Written article: Bit Chain Vision Xiaozou
On April 15, 2024, Vitalik turned 100 ETH into the privacy agreement Railgun.The next day, Vitalik pushed Railgun again that privacy was normal. Railgun used a privacy pool agreement, which made it more difficult for bad actors to join the pool without damaging user privacy.
Where did Railgun attract Vitalik?6 questions in this article take you to understand Railgun.
1As well asRailgunWhat is it?
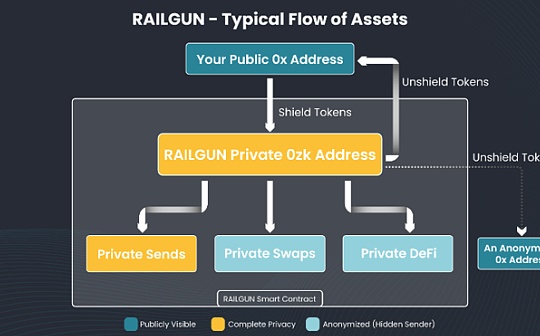
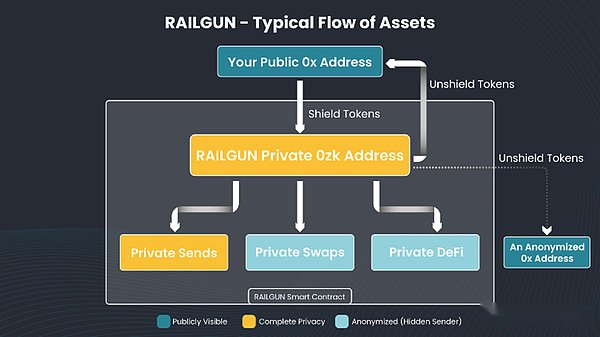
Railgun is a privacy system established directly on Ethereum, BSC, Polygon and the Arbitrum chain.It uses zero -knowledge (ZK) encryption technology to realize the privacy of smart contracts and DEFI without sacrificing the security of the user’s preferred chain.
Railgun only refers to a set of smart contracts that support back -end privacy infrastructure.Wallet providers can choose to integrate the Railgun protocol.
Since Railgun is just a smart contract logic on the chain, it has two major advantages to achieve privacy without the need for L2 verifier set or vulnerable to be attacked by vulnerabilities: it has two major advantages:
-
Safety and decentralization -less validator set issues, there is no bridge risk.Railgun is as safe as its EVM chain deployed on it.
-
The complete ecosystem -Railgun users can access all economic activities on Ethereum, and benefit from the existing DAPPS and the rich history of the builders, rather than an isolated ecosystem on an independent privacy chain.
User experience is similar to using public wallets like Metamask to interact with the Ethereum/EVM chain and interact with DEFI. The difference is only to increase the ability of private transactions.
Railgun mainly contains two major components:
-
Railgun Integrated Wallet -EVM wallet built by independent community developers, users can use the Raiglun protocol through the wallet.
-
Developer tool -TypeScript SDKS, which is used to build Railgun privacy to existing wallets or new wallets, or DAPP with privacy protection characteristics.
2As well asRailgunWhat are the advantages and use cases
Complex Defi transactions help Railgun more privacy than other protocols with similar anonymity.All transfer, exchange, lending and DAPP calls have increased interaction changes in Railgun.
Compared with other privacy systems, Railgun has achieved better privacy protection with less liquidity and shorter time framework.DAPP interaction in Railgun’s privacy system also inspires users to hold assets longer in Railgun because there is no reason to transfer funds out of Railgun.
Potential use cases are:
-
Privacy: Wallet dynamics are not known, account balance privacy, transaction strategy protection, trading habits are not monitored, prevent data collection
-
Alpha security security: traders who want to keep ALPHA confidential can be traded freely and maintain the difficulty in information advantages.
-
Privacy payments: Provide salary bills for companies that use cryptocurrencies to pay wages.If you use the current state of public blockchain’s salary, the exact salary of each employee will be displayed.
-
Anti -review: Citizens who support citizens living in countries living in unwavering or corruption of government officials conduct review donations.
-
Anonymous analysis: Contrary to services such as NANSEN or Etherscan, in NANSEN or Etherscan services, well -known wallets are marked or recognized, which means that some large investors’ personal identity is recognizable.
-
Compliance: Financial companies still abide by data protection laws, such as GDPR
Railgun is a disruptive toolkit. Objectively speaking, it is the most uncompromising and complete privacy solution for DEFI.Privacy DEFI will provide new business possibilities that cannot be achieved on public blockchains for the cryptocurrency industry.All other privacy solutions have some profits and disadvantages, such as requiring users to trust Bridges or trading with fragmented (or non -existent) liquidity.
3As well asRailgunWhat is different from other privacy protection agreements?
Other security solutions usually require dedicated infrastructure to operate, known as the L2 solution.L2 solution cannot directly access the DEFI protocol, and rely on many bridge technologies with security vulnerabilities.Because the L2 solution uses its own nodes, they do not have the complete security or liquidity of the main blockchain.
Other solutions, such as Mixers, lack function and ease of use.For example, Mixers usually does not support internal shielding transactions or interaction with smart contracts.They may also require users to send and receive a fixed amount, such as 1 or 10 ETH.Mixers cannot use the protocol simply and effectively while protecting privacy.They do not allow users to keep their balance in their wallets.However, Railgun’s privacy and security is worry -free. Even without transactions, users’ privacy will be maintained.
The privacy agreement of the previous generation cannot be compared with the convenience, flexibility and privacy that Railgun’s guarantee.
4As well asRailgunWhich tokens are supported?
Railgun does not need to be permitted.By default, all standard ERC-20s tokens can be used in the Railgun privacy system.
Some ERC-20s are non-standard, such as Rebasing tokens and lottery tokens.These tokens are currently not compatible with Railgun’s privacy system and should not be stored.
Although it does not fully meet ERC-20 standards, Tether (USDT) can be used for Railgun privacy systems.
5As well asRailgunWhat is the ease of use?
Railgun is very easy to use through the front end of Web APPS.This technology can also be easily integrated into existing agreements.
Although the code is very complicated, it is easy to use the Railgun privacy system.Wallet APPS (such as Railway) containing Railgun smart contracts has very intuitive user interface.
6How to achieve the balance of balance?What is the principle of cryptography?
The Railgun wallet consists of two keys: expenditure key and viewing key.Railgun wallet address (also known as 0ZK address) is two corresponding public keys -expenditure public key and viewing public key.
Therefore, if the user A (Alice) knows the Railgun address of the user B (BOB), she can initiate a transaction.
ALICE achieves this by creating a Note containing the so -called commitment in cryptology.The commitment includes information about tokens and the amount of tokens to be transferred.These commitments are encrypted using information in the public key of BOB.
Next, Alice created a ZK-SNARK to prove that her expenditure did not exceed her deposit.This also shows that she did not repeat consumption -she also spent the token elsewhere.
Finally, Alice sends proof, commitments and ciphertext to Railgun smart contracts.The intelligent contract verification proves that cumulative commitments and ciphertexts are issued as events.This means that it is correct for it and enables BOB to interact with transactions.
Only BOB can use his viewing key decryption text to obtain privacy information.With this information and his expenditure key, BOB can spend this note -it means that he can transfer or withdrawn tokens.