Author: 0XTODD Source: X,@0x_todd
Recently, the market is not good, and I have finally got more time. You can continue to divide some new technical routes.Although the encryption market in 2024 is not as magnificent as in the past, there are still some new technologies trying to mature, such as the topic we are going to talk about today: “FHE/Fullyhomorphic Encryption)“” “.
V God also published an article about FHE in May this year. Recommended friends who are interested in saying read.
>
So what technology is FHE?
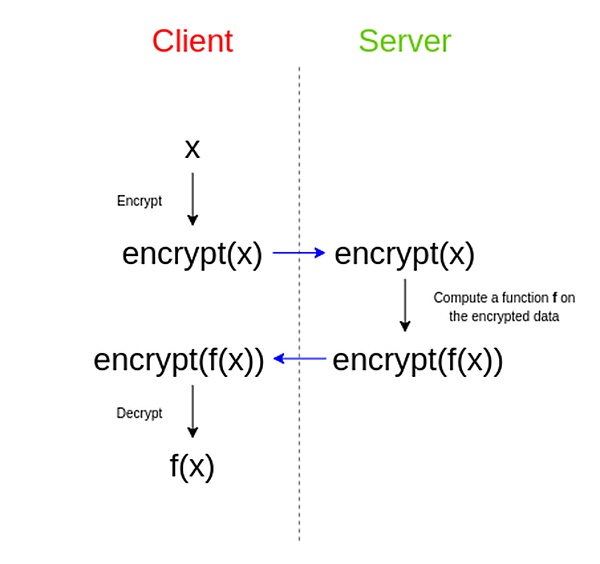
Want to understandFHE full -state encryptionThis noun term must be understood first what is“encryption”What is“Same State”And why “all”.
one,What is encryption?
Everyone is most familiar with ordinary encryption.For example, Alice will send a letter to Bob, such as “1314 520”.
If you need to send a letter to a third party C now, and the information is confidential, then it is very simple -just need to encrypt each number X2, such as “2628 1040”.
When the BOB receives it, remove each number in order in turn, and it will be tested that the original Alice is saying “1314 520”
Do you see, the two have completed information transmission through symmetrical encryption, and they have completed information transmission when they have to hire C to contribute to but do not know the information.Generally, in the spy warfare, the two liaison officers do not exceed this category.
>
2. What is the same state encryption?
Now Alice’s demand is difficult to upgrade:
For example, Alice is only 7 years old;
Alice will only be counted as the simplest arithmetic such as X2 and ÷ 2, but other operations do not understand.
Okay, now assume that Alice is going to pay electricity bills, the monthly electricity bill of Alice is 400 yuan, a total of 12 months.
However, 400*12 = a few, this topic exceeds the scope of Alice, who is only 7 years old, she will not be so complicated.
However, she doesn’t want others to know how much money she costs/a few months, because it is a sensitive information.
Therefore, ALICE asked C to help calculate without trusting C.
Because she only had X2 -2, she used the X2 multiplication to make a simple encryption, so she told C to let C calculate 800×24 = how much, that is,: (400×2) multiplication (12×2).
C is an adult,Has a strong computing mental forceSoon, 800*24 = 19200 was calculated, and the number told the number.Then, Alice will result, that is, 19200 ÷ 2 ÷ 2, and soon know that he would pay 4,800 yuan in water fees.
Do you see it? This is the simplest multiplication of the same way. 800*24 is just a mapping of 400*12. The shape is the same before and after the change, so it is called “the same state”.
This encryption method is realized:Someone wants to entrust a unscrupulous entity calculation result, but it can ensure that his sensitive figures are not leaked.
>
Third, why is it “allocated” for “the same state encryption”?
However, it is just a problem in the ideal world. The problem in the real world is not so simple. Not everyone is 7 years old, or it is as honest as C.
We assume that a very bad situation, such as C may try to push back, C can also decipher Alice to calculate 400 and 12 through the poverty method.
At this time, “full -state encryption” is needed to solve.
Alice gives each number X2, which 2 can be regarded as a noise.If the noise is too little, it is easy to be cracked by C.
Therefore, Alice can introduce an additional method on the basis of multiplication.
Of course, it is best to have this noise, like the main road intersection of the main road at nine o’clock, then the difficulty of cracching C is more difficult than the sky.
Therefore, Alice can take 4 more times and add 8 times, so that the probability of C cracking has greatly reduced
However, this way is still only “part” in the same state encryption, namely:
(1) She encrypted content can only target specific parts;
(2) She can only use the specific part of the computing standard, because the number of multiplications of the addition should not be too many (generally cannot exceed 15 times)
“Quan” means that it is allowed to allow Alice to make any time to encrypt any times for a polynomial.
A super long polyntera can express most of the world’s mathematical problems, not just calculate the problem of 7 -year -old children such as electricity costs.
Add an arbitrary encryption,From fundamentally, it almost eliminates the possibility of cherishing privacy data, and it truly realizes “both must and also.”
Therefore, the technology of “all -in -law encryption” has always been a pearl on the encryption of the Holy Grail.
In fact, the same -state encryption technology only supports “part of the same state encryption” until 2009.
The new ideas put forward by scholars such as Gentry in 2009, only the door to the possibility of full -state encryption was opened.Interested readers can also move this paper.
>
Many friends still have doubts about the application scenario of this technology. What scenarios need to use the same -state encryption (FHE) technology?
For example -AI.
Everyone knows that a powerful AI requires enough data to feed, but the privacy value of a lot of data is too high.So can you “both want and still” through FHE?
The answer is okay
you can:
(1) Encryption of your sensitive data according to FHE;
(2) Calculate with encrypted data to AI;
(3) Then AI spit out a garbled code that no one can understand.
Non -monitoring AI can be implemented, because this data is essentially a vector in it, and AI, especially GPT, such as AI, does not understand at all.Answer.
However, since this garbled following follows a certain mathematical rule, you are the owner of the encryption, then:
(4) You can disconnect the network and calmly decrypt these garbled code locally, just like Alice;
(5) Then, you achieved it:Let AI use the huge computing power to complete the calculation by using the huge computing power to complete the calculation of your sensitive data.
And now AI can’t do this. You must give up privacy. Think about everything you entered to GPT! To achieve this, you must.
This is the source of AI and FHE inherently.
Because FHE and AI are hung up, spanning two major areas of encryption and AI, naturally they have been favored. There are many projects about FHE, such as Zama, Privea, Mind Network, FHENIX, SUNSCREEN, etc., the direction of FHE applicationsIt also has its own ideas.
Take one of the projects today @privasea_ai to make an analysis.
This is a FHE project of currency and settlement. Its white paper describes a very appropriate scene, such as face recognition.
Both: Machine computing power can determine whether this person is a real person;
Also: The machine is sensitive to anyone’s face without hand.
Introducing FHE can effectively solve this problem
However, if you really want to do the FHE computing of the real world, it requires a very huge computing power. After all, Alice has to do “any” addition and multiplication encryption. Whether it is calculation, encryption and decryption are a process consuming.
Therefore, it is necessary to set up a powerful computing power network and supporting facilities in Privasea.Therefore, Privasea has also proposed an architecture of a POW+POS network to solve the problem of this computing power network.
Recently, Privasea has just announced its own POW hardware called Workheart USB. This can be understood as one of the supporting facilities of the computing power network of Privasea. Of course, you can simply understand it as a mining machine.
The initial pricing is 0.2 ETH, which can dig out 6.66%of the total agent of the network.
And there is also a POS asset called Starfuel NFT, which can be understood as a “work permit” with a total amount of 5,000.
The initial pricing is also 0.2 ETH, which can get 0.75%of the total token (via airdrop).
This NFT is also a bit interesting.It is trying to avoid “whether POS is securities in the United States”.
This NFT supports users to mortgage PRIVASEA to tokens inside, but it does not directly generate POS income. Instead, it will double the mining efficiency of the USB device that you bind, so it is a disguised POS.
PS: I have invested this project before, so I have a discount MINT early bird invitation code SIA7PO, please take it yourself
nft.privasea.ai/
The book belongs to the authenticity. If AI can really popularize FHE technology on a large scale, it is really a gospel for AI itself. You must know that the focus of regulating A in many countries is now data security and data privacy.
Even an inappropriate example, such as in the Russian and Ukraine War, some Russian military are trying to use A, but considering that a large number of AI companies’ American background, the information department is probably penetrated.
But if you do not use AI, it will naturally fall behind.Even if the gap may not be large now, for another 10 years, maybe we can’t imagine the world without AI.
Therefore, data privacy is as large as the conflict between the war between the two countries, and the face of the mobile phone is unlocked, and there is no place in our lives.
In the AI era, if FHE technology can really mature, it is undoubtedly the last line of defense of human beings.