
Author: YBB Capital Researcher Zeke
TLDR
-
Agglayer is the core component of Polygon 2.0, which is a uniform and dispersed blockchain by aggregating and ensuring atomic cross -chain transactions.Its goal is to provide a seamless user experience of a single -chain level and solve the problem of liquidity and status of the existing blockchain ecosystem.
-
Agglayer uses a new type of verification mechanism called pessimistic proof. It assumes that all access chains are unsafe, and finally use zero -knowledge certification to ensure the correctness of cross -chain operations.
-
Agglayer is more concise and efficient, and its final form will achieve more ideal chain abstraction, which is more in line with the definition of the next generation of Web3.
1. Agglayer derived from the era of modularization
1.1 Agglayer Introduction
Agglayer is one of the core components of the Polygon 2.0. The Agg in its protocol name is the abbreviation of English words Aggregation. The full Chinese name is the polymerization layer.The role of this protocol is essentially the same as the full -chain interoperability protocols such as Layerzero and Wormhole. The purpose is to connect the fragmented blockchain world.However, in terms of constructive ideas, there are indeed some differences between the two. In popular terms, traditional all -chain interoperability protocols are more like a bridge -built engineering company to design and build bridges by different chains or protocols (The adaptation of the heterogeneous chain is difficult) to achieve interconnection.Agglayer is justified, and it is more similar to a “LAN” composed of an exchange machine. The connection chain only needs to insert “ZK Proof” to access the “LAN” and perform data exchange.Compared to crossing bridges everywhere, faster, more easy and better interoperability.
1.2 Shared Validity Sequencing
Agglayer’s thought is largely due to the design of Umbra Research on Shared Validity Sequeencing (sharing effective sorting), which aims to realize the atomic cross -chain interoperability between multiple Optimistic Rollup.By shared the sorter, the entire system can handle the transaction sorting and status roots of multiple Rollup in the entire system to ensure atomic and conditional execution.
The specific implementation logic needs to pass three components:
-
Accept the shared sorter of cross -chain operations: receiving and processing cross -chain transaction requests;
-
Block construction algorithm: shared sorters are responsible for building blocks containing cross -chain operations to ensure atomicity of these operations;
-
Share fraud certificate: Sharing fraudulent proof mechanisms between related rollups to enforce cross -chain operations.
-
Native currency.By using the unified bridge, the assets in the aggregation layer are native assets, without any packaging tokens, and no need for third -party trust sources to cross -chain, everything is seamless;
-
Unified liquidity.The TVL of all access chains is shared, or it can also be called a shared liquidity pool;
-
sovereignty.Compared with the Optimistic Rollup in the above Optimistic Rollup, Agglayer has better sovereignty, and Agglayer will be compatible with shared sorters and third -party DA solutions.The connection chain can even use its native token as GAS;
-
Fast.It is still a solution that is different from the above Optimistic Rollup. Agglayer does not need to wait for 7 days to cross -chain;
-
Safety.Pessimistic proof only accepts the right behavior. On the other hand, it also ensures that no chain can extract the amount of deposit, thereby ensuring the safety of the shared asset pool of the polymerization layer;
-
low cost.The more chain connected in the polymerization layer, the lower the certificate paid to the Ethereum, because it is average, and the Agglayer does not charge additional protocol fees.
-
Trustlessness: It does not need to rely on any centralized trust entity, and can provide the same level of security as the underlying blockchain.Users and participants do not need to trust any intermediaries or third parties to ensure the security and correct execution of the transaction;
-
Extensibility: Agreement can easily apply to any blockchain platform or network, and is not limited by specific technical architectures or rules.This allows interoperability solutions to support a wide range of blockchain ecosystems, not just a few specific networks;
-
Generalization (Generalizability): Agreement can handle any type of cross -domain data or asset transfer, not limited to specific trading types or assets.This means that through this bridge, different blockchains can exchange various types of information and value, including but not limited to cryptocurrencies, smart contract calls, and any other data.
-
Token exchange: allows users to trade certain assets on one blockchain and receive another equivalent asset on another chain.By using atomic swaps and cross -chain technology (AMM) technologies, the liquidity pool can be created on different chains, so as to achieve exchange between different assets.
-
Asset bridge: This method involves locking or destroying assets through smart contracts on the source chain, and unlocking or creating new assets through the corresponding smart contract on the target chain.This technology can be further divided into three types according to the method of processing assets:
-
Lock/cast mode: In this mode, the assets on the source chain are locked, and the target chain is cast on the equivalent “bridge asset”.Original assets;
-
Destroy/cast mode: Assets on the source chain under this mode are destroyed, and the same amount of equal assets are cast on the target chain;
-
Lock/unlock mode: This method involves locking assets in the source chain, and then unlocks equivalent assets in the liquidity pool on the target chain.Such asset bridges often attract liquidity by providing incentive measures such as income sharing.
-
Native Payment: Allow applications on the source chain to trigger the payment operation of native assets on the target chain. You can also trigger cross -chain payment on another chain based on data on one chain.This method is mainly used for settlement, which can be performed according to blockchain data or external events.
-
Intelligent contract interoperability: allow smart contracts on the source chain to use the smart contract function on the target chain according to the local data call, to achieve complex cross -chain applications, including asset exchange and bridge operations.
-
Programming Bridge: This is a high -end interoperability solution that combines the asset bridge connection and message transmission function.When the asset is transferred from the source chain to the target chain, the contract calls on the target chain can be triggered immediately to achieve a variety of cross -chain functions, such as equity pledge, asset exchange, or the assets stored in smart contracts on the target chain.
>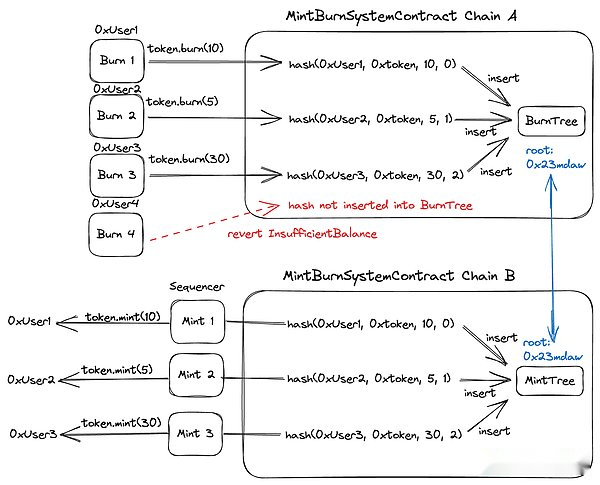
Because the current Rollup basically has the functions of two -way transmission messages between Layer1 and Layer2, as well as other special pre -compilation.So as shown in the figure above, UMBRA has only added a MintburnSystemContract contract (BURN and Mint) to make up the three components for complementing three components.
Work process
1. Burn operation on the chain A: any contract or external account can be called, and it is recorded to Burntree after success;
2. Mint operation on Chain B: The sorter records it to Minttree after the execution is successful.
Uncosty and consistency
Merkle root consistency: Burntree on chain A and the MIRKLEE root of Minttree on the chain B must be equal, so as to ensure the consistency and atomicity of cross -chain operations.
Under this design, Rollup A and B share a sorter.This shared sorter is responsible for publishing the trading batch and statement of the two Rollup to Ethereum.The shared sorter can be a centralized sorter, just like most Layer2 Rollup sorters, or decentralized sorters like Metis.The key to the entire system is that the shared sorter must publish the transaction batch and declaration status of the two Rollup in the same transaction to L1.
Share sorters receive transactions and build blocks for A and B.For each transaction on A, the sorter will execute the transaction and check whether it interacts with MintburnSystemContract.If the transaction is successfully executed and interacts with the Burn function, the shared sorter will try to perform the corresponding MINT transaction on B.If the Mint transaction is successful, the shared sorter will include Burn transactions on A and contains Mint transactions on B; if the Mint transaction fails, the shared sorter will exclude these two transactions.
In simple terms, the system is a simple expansion of the existing block construction algorithm.The sorter executes the transaction and inserts the conditions triggered from one rollup to another RollUp. When the main chain is used for fraud to verify the verification, it only needs to ensure that the combustion of the chain A and the casting of the chain B are correct (that is, in the above in the above (that is, in the above above.Merkle root consistency).In this case, multiple Rollups have become similar to a chain. Compared with a single Rollup, this design provides better sharding support, application sovereignty, and interoperability.The opposite problem is that the burden of node verification and the sorter is greater, and the probability of this scheme is still very low from various perspectives such as interest distribution and Rollups autonomy.
1.3 The core component of Agglayer
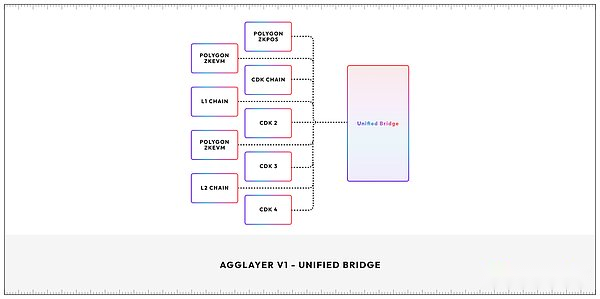
While absorbing the above solutions, Agglayer has made more efficient improvements and introduced two key components: unified bridge and pessimistic proof.
Unified Bridge: The workflow of the unified bridge is to collect and summarize the status of all access chains to the polymerization layer, and the aggregation layer regenerates the unified proof to Ethereum. In this processIn temporary state assumptions, faster interaction), confirmation (the validity of the certification submitted by the verification), and the final determination, and finally the certificate can verify the effectiveness of all access chains.
>
Pessimistic proof: Rollups accessing a multi -chain environment will produce two main problems: 1. The introduction of different verificationers and consensus mechanisms will lead to complicated security; 2. Optimistic Rollup’s collection takes 7 days.In order to solve these two problems, Polygon introduced a novel zero -knowledge certificate, that is, pessimistic proof.
The idea of pessimistic proof is that assuming all the blockchain connected to Agglayer may have malicious behaviors, and the worst situation of all cross -chain operations is assumed.Then, Agglayer uses zero -knowledge proof to verify the correctness of these operations to ensure that even if there are malicious behaviors, the integrity of cross -chain operations cannot be destroyed.
1.4 Features
Under this scheme, the following features can be achieved:
Second, cross -chain solution
2.1 Why is it so difficult to cross the chain?
As mentioned above, the purpose of Agglayer and the full -chain protocol is basically the same, so is the two?Before comparing, we may need to understand two questions first: 1. Why is it difficult to cross the chain? 2. What are the common cross -chain solutions.
Like the most famous public chain triangle problem, the cross -chain protocol also has interoperability triangle selection (Interoperability Trilemma). Due to the restrictions on the premise of decentralization, the blockchain is essentially a copy that cannot receive external information.machine.Although the existence of AMM and prophecy machine make up for the lack of DEFI, for the cross -chain agreement, this problem is dozens of times. From a certain perspectiveSo there are various packaging tokens such as XXBTC and XXETH.But the logic of this packaging tokens is very dangerous and centralized, because you need to lock the real BTC and ETH in the original chain address of the cross -chain bridge contract, and the design of the entire cross -chain may need to face the assets.The same, differentials caused by different virtual machines are not compatible, trust problems, dual -flower problems, delay issues and other problems.In order to efficient and reduce expenses, most cross -chain solutions actually use more wallet solutions.So even today, you can often see the information about XX cross -chain bridge thunderstorms.Now we have a detailed understanding of this problem from a lower level. From the perspective of the founder of Connext Arjun Bhuptani, the cross -chain agreement can only choose two of the following three key attributes to optimize:
Early cross -chain bridge division is generally prevailing on Vitalik and others. They divide cross -chain technology into three categories. Hash time locks, witness verification, relay verification (light client verification), but later based on the division of Arjun BhuptaniThe cross -chain scheme can be divided into native verification (no trust+ scalability), external verification (scalability+ generalization), and native verification (no trusitive+ generalization).These verification methods are based on different trust models and technologies to meet different security and interoperability needs.
Native Verify:
Local verified bridges rely on the consensus mechanism of the source chain and the target chain itself to directly verify the effectiveness of the transaction.This method does not require additional verification layers or intermediaries.For example, some bridges may use smart contracts to directly create verification logic between the two blockchains, allowing these two chains to confirm the transaction through their own consensus mechanisms.The advantage of this method is to increase security because it directly depends on the inherent security mechanism of participating chains.However, this method may be more complicated in technology implementation, and not all blockchain supports direct local verification.
Externally Verify:
External verification bridges use third -party verifications or verification clusters to confirm the effectiveness of the transaction.These verifications may be independent nodes, members of the alliance, or other forms of participants who run outside the source chain and target chain.This method usually involves cross -chain message transmission and verification logic, which are performed by external entities, not directly processed by the participating blockchain itself.External verification allows a wider range of interoperability and flexibility because it is not limited by a specific chain, but it also introduces additional trust layers and potential security risks.(Although there are great centralized risks, external verification is the most mainstream cross -chain method. In addition to flexibility and efficiency, it has both low costs)
Locally Verify:
Native verification refers to the status of the target chain of the target chain in cross -chain interaction to confirm the transaction and perform follow -up transactions locally.The usual approach is to run a light client on the source chain of the target chain virtual machine, or two in parallel.Native verification requires a small number of factions or synchronous assumptions. At least one honest relay (that is, an honest minority) in the committee, or if the committee cannot run normally, users must transmit transactions (that is, synchronous assumptions).Native verification is a cross -chain communication method with the highest degree of trust, but its cost is also very high, the development flexibility is low, and it is more suitable for blockchain with high status machine similarity, such as Ethereum and L2 networks.Between blockchain developed based on COSMOS SDK development.
The current cross -chain scheme “1”
Complaints in different aspects have also led to different types of cross -chain solutions. Except for verification methods.The current cross -chain solution can also be divided into multiple categories. They each adopt unique methods to achieve asset exchange, transfer and contract calls.
2.2 Agglayer is more advantageous in the future
Here we compare Agglayer to the current full -chain protocol and take the most influential Layerzero as an example.The protocol adopts an external verification improvement version, that is, Layerzero converts the source of trust in the verification into two independent entities -prophecy machines and relays to make up for the defects of external verification through the most minimalist way.The cross -chain solution belongs to a programmable bridge scheme that can achieve multiple operations.Logically, it seems to be simply cracking, so -called impossible triangle.From a magnificent narrative perspective, Layerzero has the opportunity to become the cross -chain hub of the entire Web3, and it is quite in line with the problems such as the splitting and liquidity of experience and liquidity of the under -chain explosion in the era of modularization.The main cause of crazy betting on the class protocol.
But what is the real situation?We will not talk about the recent lays operating operations of Layerzero on airdrops.From the perspective of development, it is actually very difficult to achieve the situation of the entire web3 in such an agreement, and the problem of decentralization is doubtful.In the early V1 version, the prophecy machine used by Layerzero actually had the possibility of being hacked and theoretically.Only the birth of decentralized verification network (DVN) calmed down the verbal word on social networks, but this is also based on a large number of B -end resources.
On the other hand, the development of the full -chain protocol also involves the problem of the protocol, data format and operating logic of the heterogeneous chain, and the calling of different smart contracts.To truly realize the mutual communication of Web3 not only requires its own efforts, but also the collaboration of various projects.If you use the early Layerzero, it should not be difficult to find that it basically only supports the EVM public chain cross -chain, and there are not many ecological projects that support the full -chain.This is also the same for Agglayer, but in terms of interoperability, Agglayer supports ultra -low delay and asynchronous interoperability, which is more like the Internet used on the Internet.
In summary, the Agglayer aggregation is a similar way to use, which is more concise, efficient and in line with the current modular wind direction.However, there is no absolute height between the two in the present. The full -chain protocol still has the broadest liquidity, ecology and stronger initiative, and developing more mature advantages.The advantage of Agglayer is that Layer1 and Layer2, which are hostile to each other, break the different public chain projects in the era of chain explosion, decentralized liquidity with zero -sum games with users, allow multi -chain low delay interaction, and native self -bringing chain chainAbstract, sharing liquidity pool does not require packaging tokens, which will be a very good opportunity for long -tail chains and application chains.So in the long run, Agglayer is the current most potential cross-chain solution. At present, similar projects in the development stage also include Polkadot’s “Join-ACCUMULATE MACHINE”.Now it has moved from a single film to the module, and the next step will be polymerized.
Third, ecology connected by Agglayer
Because in the early days, the Agglayer’s access chain was not many. Here we mainly mentioned three items:
3.1 x layer
X Layer is based on the Ethereum Layer2 project established by Polygon CDK. It connects the Euyi and Ethereum community so that anyone can participate in the truly globalized chain ecosystem.As a head exchange, it will bring extensive liquidity to the projects in the aggregate layer after accessing the Agglayer.The OKX Web3 wallet as the access layer of ordinary users may also provide better support for Agglayer.
>
3.2 Union
Union is a zero -knowledge infrastructure layer based on COSMOS. The project is used for general message transmission, asset transfer, NFT, and DEFI.It is based on consensus verification and does not depend on trusted third parties, prophecy machines, multiple signatures or MPCs.As an access chain, after entering the aggregation layer, the depth connection between EVM and COSMOS is implemented, because you only need to use the Union as an IBC gateway to connect Union and then connect to IBC, so that the modular ecosystem of the two separated by each other can be re -combined.
>
3.3 ASTAR
Astar Network is the network of Japanese and global companies, entertainment and game projects, and is committed to promoting “web3”.It provides customized blockchain solutions with a cross -virtual machine supported by Polygon and Polkadot.As the first complete integrated chain of Agglayer, this project will directly access tens of billions of dollars of liquidity sharing pools and achieve real user growth.
>
Reference
1. One article understands the blockchain interoperability: https://blog.chain.link/blockchain- interoperability- zh///
2.Agglayer: Why Polygon ’s Scalability Solution is a Game Changer in 2024 & amp; Beyond ?:
https://www.antiersolutions.com/agglayer-why-pointgons-scalability-solution-is-A-Game-in-2024-meyond/
3.The aggregation age is coming: https: //polygon.technology/agglayer
4.Shared value sequencing: https://www.umbraresearch.xyz/writings/shaRidity- sequencing
5.union: https: //www.rootdata.com/zh/projects/detail/union? K = mtaxmjy%3d 3d 3d 3d







