
Author: Mohamed Fouda, Medium; Compilation: Deng Tong, Bitchain Vision
Bitcoin spot ETF has led discussions in the past few weeks.After all dust settled, the community’s attention returned to the development of Bitcoin.This means to answer an eternal question: “How to improve the programming of Bitcoin?”
Bitcoin L2 is currently the most promising answer to this question.This article compares Bitcoin L2 with L1 and discusses some of the most promising Bitcoin L2 projects.Then, this article discusses interesting entrepreneurial opportunities related to Bitcoin L2.
Defend Bitcoin that does not require licenses
Since many investors can now get Bitcoin opening through regulatory products, they can use BTCs in many Tradfi products such as leverage trading and mortgage loans.However, these products do not use native BTCs.Instead, they use the TRADEFI of BTC controlled by the issuer, while the native BTC is locked by the custodian.over time,Tradefi BTC may become the main way to hold and use BTC, and transform it from decentralized assets that do not need to be licensed to another asset controlled by Wall Street.Bitcoin’s native 是 是 抵 比 is the only way out to resist the old financial system to capture Bitcoin.
Building Bitcoin original production products
L1 application
People have tried to achieve additional functions on L1 many times.The focus of these efforts is to use the ability of Bitcoin to carry any data.These any data can be used to achieve additional functions, such as issuance and transfer assets and NFT.However, these functions are not built as part of the Bitcoin protocol, but need to explain additional software to explain these data fields and operate them.
These efforts include Colored Coins, Omni Protocol, Counterparty, and the nearest Ordinals.OMNI was originally used to distribute and transfer Tether (USDT) on Bitcoin L1, and then extended to other chains.Counterparty is the underlying technology of Bitcoin stamps and SRC-20 token.Ordinals currently uses inscriptions to issue NFT and BRC-20 tokes on Bitcoin.
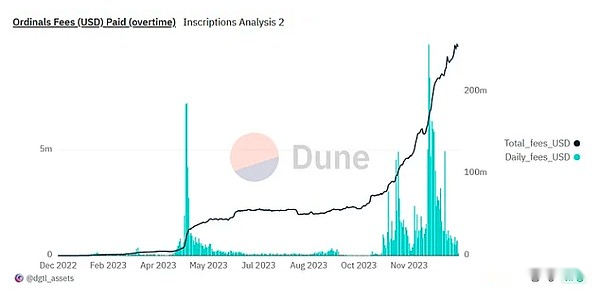
ORDINALS has achieved great success since its launch, and the cost of more than 200 million US dollars.Despite success, Ordinals is limited to asset issuance and transfer.Ordinals cannot be used to implement applications on L1.Due to the limitations of Bitcoin Script in Bitcoin native programming language, more complex applications (such as AMM and borrowing) are almost impossible to build.
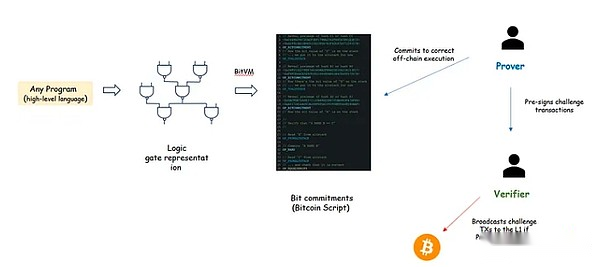
Bitvm
Bitvm is a unique effort to expand the Bitcoin L1 function.This concept is based on Taproot upgraded to Bitcoin.The concept of Bitvm is to expand the function of Bitcoin through the execution program under the chain, and ensure that it can be questioned on the chain by proven by fraud.Although BITVM seems to be used to achieve arbitrary logic under the chain, in fact, the cost of performing fraud proof on L1 has increased rapidly with the size of the program.This problem limits BITVM’s applicability of specific problems, such as trusted BTC bridges.Many upcoming Bitcoin L2 uses BITVM for bridge implementation.
Bitvm operation simplified picture
Sidechains
Another way to solve Bitcoin limited programming is to use the side chain.The side chain is a completely programmable independent blockchain, such as compatible with EVM, trying to maintain consistency with the Bitcoin community and provide services to the community.Rootstock, Blocksteam’s liquid and Stacks V1 are examples of these side chains.
The Bitcoin side chain has been in the years, but it has achieved limited success in attracting Bitcoin users.For example, less than 4,500 BTCs from the liquid bridge to the side chain.However, some of the DEFI applications built on these chains have achieved some success.For example, Sovryn and Alex on the Rootstock and Stacks.
Bitcoin L2
Bitcoin L2 is becoming the focus of building a Bitcoin -based basis.They can provide the same advantages as the side chain, but they have security guarantees from Bitcoin basic layers.The true representative of Bitcoin L2 has always been controversial.In this article, we avoided this debate, but discussed the main consideration of how to make L2 and L1 fully coupled, and discussed some promising L2 projects.
Bitcoin L2 Requirements
L1’s security
The most important requirement of Bitcoin L2 is to obtain safety from the security of L1.Bitcoin is the safest chain, and users expect security to expand to L2.For example, this is the case.
This is why the side chain is classified, and they have their own safety.For example, the security of Stacks V1 depends on the STX token.
This security requirement is difficult to achieve in reality.In order to allow L1 to protect the security of L2, L1 needs to perform certain calculations to verify the behavior of L2.For example, Ethereum Rollup obtains security from L1, because Ethereum L1 can verify zero -rollup or verify of the Optimistic Rollup.Bitcoin basic layer currently lacks computing capabilities to perform any of the above -mentioned operations.Some people recommend adding a new operating code to Bitcoin to allow the basic layer to verify the ZKP submitted by Rollup.In addition, proposals such as BITVM tried to achieve fraud proof without changing L1.Bitvm’s challenge is that the cost of fraud may be very high (hundreds of L1 transactions), which limits its practical application.
Another requirement for L2 to implement L1 level security is the unchanged record of L1 with L2 transactions.This is called data availability (DA) requirements.It allows observers who only monitor the L1 chain to verify the L2 status.Through the inscription, the record of L2 TX can be embedded in Bitcoin L1.However, this has another problem to scalability.Due to the block time limit of 4MB per 10 minutes, the data throughput of Bitcoin L1 is limited to about 1.1 kb/s.Even if L2 transaction is highly compressed to about 10 bytes/TX, assuming that all L1 transactions are used to store L2 data, L1 can only support a combination of about 100 TX/second combination L2 throughput.
Trust from L1 Trust Bridge
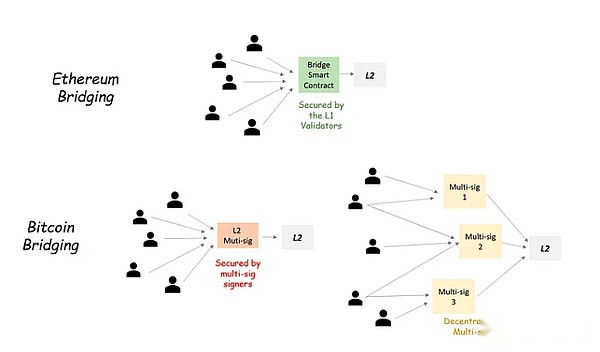
In Ethereum L2, the bridge with L2 is controlled by L1.The bridge receives L2, also known as the transfer, which actually means that the asset is locked on L1 and casts a copy of the asset on L2.In Ethereum, this is realized through the L2 smart contract.The smart contract storage bridge is connected to all assets of L2.The security of smart contracts originated from the L1 verification device.This makes the bridge of L2 a safe and trustworthy.
In Bitcoin, it is impossible to have a bridge protected by the entire L1 miner.On the contrary, the best choice is to have multiple signature wallets that store L2 assets.Therefore, the security of the L2 bridge depends on the security of multiple signatures, that is, the number of signatures, their identity, and the safety of the hook and transferring operation.One way to improve the security of the L2 bridge is to use multiple multi -signatures, rather than using a single multiple signature to save all L2 bridge receiving assets.Examples in this area include TBTC, and multiple signatures must provide mortgages. If cheating, mortgages may be cut.Similarly, the proposed Bitvm bridge requires multiple signatures to provide security guarantees.However, in this multiple signatures, any signature can initiate a transfer transaction.Transfer and hook interactions are protected by Bitvm fraud.If the signature person performed malicious behaviors, other signatures (verifications) can submit a fraud certificate on L1, which will cause malicious signatures to be punished.
Bitcoin L2 map
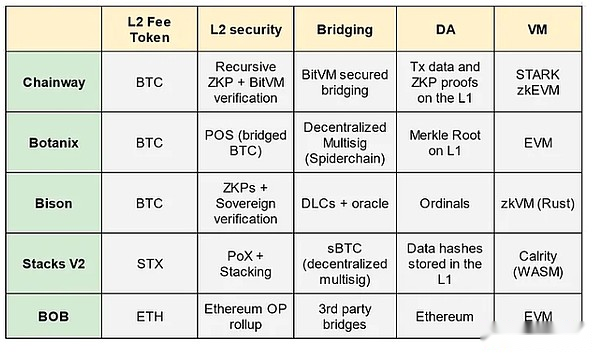
Bitcoin L2 project summary comparison
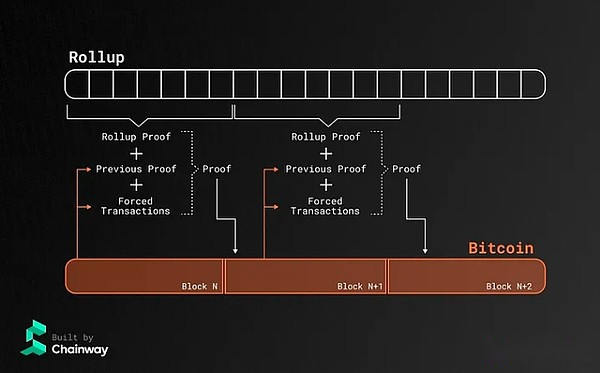
Chainway
Chainway is building ZK Rollup on the Bitcoin.Chainway Rollup uses Bitcoin L1 as a DA layer to store Rollup’s ZKP and status differences.In addition, Rollup uses proof of recursion so that each new certificate will concentrate on the certificate issued on the previous L1 block.The proof also aggregates “forced transactions”, which is a L2 related transaction broadcast on L1 to enforce it on L2.There are several advantages of this design.
The compulsory transaction guarantees that the Rollup sequencer cannot review L2 transactions and gives users the power of these TX by broadcasting these TXs on L1.
Using proof of recursive means that the proof of each block must verify the previous proof.This creates a trust chain and guarantees that the invalid proof will not be included in L1.
The Chainway team also discussed the correct execution of using BITVM to ensure the proved verification and transfer/transfer transaction.Using BITVM verification bridge transaction can reduce the trust assumptions of the trust of the ethnic minority factions.
Botanix
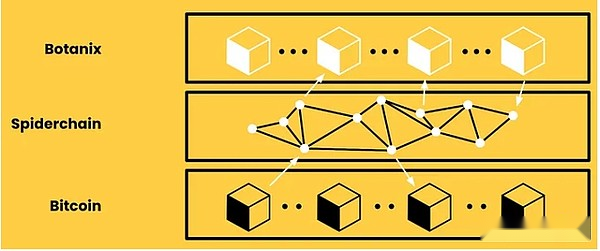
Botanix is building EVM L2 for Bitcoin.In order to improve the consistency with Bitcoin, Botanix L2 uses Bitcoin as a POS asset to reach a consensus.The L2 verification device earns fees from the transaction performed on the L2.In addition, L2 uses inscriptions to store the Merkle tree roots of all L2 transactions on L1.This provides some security for L2 affairs, because the L2 transaction log cannot be changed, but it cannot guarantee the DA of these transactions.
BOTANIX is processed from L1 by L1 by the decentralized multi -signature system network called SpiderChain.The signature of multiple signatures is randomly selected from a group of coordinators.Orchestrator locks user funds on L1 and signed a certificate to cast an equal amount of BTC on L2.The commander must pay the deposit to be qualified to play this role.If malicious behavior occurs, the security deposit will be greatly reduced.
BOTANIX has launched the public test network, which is planned to be launched in the first half of 2024.
Bison network
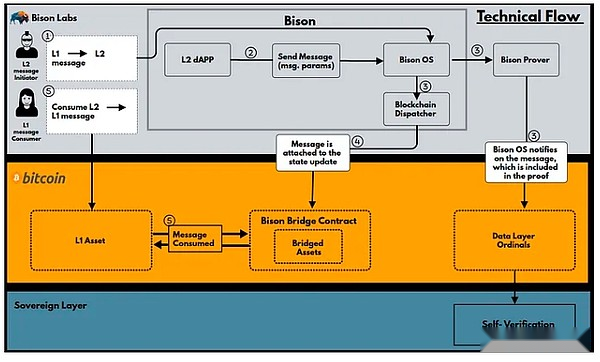
BISON’s Bitcoin L2 adopts sovereign ROLLUP style.BISON uses Stark to implement ZK Rollup, and uses Ordinals to store L2 TX data and generated ZKP to L1.Since Bitcoin cannot verify these proofs on L1, the verification work will be commissioned to users who verify ZKP in its device.
For the BTC bridge with L2, BISON uses Discreet Log Contract (DLC).DLC is protected by L1, but depends on external prediction machines.The prediction machine reads the state of L2 and transmits information to Bitcoin L1.If this prophecy machine is centralized, the prophecy machine can maliciously spend L1 lock -up assets.Therefore, it is very important for BISON’s final turn to decentralize DLC prophecy.
The BISON plan supports Rust -based ZKVM.At present, BISON OS has implemented many contracts, such as token contracts that can use BISON proof for proof.
Stacks v2
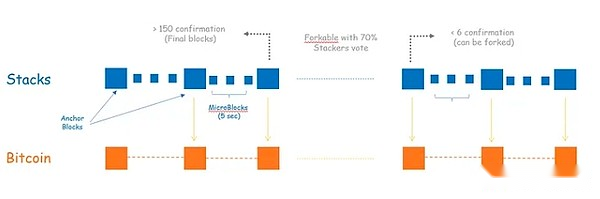
Stacks is one of the earliest projects that focus on expanding Bitcoin.Stacks is undergoing transformation to better consistent with Bitcoin L1.This discussion focuses on the upcoming Stacks V2, which is expected to be released on the main network in April 2024.Stacks V2 realizes two new concepts, which are improving the consistency with L1.The first version is the Nakamoto version, which updates the Stacks consensus to follow the Bitcoin block and the final nature.The second is the improved BTC bridge, called SBTC.
In the release of Nakamoto, the blocks in Stacks are mining by miners who promised BTC bonds on L1.When Stacks miners created a block, these blocks were anchored to Bitcoin L1 and received confirmation from L1 POW miners.When a block receives 150 L1 confirmation, the block is considered the final block and cannot be split in the absence of a non -fork Bitcoin L1.At this time, Stacks miners who mine the block will receive STX rewards, and their BTC bonds will be assigned to the network Stacker.In this way, any more than 150 blocks (about 1 day) Stacks block depends on the security of Bitcoin L1.For newer blocks (& lt; 150 confirmation), only 70% of Stackers support forks, the Stacks chain can split.
Another upgrade of Stacks is SBTC, which provides a more secure way to receive the BTC bridge to Stacks.In order to receive the asset bridge to Stacks, the user deposits its BTC into the L1 address controlled by L2 Stacker.When the deposit transaction is confirmed, SBTC will be cast on L2.In order to ensure the security of BTCs, Stackers must lock bonds exceeding the BTC value in the STX.The stack device is also responsible for executing the transfer request from L2.Transfer and hook requests are broadcast as L1 transactions.After confirming, Stackers destroyed SBTC on L2, and signed L1 TX in collaboration to release the user’s BTC on L1.For this work, Stackers won the miners’ margin reward they had discussed earlier.This mechanism is called transfer proof (POX).
Stacks is consistent with Bitcoin and requires many important L2 transactions (such as miner POX bonds and hook transactions) as L1.This requirement does improve the consistency and security of the bridge BTC, but due to the volatility and high cost of L1, it may lead to a decline in user experience.Overall, the upgraded Stacks design solves many problems in V1, but there are still some weaknesses.This includes the use of STX as a native asset in L2 and L2 DA, that is, the hash value of only trading and smart contract code on L1.
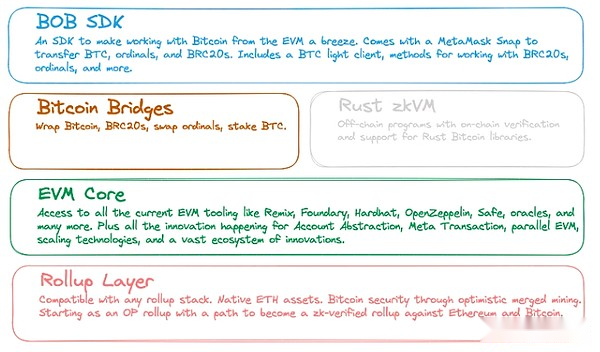
Bob
Bulid-On-Bitcoin (BOB) is an Ethereum L2 aimed to be consistent with Bitcoin.Bob runs as an Optimistic Rollup on Ethereum and uses the EVM execution environment to implement smart contracts.
BOB initially accepted different types of bridges BTC (WBTC, TBTC V2), but it is planned to use a safer two -way bridge with BITVM in the future.
In order to distinguish between other Ethereum L2 that also supports WBTC and TBTC, BOB is constructing the function of allowing users to interact directly with BOB BOB.Bob SDK provides a smart contract library that allows users to sign a transaction on Bitcoin L1.The execution of these transactions on L1 is monitored by Bitcoin Light Client.The light client adds the hash value of the Bitcoin block to the BOB to allow simple verification (SPV), that is, the submitted transaction has been executed and included in the block.Another function is an independent ZKVM, which allows developers to write RUST applications for Bitcoin L1.The correct execution proof can be verified on the Bob Rollup.
BOB’s current design is more suitable for describing as a side chain, not Bitcoin L2.This is mainly because the security of BOB relies on Ethereum L1, not the security of Bitcoin.
Bulid-On-Bitcoin (BOB) is an Ethereum L2 aimed to be consistent with Bitcoin.Bob runs as an Optimistic Rollup on Ethereum and uses the EVM execution environment to implement smart contracts.
BOB initially accepted different types of bridges BTC (WBTC, TBTC V2), but it is planned to use a safer two -way bridge with BITVM in the future.
In order to distinguish between other Ethereum L2 that also supports WBTC and TBTC, BOB is constructing the function of allowing users to interact directly with BOB BOB.Bob SDK provides a smart contract library that allows users to sign a transaction on Bitcoin L1.The execution of these transactions on L1 is monitored by Bitcoin Light Client.The light client adds the hash value of the Bitcoin block to the BOB to allow simple verification (SPV), that is, the submitted transaction has been executed and included in the block.Another function is an independent ZKVM, which allows developers to write RUST applications for Bitcoin L1.The correct execution proof can be verified on the Bob Rollup.
BOB’s current design is more suitable for describing as a side chain, not Bitcoin L2.This is mainly because the security of BOB relies on Ethereum L1, not the security of Bitcoin.
Satoshipmm
Satoshipm is another project to launch ZKEVM Bitcoin L2.With the launch of the test network in early January, the project suddenly appeared.The technical details of the project are very small, and it is not clear who the developers behind the project are.SATOSHIVM’s minority documents pointed out that the use of Bitcoin L1 for DA is used to resist the review by supporting the ability of broadcast transactions on L1, and use BITVM -style fraud certification to verify L2 ZKP.
In view of its anonymity, there are many controversy in the project.Some surveys have shown that the project is linked to BOOL Network. BOOL Network is an older Bitcoin L2 project.
Entrepreneurship opportunities in Bitcoin L2 paradigm
The space of Bitcoin L2 has brought some entrepreneurial opportunities.Leaving aside the obvious opportunity to build the best L2 for Bitcoin, there are several other entrepreneurial opportunities.
Bitcoin da layer
Many upcoming L2 aims to enhance consistency with L1.One way is to use L1 for DA.However, considering the strict restrictions on the size of the Bitcoin block and the delay of the L1 block, L1 will not be able to store all L2 transactions.This creates opportunities for Bitcoin’s specific DA layer.Existing networks (such as Celestia) can expand to fill this gap.However, Creating DA solutions under the chain that depends on Bitcoin security or BTC collateral can improve the consistency with the Bitcoin ecosystem.
MEV extract
In addition to using Bitcoin L1 for DA, some L2 may choose to entrust L2 transactions to sorters binding BTC, and even entrust to L1 miners.This means that any MEV extraction will be entrusted to these entities.In view of the ability to complete this task, Bitcoin miners do not have the ability to complete this task. This is an opportunity for companies like Flashbot to focus on Bitcoin L2 and private order streams.MEV extraction is usually related to the virtual secrets used, and given that the Bitcoin L2 does not agree with the agreed virtual machine, there may be multiple participants in this field.Each focuses on different Bitcoin L2.
Bitcoin income tool
Bitcoin L2 needs to use BTC mortgages to select verification, DA security and other functions.This creates income opportunities for holding and using Bitcoin.At present, there are some tools to provide such opportunities.For example, babylon allows pledged BTC to protect the security of other chains.With the booming development of the Bitcoin L2 ecosystem, a platform for aggregating BTC native income opportunities is facing huge opportunities.







