Author: JW, Four Pillars researcher; Translation: Bit Chain Vision Xiaozou
Abstract:
-
There are three basic components of modern encryption wallets: key management for processing the encryption key, accounts for user identity verification and interaction, and interfaces for user participation.Each part has different challenges and innovations, which jointly shaped the overall wallet experience.
-
Key management has developed from simple private key management to more complicated solutions: Shamir’s Secret Sharing solution divides the key into multiple fragments, Threshold Signature Schemes supports multi -party computing without reconstruction of key reconstruction, TrustedDEDEXECUTION Environment (trusted execution environment) uses hardware -level isolation.Projects such as Privy, Particle Network, and Turnkey use these methods in practice.
-
Account abstract By converting complex accounts into programmable interfaces, the blockchain interoperability is more user -friendly.This makes functions such as GAS transactions, social recovery and customized security settings, making it easier for blockchain technology to be used by mainstream users, as displayed in projects such as ABSTRACT’s Global Wallet.
-
Chain abstraction allows a variety of blockchain to be invisible to end users, thereby solving the complexity of cross -chain interaction.Users can manage the balance across the chain, use any token for payment, and seamlessly interact with multiple blockchain while maintaining decentralized characteristics and security.One Balance’s Credible Accounts system shows us a way to implement these functions.
-
The encrypted industry is rapidly shifting from desktop to mobile priority development models. Platforms such as Zora lead the transformation by providing complex mobile experiences, while maintaining the complexity of the blockchain at the bottom.
-
The future of wallet development is to simplify the user experience while not harming security.The road to a wider range of adoption requires moving from the private key to social login. At the same time, it must have a seamless experience comparable to the web2 application, and retains the core advantage of the blockchain.
1. Introduction to wallet stack
For encrypted applications for end users, wallets are far more than the digital containers of assets -they are the portal to the entire blockchain experience.Each interaction with encrypted applications, from initial settings to daily transactions, must pass through the wallet of users.This makes wallets not just a feature, but the most basic infrastructure that determines the user’s blockchain experience.
Creating a new wallet and depositing funds in the wallet requires users to invest a lot of time, energy and risk tolerance.Although this high threshold has pushed the user’s acquisition cost, it has also created a powerful retain mechanism -once the user uses a wallet, he is likely to always use this wallet without choosing it without choosingSwitch to other wallets to experience this process again.
However, although encrypted wallets have played a key role, it has won reputation due to the most challenging user experience in terms of technology.Users who use encrypted wallets for the first time often find that they are lost in the maze of technical concepts -private key, public key, and help words -there is almost no room for making mistakes.This complexity has caused many people to question whether to make full use of blockchain technology to really need such a steep learning curve.
However, this situation is finally changing.After years of stagnation, wallet technology is experiencing a great rejuvenation because people pay more and more attention to the user experience.Hyundai wallet is being innovated through social boarding certification, biometric verification, and GAS fees abstraction. A bridge is set up between the convenience of web2 and the security of the web3.These development eventually make the encrypted wallet closer to people’s expectations of user -friendly experiences of modern applications.
The technical infrastructure of the blockchain wallet contains three basic layers:
-
Key management:This basic layer is responsible for arranging the production, storage and recovery of the encryption key.It contains key technical decisions about encryption methods, security protocols and access control.Modern solutions have surpassed basic key storage, including multi -party computing (MPC), Shamir Secret Sharing (SSS), social login integration, and mobile friendly Passkey and other methods.
-
Account:This layer defines the user recognition method and the user’s interaction with the blockchain network.It covers a complex concept such as the basic concepts such as external accounts (EOA) to the smart contract account (SCA).Each type of account can be enhanced through different functions -from GAS fees sponsorship and multiple signature requirements to customized transaction control -this ultimately determines the functionality and generalability of the wallet.
-
interface:This is where users interact directly with the blockchain.Whether it is expanded by browser, mobile APP or web interface, this layer provides key points for users to operate, such as signing transactions, management assets, and connecting DAPP.
Each layer has its own set of design considerations and weighing.Their realization and integration method determines the overall wallet experience.In this article, we will study components and latest innovations of each layer, and explore how to help create more user -friendly crypto applications through various methods.
2. Key management: Where to store and how to store your key
The key management layer contains three key decision points:
-
Key generation:The core of the key generation method is to define how to create a key and use the key to sign the transaction.Although the single private key method is still a traditional method, more and more complicated solutions are adopted in the industry, such as multi -party computing (MPC) and Shamir Secret Sharing (SSS).These new methods distribute the key generation and signature process to multiple parties, thereby achieving a better balance between security and availability.
-
storage:This component determines where the generated key or key fragment is stored.The ultimate choice depends on various factors: safety needs, accessable needs, operating costs and decentralization required.The available options include centralized cloud servers (such as A. such as A.), decentralized storage solutions, personal storage equipment and hardware wallets. Each option has unique advantages and weighing weighing weighing.
-
Authentication:Users prove their identity access to their keys through various identity verification methods.The traditional password system is allowing a more friendly way, such as social login and passkey, which reflects the transformation of the industry to a better user experience, especially mobile devices.
When deploying key management systems, each component can be configured differently according to specific requirements (whether it is the purpose, technical restrictions or business requirements of the application).In the current market solution, the key difference is usually the choice of key generation method and authentication method combination, because these options fundamentally determine the degree of balance between security and user experience.
>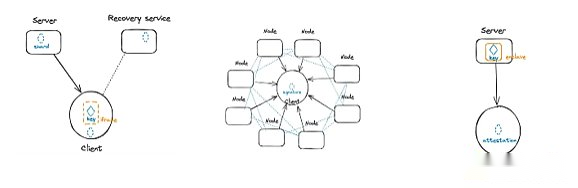
The earliest key management method is simple, but the requirements are high: users have fully controlled their private keys through external accounts (EOA).Although this direct ownership model continues to be widely used, its limitations are becoming increasingly obvious.New users often worry about the technical complexity of key management. Even experienced users are facing major security risks -whether potential hacker attacks or error storage keys leading to permanent losses of funds.
In order to cope with these challenges, the industry has developed three different modern key management methods: Shamir Secret Sharing (SSS), which distributes key fragments to multiple positions; multi -party calculation (MPC), which supports the signing of the trading; credible is credible;Executive environment, it provides a Secure Enclave for key operation.Each of these solutions solves the restrictions of traditional wallets in a unique way, providing different security, availability and decentralization balance. We will conduct in -depth discussions below.
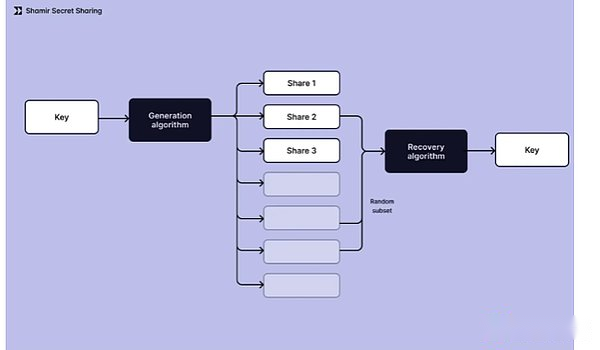
2.1 Shamir Secret Sharing (SSS)
SSS developed in the 1970s was an encryption algorithm that improved security by dividing the key into multiple fragments.There are two main purposes of this method: it eliminates the inherent single -point failure of single -secret management, while ensuring that the key is maintained when required.The key feature of the system is its threshold mechanism -combining key fragments that meet the requirements of a specific minimum number must be reconstructed to rebuild the original key. Any smaller fragments collection cannot disclose the key content of the key.
In practice, SSS divides them into multiple fragments by generating private keys on user devices, and distribute these fragments to different stakeholders (usually including users and service providers).For transaction signatures, the system temporarily re -uniformly re -uniformly re -uniformly reconstruct the key.This method enhances security and can be seamlessly integrated with existing blockchain infrastructure.
-
advantage:
-The stability of verification:This algorithm has provided extensive verification for decades, and has produced open source implementation of several practical tests.
-The flexible key distribution:Administrators can accurately customize the total number of keys and the threshold required for the reconstruction key.
-Hodified:The storage solution of a single fragment can be updated independently. It can achieve targeted system improvement without a comprehensive update.
-The scalability:Regardless of the size of the user group, the client calculation model can ensure consistent performance.
-
shortcoming:
-The key reconstruction vulnerability:A temporary security vulnerability is generated when the key reconstruction is performed during the transaction signature.
-Adrawal restrictions:SSS lacks encryption methods to verify whether the fragment is successful or whether the initial key generation is accurate.
-The complex implementation:Solution usually requires complex development of professional knowledge, especially in ensuring the security of client operations.
-
Case research: Privy
>
Privy shows advanced SSS deployment in the modern wallet architecture.Their embedded wallet solution uses a safe IFRAME environment to use CSPRNG to generate wallet vouchers in this environment.Then, the system obtains the public address and private key of the wallet through the generating notes.
After the initial generation, the system uses SSS to divide the private key into three different fragments:
-The device sHARE: Local storage on user devices, and stored in the browser’s local storage when using web applications.
-Adge SHARE:Stored on the PRIVY server in the form of encryption and access during the authentication process.
-Su recovery share:Can be stored flexibly in Privy’s key management infrastructure, or users can also be stored directly.
A key security feature is that the complete private key is temporarily stored in memory during operation without being permanently preserved.The architecture of the system requires any two fragments to rebuild the key, thereby creating three powerful recovery paths:
-Equipment Share + Certification Share:This is a standard user process.Users perform identity verification through social login or similar ways to trigger the user’s certification Share decryption, and the certification share is combined with the user’s local equipment Share.
-Equipment Share + restore Share:When the Prive server cannot access or the user cannot access its main authentication method, the path provides Fallback return mechanism.
-Adge SHARE + Restore SHARE:By generating new equipment Share on other devices, seamless migration of the device.
Privy’s advanced recovery system can safely access wallets without affecting security.The deployment successfully achieved a subtle balance between reliable security measures and user access in digital asset management.
2.2 Threshold Signature Scheme (TSS)
TSS is a form of multi -party computing (MPC). It is generated by multiple participants and signed the SHARES to perform encryption operations on shared key.Unlike SSS, a key feature of TSS is that participants can combine their signature shares to perform operations without reconstruction of the key.
TSS can be implemented in various ways, from large -scale networks involving multiple computing nodes to simple two -party signature schemes between users and service providers.Participants can contribute to the signature generation without knowing the key, and maintain high security while achieving a flexible signature process.
-
advantage:
-In enhanced security:By eliminating the needs of key reconstruction, a single point failure in SSS is eliminated
-The flexible architecture:Settle the number of participants and the required signatures to support all kinds of trust models.
-
shortcoming:
-The technical maturity:As a relatively new commercial technology, there are few cases of verified deployment and large -scale deployment.
-The expansion limit:The TSS -based system requires communication between participants, resulting in slow processing speed, especially when ECDSA deployment is performed on Ethereum.
-Stimetering complexity:Multi -party coordination and communication are needed, resulting in complex deployment and high operating costs.
In short, although TSS has attracted attention as a powerful alternative to solving the SSS single -point failure problem, its current deployment is facing some restrictions in terms of performance and complexity.These restrictions to a certain extent restrict their scalability in practical applications.
-
Case study: Particle Network
-
>
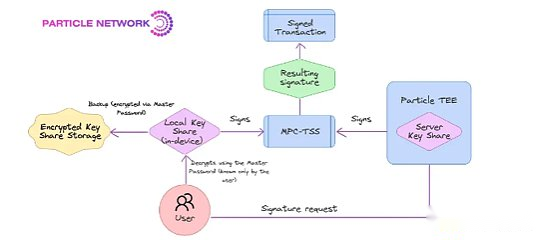
Particle network is a main example of a wallet solution that provides user-friendly wallets that provides user-friendly wallets through MPC-TSS deployment.They especially adopt a 2/2 TSS method to ensure that the private key will never be concentrated in its entire life cycle (from generation to storage and use).
In the TSS deployment of the PARTICLE network, two independent key Shares is generated and stored them in different positions.One Share is stored in the user’s local environment, while the other is stored in the trusted execution environment (Tee) of Particle.It is important that each separate Share will not disclose any information about the complete key, and perform operations by combining shares without reconstruction of the complete key.
As an additional security layer, users can set up a main password to encrypt the local storage key Share.This provides additional security other than social login identity, while still supporting safe money recovery across different equipment.
At present, the PARTICLE network provides MPC signature support for Solana and EVM chains.Through this method, the PARTICLE network provides a safe, non -hosting key management system. It is still user -friendly and unrelated.
2.3 Trusty Executive Environment (Tee)
Tee uses a completely different method from SSS and MPC.It performs all private key -related operations in the safe isolation execution environment.This security is guaranteed by platforms such as Intel SGX or AWS Nitro Enclaves.
In a TEE -based system, the authorized code runs in remote Enclave with isolation CPU and memory resources, avoiding external surveillance or interference.Enclave can generate certificates for proof operation correctly, allowing users to verify whether its private keys are handled safely.This provides a simple and powerful platform for key management.Unlike SSS or TSS calculated by complex key divisions or multi -partial calculations, Tee uses hardware to ensure security key management.
-
advantage:
-A strong security:Provide advanced security through hardware -level isolation.
-Adividated:You can prove that all operations are performed as expected.
-Efficient performance:Compared with TSS, less network communication is required to achieve relatively faster processing.
-
shortcoming:
-A hardware dependencies:High dependence on specific hardware or suppliers may lead to centralization or review risk.
-S safety vulnerability:If ENCLAVE itself is attacked, the entire system may be in danger.
TEE provides a practical solution for key management problems based on hardware security.Although its deployment is simpler than SSS and operations is more efficient than TSS, dependence on hardware platforms is still a question that needs to be considered carefully.
-
Case research: turnkey
>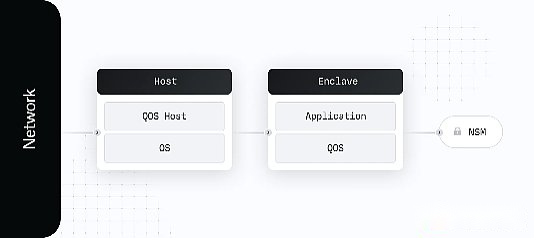
Turnkey’s core security strategy is carried out around the processing of all key security operations in Tee.In the TURNKEY system, all security sensitive services -including key generation, signature and strategic engines -all execute within the safe Enclave.
The architecture of Turnkey includes the following two main parts:
-Orfo:This is a standard AWS virtual machine, which runs basic applications for receiving network traffic and performing ENCLAVE calls.It acts as a buffer between ENCLAVE and external systems to collect indicators and other operating information related to ENCLAVE operations.
-Enclave:This is an environment that is completely isolated from the external connection, and there is only one virtual serial connection with the host and its own security associate processor. It is called the NITRO security module (NSM) in AWS.This environment runs Quorumos (Qos), Turnkey’s Enclave operating system, and security applications running on it.
Through this structure, TurnKey can prove to themselves and users that all the key security systems are fully operated as expected.ENCLAVE runs in a highly limited computing environment, without permanent storage, interactive access or external networking, so it can provide the highest level of security.
3. Account: Invisible account and chain
With the continuous development of blockchain technology and obtaining mainstream adoption, people more and more need to abstract their technical complexity.Wallets are the main contact points between users and blockchain networks, but they often have a high threshold for entry.New users must work hard to master some unfamiliar concepts, such as private key management, GAS fee payment and transaction signatures. For ordinary users, these technologies may be daunting and too complicated.
This demand for abstract also reflects the development of other technologies we use daily.Think about how we interact with the Internet: Users do not need to understand the TCP/IP protocol or DNS system to browse the website.Similarly, you don’t need to understand GSM or LTE technology.This model is consistent in mature technologies -with their development, technical complexity is increasingly hidden behind the user -friendly interface.
In this article, we will explore two basic abstract concepts that reshape the wallet user experience.The first is account abstraction. It converts complex blockchain accounts into a programmable, user -friendly interface.The second is Chain Abstraction, which eliminates the complexity of cross -chain interaction and gives users the ability to seamlessly operate seamless operation across different blockchain networks without understanding the underlying mechanism.
3.1 Account Abstract
The initial EOA only provided some basic functions: storage address and signing transactions.The lack of programming at the account level means that any advanced function or customized operation is impossible.The introduction of account abstraction has changed this situation through the enhancement function directly at the account level.Although the account abstraction originally showed the hope of solving the challenge of the blockchain user experience, there were some obstacles delayed its widely adopted.Complex deployment requirements, high GAS costs, and poor compatibility with existing EOA all lead to slow adoption than we expect.This technology has matured, overcoming early challenges, and is now moving towards the direction of actual application.Some consumer applications recently launched have successfully integrated account abstraction. End users can interact seamlessly with blockchain applications, and they usually do not realize that they are using wallets or blockchain.This development marks the potential of more extensive encryption in the existing encrypted user base.The impact of account abstraction has continued to expand throughout the encrypted ecosystem.L2 Rollup is now integrated with an agreement level to enhance the user experience, and the wallet is a more advanced embedded wallet solution.The upcoming Ethereum PECTRA upgrade further highlights the importance of the technology. The upgrade includes EIP-7702-allowing EOA to use the temporary programming of the main network SCA.
-
Case research: abstract
>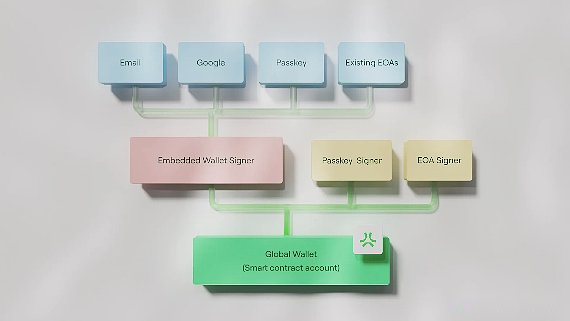
Abstract developed ABSTRACT Global Wallet (AGW), which is a common embedded wallet to provide support for each application of its platform.Unlike specific application wallets, AGW, as a comprehensive solution, allows users to access any application in the ABSTRACT ecosystem.This wallet solves a actual demand: allows users to manage their data and assets across multiple applications through a single access point.
Compared with traditional EOA, AGW realizes native account abstraction (Native Account ABSTRACTION) to create smart and flexible smart contract wallets.This method treats all accounts as smart contracts to ensure that they follow the same transaction life cycle.Although the traditional Ethereum is a separate process for the maintenance of the EOA and smart contract accounts, ABSTRACT deployment will uniformly handle all accounts to provide consistent functions for existing EOA users and users using new AA wallets.
The wallet creation process follows a simple two -step method for EOA and smart contract account (SCA) integration.When users log in through common methods such as email, social login or password, the system will create an EOA wallet in the background.The EOA address then became an authorized signature of the deployed smart contract wallet.This design eliminates the complexity created by the blockchain wallet, while maintaining its security characteristics.
Abstract’s local account abstraction follows the ZKSYNC standard, including the following key components:
-Iccount standard interface:Define the methods required by all smart contract accounts, standardize account behavior, and ensure consistency.
-DEFAULTACCOUNT conversion:EOA Wallet (such as Metamask) automatically converted into the DefaultAccount deployment of IACCount during transaction processing, so that they can access SCA’s advanced features.
-Paymaster support:All accounts can sponsor GAS fees for other accounts, or use ERC-20s to pay GAS fees instead of ETH, which greatly reduces the entry threshold of new users.
Through this architecture, ABSTRACT supports users seamlessly accessing advanced functions without understanding the underlying complexity.Users only need to log in through familiar methods such as email or social accounts, and the system will automatically handle EOA creation and smart contract wallet deployment in the background.After the initialization, users can access functions such as multi -sign settings, transaction restrictions, and account recovery mechanisms.
>
In addition to native account abstraction, AGW also integrates Privy’s Cross App Wallet to support it for consumers -centered methods.Although traditional embedded wallets provide simple social login and key management, they are limited due to the nature of its specific applications, resulting in fragmented problems of cross -platform asset management.The concept of Cross-APP Wallet deployed in AGW allows users to access their assets and data across multiple applications across multiple applications to solve this problem.
The development of general -purpose embedded wallets has brought major technical challenges, especially in terms of security architecture.Unlike a specific application wallet containing security risks, cross -application wallet means that security issues in an application may affect all customs applications.This requires a more reliable security model.However, the advantage of this method is huge:
-Simplify asset management: A deposit point can be used for all integrated applications.
-Cy centralized tracking assets:Cultivate assets for users and developers across multiple applications.
-An seamless transfer:Different applications can be transferred between different applications in the ecosystem.
3.2 Chain abstraction
In addition to account abstraction, chain abstraction has recently become an important concept in blockchain development.The account abstraction focuses on improving the user experience in a single blockchain, while the chain abstraction solves a different challenge: the user can interact with the assets on multiple chains without involving the bridge mechanism.The core of chain abstraction is to make the concepts of different blockchain transparent to end users. As more and more modular blockchains continue to create more complex chain ecosystems, this demand has become increasingly important.
>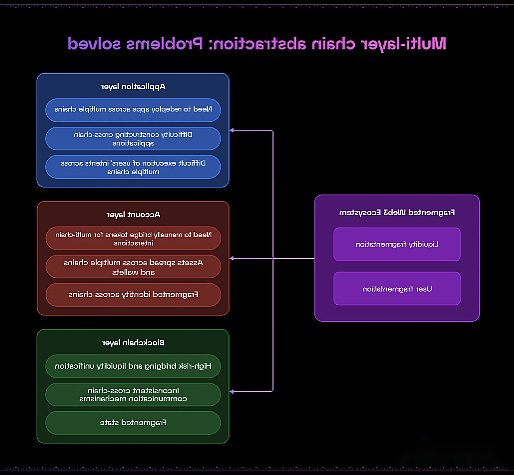
Different from account abstraction defined by specific technical specifications (such as EIP-4337), chain abstraction is a broader method.It can deploy across the layers of the blockchain stack -from applications and accounts to protocol -the purpose is to abstract the complexity of cross -chain interaction.
Chain abstraction can provide enhanced blockchain user experience, including but not limited to:
-In unified balance management:Users can manage their assets through a single interface, no matter which blockchain the assets are.This unified management method eliminates the requirements for tracking the balance of different chains or understanding the underlying blockchain architecture.
-The flexible payment system:Users can use any tokens on any tokens on any chain.There are special solutions to process complexity in the background -receiving various payment tokens, managing cross -chain bridge connections, and processing GAS fees -at the same time provide users with a simple payment experience.
-Set seamless cross -chain interaction:Although centralized applications can easily provide similar functions, chain abstraction is to achieve these benefits while retaining the core principles of blockchain technology (decentralization, personal asset ownership and security).
-
Case research: One Balance
>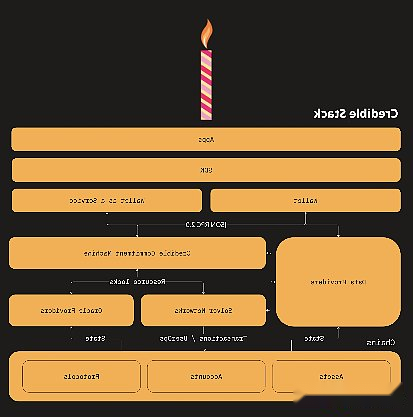
One Balance is a project initiated by the Frontier Research team, which is famous for proposing their CAKE (chain pumping key element) framework.The core of their solutions is the concept of “Credible Account”, which combines the advantages of EOA and SCA.
The trusted account has expanded the traditional blockchain account format to provide trusted guarantees without requiring cross -chain consensus requirements.These accounts run on the security machine selected by the user and make a trusted commitment to the signature of the message.They maintain SCA’s security guarantee and support the key features of account abstraction, including GAS abstraction, social recovery, permissions strategies and modern identity verification methods.
Trusty accounts can generate any number of sub -accounts and manage any number of sub -accounts, and fully control each chain status.They are designed to be universal compatibility and compatible with various blockchain networks (Ethereum, Solana, Bitcoin) and various smart contracts and assets (including ERC20 tokens, NFT, DAO, and DEFI protocols).
One Balance’s chain abstraction system is based on the following two key components:
-Resource lock:Users under this mechanism make verification promises and lock their assets until they meet specific conditions or expires.Unlike traditional smart contract deposits or ERC20 approval, these are account -level locks and do not require the end of the chain.For example, when using Ethereum USDC to buy Solana NFT, the user will lock their USDC until they reach a specific block height of NFT.This design can protect Solvers from risks such as double flower attacks and ensure transaction integrity during cross -chain operations.
-The trusted commitment machine:This is a security infrastructure that performs cross -chain transactions.These machines run in a special security environment and perform two basic functions: they verify the effectiveness of the resource lock set by the user and ensure accurate execution when meeting the lock conditions.For example, when using Ethereum USDC to purchase Solana NFT, the promise machine verifies the user’s USDC ownership and manages the security transfer to the seller after the NFT purchase is completed.This automation process follows the predefined rules to ensure that all participants can be implemented by reliable execution.The commitment machine can be deployed through four methods: Tee, MPC, SCA or protocol virtual machine.
Although One Balance is still in the development stage, it has released an integrated example of using Privy.Their methods stood out from other chain abstraction solutions, providing a framework for integrating existing blockchain infrastructure or applications. There is no special chain or system, which reduces obstacles to the greatest extent.
4. Interface: Mobile application is the next cutting -edge
High -quality mobile applications are rare in the encryption ecosystem.Most encrypted applications are mainly developing around the desktop platform, mainly because of the following two points.
The main reason is the nature of the encrypted application itself.These platforms usually handle complex financial transactions, which need to display detailed information, comprehensive analysis and multiple data points at the same time -all these are more suitable for desktop interfaces.Although mobile platforms are good at providing simplified and user -friendly experiences, they often have to sacrifice the depth and breadth of the depth and breadth required by traders and users.This natural limitation makes desktop development naturally a priority consideration for most encrypted applications.
This development centered on the desktop shapes the interaction between users and encrypted applications: they usually maintain a main wallet and connect to various applications as needed.However, this mode will produce huge friction when switching to the mobile environment.Users will find that they often switch between wallet applications and master applications, and carry out basic operations such as logging in or signing transactions again and again.This repeated back and forth operation is in sharp contrast to the seamless interaction obtained from traditional applications.
The second main reason is the restricted policy of mobile app stores. Apple’s App Store is particularly challenging.Their strict policies for crypto -related payments forced many encrypted applications to seek creative solutions.Early attempts to avoid these restrictions through the gradual web apps (PWAS) showed the initial dawn, but they failed to get attention, mainly because the user was unfamiliar with the installation and use process and the operation was cumbersome.The successful case of the Telegram App Center further highlights this distribution challenge. It successfully harvested an amazing 500 million MAU in more than 1,000 small applications, indicating that when encrypted applications obtain effective distribution channels, the potential is huge.
>
However, the situation is slowly changing.As the encrypted market expands from pure financial services markets to more friendly collars for consumers (such as MEME currency and artificial intelligence applications), we have seen the revival of mobile priority development models.The emergence of new players such as social platforms (Farcaster, Interface) and MEME Coin Trading Platform (Moonshot, Sauce) clearly reflects this trend evolution, and they are preferred to consider complex mobile experiences.Even traditional DEX like Jupiter and Uniswap also set its sights on the mobile optimization interface to attract more users.This trend has been further supported by infrastructure providers. The WAAS platform such as Privy and Re “has expanded their SDK features such as WAAS platforms such as WalletConnect, providing better support for mobile development.These development shows that the entire industry clearly realizes that mobile optimization is no longer an option, but a must -have for mainstream encryption.
-
Case research: zora
>
ZORA is the best example of how the encrypted application is successfully adopted to adopt the principle of mobile priority design.As a digital creation social network, Zora users can seamlessly create, share and trade various forms of digital content -whether it is image or video, or music, meme.
The uniqueness of Zora lies in its comprehensive mobile optimization, from the initial account to NFT casting.The login process is very simple: the user only needs to enter a email address to register. Those users who already have Farcaster or Instagram accounts can associate these accounts, immediately receive personalized feed recommendations and find friends.Perhaps the most important point is that Zora uses native mobile functions -users can take photos or videos directly through the camera of the mobile phone, and immediately cast them into NFT to create a natural experience like publishing the same natural social media.
At the bottom, ZORA uses complex blockchain technology, while maintaining simplicity for users.They have deployed a modern account abstract stack to combine PRIVY’s embedded wallet technology with Coinbase’s smart wallet infrastructure.This technical architecture allows Zora to complete complex operations in the background, such as GAS fee management and transaction batch processing.Users do not need to understand these technical elements or interact with them so that they can only focus on content creation and sharing.
A unique innovation of ZORA lies in its inside currency system named “Spark”.Spark’s valuation unit is one -million -dollar (equivalent to 1,000 GWEI), which can be purchased directly through common payment methods such as credit cards or debit cards.The design of the system is very simple: with a sufficient SPARK balance, users can use simple double -click for NFT casting.Each NFT casting costs 111 Sparks, including no GAS transactions.The important thing is that the Sparks you buy will never expire. Even if Zora’s casting costs have changed in the future, they will remain effective.
Zora is particularly noteworthy that they successfully abstracted the complexity of the blockchain.All technical elements that usually bring friction in encrypted applications -wallet creation, GAS fees management, NFT casting process -all are all invisible in the background.As a result, there is no different experience with any pop social media, while reserving all the benefits of blockchain technology.This method sets new standards for the goal of mobile -priority encryption applications, showing how blockchain technology is seamlessly integrated into the daily mobile experience.
5. Conclusion
Since the application has exploded in the summer of Defi & AMP; NFT in 2021, the crypto industry has gone through a long way.DEFI & amp; NFT summer marks the era of innovation explosion in the field.In the following two years, the infrastructure has made significant progress: modular blockchain has emerged, the L1 network has achieved significant performance improvement, and technologies such as Oracle and bridge have been greatly mature.These development effectively overcome many problems that have been hindered by blockchain, especially the problems that have always existed, especially the slow transaction speed and high costs.
However, although the technical foundation has been greatly strengthened, the user experience has not kept pace.Although the application layer is constantly experimenting and developing, there are few encrypted platforms comparable to the seamless and intuitive experience obtained by users from Web2 applications.As our infrastructure is becoming more and more reliable, we are ready to support the next generation of applications, and this experience gap will become more and more obvious.The most urgent challenge is to create a service that can bring familiar Web2 user experience, and at the same time, it can also retain the unique advantages of blockchain technology.
The core of this challenge is to encrypt the wallet -maybe encrypted wallets are the most critical factor that determines the overall user experience.Wallets are the entrance point of new users, and it is also a portal of all important operations in the application. From simple login to transaction approval.Therefore, the encrypted wallet is positioned as the basic layer of the user interacting with the entire encryption ecosystem. Their design and functions are critical to the mainstream.
The innovation of wallet technology is not limited to a certain level, but at the same time across multiple dimensions -from key management and account structure to UI/UX.Each layer shows different design parameters, which change these parameters depending on the characteristics and needs of the application.The innovation of wallet technology continues, and new narratives have appeared around account abstraction and chain abstraction. At the same time, new technologies such as Webauthn and Tee have also introduced.
Therefore, the success of the application may require a good understanding of the decision -making process of each layer of the wallet architecture.By analyzing successful deployment cases and understanding the balance of pros and cons, the team can make wise choices based on their specific cases, while maintaining a balance between functionality and user experience.
Whether cryptocurrencies can be widely adopted depends on whether we have the ability to allow daily users to use complex blockchain technology without damage to the basic principles of decentralization characteristics and basic security.Although recent case studies have shown that gratifying progress has been made in this direction, and innovative solutions have appeared in the ecosystem, but we are still in the early stages of this transformation.The future challenge is to create an experience not only matching, but also to surpass traditional digital services, while retaining the unique value proposition of blockchain technology.With the continuous development of wallet technology, it will play an increasingly important role in shaping how the next generation of users interact with crypto applications.