Author: Calibre, Web3 Venture Builder Source: mirror Translation: Shan Oppa, Bitchain Vision
Bitcoin Layer 2 Overview
In the complex field of financial technology, Bitcoin is a beacon of innovation. It is a digital currency that avoids traditional financial intermediaries and can realize peer-to-peer transactions without intermediaries.However, with its rise, it also presents a set of inherent challenges, most notably those related to scalability and transaction throughput – important obstacles to wider use.
These challenges are not unique to Bitcoin. Although Ethereum is also designed with flexible application development capabilities, it also has similar problems.Many solutions have been proposed to solve these two problems, such as sidechains, layer 2 or payment channel networks.With Ethereum, the Layer 2 ecosystem is rapidly expanding and offers a variety of solutions such as EVM rollups, sidechain transitions to rollups, and projects working to achieve varying degrees of decentralization and security.The security implications of Tier 2 solutions, with particular focus on asset assurance and the ability of these systems to read and adapt to changes in the Ethereum blockchain.It highlights a key trade-off: higher security is often at the expense of scalability and cost efficiency.
Despite impressive progress in improving its capabilities, Bitcoin still faces some significant challenges in developing a layer 2 (L2) solution similar to Ethereum.Bitcoin’s design limitations are particularly evident when it comes to ensuring withdrawals in Bitcoin’s Layer 2 solutions.Its scripting language intentionally limits functionality and lacks Turing completeness, which limits its ability to perform complex computations and support advanced features.This design choice prioritizes Bitcoin’s security and efficiency, but limits its programmability compared to more flexible blockchain platforms such as Ethereum.Moreover, the probability finality will also destroy the reliability and speed necessary for layer 2 solutions, which may lead to problems such as chain restructuring that affects transaction durability.Although Bitcoin is built on the principles of reliability and security, these aspects make it difficult for its L2 system to adapt quickly to new changes.
SegWit and Taproot are the game changers of Bitcoin.SegWit optimizes Bitcoin’s infrastructure by isolating signed data, increasing transaction speeds and enabling fast payment processing from the Lightning Network.Since then, Taproot has improved efficiency and privacy by compressing transaction data and blocking transaction complexity.Together, SegWit and Taproot have sparked a new wave of Layer 2 innovations, becoming the backbone of future Layer 2 designs and significantly expanding Bitcoin’s capabilities beyond its original scope as a digital currency.
Understand the Layer 2 Solutions for Bitcoin
Bitcoin L2 triad
In the expanding Layer 2 solution space of Bitcoin, we see many different systems emerging, all designed to enhance scalability and improve adoption in various ways.These solutions provide a unique way to overcome the limitations of Bitcoin built-in.As Trevor Owens [2] introduced, one way to classify these solutions is to organize them according to the solution to the Bitcoin L2 tribulations, which divides the L2 solution into off-chain networks, decentralizedEach solution presents unique characteristics and trade-offs:
-
Off-chain networking: Prioritize scalability and privacy, but may present challenges to the user experience.For example, Lightning & RGB.
-
Decentralized sidechain: Introducing new tokens and consensus mechanisms to expand functionality, but may complicate the user experience and increase centralized concerns.For example, Stacks, Babylon, Interlay, etc.
-
Joint Side Chain: Simplify operations through trusted consortiums, providing efficiency, but may be at the expense of the basic decentralization of Bitcoin.For example, Liquid, Rootstock, Botanix.
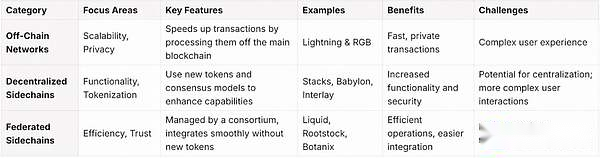
This triad provides a useful way to classify Bitcoin’s Layer 2 solution, but it may not fully capture all the complex details of its design.Furthermore, it points to the trade-offs of current solutions, rather than unsolvable obstacles, suggesting that these elements of the triad are part of the developer’s decision-making process.
For example, decentralized sidechains issue new tokens to improve security and promote network participation, which may make user interaction more complex and may not be popular with Bitcoin purists.On the other hand, the Federal Side Chain chose to skip new tokens to make the user experience smoother and reduce resistance within the Bitcoin community.Another option is to use a full virtual machine/global state, which allows complex features including creating new tokens on the smart contract platform.However, this approach makes the system more complex and often increases its vulnerability to attacks.
Technical classification
From another technical perspective, we group it according to the main technical features of Bitcoin’s Layer 2 solutions.This different classification approach looks at a variety of technical details and structures, providing a nuanced understanding of how each solution can help enhance Bitcoin’s overall goal of scalability, security, and functionality.Each method has its own unique purpose, and these purposes do not conflict with each other and cause triad difficulties.However, each approach has its own advantages and disadvantages in terms of security and scalability.Therefore, some systems can utilize a combination of these methods.We will discuss this in more detail in the next section of this article.Let’s explore these categories:
-
Sidechains utilizing bidirectional anchoring protocol: These sidechains work similarly to connecting to layer 2 of Bitcoin through a method called bidirectional anchoring.This setup allows Bitcoin to be transferred between the main blockchain and the sidechain, allowing experimentation and to implement features that are not directly supported by the main blockchain.This approach improves Bitcoin’s ability to handle more transactions and different types of applications by supporting a wider range of uses.The two-way anchoring mechanism plays a key role in transferring BTC value to sidechains.On these sidechains, developers build environments; some choose to use an EVM-compatible ecosystem, while others choose to create VM environments using their own smart contracts.
-
For example, Stacks, Rootstock, Liquid, Botanix, etc.
-
Blockchain rollups: This method uses Bitcoin as the data storage layer for the aggregation technology, inspired by the Inscription Protocol.In this setup, each UTXO is like a small canvas where more complex information can be written.It is conceivable that each Bitcoin can store its own set of detailed data, which not only increases value, but also broadens the types of data and assets that Bitcoin can handle.It opens up a wide range of possibilities for digital interactions and representations, making the Bitcoin ecosystem richer and more diverse.
-
For example, B2 network, BitVM
-
Payment Channel Network: Think of it as a fast-track network in the wider Bitcoin space.They help speed up large volumes of transactions on the Bitcoin road, reduce congestion and ensure transactions are both fast and cost-effective.
-
For example, Lightning and RGB
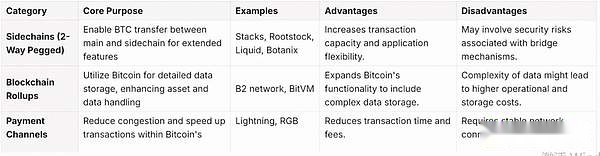
By breaking it down this way, we can have a clearer understanding of how each tool can help improve Bitcoin, making it more scalable, secure and versatile.Let’s dive into and get a better understanding of these tools:
2 Two-way anchoring protocol:
Bidirectional anchoring allows assets to be transferred between two different blockchains, usually the main chain and the side chain.The system enables assets to be locked on one chain and subsequently unlocked or minted on the other chain, thus maintaining a fixed exchange rate between the original and anchored assets.
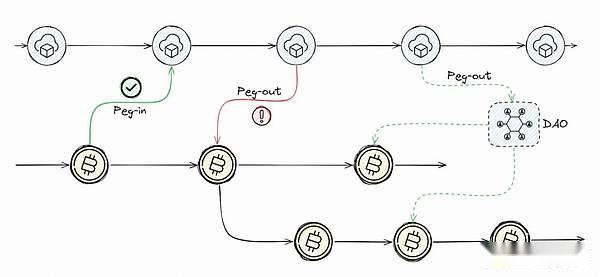
Understand the anchoring process
Imagine launching a journey to transfer your assets from the main chain, such as Bitcoin, to the side chain.The anchoring process is your starting point.Here, your assets are securely locked on the main chain, similar to storing them in a vault for custody.Then, create a deal on the main chain to consolidate the lock.After the side chain recognizes the transaction, it will mint an equal amount of anchor assets.This process is similar to receiving vouchers of equal value in a foreign country, allowing you to use your wealth in a new environment while ensuring your original assets remain intact and secure.
Guide the anchor process
When you decide to restore the asset to the original main chain, the turn-out of the anchoring process comes into play.This is the backhaul, where anchored assets on the side chain are metaphorically “burned” or locked, meaning they are put on hold and no longer circulated on the side chain.You then provide the main chain with proof of this action.Once the main chain verifies your claim, it releases the original assets of equal value to you.This mechanism ensures the integrity and balance of asset allocations on both blockchains, preventing duplication or loss.
Implementation of bidirectional anchoring system:
Rootstock
RSK’s two-way anchoring system is an advanced framework designed to seamlessly integrate Bitcoin with smart contract capabilities through the RSK platform.By leveraging SPV for efficient transaction verification, using a powerful federal model for transaction approval, and integrating SegWit and Taproot, RSK not only improves transaction efficiency, but also closely integrates with Bitcoin’s security model.In addition, the merged mining method improves the security level of the system and incentivizes more miners to participate.
-
RSK joint model:
Pegnatories are a selected group of officials, guardians of the bridge or trusted custodians in this federal model, ensuring that each transfer in and out is subject to the agreed agreement.Think of them as a board of guardians, each holding the key to a collective vault.Their role is crucial – they ensure that every cross-bridge transaction is conducted in a manner of integrity and consensus, thus maintaining the safe and orderly flow of digital assets on this important channel.
-
Segwit and Taproot:
SegWit helps by separating signature information from transaction data, reducing transaction size and processing time.In addition, combining the Schnorr signature scheme with MAST (Merkelized Abstract Syntax Tree) and other enhancements from Taproot can make transactions more efficient and private.
-
RSK merge mining:
In RSK’s merge mining method, miners protect both Bitcoin and RSK networks without additional computing requirements, thereby improving RSK security.This approach takes advantage of Bitcoin’s mining benefits, provides additional rewards for miners and demonstrates the innovative use of existing blockchain infrastructure.However, the success of this integration depends on the accurate alignment of the tags within the Bitcoin block to correspond to the RSK block, which emphasizes the need for detailed and precise execution to maintain security and consistency of the interconnected network.
Botanix
Botanix integrates a Bitcoin-based Proof of Stake (PoS) consensus and a decentralized EVM network Spiderchain multi-signature architecture to manage Turing complete smart contracts on the main Bitcoin blockchain.While Bitcoin serves as the primary settlement layer, Botanix uses advanced multi-signature wallets and off-chain encryption verification to ensure transaction integrity.
-
Spiderchain: A distributed multi-signature network that protects all actual Bitcoins on Botanix.
-
Architecture: Spider chain consists of a group of Orchestrator nodes—the node operator and liquidity source of the entire chain.It consists of a series of multi-signature wallets for managing the custody of assets within the network.Any transaction for each wallet in the series requires multiple Orchestrator approvals to ensure there is no single point of failure.
-
Dynamic Operation: For each new Bitcoin block, the corresponding coordinator for the upcoming “epoch” (the term used to define the period between Bitcoin blocks in Botanix systems) uses Bitcoin block hashingRandom functions can be verified to determine.The subsequent slot selection of Orchestrator is calculated by hashing the block hash using SHA256, and then modulo the number (N) of active Orchestrators to ensure fairness and randomness of Orchestrator selection.This ensures fair and secure allocation of operational tasks, minimizing centralized risks.
-
Two-way anchoring system: Multi-signature wallets play a crucial role here, requiring consensus among selected coordinators to be reached in order for any transaction to be executed.
-
Anchor process: The user sends Bitcoin to a new multi-signature wallet and locks securely there.This action will cast an equal amount of synthetic BTC on the Botanix chain.Creating this wallet involves multiple Orchestrators, they must all agree and sign, ensuring that no one can control the wallet independently.
-
Transfer out anchoring process: On the contrary, for transfer out anchoring, the synthetic BTC will be burned, and the corresponding Bitcoin will be released from the multi-signature wallet back to the user’s Bitcoin address.This process is protected by the same multi-signature protocol and requires multiple Orchestrators to approve the transaction.
-
PoS consensus and EVM implementation:
-
Consensus: In Botanix’s PoS system, Orchestrator stakes their Bitcoins to participate in the network.They are responsible for verifying transactions and creating new blocks within the Botanix chain.The selection process of these coordinators is based on their interests and is randomized using the methods mentioned in the Spider Chain section.
-
EVM implementation: EVM on Botanix supports all operations compatible with Ethereum, enabling developers to deploy and execute complex smart contracts.
Stacks:
The Stacks platform aims to expand Bitcoin’s infrastructure by enabling smart contracts and decentralized applications (dApps) through innovative mechanisms such as sBTC two-way anchoring, transfer proofs, and Clarity smart contracts.
-
sBTC bidirectional anchoring protocol:
-
Threshold Signature Wallet: This wallet adopts a threshold signature scheme and requires a predefined subset of signers (Stackers) to collaborate on signing anchor transactions.These Stackers use verifiable random functions (VRFs) to select based on the number of STXs they lock and rotate each cycle (usually two weeks), ensuring dynamic membership and consistent with the current network status.This significantly enhances the safety and robustness of the anchoring mechanism by preventing dishonest behavior and potential complicity among participants, while also ensuring fairness and unpredictability of the selection process.
-
Proof of Transfer (PoX):
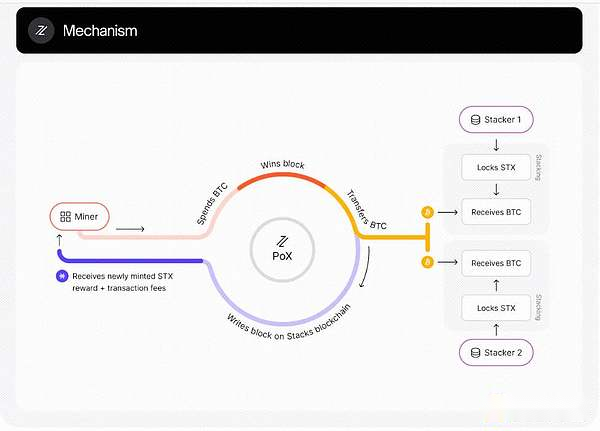
-
In PoX, instead of destroying Bitcoin like Proof of Burn, miners transfer BTC to the Stack network to improve security by leveraging Bitcoin’s powerful proof-of-work system.This not only motivates participation through BTC rewards, but also directly links Stacks’ operational stability to Bitcoin’s proven security features.Stacks transactions are anchored to Bitcoin blocks, and each Stacks block uses opcode to record the hash value in Bitcoin transactions.
OP_RETURN, which allows embedding40 bytesAny data.This mechanism ensures that any changes to the Stacks blockchain require corresponding changes to the Bitcoin blockchain, thus benefiting from Bitcoin’s security without any changes to its protocol.
-
Smart Contract Programming Language used on Stacks Blockchain Clarity ensures developers’ predictability and security by enforcing strict rules to ensure that all operations are performed as defined without unexpected results.It provides determinability, i.e. the result of each function is known before execution, thereby preventing accidents and improving contract reliability.Additionally, Clarity interacts directly with Bitcoin transactions, allowing the development of complex applications that leverage Bitcoin’s powerful security capabilities.It also supports modular features, similar to interfaces in other languages, which helps reuse code and maintain a clean code base.
Liquid:
Liquid Network provides joint sidechains for the Bitcoin protocol, significantly enhancing transaction capabilities and asset management.At the heart of the Liquid network architecture is the concept of a strong alliance [6], which consists of trusted functional personnel responsible for block verification and signature.
-
Watchmen: Watchmen manages the anchoring process from Liquid to Bitcoin, ensuring that every transaction is authorized and valid.
-
Key Management: Watchmen’s hardware security module protects the keys required for authorized transactions.
-
Transaction Verification: Watchmen verifies transactions through cryptographic proofs, confirms compliance with Liquid’s consensus rules, and uses a multi-signature scheme to enhance security.
-
Anchor mechanism:
-
Peg-Ins: Bitcoin is locked on the Bitcoin blockchain (by using the Watchmen’s multi-signature address) and issuing equivalent Liquid Bitcoin (L-BTC) on the Liquid sidechain using encryption methods to ensure transmissionaccuracy and safety.
-
Peg-Outs: This process involves burning L-BTC on the Liquid sidechain and releasing the actual Bitcoin accordingly on the Bitcoin blockchain.The mechanism is closely monitored by designated staff members known as the Watchmen to ensure that only authorized transactions can be carried out.
-
Proof of Reserves (PoR): An important tool developed by Blockstream to provide transparency and trust in network asset holdings.PoR involves creating partially signed bitcoin transactions to prove control over funds.Although the transaction is invalid on the Bitcoin network, it proves the existence and control of the claimed reserves.It allows an entity to prove that it has funds without moving them.
Babylon
Babylon aims to integrate Bitcoin into the Proof of Stake (PoS) ecosystem, enhances the security of the PoS chain by allowing Bitcoin holders to stake their assets, leveraging Bitcoin’s huge market capitalization without the need for direct transactions or smart contractsFeatures Bitcoin blockchain.Importantly, Babylon does not attempt to move or lock Bitcoin through fragile bridges or third-party custodians, thus avoiding the complexity and security risks of the bridge, thus protecting the integrity and security of the staking assets.
-
Bitcoin timestamp:
-
Babylon adopts a timestamp mechanism to embed PoS chain data directly into the Bitcoin blockchain.By anchoring PoS block hashing and key staking events to Bitcoin’s immutable ledger, Babylon provides historical timestamps protected by Bitcoin’s extensive proof-of-work.Using the Bitcoin blockchain for timestamping not only takes advantage of its security, but also its decentralized trust model.This approach ensures an additional layer of security that prevents remote attacks and state corruption on interconnected blockchains.
-
Responsible assertion:
-
Babylon uses responsible assertions to manage stake contracts directly on the Bitcoin blockchain, allowing the system to expose the staker’s private keys in the event of misconduct such as double signatures.The design uses a chameleon hash function and a Merkle tree to ensure that the assertions made by the staker are cryptographically associated with their stake, enabling automatic cuts.This approach enforces protocol integrity through encryption liability, where any deviations from the risk taker (such as signing conflicting statements) lead to deterministic exposure of his private key, triggering automatic penalties.
-
Pledge Agreement:
-
One of Babylon’s major innovations is its staking agreement, which allows for rapid adjustment of staking allocations based on market conditions and security needs.The agreement supports rapid equity unbinding, allowing equity holders to quickly transfer their assets without having to go through the longer lockdown period associated with the PoS chain.In addition, the protocol is built as a modular plug-in and is compatible with various PoS consensus mechanisms.This modular approach allows Babylon to provide staking services to a wide range of PoS chains without major changes to its existing protocols.
Payment Channels and Lightning Network:
Payment channels are tools designed to support multiple transactions between two parties without having to submit all transactions to the blockchain immediately.Here is how they simplify their transactions:
-
Initial: Open the channel through a single on-chain transaction to create a multi-signature wallet shared by both parties.*
-
Transaction process: In the channel, all parties conduct transactions privately through instant transfers, adjusting their respective balances without broadcasting to the blockchain.*
-
Close: The channel is closed by a transaction on another chain, which settles the final balance based on the recently agreed transaction between the parties.*
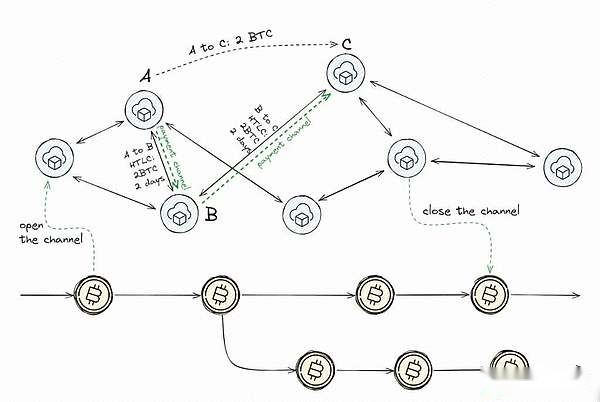
Explore the Lightning Network:
Based on the concept of payment channels, Lightning Network extends these concepts into the network, allowing users to send payments on the blockchain through the path of connection.
-
Routing: Just like using a trail to find a route through the city, the network will find your payment path even if you don’t have a direct access to the final recipient.
-
Efficiency: This interconnect system significantly reduces transaction fees and processing time, making Bitcoin suitable for daily transactions.
-
Smart Lock (HTLC): This network uses advanced contracts called hash time lock contracts to protect payments on different channels.It’s like making sure your shipment passes through multiple checkpoints safely before reaching its destination.It also reduces the risk of intermediary defaults and makes the network reliable.
-
Security Agreement: If there is a disagreement, the blockchain will act as a judge to verify the latest agreed balances to ensure fairness and security.
Taproot and Segwit have greatly promoted the development of the Bitcoin network, especially the Lightning Network, which has enhanced privacy and efficiency:
-
Taproot is like an aggregator for Bitcoin transactions—it bundles multiple signatures into one.This not only keeps off-chain transactions neat, but also makes them more private and cheaper.
-
Segwit has changed the way data is stored in Bitcoin transactions, so that a block can contain more transactions.For Lightning Network, this means opening and closing channels is cheaper and smoother, further reducing fees and increasing transaction throughput
Inscription-based layer 2 solution:
The inscription triggered a new wave of innovation in the second layer of Bitcoin ecosystem.With the advent of two breakthrough updates (Segwit and Taproot), the Ordinals protocol was introduced, allowing anyone to attach additional data to UTXO’s Taproot scripts up to 4MB.This development has made the community aware that Bitcoin can now act as a data availability layer.Inscriptions provide a new perspective on security.Data (such as digital artifacts) are now stored directly on the Bitcoin network, making it unchangeable and preventing it from being tampered with or lost due to external server problems.This not only enhances the security of digital assets, but also embeds them directly into Bitcoin’s blocks, ensuring they are permanently reliable.Most importantly, Bitcoin aggregation has become a reality, and the inscription provides a mechanism for incorporating additional data or functionality into transactions.This allows more complex interactions or state changes to occur outside the main chain while still anchoring to the main chain’s security model.
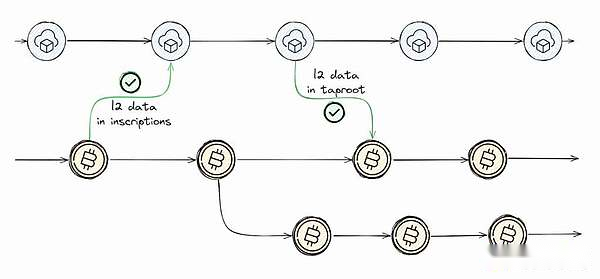
Implementation of the inscription-based layer 2 solution:
BitVM:
BitVM combines Optimistic Rollup technology with cryptography proof in its design.By moving Turing’s complete smart contracts off-chain, BitVM significantly improves transaction efficiency without compromising security.Although Bitcoin is still the basic settlement layer, BitVM ensures the integrity of transaction data by cleverly leveraging Bitcoin’s scripting capabilities and off-chain encryption verification.Currently, BitVM is being actively developed by the community.[9] In addition, it has become a platform for several top projects such as Bitlayer [7] and Citrea [8].
-
Similar storage methods for inscriptions:
BitVM uses Bitcoin’s Taproot to embed data into Tapscript, similar to the concept of the Inscription protocol.This data usually includes important computational details, such as the state of the virtual machine at different checkpoints, the hash value of the initial state, and the final computational results.BitVM effectively integrates transaction data directly onto the Bitcoin blockchain by anchoring this Tapscript in an unused transaction output (UTXO) stored in a Taproot address.This approach ensures persistence and immutability of data while benefiting from Bitcoin’s security features to protect the integrity of record computing.
-
Evidence of fraud:
BitVM uses fraud proof to ensure the security of transactions.Here, the prover promises the computed output of a specific input, and the promise is not executed on the chain, but is indirectly validated.If validators suspect that the promise is wrong, they can question it by providing concise evidence of fraud that leverages Bitcoin’s scripting capabilities to prove the incorrectness of the promise.The system significantly reduces the computing load on the blockchain by avoiding full on-chain computing, in line with the design philosophy of Bitcoin’s minimum transaction load and highest efficiency.At the heart of this mechanism are hash locks and digital signatures, which protect statements and challenges and link them to actual off-chain computing efforts.BitVM adopts an optimistic verification approach—the operation is considered correct unless otherwise proven, which improves efficiency and scalability.This ensures that only valid calculations are accepted and that anyone on the network can independently verify their correctness using available encryption proofs.
-
Optimistic rollups:
BitVM uses optimistic aggregation technology to significantly enhance Bitcoin’s scalability by batching multiple off-chain transactions for collective processing and verification.In fact, BitVM processes these transactions off-chain and intermittently records its results on the Bitcoin ledger to ensure integrity and availability.Using optimistic summary in BitVM represents a way to overcome the inherent scalability limitations of Bitcoin by leveraging off-chain computing capabilities while ensuring transaction validity through periodic on-chain verification.The system effectively balances the load between on-chain and off-chain resources and optimizes the security and efficiency of transaction processing.
Overall, BitVM is not just another Layer 2 technology, but it represents a potential fundamental shift in how Bitcoin scales and develops.It provides a unique solution to the limitations of Bitcoin, but further development and improvements are still needed to reach its full potential and gain wider adoption within the community.
B2 Network:
The B2 Network is Bitcoin’s first zero-knowledge proof verification commitment rollup, leveraging rollup technology and zero-knowledge proof to increase transaction speed and minimize costs.This setup allows off-chain transactions to execute Turing-complete smart contracts, thereby significantly improving efficiency.Bitcoin acts as the basic settlement layer of the B2 network, where B2 aggregated data is stored.This setting allows the complete retrieval or recovery of B2 aggregate transactions using Bitcoin inscriptions.In addition, the computational validity of the B2 summary transaction is verified by zero-knowledge proof confirmation on Bitcoin.
-
The important role of inscriptions:
The B2 network uses Bitcoin inscriptions to embed additional data in Tapscript, including important information, such as the storage path of the aggregated data, the Merkle tree root hash of the aggregated data, the zk proof data, and the parent B2 inscription UTXO hash.By writing this Tapscript to the UTXO and sending it to the Taproot address, B2 effectively embeds the aggregated data directly into the Bitcoin blockchain.This approach not only ensures the persistence and immutability of data, but also uses Bitcoin’s powerful security mechanism to protect the integrity of aggregated data.
-
Zero-knowledge proof for enhanced security:
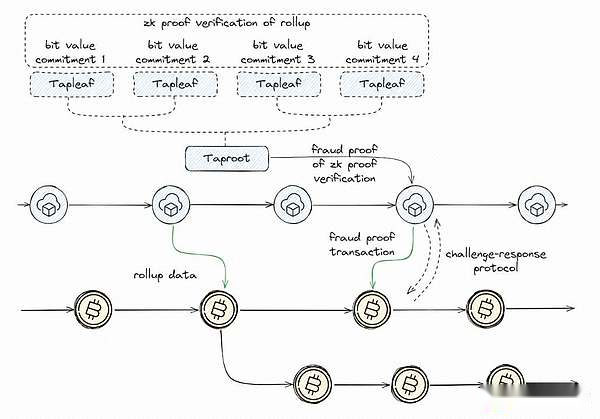
B2’s commitment to security is further reflected in its use of zero-knowledge proof.These proofs enable the network to verify transactions without exposing these transaction details, thus protecting privacy and security.In the context of B2, the network breaks down the compute cells into smaller cells, each represented as a bit value promise in the Tapleaf script.These promises are linked together in a main root structure, providing a compact and secure way to verify transaction validity across Bitcoin and B2 networks.
-
Scalable Rollup technology:
At the heart of the B2 architecture is Rollup technology, especially ZK-Rollup, which aggregates multiple off-chain transactions into a single transaction.This approach significantly improves throughput and reduces transaction fees, solving two of the most pressing scalability issues in Bitcoin.The summary layer of the B2 network processes user transactions and generates corresponding proofs to ensure that transactions are valid and finalized on the Bitcoin blockchain.
-
Challenge-response mechanism: In a B2 network, after using zk proof to batch and verify transactions, if an invalid transaction is suspected to be included, the node has the opportunity to challenge these batches.This critical stage utilizes a fraud proof mechanism, and the challenges must be finally resolved before batches can be continued.This step ensures that only transactions that have been verified as legitimate can enter the final confirmation.If no challenges occur within the specified time lock or existing challenges fail, the batch will be confirmed on the Bitcoin blockchain.On the other hand, if any challenge is verified, the summary will then be restored.
Final thoughts:
The good side:
-
Unlock the DeFi market: Bitcoin can enter the multi-billion-dollar DeFi market with EVM-compatible layer 2 solutions enabling features such as smart contracts.This is not only to expand the practicality of Bitcoin, but also to unlock new financial markets that were previously only accessible through Ethereum and similar programmable blockchains.
-
Expanded use cases: These tier 2 platforms support not only financial transactions, but also a range of applications in areas such as finance, gaming, NFT or identification systems… thus extending Bitcoin’s use cases far beyond its original scope as a simple currency[3, 4, 5].
Bad things:
-
Centralization risk: Some mechanisms involved in certain Tier 2 solutions may lead to an increase in the level of centralization.For example, in mechanisms that require locking in BTC value, unlike Ethereum’s Layer 2 solution, interactions from Layer 2 to Bitcoin are not protected by the Bitcoin security model.Instead, it relies on smaller decentralized networks or federated models, which may undermine the security of trust models.This structural difference may introduce failure points that do not exist in the decentralized model.
-
Increased transaction fees and blockchain inflation: Data-intensive use of serial numbers and other inscription protocols may lead to blockchain inflation, slowing down the network and increasing transaction costs for all users.This may result in higher costs and slower transaction verification times, which affects the efficiency of the network.
-
Complexity and User Experience: The technical complexity of understanding and interacting with Layer 2 solutions can be a significant barrier to adoption.Users need to manage other elements, such as payment channels on Lightning Network or handling different token types on platforms like Liquid.
Ugly:
-
Regulatory and Ethical Issues: The immutability of these inscriptions, while technically advantageous, also raises potential regulatory and ethical issues.If the data is illegal, immoral or completely wrong, it can bring significant challenges, resulting in unrecoverable permanent consequences.
-
Impact on Fluency: If certain bitcoins are “labeled” by non-financial data, it may affect their substitutability (each unit should be indistinguishable from another unit), which may result in the value of some bitcoinsOr less acceptable than other units.