Author: Four Pillars; Translation: 0xjs@作 作 作 作 作 作
Point
-
Intellectual property (IP) management in the digital field is facing major challenges, and new intellectual property management systems need to be developed to cope with advanced AI technology and the emergence of various IPs of these technologies.
-
Creators can register their IP on Story Protocol in order to easily track the usage of their IP and force the revenue rights of derivative IP via code.This provides a structured method of allocating IP registration, license and franchise fees.
-
Through the agreement to protect and enhance the system of creators IP, Story Protocol will lay the foundation for the further expansion of the digital world IP industry, and eventually become the liquidity layer of programmable IP.
1. New paradigm of cooperation
Cooperation is the key to music.The completion of a song requires the efforts of many people, and it is difficult to complete it by one person’s thoughts or efforts.The latest progress of the Internet, social media and AI technology has greatly changed the paradigm of music collaboration.
1.1 Internet: cooperation between artists

Source: DRAKE’s Donda
Before the emergence of the Internet, artists must appear in the same studio in order to create music together, which limits their scope of cooperation.However, with the emergence of the Internet, the melody written on its own computer can be sent to the other party in the form of WAV files or FLP project files without any physical restrictions.
How many people have participated in Kanye West’s Donda’s song “Hurricane”?According to sources, a total of 43 people participated in the production, 6 of them were responsible for the lead singer, 11 people were responsible for production, 18 were responsible for the project, and 23 people were responsible for composition and lyrics.
Although not like Kanye West’s “Hurricane”, it is a common trend to participate in a song.For example, if you look at Destroy Lonely’s song “No STYLIST”, you will find that CXDY and Chef9thegod contribute to this song. Among them, Chef9thegod created the overall melody, and CXDY created the drum line.This division of labor is naturally professional because each composer is developed with the development of the industry, but I think the commercialization of the Internet is the biggest reason.
1.2 Social media: cooperation between artists and fans
Source: Sabrina Carpenter @ Spotify
With the progress of the Internet and social media, it has begun to significantly affect the spread of music after the release of music.
At present, the most important platform of the music industry is TIKTOK.Because short video length and NightCore trend (Note: NightCore is a music creative method, it increases about 1.35 times the speed of sound and increase the sound tone), KOL began to create TIKTOK with the “acceleration” version of the existing songs.In fact, the unofficial Speed UP version has always existed on YouTube, but the popularity of these videos on TIKTOK has prompted artists and record companies to publish the Speed UP version as the official track.
In addition to TIKTOK, the personal selected playlists on YouTube and Spotify also play an important role in promoting and discovering music.There are so many music, I am convinced that I am not the only person who has experienced this: listening to the playlist planned by people with tasteful people on YouTube, found a great song in the middle, and then returned to find an artist.For example, although the playlist (https://www.youtube.com/watch?v=75kysstfabqq) only includes Korean independent artists, it is very popular, with more than 12 million viewing and more than 12 million comments.Today, the popular playlist included in Spotify has become a key factor in the success of the track.
1.3 AI: The boundary between fuzzy artists and fans
Source: @jenny ____ ai
Drake and The Weeknd’s song “Heart on My Sleeve” was the hottest song in the second quarter of 2023, but the problem was that it was not released by two artists, but an anonymous Tiktok user called “Ghostwriter977″.The voices of the two artists are produced in AI.”Heart on My Sleeve” was released on all music streaming platforms on April 4 and was removed from UMG on April 17.In a short period of time, it received 600,000 playback on Spotify, 275,000 views on YouTube, and obtained more than 15 million views on Tiktok.More than 1,000 Tiktok videos were produced, and Billboard estimated that the total revenue of this song was about $ 9,400.If Drake or UMG has created this song itself, this will be a huge viral marketing measure, but if they do not, then it proves that we are at the beginning of a new era. Anyone can use any of the help of AI.The sound of celebrities they want to create songs.
In fact, Voicify allows you to easily create your own AI cover songs, and Mubert allows you to create your own emotional music.Splice is the largest music sample service. Now uses the AI model trained on its library to find the best combination of samples and make suggestions.
1.4 Changes in the supply chain
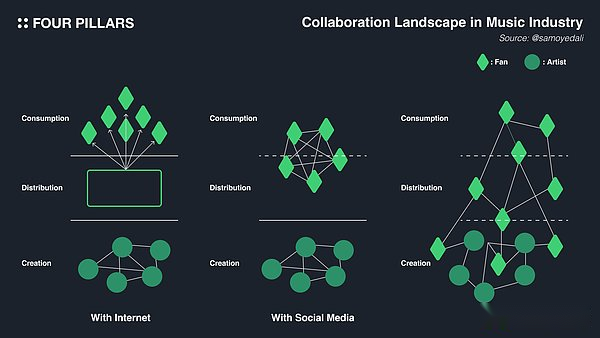 All in all, the emergence and commercialization of Internet, social media, and AI make the cooperation between people in the music supply chain easier and more active.With the emergence of the Internet, the cooperation between artists has increased.With the emergence of SNS, the cooperation between artists and consumers has increased; through AI, the boundaries between artists and consumers are becoming blurred, and the scope of cooperation is also expanding.In particular, before AI, the cooperation between artists and consumers is limited to issuance and promotion, but now it will become the conventional part of music creation.For example, if Drake’s fans do not like his new album, they will start using Drake’s sound of DIY their own style songs.
All in all, the emergence and commercialization of Internet, social media, and AI make the cooperation between people in the music supply chain easier and more active.With the emergence of the Internet, the cooperation between artists has increased.With the emergence of SNS, the cooperation between artists and consumers has increased; through AI, the boundaries between artists and consumers are becoming blurred, and the scope of cooperation is also expanding.In particular, before AI, the cooperation between artists and consumers is limited to issuance and promotion, but now it will become the conventional part of music creation.For example, if Drake’s fans do not like his new album, they will start using Drake’s sound of DIY their own style songs.
2. Cultivation conflict
Cooperation is an important foundation for culture and industry, but as there are more and more subjects participating in cooperation, problems have increased significantly.This is mainly caused by credit issues.
2.1 Cultivation of production
As the cooperation between producers becomes more and more frequent, it is not uncommon for unknown producers to be recognized.For example, Kanye West made a rhythm for NAS’s “Poppa Was A Playa” in the early days, but his mentor D-Dot did not attribute to him.Recently, a German bulletin producer named PVLACE was criticized by previous colleagues Gunboi and was criticized by his previous colleague Gunboi and sold them in his own name.There are two main reasons for these things.
-
Tracking creative difficulties: Beatmaker often sends their samples to different producers, and they cannot track whether their samples have been used by producers.Therefore, it is difficult to know if the malicious producer does not authorize your sample and does not pay you.It is also unrealistic to prove that your sample is used for this track.
-
The complexity of the copyright process: For big -name producers, some people and the company will deal with the legal issues of copyright for them, but as an individual, it is not easy to deal with this process.For example, if your music wants to get paid globally, you must join multiple copyright institutions in each country, which is expensive and time -consuming, let alone the problem of dual contracts.Therefore, in terms of cooperation, unknown producers are more likely to do what the famous producers tell them.
Due to these difficulties, it is not easy to maintain 100%of the rights when cooperating.
2.2 Cultivation of distribution

Source: routenote
In fact, the top Tiktok Internet celebrities and YouTube creators are paid by the record company to create publicity content for specific songs.Of course, these creators are the starting point of viral videos, but viral communication requires the help of other personal creators to continue.Only by creating and maintaining viral communication from the bottom up through individuals who create Tiktok and YouTube videos for entertainment, fans or self -actualization.
However, it is difficult for these temporary KOLs to get their own credit for their virus influence on a specific track.TIKTOK requires high powder to broadcast the Lord and Watch to make a profit through the video itself, and the area available is limited.On YouTube, the music playback list video cannot be profitable through ADSENSE, so it is difficult to profit through them unless they cooperate with external brands, and this only well -known account can be achieved.In Spotify, the inside curator has high paid, but the external curator has no way to make money.
All these platforms have one thing in common: they reward some well -known creators, but they do not reward them are often small individual creators with virus video pillars.
2.3 Cultivation of Sound
The number of coverage of sound creation generated by artists uses AI is unlikely to decrease in the future.In this case, artists and record companies need to be able to protect their rights.The main record company has launched a war with AI without permission to use its track library, but this is unlikely to prevent this trend.Artists like Grimes have adopted the opposite method. They did not let the sound of AI generated open for easy use. Instead, they forced to divide the ratio of 5: 5 for commercial use taxes.
3. Basic issues
In fact, the changes and problems discussed so far are the same in the entire IP industry, not just in the field of music.I think the root cause of these problems is the lack of IP management system based on the Internet.
3.1 Digital IP Supervision
In the United States, since the 1990s, the Digital Millennium Copyright Law (DMCA) has been trying to cope with the issue of the digital age.DMCA is widely included in the following terms:
-
Prohibit technical protection measures: prohibit technical protection measures to prevent unauthorized access and copy digital content.
-
Protecting online service providers: It is difficult for online service providers such as YouTube and other online service providers to verify whether the content published by users violate copyright.If online service providers abide by certain conditions, DMCA will be exempted from its copyright infringement liability.
-
Notice and deletion program: If the copyright owner finds the copyright infringement, they can notify the online service provider and must delete the content.
As far as we know, most online platforms follow the provisions of DMCA to monitor copyright infringement.For example, Youtube’s Content ID system is deeply influenced by DMCA.This is a system that can automatically check the uploaded videos based on YouTube’s database to see if they violate the copyright. If the copyright violates the copyright, the copyright owner can take various actions.If the system is missed and the copyright owner requested to delete manually, the platform can still delete the video according to DMCA.
3.2 Limitation of Digital Millen Rights Copyright Act (DMCA)
In my opinion, DMCA has two major problems.
First of all, DMCA is outdated.Although the rights of the original creators are respected, it is good, but social media and AI have brought more collaboration and secondary creations, but DMCA has not kept up with these changes.
Secondly, DMCA does not provide specific guidance or methods to how to manage and track its intellectual property rights for copyright owners. Therefore, although DMCA theoretically aims to protect the rights of the original author, it fails to do this in practice.Unless it is part of a large company, copyright owners must use third -party services and resource at their own expense.
3.3 What do we need
DMCA played its role in the early days of the Internet.But now we need a new infrastructure.I said infrastructure, not supervision, because in my opinion, supervision is just to prevent certain behaviors, and we have not been in that era.The digital native IP infrastructure suitable for the current trend should be achieved:
-
Provide tools and guidance for the original author to track and monitor the use of his works.Simply speaking, “If your copyright is violated, you can delete it at any time.” This does not take into account the actual situation.You need to provide a method or tool for anyone to easily view the actual use of its copyright.
-
We need to ensure that both original creators and secondary creators can benefit.The original authors should be able to ensure that their rights are not violated, and secondary creators should be able to confidently create existing IPs and claim credit for them.
4. Story protocol

Source: Story Protocol
In short, Story Protocol is an infrastructure that provides the framework of IP registration and expansion of these IPs on the chain.Story Protocol aims to be a new infrastructure based on digital IP.It is not to replace the existing leftover regulations and infrastructure, but as Arxiv.org has become an increasingly important parallel mechanism of academic papers, we believe that Story Protocol can play a similar role for digital IP.
4.1 Story protocol architecture
Story Protocol adopts the structure inspired by TCP/IP to become a programmable IP layer.It is mainly composed of a data layer (known as a noun) and a functional layer (called a verb (module)), and above it is an ecosystem that uses the story protocol.
-
Noun (NOUNS): As a data layer, including the core elements of the story protocol, such as IP assets, licenses and taxes.
-
Verbs: This layer defines various operations that can be taken to the data defined in the noun.
4.2 Noun (NOUNS)
Let’s discuss the key elements defined in the noun in the story agreement.
4.2.1 IP assets
In Story Protocol, IP is called IAsset, which represents NFT on the chain describing IP and related iPaccount.Unlike static NFT, iPasset is essentially programmable, as the basic unit of the Story protocol.IASSETS contains metadata such as IP type, creator, IPA number.An important attribute to be noticed is iPaccount, because the address of the iPaccount as the only ID is included in IAsset, which helps to easily manage and track related information.information.
4.2.2 ipaccout
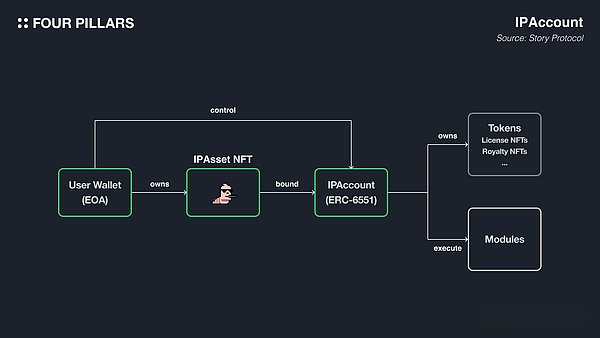
IPaccounts is an account based on ERC-6551 modified version, paired with each IASSET, and transferred with the ownership of IASSET.Due to ERC-6551, they can hold tokens such as licenses NFT and tax NFT and perform various modules.All interactions in Story Protocol are carried out around iPaccount to support key functions such as licenses, tax sharing and mixing.The core function of iPaccount is to call any VERB (module) through the Execute () function.
4.3 Module (VERBS)
The main role of the module is to change the data/state related to IP.Names recorded data related to IP, and modules (VERBS) provide a framework for interacting with this data.In addition to basic Modules, Story Protocol also allows ecosystem developers to build HOOKS based on the Module framework.Let’s analyze the main modules:
4.3.1 License module
Story Protocol can be regarded as a social graph that defines the relationship between IP on the blockchain, which permits how derivative IP is connected to the social map.The creators in Story Protocol can re -create various IPs into videos, images, etc.In the process, the right to specify the IP is very important, and it is managed by the permit module.
IP rights are expressed in the form of license NFT, including information such as ID and strategy ID of iPasset, and identified by the unique license ID.License NFT follows the ERC-1155 standard and allows multiple NFTs.Policy definition of licensing clauses related to intellectual property rights, such as the commercial use or transferable of the license.Intellectual property owners can choose from multiple strategies through combination.
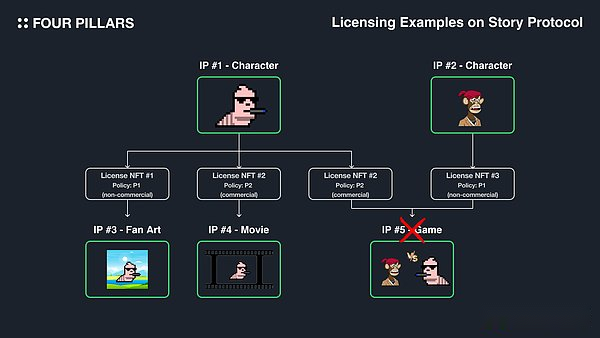
Only the holder of a specific IP license NFT can create derivative IP from the parent IP, and register the derivative IP under the parent IP, the license NFT will be burned.For example, assuming the owner of Larva LADS registered IP #1 and casts a license NFT #1 with non -commercial use policies (P1), and two licenses with commercial use policies (P2) NFT #2.The owner of the license NFT #1 can record it to register non -commercial fan art as an IP #3.Similarly, the owner of the license NFT #2 can register the commercial movie as IP #4.
Derivative IP can also be registered under two mother IPs, so that innovative content can be created through a combination of various IPs.However, if the License NFT of the two parent IP has a conflict strategy, the derived IP cannot inherit the two.For example, if someone intends to create a business game with the role of LARVA LADS and Bayc of IP #5, but the owner of IP #2 only follows the non -commercial P1 policy to issue licenses NFT, but it cannot register.
4.3.2 version tax module
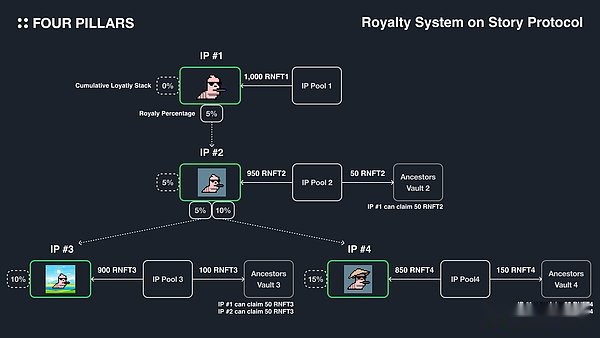
Story Protocol introduced a function that forcibly charging IP fees through code, solving common problems in the traditional IP environment.You can define the tax strategy between the two IASSETs, and set the minimum tax percentage of the parent IASSET from its derived IP.Each iPasset has an IP pool with 1,000 ERC-1155 version tax NFT. The holder can share the income generated by the relevant IP pool in proportion.
For example, if IP #2 is registered with a 5% version of IP #1, 5% of 1,000 RNFT2 (50 RNFT2) will be stored in ANCESTORS VAULT 2, and IP #1 will have the right to obtain these 50 RNFT2.Similarly, if IP #4 is registered, it will charge 10% tax on IP #2, and 15% (5% from IP #1, 10% from IP #2) in 1,000 RNFT4 (150 RNFT4) will be stored in Ancestors Vault 4, IP #1 has the right to request 50 RNFT4, IP #2 has the right to request 100 RNFT4.This mechanism allows the mother IP to ask for part of the income generated by its derivative IP.
Although tracking the use of IP in the digital field and charging version tax have always been challenging, Story Protocol has successfully solved this problem.However, with the deepening of the IP relationship tree, the percentage of accumulating franchise fees may increase significantly, which highlights the importance of choosing the appropriate fees for the appropriate charter.
4.3.3 Controversy module
If malicious users use other people’s IP, what will happen to claim that the original IP is created?To solve this problem, the Story protocol includes a dispute module for mediation disputes.If malicious activities are confirmed, illegal IP and its owners will face penalties.
4.4 Registration
IPACCOUNT storage information related to specific IP, while registration is used to store the global state of Story Protocol.The type of the registration center includes:
-
IASSETREGISTRY: The iPasset registered in the management protocol and deployed the corresponding iPaccount.
-
Registration module: the global list of managing and updating modules and HOOKS that has not been registered.
-
License registration: Management and license NFT interaction and all information related to the license.
4.5 potential users
4.5.1 IP owner
If IP owners can register their intellectual property as iPassets (intellectual property contracts) on Story Protocol to protect their rights and encourage derivatives, then they have no reason not to use it.
4.5.2 Creator
For creators, if their favorite IP has IASSET on Story Protocol, and the benefits of receiving the fair version of the tax offset the trouble or difficulty of using the protocol, then there is no reason not to use it.
4.5.3 Investor
If investors want to invest in specific IPs, they can easily implement Loyalty NFT through platforms such as OpenSea or Blur.However, in order to seamlessly follow this process, first of all, competitive IPs must be registered on Story Protocol. Secondly, Story Protocol must be able to effectively manage and track the under -chain tax.
5. Look at the future
Story Protocol currently lacks the ability to take legal operations on IP copyright infringement, and it is not simple to track the tax on the chain.So, can Story Protocol become a new infrastructure of Internet IP?I can’t say it for sure.Nevertheless, Story Protocol’s concern is true, and they do exist on the Internet.
The emergence of technology -based parallel institutions will be an important trend in the future, giving people more choices, and stimulating the development of existing infrastructure.Story Protocol is very suitable for the role of parallel organizations, especially in the IP field.If Story Protocol can identify the clear needs of the IP owner and accurately locate, we may soon see a copyright owner.Create and get the corresponding version of the tax environment.