
Author: Faust & Wuyue, Geek web3
Introduction: American management scientist Lawrence Peter once proposed the “barrel theory”, which believes that the overall performance of a system is limited by its weakest part.In other words, how much water a barrel can hold is determined by the shortest board.Although this principle is simple, it is often overlooked.Previous debates on Layer2 security mostly ignored the priority and importance of different components, and basically focused on the reliability and DA issues of state transitions, but ignored more underlying and more important elements. In this way, the entire theoretical foundation may beNot tenable.Therefore, when we explore the complex system of multiple modules, we must first figure out which piece is the “shortest wooden board”.
Inspired by the barrel theory, after doing systematic analysis, we found that there are obvious dependencies between different components in the Bitcoin/Ethereum Layer2 security model, or that the security of some components is more secure than other components.Sex is more basic and more important, which is the so-called “shorter”.
In this regard, we can initially prioritize the importance/basicity of different components in the mainstream Layer2 security model as follows:
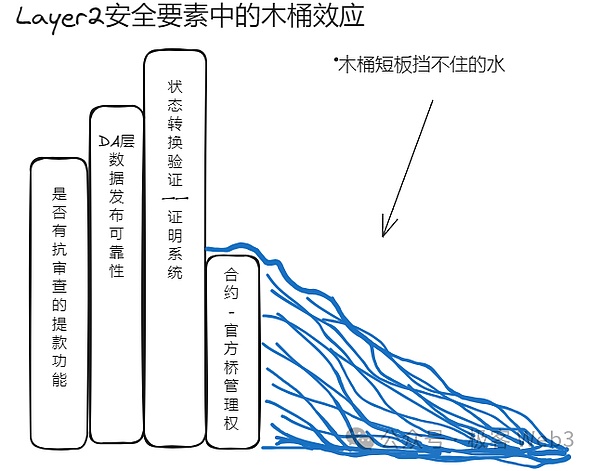
1. Whether the control authority of the contract/official bridge is reasonably distributed (multiple sign control rights are more concentrated)
2. Whether there is a withdrawal function that resists review (mandatory withdrawal, escape pod)
3. Is the DA layer/data publishing form reliable (whether DA data is published on Bitcoin or Ethereum)
4. Whether a reliable fraud proof/validity proof system is deployed on Layer1 (BitVM is required for Bitcoin L2)
We should moderately absorb the research results of Layer2 by the Ethereum community to avoid Lisenkoism
Compared with the highly orderly Ethereum Layer2 system, Bitcoin Layer2 is like a new world. This new concept that appears to be increasingly important after the inscription boom has shown its rising momentum, but its ecological system is becoming increasingly chaotic and trendy.In the chaos, all kinds of Layer2 projects emerged one after another, like mushrooms after a rain.While they bring hope to the Bitcoin ecosystem, they deliberately conceal their own security risks. Some people even threatened to “denie the Ethereum Layer2 and take the unique path of the Bitcoin ecosystem”, and have a great momentum to take the extremist route.
Considering the difference in functional attributes between Bitcoin and Ethereum, Bitcoin Layer2 was destined to be unable to align with Ethereum Layer2 in the early stages, but this does not mean that we should completely deny that Ethereum and even the modular blockchain world had a conclusion.Industry common sense (refer to the former Soviet biologist Li Senke, who took advantage of ideological issues to persecute Western genetics supporters.)
On the contrary, these judgment criteria obtained by the “predecessors” have already shown strong persuasion after being widely recognized. It is by no means rational to deliberately deny the value of these achievements.
While building Bitcoin Layer2, we should fully recognize the significance of “learning Western learning from the East” and moderately absorb and optimize many conclusions of the Ethereum community.However, when drawing on views outside the Bitcoin ecosystem, it is necessary for us to realize the differences in its starting points and ultimately seek common ground while reserving differences.
This is like exploring the similarities and differences between “Western people” and “Oriental people”.Whether it is Western or Eastern, the suffix of “people” expresses many similar characteristics, but when it corresponds to different prefixes such as “Western” and “Eastern”, the subdivided characteristics will be different.
But in the final analysis, there is a destined overlap between “Westerns” and “Orientals”, which means that many things that apply to Westerners are equally applicable to Easterners, and many things that apply to “Ethereum Layer2” are alsoThe same applies to “Bitcoin Layer2”.Before distinguishing the differences between Bitcoin L2 and Ethereum L2, it may be more important and meaningful to clarify the interconnection between the two.
Adhering to the principle of “seeking common ground while reserving differences”, the author of this article does not intend to discuss “what is Bitcoin Layer2 and what is not”, because this topic is too controversial, and even the Ethereum community does not regard “what is Ethereum Layer2 and what is not Layer2.”” and reach objective and consistent opinions.
But it is certain that while different technical solutions bring expansion effects to Bitcoin, their security risks are different. The trust assumptions in their security model will be the topic that this article intends to focus on.
How to understand the safety and evaluation criteria of Layer2
In fact, Layer2’s security is not a new point of discussion.Even the word security is a composite concept that contains multiple subdivided attributes.
Previously, the founder of EigenLayer simply subdivided “security” into four elements: “transaction irreversibility (rollback resistance), censorship resistance, DA/data release reliability, and state transition validity”.
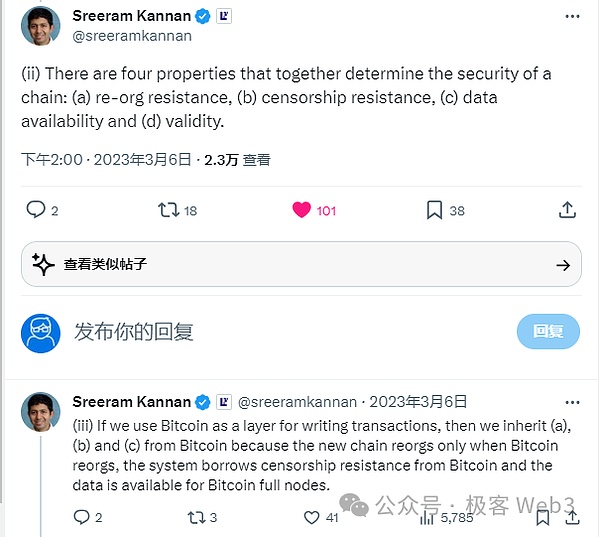
(The founder of EigenLayer once expressed his views on how the client verification/sovereign Rollup solution inherits the security of the Bitcoin mainnet)
L2BEAT and Ethereum community OG have proposed a relatively systematic Layer2 risk assessment model. Of course, these conclusions are aimed at smart contract Layer2, rather than typical non-smart contract Layer2 such as sovereign Rollup and client verification.
Although this is not 100% suitable for Bitcoin L2, it still contains many conclusions worthy of recognition. Most of its views have been widely recognized in Western communities.It also facilitates us to objectively evaluate the risks of different Bitcoin L2s.
(Vitalik once said that since the Rollup solution cannot achieve theoretical perfection at early start, some auxiliary means must be used to improve security, which are called “assisted wheels” and will introduce the assumption of trust.Trust assumption is risk)
So where do security risks come from?Considering that at present, whether it is Ethereum Layer2 or Bitcoin Layer2, many rely on centralized nodes to act as sorters, or “committees” in the form of side chains composed of a few nodes, these tend to be centralized sorters/committees.If it is not restricted, users’ assets can be stolen and run away at any time. User transaction requests can be rejected, resulting in the assets being frozen and unusable.This involves the state transition effectiveness and censorship resistance mentioned by the founder of EigenLayer.
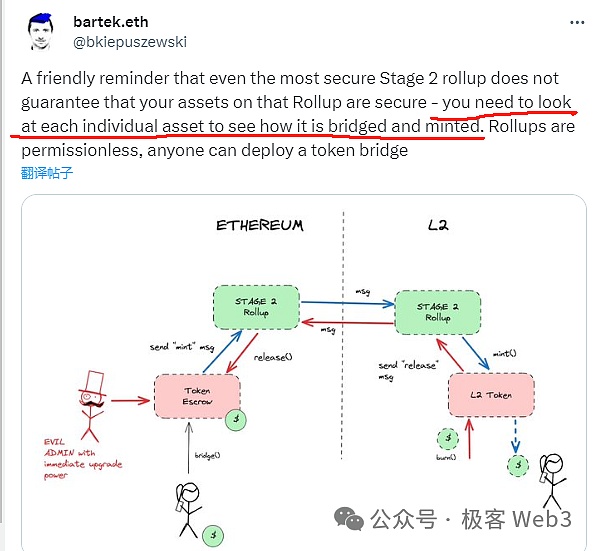
At the same time, since Ethereum Layer2 relies on contracts on the ETH chain for state transition verification and withdrawal behavior verification, if the contract controller (actually Layer2 official) can quickly update the contract logic and dopant malicious code segments (for example,Allow all the tokens locked on the L1-L2 withdrawal contract can be transferred away at a specified address, and the custodial assets can be directly stolen.
This is attributed to the “contract multiple sign allocation problem”, and the multi sign allocation problem also applies to Bitcoin Layer2, because Bitcoin Layer2 often relies on “notary bridge”, requiring multiple nodes to release cross-chain requests through multiple signs.Therefore, there is also a problem of how to allocate multiple signs in Bitcoin Layer2. We can even regard it as the most basic “auxiliary wheel” in Bitcoin Layer2.
In addition, the DA issue is also extremely important.If Layer2 does not upload data to Layer1, but chooses some unreliable DA publishing sites on its own, if this off-chain DA layer (usually known as the DAC Data Availability Committee) conspires to refuse to publish the latest transaction data outside, and the data hierarchy attack is caused by data hierarchy.This will lead to network scrapping and may make it impossible for users to withdraw money smoothly.
L2BEAT summarizes the above problems and summarizes several core elements in the Layer2 security model:
1. State Validation/prove the system’s reliability (State Validation)
2. Whether the DA data release method is reliable (Data Avalability)
3. If the Layer2 network deliberately rejects your transaction/downtime, can you forcefully withdraw your assets from Layer2 (Sequencer Faliure, Proposer Failure)
4. Layer2 related contract – whether the control of the official cross-chain bridge is sufficiently scattered.If the power is relatively concentrated and “guarding and theft” occurs, can the user have enough time to respond to the emergency (Exit Window)
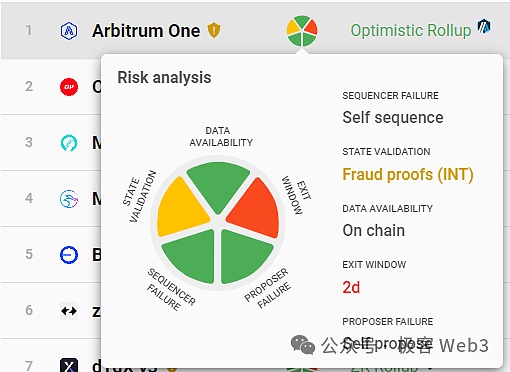
(“Risk Element Display Picture” set on L2BEAT for different Layer2 projects)
Anyway, when we analyze Layer2 security risks, we are actually discussing how many scenarios exist in the Layer2 network that may cause damage to user assets. For these dangerous situations, can the Layer2 system effectively restrict these dangerous situations through mechanism design.If certain malicious behaviors cannot be eliminated, how much “trust” we need to introduce, how many individuals in a group need to trust, and how many “auxiliary wheels” we need to rely on.
Below we will analyze the existing risk factors in the common Ethereum Layer2/Bitcoin Layer2 model (the objects mentioned in this article do not include “state channels” or “payment channels”, nor do they include the inscription index protocol, becauseThey are more special).And we will try to discuss which factors are more basic, underlying and more important in the Layer2 security model. These more basic shortcomings will be trust risks that are worthy of our attention than other shortcomings.
Layer2’s barrel effect – what are the shortcomings
The shortest board – the management rights of contract/official bridge
Here, we might as well use the “barrel effect” to analyze the security issues of Layer2. It is easy to see that the shortest wooden board is the “contract upgradeability” mentioned above (mainly for Ethereum Layer2), or go further.It is the “management rights of the official cross-chain bridge” (both Bitcoin and Ethereum Layer2 are applicable).

For Ethereum Layer2, as long as Layer2 official can quickly upgrade the contract on the Layer1 chain, it can theoretically steal the token locked at the L2 official bridge withdrawal address, no matter how reliable its DA layer or proof system is.
It can be said that the control authority of the bridge contract is related to the safety of the entire system. It is the most basic and critical part of the entire Layer2 and even the modular blockchain stack.If the bridge component/contract can be updated and iterated under multi-sign control, then we need to introduce the “trust assumption” here, assuming that the controller of the Layer2 contract/official bridge will not do evil.
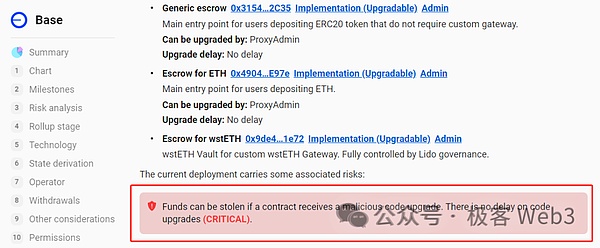
(L2BEAT has marked the contract upgrade delay of different Layer2 projects. Most L2 contracts can be upgraded by the controller immediately. If the contract controller wants to steal assets, or his private key is stolen by hackers, the user assets escrowed by L2 must be certainDisaster)
Unlike Ethereum Layer2, the bridge of Bitcoin Layer2 is basically not controlled by the contract on Layer1, because Bitcoin does not support smart contracts in the original state.Relatively speaking, the entire workflow of Ethereum Layer2 is highly dependent on the contracts on Layer1, and Bitcoin Layer2 cannot do so.
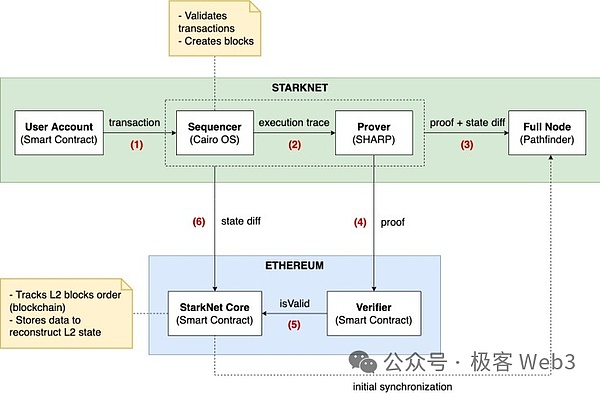
(Starknet schematic)
This is an unavoidable issue for Bitcoin Layer2, and it can be said that it has both advantages and disadvantages.At present, it seems that the “detrustworthy bridge” implemented by Ethereum Layer2 relying on contracts cannot be realized in Bitcoin L2.This “Trustless Bridge” requires the deployment of a dedicated contract on Layer1, and also requires the cooperation of the DA+ fraud proof/ZK proof system, which is essentially similar to the “optimistic bridge” of Orbiter or the ZK bridge of Polyhedra.
The mainstream view in the industry at present is that if you do not consider the possible bugs in practice and only consider the theoretical model, the security level of Optimistic Bridge and ZK Bridge is basically the highest, as long as the contract code does not contain bugs, or cannot be upgraded maliciously.Basically, it is trustworthy.
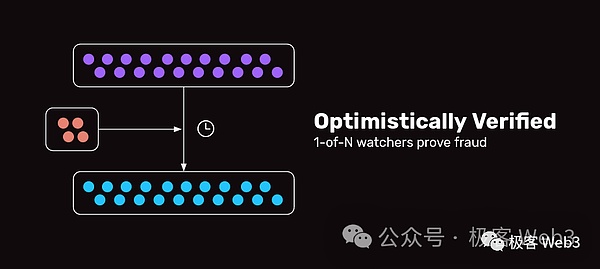
(Optimistic Bridge only needs to be done. Among the N Watchmen, 1 honesty can ensure safety. The trust model is 1/N)
Since Bitcoin Layer2 cannot deploy contract components on Layer1 (I won’t talk about Lightning Network here), its official bridges are basically “notary bridges” composed of a few nodes, or “multi-signature bridges”. The security of this kind of bridge isDepending on the way multi-signal/threshold signature is set, a strong trust assumption is needed: assuming that these notaries will not conspire or will not be stolen from private keys.
Currently, most bridges based on notary/threshold signatures cannot be compared with Ethereum Layer2’s official “trust-destructive bridge” (the premise is that Ethereum Layer2’s contract will not undergo malicious upgrades).Obviously, the asset security of Bitcoin Layer2 network hosting will be subject to the security of its official bridge, or the power dispersion of multiple signature bridges, which is its first “auxiliary wheel”.
Since the “upgrade permissions” of the official bridge of Ethereum Layer2 are often concentrated in the hands of a few more signing controllers. If the multi-signing controller conspires, there will be problems with the Ethereum Layer2 bridge, unless the contract is not possibleUpgrades, or subject to a long delay limit (currently only Degate and Fuel V1 are the case).
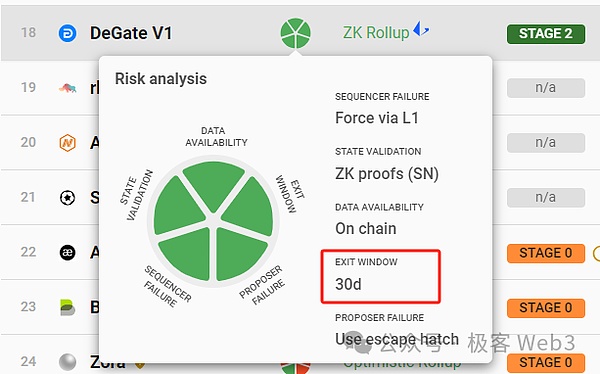
(Degate will reserve a 30-day safe escape period for users every time they upgrade the contract. During this period, as long as you find that the new contract code has malicious logic, you can safely escape through the forced withdrawal/escape pod function)
Regarding the “official bridge”, the trust model of Ethereum Layer2 and Bitcoin Layer2 is basically the same: the controller who needs to trust multiple signatures will not conspire to commit evil. This set of multiple signatures can control the L2 official bridge, or change its code logic.Or directly release an invalid withdrawal request, and the final result is: the user’s assets may be stolen.
The only difference between the two is that as long as the contract does not maliciously upgrade/upgrade window period is long enough, its official bridge is trustworthy, but Bitcoin Layer2 cannot achieve this effect no matter what.
The second short board – mandatory withdrawal of anti-censorship
If we assume that the issue of multi-sign/official bridge control mentioned above can be ignored, that is, there is no problem at this level, then the most important layer next is the censorship resistance of withdrawal behavior.
Regarding the importance of the anti-censorship mandatory withdrawal/escape pod function, Vitalik emphasized in his article “Different types of layer 2s” a few months ago that it is very important whether users can successfully withdraw their assets from Layer2 to Layer1.safety indicators.
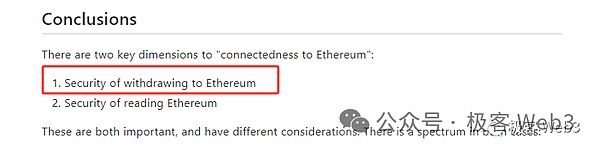
If the Layer2 sorter keeps rejecting your transaction request, or fails/downtime for a long time, your assets will be “freezed” and you can’t do anything.Even if the DA and fraud proof/ZK proof systems are available, such Layer2 is not safe enough without a censorship resistance and can seize your assets at any time.
What’s more, the Plasma solution, which once flourished in the Ethereum ecosystem, allows anyone to safely withdraw assets to Layer1 when DA is invalid or fraud proof is invalid.At this time, the entire Layer2 network is basically scrapped, but your assets still have a way to get rid of them.Obviously, the withdrawal function that is resistant to censorship is more basic and underlying than the DA and proof system.
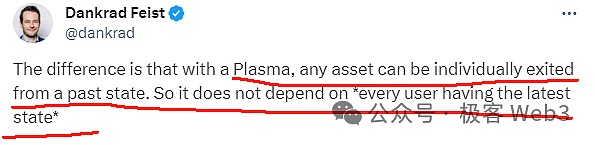
(Dankrad of the Ethereum Foundation said that Plasma can still allow user assets to be safely evacuated when DA failures/users cannot synchronize the latest data)
Some Ethereum Layer2, such as Loopring and StarkEx, dYdX, Degate, etc., will set up a censor-resistant force withdrawal/escape pod activation function on Layer1. Taking Starknet as an example, if the user submits a Forced Withdrawal request on Layer1,When the 7-day window ends, if the Layer2 sorter response is not received, you can manually call the freeze Request function to let L2 enter a frozen state and activate the escape capsule mode.
At this time, the sorter cannot submit data to the Rollup contract on L1, and the entire Layer2 will be frozen for one year.Then, the user can submit a merkle proof to prove his asset status on Layer2, and withdraw money directly on Layer1 (in fact, it is to take away his own equal amount of funds from the official bridge’s withdrawal address).
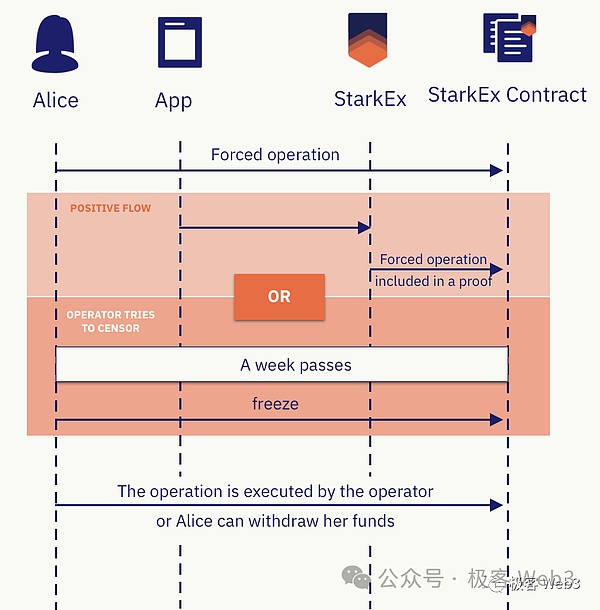
Obviously, the escape pod mode can only be implemented on a chain like Ethereum that supports smart contracts, and Bitcoin cannot run such complex logic.In other words, the escape pod function is basically the patent of Ethereum Layer2. Bitcoin Layer2 must use some additional auxiliary means to imitate it. This is the second “assistance wheel”.
But simply declaring a “mandatory withdrawal request” is much more convenient than directly activating the escape pole.The former only needs to ask the user to submit a transaction to the specified address on Layer1, and declare in the additional data of the transaction that he wants to submit to all Layer2 nodes (this can directly bypass the sorter and convey the request to other Layer2 nodes).If the “forced withdrawal” does not receive a response for a long time, the user will then trigger the escape pod mode, which is a relatively reasonable design.
(Reference: For Layer2, how important are the forced withdrawal and escape pod functions?
https://mp.weixin.qq.com/s/EheKZWDcJHYZ7vBZZPOMDA)
At present, the Bitcoin Layer2 team has planned to imitate Arbitrum’s forced transaction implementation method and allow users to issue Forced Transaction Envelopes on the Bitcoin chain.Under this solution, users can bypass the sorter and directly “transmit their voices” to other Layer2 nodes.If the sorter still refuses the user’s request after seeing the user’s forced transaction statement, it will be noticed by other Layer2 nodes and may be punished.
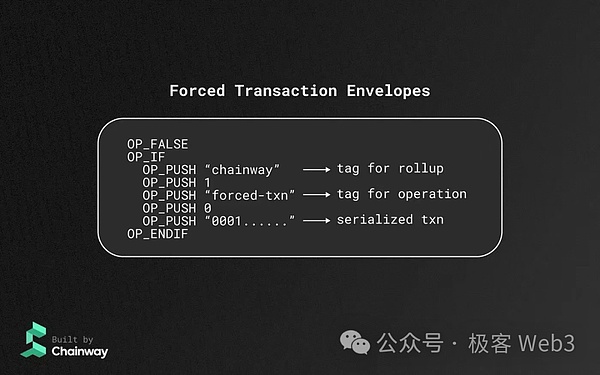
But the problem is that Arbitrum’s forced trading function, benefiting from its fraud proof system, can punish Sequencer/Proposer, which has always ignored user transactions.However, for Bitcoin Layer2, which is difficult to verify fraud proof on Layer1, it will encounter certain challenges in this regard.(Not discussing BitVM for now) If it is a sovereign Rollup solution with no big difference in security level and client verification, it is difficult for us to seriously evaluate its reliability, and it may be necessary to evaluate the implementation details of different projects.
Of course, given that many Bitcoin Layer2 currently operate in a form similar to side chains, it is equivalent to implementing a decentralized sorter, which can solve the problem of censorship resistance to a certain extent.But this is just an effective auxiliary means and certainly not the ultimate solution.
ps: Some Layer2 solutions now, such as Validium, are not perfect in the mechanism design of the escape pod. When the sequencer launches a data entrusting attack/DA is unavailable, users can’t withdraw money.But this is attributed to the incomplete design of Layer2’s escape pod. Theoretically, the optimal escape pod withdrawal can only rely on historical data and do not need to rely on the availability of DA/new data)
The third short board: the reliability of DA-layer data release
Although DA is called data availability, this term actually refers to data release. It is only because Vitalik and Mustafa did not think carefully when they initially named this concept that DA/data availability is called “not consistent with the name”..
Data release, as the name implies, refers to whether the latest block/transaction data/state transition parameters can be successfully received by those in need.Publishing data on different chains has different reliability.
(Reference: Misunderstanding of data availability: DA=Data release ≠Historical data retrieval
https://mp.weixin.qq.com/s/OAM_l4Pe9Gphn8H55OZUtw)
Western communities generally believe that old public chains such as Bitcoin and Ethereum are the most trusted DA layers.If the Layer2 sorter releases new data on Ethereum, anyone can download and synchronize it by running the Ethereum geth client, and it will be almost impossible to block it. This is the huge scale of the Ethereum network, and a wide variety of public data sources to implement.
It is worth mentioning that Ethereum Rollup will force the sorter to publish transaction data/state transition parameters on Layer1, which is guaranteed by proof of validity/fraud proof.
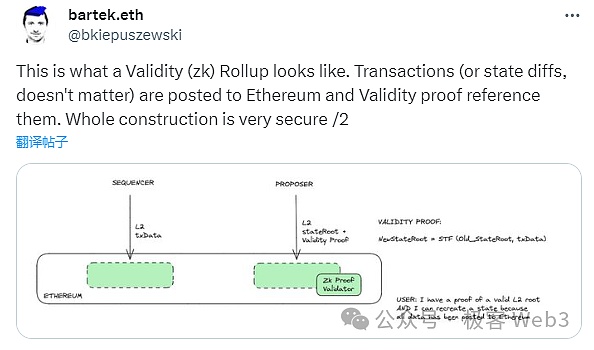
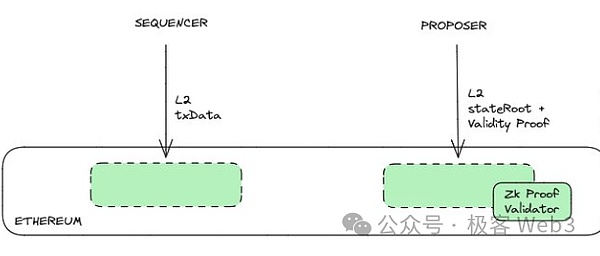
For example, after ZK Rollup’s sorter publishes transaction data on Layer1, it will trigger the contract logic to generate a datahash, and the validator contract needs to be confirmed, and the validity proof submitted by the Proposer corresponds to the datahash.
This is equivalent to confirming that the zk Proof and Stateroot submitted by the Proposer are associated with the Tx data submitted by the Sequencer, that is, New Stateroot=STF(Old Stateroot, Txdata).STF is the state transition function state transition function.
This ensures that the state transition data/DA is forcibly linked. If only stateroot and validity proof are submitted, it will not be possible to pass the verification of the validator contract.
The Ethereum/Celestia community has already fully discussed which DA data release or proof verification system is more basic. The general conclusion is that whether the DA layer is reliable is more important than the completeness of the fraud proof/validity proof system.For example, solutions such as Plasma, Validium, Optimium, and other solutions that DA layer are under the Ethereum chain and settlement layer are on the Ethereum chain are prone to “data hindrance attacks”, which means:
Sequencer/Proposer can conspire with the DA layer nodes under the ETH chain to update stateroot on Layer1, but the input parameters corresponding to the state transition are not sent out, making it impossible for outsiders to judge whether the new stateroot is correct, becoming “blind”.
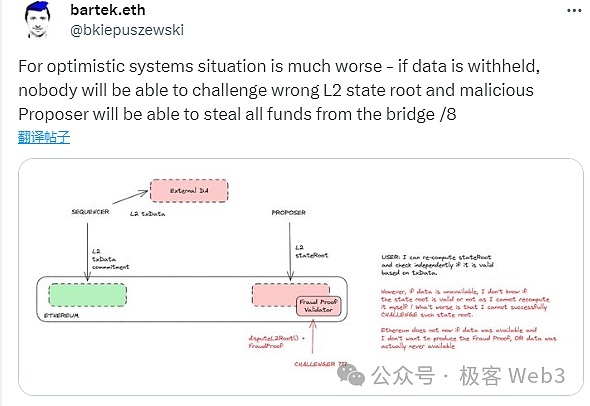
If this happens, the entire Layer2 network is equivalent to being scrapped, because at this time, you have no idea what the Layer2 account book has become.If it is Layer2 (Plasma and Optimium) based on fraud proof, the sorter can rewrite the data/assets under any account at will; if it is Layer2 (Validium) based on validity proof, although the sorter cannot rewrite your account at will, thisAt that time, the entire Layer2 network became a black box, and no one knew what was happening inside, and it was no different from scrapping.Because of this, the orthodox Layer2 solutions within the Ethereum ecosystem are basically Rollup, while Validium and Optimium are often not recognized by the Ethereum Foundation.
(Reference: Data withholding and fraud proof: Why Plasma does not support smart contracts
https://mp.weixin.qq.com/s/oOPZqIoi2p6sCxBdfUP4eA)
Therefore, the reliability/availability of state transition parameters of the DA layer is more important and more basic than the completeness of the fraud proof/validity proof system.For Bitcoin Layer2, especially Layer2 based on client verification model, even if the fraud proof/validity proof verification system is not set on Layer1, as long as the DA layer works as usual, everyone can still know whether the L2 network has an error status.Convert.
Currently, it is difficult to verify the fraud proof/proof of validity (BitVM is not discussed here). Let’s first assume that Bitcoin L2 does not have a proof verification system.Ideally, if the L2 sorter does evil and publish a stateroot that is not associated with DA data on the settlement layer/BTC, it still cannot truly steal user assets because it unilaterally submits the stateroot/state transition results., will not be recognized by honest nodes, and may just be self-entertainment in the end.
(At this time, as long as the nodes running by the peripheral facilities providers in the ecological such as exchanges and cross-chain bridges do not conspire with the sorter, the sorter cannot quickly cash out the stolen assets by publishing wrong data. After that, as long as there isIf an honest node finds that the situation is wrong, and sends an alarm at a critical moment, it can correct the errors through social consensus. However, the cost of social consensus itself is very high and cannot take effect immediately)
If it is a model similar to a side chain, most nodes conspire to perform malicious state changes, and people can quickly discover the problem.As long as third-party facilities such as cross-chain bridges and exchanges do not recognize the wrong data, the malicious controller of Layer2/sidechain cannot successfully cash out unless he persuades others to directly OTC on the chain with him.
(Viatlik once pointed out in the article that client verification is the real foundation for ensuring blockchain network security, Verify by yourself)
There is a very interesting point here. In fact, whether it is Ethereum Layer2 or Bitcoin Layer2, you can achieve “client verification”.However, based on “client verification”, Ethereum Layer2 uses Layer1 and the proof verification system to ensure the effectiveness of state transitions, and basically does not have to rely on social consensus (presumably there is a mature fraud proof/validity proof system).
Bitcoin Layer2’s “client verification” solution often has a strong dependence on “social consensus” and will bring corresponding risks (for Bitcoin Layer2, this security risk is basically controllable, but it may still lead to somePeople lose assets. For Ethereum Layer2, because its official bridge needs to prove the cooperation of the system, if the proven system is incomplete, the sorter can steal user assets and mention L1 to run away. Of course, it depends on the cross-chain bridgeHow to design components).
Therefore, a Layer2 that can implement fraud proof/validity proof verification system on Layer1 is always much better than a simple “client verification” model.
PS: Since most Bitcoin Layer2, which uses fraud proof/validity proof system, cannot allow Layer1 to directly participate in the proof verification process, its essence is still just to treat Bitcoin as the DA layer, and the security model is equivalent to “client verification””.
Theoretically, through the BitVM solution on Layer1, fraud proof can be verified on the Bitcoin chain, but this solution project is very difficult to implement and will encounter great challenges.Since the Ethereum community has already made a lot of discussions on the Layer1-based proof verification system and is well known to everyone, this article does not intend to repeat the “Layer1-based proof verification system”.
Summarize
After a simple analysis of the wooden barrel model, we can draw a preliminary conclusion: in the mainstream Layer2 security model, the following order can be sorted according to the importance/basic level:
1. Whether the control authority of the contract/official bridge is reasonably distributed
2. Is there a withdrawal function that resists review?
3. Is the DA layer/data publishing form reliable?
4. Is there a reliable fraud proof/validity proof system deployed on Layer1
Of course, we did not analyze the ckBTC, inscription index protocol and other solutions of Lightning Network/State Channel and ICP ecosystem, because they are quite different from typical Rollup, Plasma, Validium or client verification solutions.Due to time constraints, it is still difficult for us to carefully evaluate their safety and risk factors, but considering their significance, relevant assessment work will be carried out as scheduled in the future.
At the same time, there are serious differences among many project parties regarding whether the inscription index protocol should be regarded as Layer2. However, regardless of the definition of Layer2, new things such as the inscription index protocol have brought full technological innovation to the Bitcoin ecosystem.And will eventually burst into great vitality.






