Author: Onkar Singh, CoinTelegraph; Compiled by: Tao Zhu, Bitchain Vision
1. Explanation of Infinite Coin Attack
An infinite coin attack refers to an attacker manipulating contract codes to continuously mint new tokens that exceed the authorized supply limit.
This type of hacking is most common in decentralized finance (DeFi) protocols.This attack damages the integrity and value of a cryptocurrency or token by creating an unlimited number of tokens.
For example, a hacker exploited a smart contract vulnerability in the Paid network to mint and destroy tokens, resulting in a $180 million loss and PAID value drop by 85%.More than 2.5 million PAID tokens were converted to Ethereum (ETH) before the attack stopped.The network compensated users, eliminating rumors about internal crimes (rug pulls).
Malicious actors may profit from such attacks by selling illegally created tokens or interfering with the normal operation of the affected blockchain network.The prevalence of unlimited coin attacks emphasizes the importance of conducting thorough code reviews and incorporating security measures into smart contract development to prevent such vulnerabilities.
2. How does the Infinite Coin Attack work?
To create a vulnerability that allows an attacker to mint an unlimited number of tokens, the infinite coin attack targets vulnerabilities in smart contracts, especially those related to the token minting capabilities.
Step 1: Vulnerability Identification
Attack methods require finding logical weaknesses in the contract, which are usually related to input verification or access control mechanisms.Once a vulnerability is discovered, the attacker creates a transaction that exploits the vulnerability, causing the contract to mint new tokens without the need for authorization or verification.This vulnerability may allow bypassing the expected limit on the number of tokens that can be created.
Step 2: Utilize
The vulnerability is triggered by a malicious transaction built by an attacker.This may require changing parameters, performing specific functions, or leveraging unforeseen connections between individual code segments.
Step 3: Unlimited Mining and Token Dumping
The vulnerability allows an attacker to issue tokens that exceed the protocol architecture’s expectations.This token flooding may lead to inflation, thereby reducing the value of the token-related currency and potentially causing losses to various stakeholders, including investors and users.
Token dumping is the practice of an attacker quickly flooding the market with newly created tokens and then exchanging it for stablecoins or other cryptocurrencies.The value of the original token fell sharply due to unexpected increase in supply, causing the price to plummet.However, sell tokens before the market has a chance to benefit the attacker.
3. The consequences of the Infinite Coin Attack
An infinite coin attack can lead to rapid depreciation of token value, financial losses and ecosystem destruction.
An unlimited coin attack can generate an unlimited number of tokens or cryptocurrencies, causing the affected assets to depreciate immediately and causing huge losses to users and investors.This undermines confidence in the affected blockchain network and its connected decentralized applications, thus undermining the integrity of the entire ecosystem.
Furthermore, by selling tokens before the market fully reacts, the attacker can make a profit and potentially allow others to hold worthless assets.Therefore, if the attack causes a liquidity crisis, investors may find it difficult or impossible to sell their assets at a fair price.
For example, during the December 2020 Cover Protocol attack, the value of the token fell from over $700 to less than $5 in a few hours, and investors holding COVER tokens suffered financial losses.Hackers have minted more than 40 trillion tokens.
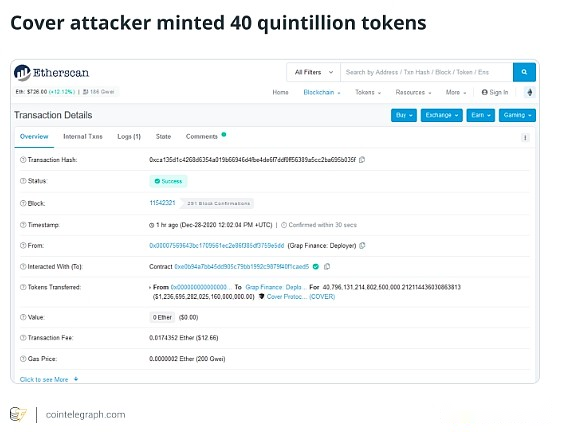
The collapse of token value could damage the entire ecosystem, including decentralized applications (DApps), exchanges and other services that rely on token stability.Attacks can lead to legal issues and regulatory review of projects, resulting in fines or other penalties.
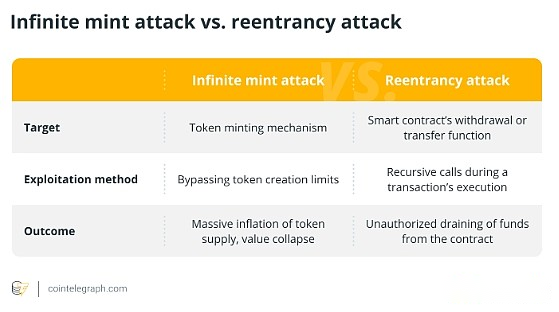
4. Infinite coin attack and reentry attack
The Infinite Coin Attack is designed to create an unlimited number of tokens, while the Reentry Attack uses a withdrawal mechanism to continuously consume funds.
Infinite Coin minting attacks exploit flaws in the token creation process to generate unlimited supply, thereby lowering value and causing losses to investors.
On the other hand, the reentry attack focuses on withdrawal procedures, allowing the attacker to continuously pull funds from the contract before it has a chance to update the remaining balance.
While any attack can have catastrophic consequences, understanding the differences is crucial to developing effective mitigation techniques.
The main differences between an infinite coin attack and a reentry attack are:
5. How to prevent unlimited coin attacks in cryptocurrencies
By emphasizing security and taking precautions, cryptocurrency projects can significantly reduce the likelihood of being targeted by unlimited coin attacks and protect investments from community members.
A multifaceted strategy needs to be developed that puts security first at every stage of the cryptocurrency project to prevent unlimited coin attacks.It is crucial to conduct thorough and frequent smart contract audits by independent security experts.These audits carefully check the code for defects that can be used to mint unlimited tokens.
Strong access control must be implemented; coin rights should only be granted to the authorized party; multi-signature wallets should be used to improve security.Real-time monitoring tools are essential to quickly respond to possible attacks and identify any strange trading patterns or sudden surges in token supply.
Projects should also have a strong backup plan, ready to quickly handle any possible attacks and minimize losses.This requires open communication channels with exchanges, wallet providers and the community as a whole to anticipate possible problems and develop solutions.