Source: Byte Yuan CKB
In the previous articleHow Lightning Network Works (1)In 》, we discuss the operating principles of Lightning Network and the security-assurance technologies of two-way payment channels.In this article today, we will continue to introduce Lightning Network and explain the relevant principles and technologies for expanding the two-way payment channel into Lightning Network.
Expanding two-way payment channel into lightning network: multi-hop routing technology
We also use Alice and Bob to establish channels as the basic background, but in this world, except for Alice and Bob, what should we do if others want to access the Lightning Network?Is there any way to connect everyone to the network and ensure that payments can be initiated to any person on the network?
To solve this problem, we needExpand the two-way payment channel into a lightning network.And use multi-hop routing technology.”routing” literally means “find a path”,In the lightning network, it is necessary to find the path to pay for specific objects that are connected by the front and back of the channel.
Take Alice pays 2000 to David as an example, assuming that there is no payment channel between them, but payment channels have been established between Alice and Bob, between Bob and Carol, and between Carol and David.In this case, Alice can transfer the money to Bob first, then from Bob to Carol, and finally Carol to David, which seems to realize the payment channel from Alice to David, where Bob and Carol act as the networkrouting node in.If a payment channel is also established between Alice and Eva, and between Eva and David, then Alice can also choose to transfer the money to Eva first, and then transfer it to David from Eva.
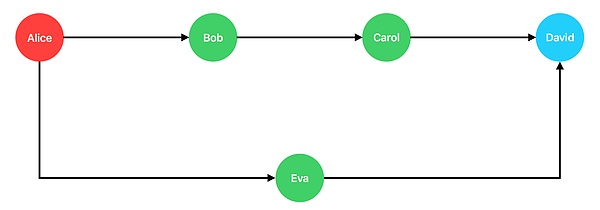
From the path, it is obvious that Alice transfers money to David through Eva is the shortest choice.However, in actual operation, the shortest path that seems to be is not always the best choice, because other factors need to be considered, such as the capacity of the channel, the charging standards of the routing node, whether the routing node is online, etc.
At present, mainstream Bitcoin Lightning Network implementations (clients), such as LND developed by Lightning Labs and CLN developed by Blockstream developed by CLN developed by Blockstream, have used a variant of the Dijkstra algorithm in the routing algorithm, and the Lightning Network launched by Nervos CKBFiber Network also uses the Dijkstra algorithm to find the optimal routing path.
Ensure routing security: From HTLC to PTLC
In the above example where Alice wants to pay David, how can we ensure that the intermediate routing nodes will not cheat and will not maliciously withhold funds?Traditional financial systems usually rely on credit guarantees from large well-known financial intermediaries, but Lightning Network is a P2P network and does not have such a third party independent of traders to provide credit guarantees. We need a different mechanism to ensure transaction security.This isHTLC (hash time lock contract)where the function is.
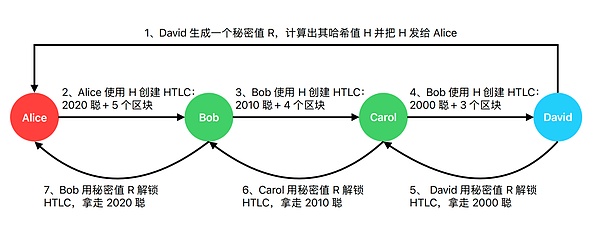
HTLC consists of two parts: hash verification and expiration verification.Let’s take Alice to pay David 2000 and choose Bob and Carol as routing nodes in the network as an example to understand how HTLC works:
-
First, David wants to generate oneSecret value R, any word or number can act as this secret value, and then calculate itHash value Hand send it to Alice.This hash value H will be placed in the lock script of the transaction output, and only those who know the secret value R corresponding to H can use this output, which R is called “preimage” in the Lightning Network.If the secret value R is not disclosed in a timely manner, the payment will not be used and the sender will recover all the funds.
-
Then, Alice uses the received hash value H to create an HTLC, the time lock is set to the next 5 blocks, and the output amount is 2020 Cong, of which 20 Cong is the handling fee to the routing node Bob.To put it in plain words, Alice will pay Bob 2020, as long as he can provide the secret value R in 5 blocks, otherwise the money will be returned to Alice.
-
Bob creates an HTLC in his own and Carol channels using the same hash value H as provided by Alice, and sets the time lock to the next 4 blocks. The output amount is 2010 Satoshi, of which 10 Satoshi are for the routing node Carol.handling fee.To put it in plain words, Bob will pay Carol 2010, as long as he can provide the secret value R in 4 blocks, otherwise the money will be returned to Bob.
-
Carol uses the same hash value H to create an HTLC in his own and David’s channel, and the time lock is set to the next 3 blocks, and the output amount is 2000 Sato.To put it in plain words, Carol will pay David 2,000, as long as he can provide the secret value R in 3 blocks, otherwise the money will be returned to Carol.
-
David used the secret value R to unlock the HTLC set by Carol and took away 2000 Satoshi.
-
After David took away the funds, Carol would also know the secret value R. He used R to unlock the HTLC set by Bob and took away the 2010 Satoshi.
-
After Carol took away the funds, Bob also got the secret value R. He used R to unlock the HTLC set by Alice and took away the 2020 Satoshi.
Through this mechanism, Alice successfully paid David 2,000 without directly establishing a payment channel.During the whole process, all parties do not need to trust each other.The routing node also receives the due handling fee.Even if payment is interrupted at a certain stage, no party will suffer losses due to the existence of the time locking mechanism, and the funds will automatically return after the locking time.
However,HTLC also has a potential privacy issue:The entire path uses the same secret value (original image).If an entity controls multiple nodes on the payment path, it is possible to infer complete transaction information by comparing the input and output of different nodes, and even guessing the payer and the payee, which weakens the Lightning Network throughPrivacy protection achieved by onion routing.
To solve this problem, the Bitcoin community proposesPTLC (point time lock contract).In the PTLC scheme, each hop in the path uses a different secret value, so that privacy achieved through onion routing is protected.Fiber Network, the Lightning Network launched by Nervos CKB, plans to introduce PTLC in the future to further enhance the privacy protection capabilities of the Lightning Network.
Conclusion
With the continuous advancement of technology, Lightning Network is still continuously optimizing and improving.From LN-Penalty to eltoo to Daric, from HTLC to PTLC, we have seen the continuous improvement of Lightning Network in terms of security, privacy protection, etc.In the future, with the application of more innovative technologies and the improvement of ecosystems, Lightning Network is expected to become a key infrastructure to promote the popularization of cryptocurrencies and contribute to the realization of a true P2P economy.
References
-
https://www.btcstudy.org/2021/09/15/lightning-network-in-depth-part-1-payment-channels/
-
https://www.btcstudy.org/2021/09/15/lightning-network-in-depth-part-2-htlc-and-payment-routing/
-
https://www.btcstudy.org/2022/01/27/breaking-down-the-bitcoin-lightning-network-eltoo/
-
https://www.btcstudy.org/2024/02/07/lightning-network-technology-improvement-and-users-experience-part-2/
-
https://www.btcstudy.org/2024/02/23/lightning-network-technology-improvement-and-users-experience-part-3/
-
https://www.btcstudy.org/2022/08/19/what-are-ptlc/