Is DeepSeek easy to use?When DeepSeek recovers from the DDOS attack that is noticed across the entire network, we are in the DeepSeek interface request after resurrection.Bitcoin was found.
Let me tell you slowly.
1. DeepSeek is stuck
DeepSeek is facing the largest DDOS attack.
It is rumored that the peak attack traffic exceeded 3.2Tbps, which is equivalent to tens of millions of devices “knocking” at the same time every second, causing the R1 big model service to go down for nearly one day.
DeepSeek survived.Whose credit?

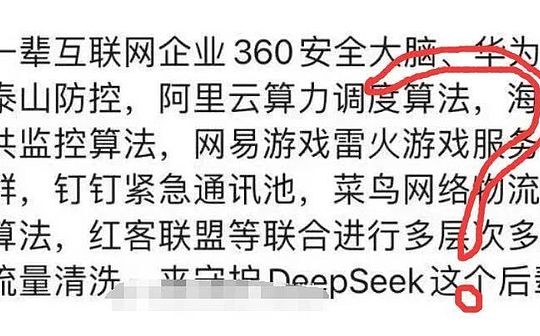
Some people say that it is the older generation of Internet companies, the Taishan prevention and control of 360 security brain, Huawei Cloud, Alibaba Cloud computing power scheduling algorithm, Hikvision public monitoring algorithm, NetEase Game Leihuo Game Server Cluster, Dingding Emergency Communication Pool, Cainiao Network Logistics ScheduleAlgorithms, RedCar Alliance and others jointly carry out multi-level and multi-dimensional traffic cleaning to protect the younger generation of DeepSeek.
Please,I hope you don’t believe this kind of cool writing logic.In addition to Zhou Hongyi, who is also working tirelessly to fight DeepSeek, I think other major factories are confused.
Behind this “digital riot” is actually a microcosm of the cybersecurity offensive and defensive battle – the attacker controls the “zombie legion” to launch a tide of requests, while the defender needs to find a way to break the deadlock in the game of computing power and wisdom.
It’s indeed a bit difficult.
But what’s interesting is,The key to breaking the deadlock in DeepSeek is not in the cool article, but in Bitcoin.
2. Iron evidence
At first I was just curious. After the recovery DeepSeek starts to rotate for a long time every time it requests, the computer fan also starts to start at full speed.Feeling that’s a lot like Bitcoin mining we know about.
It was not until I opened F12 and saw the DeepSeek request that there was create_pow_challenge, and I realized that DeepSeek was using Bitcoin’s PoW mechanism to fight DDOS attacks.
Is it true?Let me ask DeepSeek’s classmates
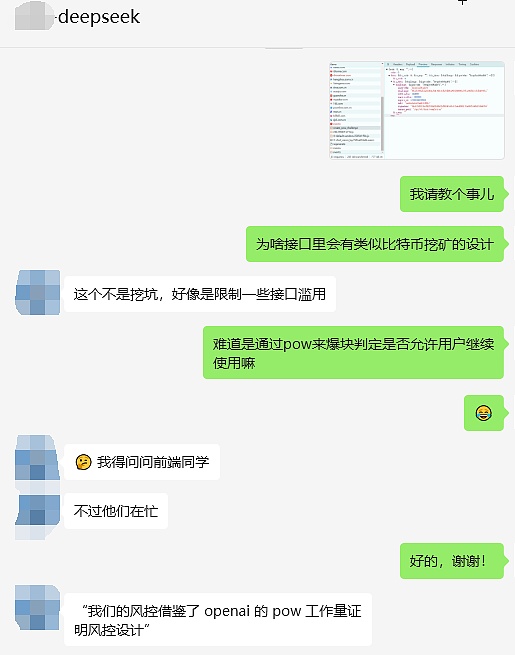
It’s true, not only used, but also OpenAI.
So, why Bitcoin?
3. The revelation of Bitcoin
The essence of DDoS attacks is to flood the target system through massive invalid requests until the target system is overwhelmed and refuses service.
Traditional defense methods such as traffic cleaning and IP ban can alleviate symptoms, but are difficult to cure the root cause – the cost of attack is low and the cost of defense is high, just like “using fire hydrants to fight floods.”
DeepSeek’s new strategy borrows from Bitcoin’s Proof of Work (PoW) mechanism.Simply put, if a user wants to call AI services, he must first complete a calculation problem (similar to Bitcoin mining) so that those who successfully solve the problem can obtain a “pass”.This design allows every request to pay real computing power costs, and if an attacker wants to launch a large-scale attack, the cost will increase exponentially.
What is the logic behind this?
Bitcoin ensures network security through PoW: miners consume computing power in exchange for accounting rights. If an attacker wants to tamper with the data on the chain, he needs to control more than 51% of the computing power in the entire network, which is far beyond the profit.DeepSeek migrates this logic to the risk control field – if an attacker wants to forge a massive request, he will have to pay a computing power price equivalent to that of a real user, and this will be of no economical importance to the attacker.
This is so great.
4. The other side of the coin
DeepSeek’s attempt reveals a trend: the underlying philosophy of blockchain is reshaping cybersecurity.PoW’s “economic game” thinking provides a new paradigm for combating distributed attacks – no longer relying solely on technical suppression, but instead letting attackers “responsible abandon” through mechanism design.
Just as Bitcoin uses decentralization to fight financial monopoly, DeepSeek uses computing power to compete against traffic torrents.This is perhaps the charm of technology:It seems irrelevant to the field often hides the key to solving the problem.
Ultimately, the essence of security is not to build walls, but to make the cost of damage higher than the benefits.The “cross-border cooperation” between DeepSeek and Bitcoin may be the best annotation of this logic.
May you own both DeepSeek and Bitcoin.