by revealing the input and output.Until confirming the vague situation or Vicky exhausted the possibility of further challenges, this process will be repeated.Vaguely said that Paul claims that an input X was 0 when a logical door was opened, but it was 1 when another logical door was opened.
Paul needs to deposit funds to ensure the evidence he claims by using the pre -sign -nickname transactionEssenceThese transactions have created a chain that allows proceeding based on the ongoing interaction, and the funds are swinging between challenges and response addresses.
The funds in the response address can flow along multiple paths according to the results of the challenge:
This system provides a solid and transparent structure for the execution of disputes and verification procedures on the blockchain.By combining financial incentives, it promotes the integrity and accuracy of execution and program results.Initially, the design supported the challenge-response mechanism of the two parties.However, as we will show later, the contributors of Bitvm have found a solution to allow many participants to participate as challengers.
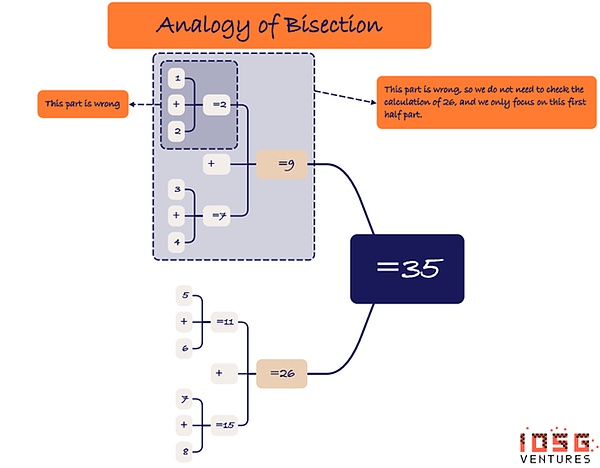
Bisection: Improve the efficiency of dispute resolution
In order to improve the efficiency of the verification on the chain, the verificationrs can use the bisection method, which is a method of high -efficiency search on the logical door that is submitted in advance to find the logical door that should be challenged.The challenge process has improved significantly.By dividing the problem of the problem into two, the division method allows the verification to quickly reduce the scope of the potential error, thereby reducing the steps and time required to solve the dispute.This method provides a more efficient and direct path when processing the complex verification process, especially when the error location needs to be accurately determined.
In the following, we use a simplified example to explain how the division method works:
Paul and Vicky are doing mathematical questions, the title is calculation ((1+2)+(3+4))+((5+6)+(7+8)).
The process of correcting this calculation is ((1+2)+(3+4))+((5+6)+(7+8)) = (3+7)+(11+15) = 10+26= 36.
The answer given by Paul is 35, because the way he calculates is ((1+2)+(3+4))+((5+6)+(7+8)) = (2+7)+(11+15) = 9+26 = 35.
When Vicky challenges Paul, she only needs to challenge the calculation involved in the first part of the calculation (that is, open the logic door), because they agree that the calculation of the second part is accurate ((5+6)+(7+8)) = 26)Essence
>
>
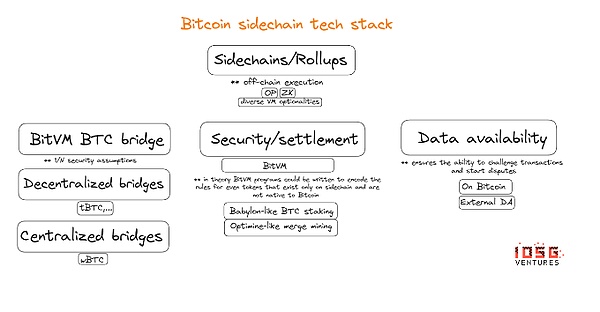
3. Use Bitvm to build a trusted bridge (Trust-Minimized Bridge)
Bitvm’s first actual implementation is likely to be a program that represents the minimum trust Bitcoin Bridge.By analyzing the details of the bridge, we can better understand the additional complexity of the Bitvm program.Below, we summarize the proposal of Alexei Zamyatin, co -founder of Bob.
First of all, you need to create a method that allows Bitcoin to use Bitcoin script to operate a side chain bridge program, including a side chain light client.
Then, you need to build oneLeague/Multi-SigThe network is facilitate the transfer of BTC and running challenges-response games.The alliance must promise to run the bridge as part of the BITVM settings.
The complexity of the initial settings of the alliance grows in a secondary growth with the increase of the number of members. Because each member of the alliance must interact with each member, the size of the alliance has a certain limit. Researchers speculate that n = 100 is the N = 100 is the N = 100 is the N = 100 is the N = 100 is the N = 100 is the N = 100 is the N = 100 is the N = 100 is the N = 100 is.Feasible.
>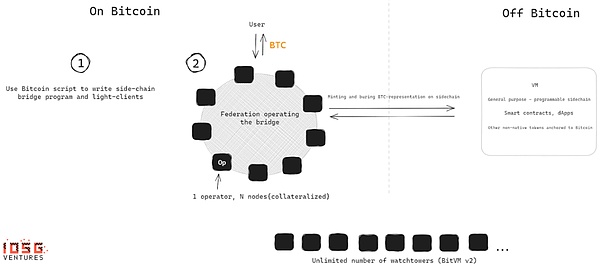
Unlike OP Rollup, the latter has no limit to the size of N, and the security assurance provided by this scheme is weak.However, the proposed work solution is likely to include rotation of alliance members, so that N will be greater than 100 within a long time range.At any time, as long as one of these 100 members is honest, the deposit will remain safe.Assuming those with malicious actors, they can be challenged at any time on the chain. If they are proven to cheat, they can be banned by the alliance.
Alliances are responsible for managing deposits and withdrawals and verifying the states of the side chain at any time.Both the operator and the monitoring tower (WatchTowers) need to submit mortgages to motivate correct behaviors and prevent false challenges.
Another reason why this scheme does not conform to the most stricter convolution is that users cannot unilaterally exit the side chain, but must request for withdrawal with alliances based on 1/N security assumptions.
>
4. Bitvm V2: Can BITVM support that Permisionless Verification (Permisionless Verification)?
On March 25, Robin Linus introduced Bitvm V2.The key change of the Bitvm V2 proposal is that the proofer needs to submit the output status and all intermediate results at one time, rather than open the logical door one by one in the process of challenge-verification.With this change, Bitvm ensures that any challenge to these commitments must be supported by encryption evidence.This mechanism filters out of the unfounded garbage challenges, because challengers must provide specific encryption certificates to controversial proofs.
By allowing unlimited participation in the verification and challenge process, BITVM 2 has expanded its security assurance to the restrictions of multiple signature alliances and make Bitvm closer to the security assumption of optimistic convolution.
However, the construction of the bridge still requires the multi -signature of the alliance to promote, which means that members of the alliance may cause activity problems. In the worst cases, they tried to extort their ransoms to users to thaw their funds.This is an additional security assumption for optimistic convolution, because in optimistic convolution, users can exit L1 without obtaining any intermediary approval.
>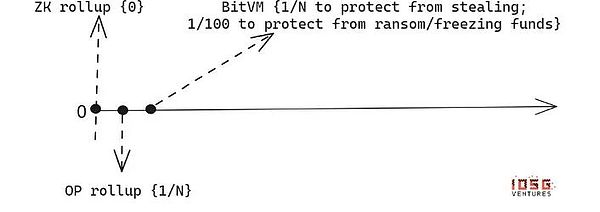
Extra security assumptions on the basic chain
>
5. Bitvm restrictions
As we discussed above, the best solution that Bitvm can provide is the security assumptions close to optimistic convolution.In addition to the complexity of the alliance responsible for insurance deposits and its activity issues, some additional complexity unique to BITVM includes::
>
6. Conclusion
Considering the valuation of the Ethereum expansion solution, the potential market value of about 15-20%of Ethereum’s market value-the potential market value of the second-layer solution of Bitcoin may be huge.
Although BITVM is still in the early stages -it is essentially an unscrupulous virtual computer concept -it has stimulated a lot of interests and statements from various projects, which are eager to use their potential.Many projects that have nothing to do with the Bitvm team are scrambling to make a grand announcement, hoping to occupy a place in a promising new field of Bitcoin in their opinion.However, more carefully reviewed a more sober reality: The GitHub account of Bitvm has only a few contributors, and only a few Bitvm Builders Telegram groups are actually involved in the group.
Any key principle that Bitcoin’s any scalability solutions must follow is that the core architecture of Bitcoin should remain unchanged (according to predictability principles).Bitvm adhering to this principle, becoming the first pioneer solution to provide a programmable layer on the Bitcoin without changing its core.
This article is written in the early stage of Bitvm development. Considering its rapid development, the information here is likely to be outdated.For example, until recently, the idea of realizing ZK convolution on Bitcoin seems to be as unrealistic as the empty tower, because the basic ability required -such as the ability of Bitcoin to verify the ZK certification -does not exist.However, recently Bitvm researchers shared the progress of the Bitcoin script, which may lead to the Stark verification device on Bitcoin.
The realization of Bitcoin expansion solutions surpasses pure technical challenges; it includes factors such as community support, user experience and timing.Although the current time provides a unique opportunity window for these innovations, the rapid inflation of the project’s number of projects and the significant risks brought by misleading statements and marketing may destroy the prospects of more legal projects.
As the ecosystem stands at this crossroads, the problem of whether the success of Bitcoin expansion solutions can copy Ethereum is not only technical, but also deeply rooted in the broader dynamics of the blockchain community.After all, the core Ethereum community has chosen L2 as the key part of the Ethereum expansion route diagram, and the Bitcoin community cannot say so.
Reference







