
Original title: New path of cross -chain communication: Layerzero and Eigenlayer launched CryptoEconomic DVN framework
Author: YBB Capital Researcher AC-Core
TLDR
-
CryptoEconomic DVN framework combines Layerzero’s cross -chain message with Eigenlayer’s economic security and incentives.
-
The DVN framework runs through a structured process, divided into three stages: verification, rejection and punishment.
-
The cooperation between Layerzero and Eigenlayer deepened the decentralization of DVN by accepting ETH, Zro, and Eigen as the collateral, creating new growth opportunities for the two token.
-
The CryptoEconomic DVN framework is expected to enhance the security of the entire blockchain ecosystem.
1. Understand narrative: iteration upgrades of Eigenlayer and Layerzero

Picture source: layerzero official
According to the announcement on October 2, 2024, Layerzero Labs cooperated with EIGEN Labs to launch CryptoEconomic DVN Framework to provide encrypted economic security for cross -chain messages.Under this framework, developers can deploy their own DVN on Eigenlayer, and introduce the incentive mechanism to enhance the security and reliability of cross -chain messages.
In short, CryptoEconomic DVN Framework combines Layerzero’s cross -chain security mechanism with EIGENLAYER’s re -encrypted economic model.Its core goal is to use Eigenlayer’s encrypted economic framework to provide higher security and incentives for decentralized verification networks (DVN).
1.1 The first stage: laid the foundation for CryptoEconomic DVN and Layerzero V2
Layerzero is not only a cross -chain asset bridge, but also a cross -chain communication protocol that does not need to be trusted.It uses ultra -light nodes to transmit cross -chain messages.
Layerzero V2 architecture is divided into three core components: protocols, standards and infrastructure.
1. Protocol
Layerzero’s protocol part is consistent in all supported blockchains, maintaining unable to tamper and no license characteristics to ensure anti -examination and long -term stability.It consists of two main components:
-
Endpoints:The unsatisfactory and non -upgraded smart contracts deployed on each blockchain are the core of the Layerzero protocol.These endpoints provide standardized interfaces for applications to manage security configuration and send/receive cross -chain messages.
-
MESSAGELIBS: These libraries are connected to the endpoint to process the verification and communication of cross -chain messages.During the update, MESSAGELIBS will be attached rather than replace, thereby ensuring backward compatibility and allowing developers to use the old versions if necessary.
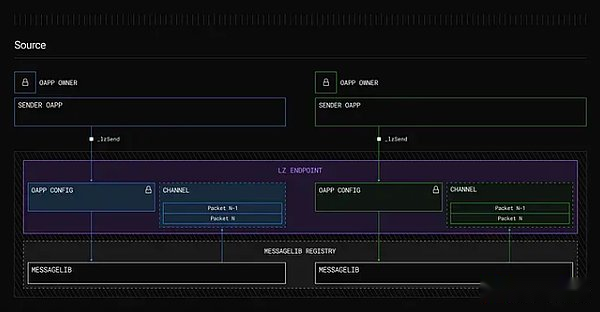
Image source: layerzero endpoint description
2. Standard
Layerzero’s standard enables developers to build unified applications and tokens across multiple blockchains.This ensures cross -chain consistency and scalability.
-
Contract standard:Layerzero provides standards such as OAPP (all -chain application) and OFT (all -chain tokens). These standards have expanded existing smart contract standards, enabling developers to quickly create applications running on all Layerzero supported by the blockchain supported by Layerzero.And token.
-
Message package:These data packets transmit data and commands between the blockchain, including random numbers, source/target chain IDs, and effective loads.This structure ensures the accuracy and security of cross -chain message transmission, even if it is across EVM and non -EVM chains.
-
Design mode:AB, ABA, Combination AB and other design patterns to help developers build efficient cross -chain interaction and user experience.

Image source: combination ABA design mode
3. Infrastructure
Layerzero’s infrastructure is open and modular, allowing any entity to join the network to verify and execute transactions.
-
Detainer verification network (DVN):These networks verify cross -chain messages.Applications can choose appropriate verification networks to meet their security needs and avoid being locked to a single authenticator network.
-
Executive:Responsible for ensuring the entity executed on the target chain on the target chain.The executor simplifies the user experience by allowing users to pay GAS only on the source chain.
-
Safe stack:Each application can be configured with a unique security stack, including DVN, executor, and security preferences to provide highly customized security solutions.
To understand the CryptoEconomic DVN framework, we must understand the role of DVN in Layerzero V2:
-
DVNResponsible for verifying cross -chain messages.
-
Openness:Anyone can create or develop DVN to provide various verification methods.
-
Customized security:Applications can choose DVN according to their security needs.
-
DVN combination:Applications can be configured with multiple DVNs to verify messages, such as “1 of 3 of 5” configuration.
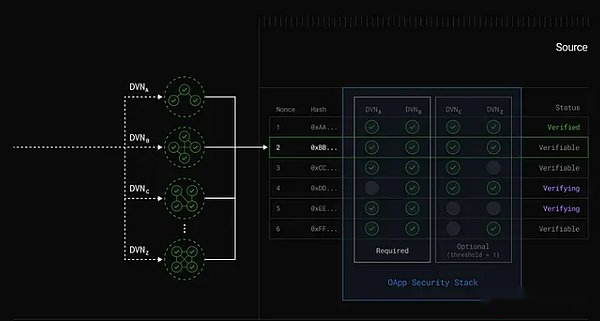
Image source: DVN’s location in the V2 architecture
1.2 Phase II: CryptoEconomic DVN, which is protected by Eigenlyer
EIGENLAYER consists of a smart contract, allowing users to “re -pledge” its ETH or mobile pledged token (LST), thereby enhancing the security and decentralization of modular blockchain networks.In essence, Eigenlayer sells Ethereum security for a wider range of ecosystems.Key aspects include:
1. Native pledge:Make verification multiple commitments to ensure that all promises have solvency.
2. Reconstruction of liquidityTheThe tokenization of pledged assets is provided to release liquidity.
3. AVS economy:A decentralized system combined with technology and trust structure.
4. Massive Rollups:Unlimited extensions are achieved through EIGENDA and other mechanisms.
5, trustworthy application:To maximize the promise and provide Ethereum security level decentralized services.
Therefore, EIGENLAYER expands Ethereum security models by providing modular and scalable solutions, thereby enhancing decentralized networks.
2. Token Economic Empowerment: Layerzero X Eigenlayer cooperates, empowering Zro and EIGEN as mortgage assets
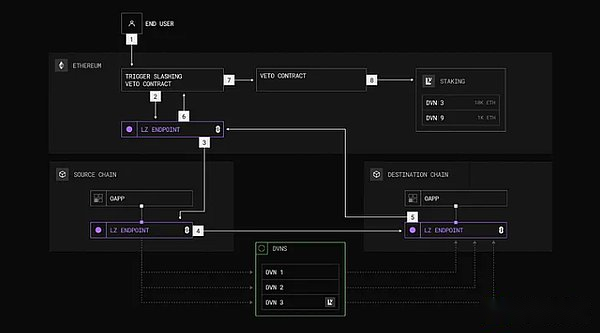
Photo: pledge, verification, rejection and punishment process
In short, the encrypted economic distributed verification network (DVN) enhances cross -chain security through three key ways:
1. Economic security:DVN introduced the punishment mechanism.If DVN can do or make mistakes, its pledged assets may be punished.This economic model motivates DVN to take responsible actions, because improper behaviors can lead to major financial losses, thereby promoting a sense of responsibility and security.
2. The security defined by AVS:Each active verification service (AVS) defines the types and punishment conditions that can be pledged.This flexibility allows different types of DVNs (such as ZKP, intermediate chain or authoritative certificate) to enhance security through additional mortgages, thereby increasing economic deterrent to malicious behavior.
3. No need to permit security:Anyone can contribute to the security of DVN through pledge assets, so that the system is more open and tolerant.DVN can choose to accept any assets (such as ZRO, ETH, or EIGEN) as mortgages, thereby expanding security options and promoting decentralization.
The CryptoEconomic DVN framework is an open source system that aims to enhance the security of decentralized verification network (DVN) through economic incentives based on token.It uses Layerzero’s DVN to verify message and add additional security layers.The framework runs through four key mechanisms: pledge, verification, rejection, and reduction.
-
Pledge:Verifications (pledges) locked to tokens such as ZRO, EIGEN, or ETH as mortgages in the DVN active verification set (AVS).These pledge funds can inspire authenticants to act honestly because improper behavior may lead to punishment.
-
verify:Users or applications can trigger cross -chain round trip messages (for example, Ethereum → Source Chain → Target Chain → Ethereum) to verify whether the hash recorded DVN matches the hash on the chain.If matching, the process ends.
-
reject:If there is a situation that is not matched, start the refusal process to allow the toke holders to vote for whether to punish the pledged assets of DVN.This step can prevent errors caused by non -malicious issues such as blockchain reorganization.
-
punish:If it fails to fail, confirm malicious behavior or verification errors, DVN’s pledged assets will be cut as punishment.
The framework is divided into three stages of operation:
1. Verification—— Use independent DVN to verify messages on multiple chains to ensure fairness.
2. Reject——If found differences, the contract will be triggered, allowing token holders to vote for punishment DVN.
3. Punishment——If the process fails, DVN’s pledged assets will be punished for malicious behavior or verification errors.
3. CryptoEconomic DVN framework outlook

With the maturity of Ethereum infrastructure and the firm establishment of the multi -chain pattern, cross -chain communication security is still a major challenge.The key innovation of the CryptoEconomic DVN framework is to use AVS to provide core components for DVN to define pledge assets and punishment conditions.In the long run, it can help improve the security of cross -blockchain.However, balance security and flexibility are still challenges that the entire industry must solve.
There is no doubt that the CryptoEconomic DVN framework represents mutual empowerment and cooperation between Layerzero Labs and Eigen Labs.From a technical point of view, it has introduced guarantee measures through pledge, punishment, verification, and rejection mechanism.But from an economic point of view, this cooperation is still the expansion of POS pledge rewards.
Through cooperation with Eigenlayer, Layerzero deepened the decentralization of its DVN and accepted ETH, ZRO, and Eigen as a collateral, and created a new growth cycle for these two token.Layerzero provides a technical foundation, and Eigenlayer provides funds, reward verifications, and encourages the honesty in the economic system.








