Author: faust & amp; nickqiao, geese web3
summary:InZK Bridge deployed smart contracts on Chain A, and directly received the verification verification of the B -chain block header and the corresponding zero knowledge certificate to confirm the validity of the cross -chain message, which is the most safe -level bridge.Chain messages are challenged on the chain. As long as there is a reliable challenger, you can ensure the safety of the cross -chain bridge capital pool;
InBecause of technical restrictions, the Bitcoin main network cannot directly deploy the ZK bridge, but it can achieve the optimistic bridge through BITVM and fraud.Teams such as Bitlayer and Citrea use the Bitvm bridge plan to introduce the nominal nickname, combining the channel’s ideas, allowing users to limit the processing process after the execution of the deposit is executed.Essence
InBitvm bridge essence is based on the “padding-reimbursement” modelThere are special operator nodes to make money for the withdrawal users, and Operator can regularly apply for reimbursement from the public deposit address.If the operator has false reimbursement applications, it can be challenged by anyone and SLASH;
InThe theoretically does not have security problems in theoretically, but there is a problem of activity/availability, And it cannot meet the needs of specific users for capital independence and anti -money laundering (essentially the model of the capital pool).Bitlayer adds a bridge scheme called OP-DLC, which is similar to DLC.LINK. It introduces fraud proof on the basis of channels and DLC to prevent the DLC bridge from evil.
InDue to the difficulty of the landing of BITVM and fraud, the DLC Bridge will take the lead in landing and form a temporary alternative.As long as you solve the risk of trust machines, integrate a more reliable and mature third -party prophecy,DLC Bridge can become a safer withdrawal of withdrawal verification programs than Duo Duo Bridge at this stage.
>
Introduction:Since the inscription boom last year, the Bitcoin ecology has entered a period of high -speed growth with a blowout.In just half a year, the project under the banner of BTC Layer2 has reached nearly 100.It has become a new continent with chaotic and opportunities to coexist with scams.It is no exaggeration to say that the current Bitcoin ecosystem is already the “multi -ethnic melting furnace” of Ethereum, COSMOS and CELESTIA, CKB and Bitcoin Native ecology. In addition, the lack of authoritative voices, the Bitcoin ecosystem is like the 19th century.Like the United States, it has become a new world of absorbing various forces.While bringing prosperity and vitality to the entire Web3 narrative, it also introduces huge risks.
When many projects have not even released the technical solutions, they have begun to speculate wildly, holding the name of Native Layer2, claiming that they can fully inherit the security of the Bitcoin main network;, Inventory of a bunch of strange noun terms as lines that promote their superiority.Although it is the current situation of Bitcoin ecosystem, many top KOLs have made an objective voice.
Not long ago,The founder of the blockchain browser MEMPOOL Monanaut publicly criticized the current Bitcoin ecosystem,He sharply pointed out that if a Bitcoin Layer2 simply adopts a multi -signed withdrawal bridge, it is impossible to allow users to withdraw assets at any time in a form of trust. Such a project is not a real layer2.Interestingly,Earlier Vitalik also pointed out that Layer2 should be safer than simply relying on multiple -signing systems in terms of security.
>
It can be said that Monanaut and Vitalik bluntly pointed out the technical problems of Bitcoin Layer2:Many L2’s withdrawal bridges are the essence of multiple signing bridges.Either several well -known institutions hold one key or use POS -based decentralized signatures, but in any case, their security models are based on most honest assumptions, that is, most of the number of participants in the default are not conspiring.
This withdrawal of the withdrawal of the withdrawal bridge that is seriously dependent on the credit endorsement is by no means a long -term plan. History has told us that sooner or later, there will be various problems.Methods to withstand the test of time and hackers.But the status quo of the Bitcoin ecosystem is,Many project parties have not even released the technical roadmap of the withdrawal bridge. It is a design idea of how to trust or minimize the bridge to trust or minimize the trust.
But this is not the whole of the Bitcoin ecosystem.At present, there are still some project policies who have published opinions on the optimization of the withdrawal bridge.In this article,We will briefly analyze the Bitlayer and Citrea’s Bitvm Bridge, and introduce the OP-DLC bridge proposed by Bitlayer for the deficiencies of the Bitvm bridge, so that more people understand the risk and design ideas of cross-chain bridges.This is essential for the majority of Bitcoin ecological participants.
>
Optical Bridge: Bridge verification plan based on fraudulent certification
In fact, the essence of cross -chain bridge is very simple, that is, a certain incident is indeed an incident on the B chain.For example, if you cross -assets from ETH to Polygon, let the cross -chain bridge help you prove that you do transfer to the assets to the specific address on the ETH chain, and then you can receive equal amounts of funds on the Polygon chain.
Traditional cross -chain bridges generally use witnesses to sign more,They will designate several witnesses under the chain, and the witness will run the nodes of each public chain to monitor whether someone charges the funds to the cross -chain bridge collection address.
This type of cross -chain bridge security model is basically the same as that of more wallets,It is necessary to determine its trust model according to M/N, but in the end, the most hypothetical hypothesis is basically followed by the default notary person.A large number of cross -chain bridges that have occurred before have occurred on this type of multiple signature bridges, either to defend themselves or be attacked by hackers.
In contrast,The “optimistic bridge” based on the fraud certificate and the ZK -based “ZK Bridge” is much safe.Taking the ZK Bridge as an example, it will set a dedicated authentication contract on the target chain to verify the withdrawal of withdrawal on the chain to avoid dependence on witnesses under the chain.
For example, a ZK bridge across ETH and Polygon will deploy a verification contract contract on Polygon, which is now recorded as Verifier.The Relayer node of the ZK Bridge will forward the latest Ethereum block head, as well as the effective ZK Proof to Verifier, which is verified by the latter.This is equivalent to allowing the Verifier contract to synchronize and verify the latest Ethereum block head on the Polygon chain.Merkle root recorded on the block head is associated with the transaction set contained in the block, which can be used to verify whether the block contains a certain transaction.
>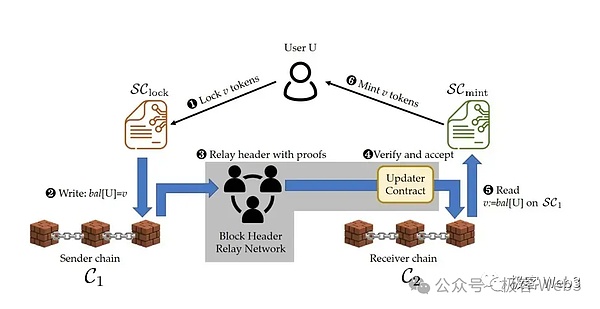
If in the Ethereum block with a block height of 101, it contains 10 transfers from ETH to Polygon, and the Relayer will generate Merkle Proof related to these 10 transactions and submit a certificate to the Verifier contract on the Polygon chain:
The 101 Ethereum block contains 10 transactions from ETH to Polygon.Of course, the ZK Bridge can use Merkle Proof to ZK, and submit ZK Proof directly to the Verifier contract.In the entire process, users only need to trust the cross -chain bridge smart contracts without loopholes, and zero -knowledge proof technology itself is safe and reliable, and there is no need to introduce too much trust assumptions like traditional multi -sign bridge.
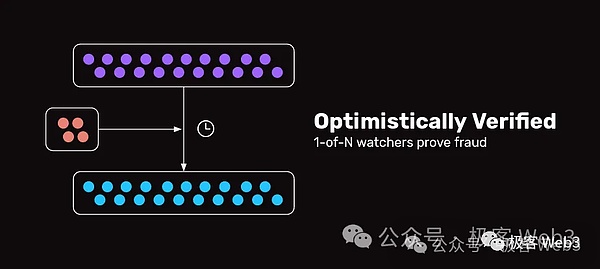
and“Optimism Bridge/Optimistic Bridge” should be slightly different. Some optimistic bridges retain the settings similar to witnesses, but they will introduce fraud proof and challenge window periodAfter the witnesses are submitted to the target chain after the cross -chain message is generated, its effectiveness will not be immediately recognized. It must be determined to be effective.This is actually similar to the idea of Optimistic Rollup (optimistic Rollup).Of course, there are other product models in the optimistic bridge, but in the final analysis, security is guaranteed by the fraud certificate agreement.
The trust of M/N Multi-signing bridge is N-(M-1)/N. You want to assume that the number of malicious people in the network is only M-1, then the number of honest people is at least n-(m-1).The trust assumptions of ZK Bridge can be ignored, and the optimistic bridge based on fraud is 1/n,Only one of the witnesses only need to have one honesty and is willing to challenge the invalid cross -chain message submitting to the target chain, and it can ensure the safety of the bridge.
>
at present,Due to technical restrictions, it can only achieve the ZK bridge in the direction of Layer2 deposit in Layer2. If the direction is the opposite, withdrawing from Layer2 to the Bitcoin chain, only supports multiple signatures or optimistic bridges, or a passage model similar to a channel model(The OP-DLC bridge to be described below is more like a channel)EssenceTo realize the optimistic bridge on the Bitcoin chain, it is necessary to introduce fraud proof that BITVM has created good conditions for the realization of this technology.
In the previous article“Minimalist interpretation BITVM: how to verify the fraud certificate on the BTC chain”We have briefly introduced,Bitvm’s fraud proves that essence is to disassemble the complex computing tasks under the chain, dismantle it into a large number of simple steps, and then pick out a certain step on the Bitcoin chainEssenceThis idea is similar to that of Ethereum such as Arbitrum, Optimism, etc. Ethereum.
>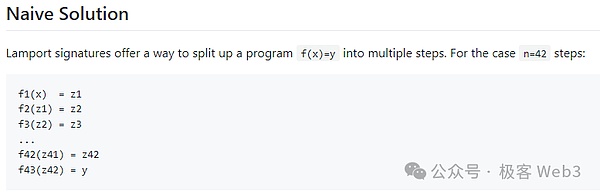
(Bitvm2 document mentioned that a computing task will be split into a large number of intermediate steps through signatures of LAMPORT, and then anyone can challenge a certain middle step)
Of course, the above statement is still obscure, but I believe that most people have long understood the meaning of fraud.In today’s article, it is limited by the overall space. We do not intend to interpret the details of the technologies of the Bitvm and the Fraud Certificate Agreement, because it involves a series of complex interactive processes.
From the perspective of product and mechanism design, we will briefly introduce Bitlayer and Citrea, Bob, and even the official Bitvm bridge designed by Bitvm, and how Bitlayer can alleviate the bottleneck of the Bitvm bridge through the OP-DLC bridge, Show everyone how to design a better withdrawal bridge plan on the Bitcoin chain.
>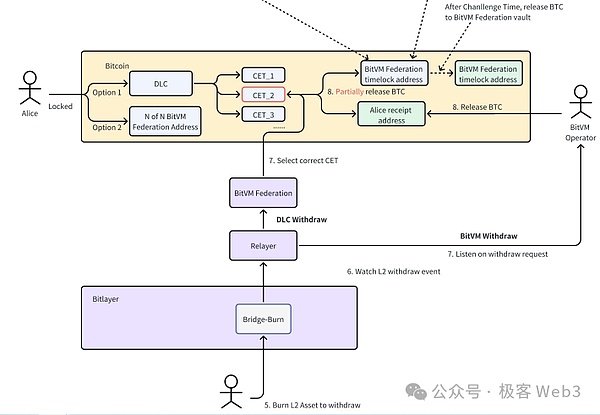
(Bitlayer’s bridge schematic diagram)
Brief analysis of Bitlayer and Citrea’s Bitvm Bridge
In the following, we use Bitlayer, Citrea, Bob’s Bitvm Bridge solution as a material to clarify the general operating process of the Bitvm bridge.
>
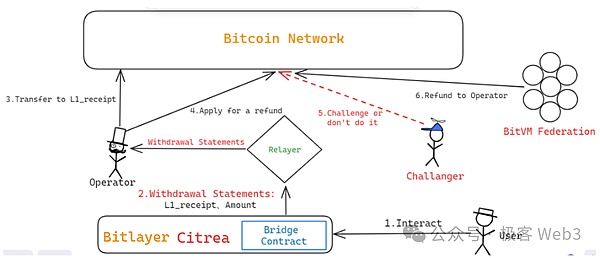
In its official documentation and technical blog, the above -mentioned project party explains the product design ideas of the Bitvm withdrawal bridge (currently in the theoretical stage).First of all, when the user withdraws the withdrawal through the BITVM bridge, it is necessary to use the Bridge contract on Layer2 to generate a withdrawal statement.The following key parameters will be specified in the withdrawal statement:
The number of mapping version of the mapping version of the withdrawal of the withdrawal (such as 1 BTC);
Cross -chain handling fees planned by the withdrawal (assuming 0.01 BTC);
The receipt address of the withdrawal in L1: L1_Receipt;
The withdrawal amount of the withdrawal (ie 1-0.01 = 0.99bTC)
after,The above -mentioned withdrawal statement will be included in the block of Layer2EssenceBitvm BridgeThe Relayer node will synchronize the Layer2 block, listen to the withdrawal statement contained in it, and forward it to the Operator node, which will be used as a withdrawal user.
>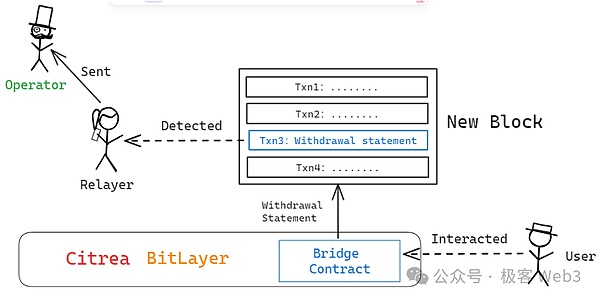
What you need to pay attention to here is,Operator is to pay for users on the Bitcoin chain first, that is, “paid” funds for the BITVM bridge, and then apply for compensation from the Bitvm Bridge’s fund pool.
When applying for reimbursement, Operator needs to provide your own cushion certificate on the Bitcoin chain (that is, to prove that you have to pay the address specified by the withdrawal user on L1, and you must take out the specific transfer records included in the Bitcoin block)EssenceAt the same time, Operator also issued a withdrawal statement generated by the withdrawal in L2 (via Merkle Proof, the withdrawal statement issued from the L2 block, not fabricated by itself).after,Operator needs to prove the following matters:
The funds paid to the withdrawal for the Bitvm bridge are equal to the amount required by the withdrawal in the statement;
When an operator applies for reimbursement, the reimbursement amount is not more than the mapping version of the BTC amount destroyed by the withdrawal in Layer2;
Operator does deal with all the L2-L1 withdrawal statements for a period of time. Each withdrawal statement can match the withdrawal record of the withdrawal on the Bitcoin chain;
This is essentially a punishment for the amount of pads on Operator or refusing to handle the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal.EssenceOperator needs to compare the key fields of the cushion certificate and the withdrawal statement under the chain to prove that the amount of BTC involved in the two is equal.
>
And if the withdrawal of the withdrawal bridge is reported, it means that Operator claims to match the Payment Proof on L1 and match with the withdrawal statement issued by the L2 withdrawal, but the actual situation is not matching the two.
In this way, the ZKP of Payment Proof = withdrawal Statement must be wrong.As long as this ZKP is released, Challange can point out which step is wrong and challenge the fraud certificate agreement by Bitvm2.
What needs to be emphasized is,Both Bitlayer and Citrea, Bob, ZKBASE, etc. both use the latest Bitvm2 route, That is, the new version of the Bitvm scheme, this scheme will use the computing task under the chain, that is, to generate ZK Proof for the computing process under the chain, then verify the ProOF, and then transform the process of verification ZKP intoIt is suitable for the form of Bitvm and facilitates subsequent challenges.
at the same time,By adopting Lamport and signing nicknames, you can optimize the multi -round interactive challenges of the original Bitvm into a single -wheeled non -interactive challenge, which greatly reduces the difficulty of challengeEssence
Bitvm’s challenge process requires a thing called “commitment”, that is, Community.We explain what is “commitment”.Generally speaking, people who release “promise” on the Bitcoin chain will claim that some data stored under the chain/The computing task that occurs under the chain is accurate, and the relevant statement issued on the chain is “commitment commitment to commitment”” “.
We can approximately understand the Community as the hash of a large number of data in a large number of dataEssenceThe size of the commitment itself is often compressed small, but it can be binded with a large number of under -chain data through Merkle Tree, and these associated linked data do not need to be on the chain.
>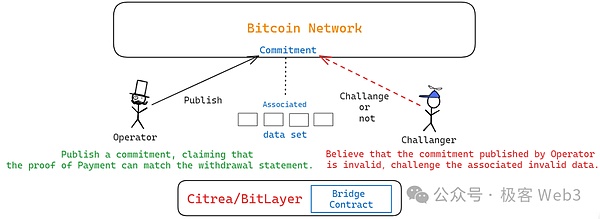
In Bitvm2 and Citrea, Bitlayer’s Bitvm bridge solution,If some people think that the promise issued by the withdrawal bridge Operator on the chain is a problem, the promise associates the invalid ZKP verification process, and the challenge can be launchedEssence(The interactive process inside is more complicated, so I do not explain here)
Because Operator is to pay funds for the Bitvm fund pool to give the withdrawal to the withdrawal, and then apply for reimbursement to the fund pool. When applying, Operator will publish a Commission款人在L2上声明要收到的钱。If this Commission has not been challenged after the scamment certificate period, Operator can take away the reimbursement amount you need.
Here we need to explain how the public capital pool of the Bitvm Bridge is maintained, which is exactly the most critical part of the cross -chain bridge.Everyone knows that the funds that the cross -chain bridge can pay to the withdrawal from the withdrawal is derived from the asset contributed by the depositer or other LP, and the money paid by Operator will eventually be withdrawn from the public fund pool, so simply depends on the funds.As a result, the amount of depositors absorbed by the BITVM bridge, the amount of depositor absorbed by the Bitvm bridge, should be equal to the amount of the withdrawal of the withdrawal.So how to keep the funds of DEPOSIT is a very important issue.
In the bridge plan of most Bitcoin Layer2, it is often managed to manage public assets by signing more. Users’ deposits are summarized into one more account. When the withdrawal of the withdrawal is required, this multi -signed account is responsible for playing.Model, this plan is obviously a huge risk of trust.
And Bitlayer and Citrea’s Bitvm Bridge uses ideas similar to the lightning network and channel.Before the deposit, the user will communicate with the Bitvm alliance to make the latter nicknamed to achieve the following effects:
After the user is transferred to the deposit to the recharge address, the money will be locked directly on a Taproot address, and can only be collected by the bridge’s operator.In addition, Operator only applies to users to apply for reimbursement to apply for the Taproot address of the above deposit through the method of reimbursement.After the challenge period is over, Operator can take away a certain amount of user deposits.
In the Bitvm bridge scheme, there is a Bitvm Alliance (Bitvm Federation) formed by N members, which will schedule the user’s deposit.However, these N members cannot misappropriate users’ deposits without permission, because users will ask the BITVM alliance to sign a signature nickname before the user uses it to ensure that these deposits can only be legally applied by operator.
>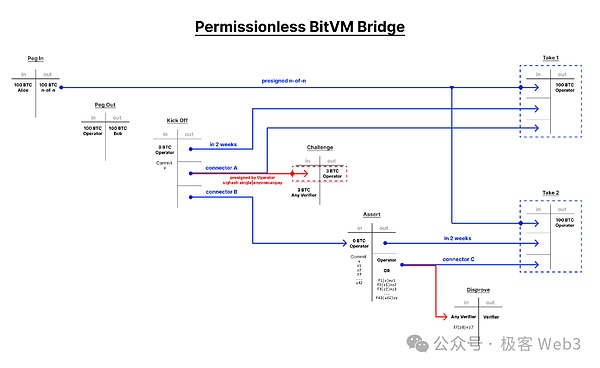
(Bitvm2’s diagram of its optimistic bridge scheme)
In summary, the BITVM bridge uses the idea similar to the channel and lightning network.Let the user “Verify By Yourset” make the Bitvm alliance unable to manipulate the deposit pool through the nominated manner,The money in the deposit pool can only be used to reimburse the funds for Operator.If Operator lies on the amount of mats, anyone can issue a fraud certificate and challenge.
If the above plan can be landed, the BITVM bridge will become one of the safest Bitcoin withdrawal bridges:There is no security problem in this bridge, and only available/activity problems are existing.When users try to deposit funds to Bitvm, they may be reviewed or refused by the Bitvm Alliance, resulting in unable to deposit funds smoothly, but this has nothing to do with security and is active/available.
But the landing of the Bitvm bridge is more difficult,And it is also impossible to meet the needs of large households with high demands for capital transparency: these people may involve anti -money laundering problems, and do not want to mix their funds with other people’s funds, but the BITVM bridge will uniformly store the money of depositors’ moneyTo some extent, it is a pond with a lot of money.
In order to solve the active problem of the above BITVM bridge, and to provide independent and clean funds in and out of the channel for people with specific needs.The Bitlayer team adds an additional cross-chain bridge solution called OP-DLC. In addition to the optimistic bridge of Bitvm2, the DLC bridge similar to DLC.LINK is used.Provide users with two entrances of the BITVM Bridge and OP-DLC Bridge to reduce their dependence on the Bitvm bridge and even the Bitvm alliance.
>
(DLC principle diagram)
DLC: Careful log contract
DLC (Discreet Log Contracts) is called a cautious log contract. It was proposed by MIT’s DIGITAL CURrency Initiative that the technology was first used to achieve a lightweight smart contract on Bitcoin.Through methods such as interactive communication and signature names under the chain, smart contract functions to protect privacy on the Bitcoin chain.Below we use a gambling case to illustrate the working principle of DLC.
Assuming that Alice and BOB will bet on the results of Real Madrid and Barcelona held 3 days later, each of them has 1 BTC.If Real Madrid wins, Alice can get 1.5 BTC, and BOB can only recover 0.5 BTC, which is equivalent to earning 0.5 BTCs by Alice and 0.5 BTC for BOB; if Barcelona is coming out, Alice can only recover 0.5 BTC, and BOB can take 1.5.5BTC.If the game is drawn, the two have taken one BTC from each.
If we want to trust the above gambling process, we must find ways to prevent any party from playing. If you simply sign with 2/2 or more than 2/3, it is obviously not enough to trust.DLC gives its own solution for this point (depending on the third party prophecy machine).The entire workflow can be divided into four parts.
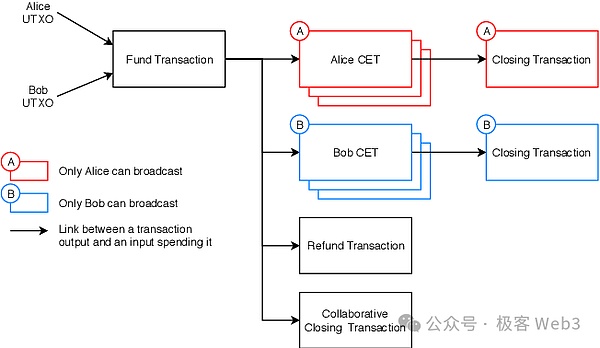
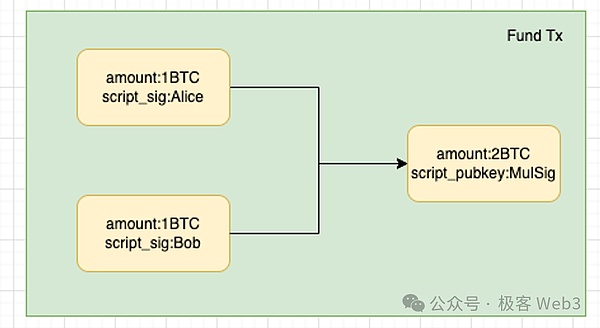
Take the previous Alice and Bob as an example.First of all, the two sides create a FUND transaction under the chain, which can lock each other’s BTC on the 2/2 signal addressIf the Fund transaction takes effect, the two BTCs in the multi -signed address need to be authorized by both parties to be spent.
Of course, this Fund transaction is not on the chain first, leaving only the Alice and BOB clients under the chain. They all know what the consequences will be after the transaction is effective.At present, the two sides are only conducting theoretical deductions, and then reached a series of protocols based on the results of the deduction.
In the first stage of DLC creation, what we can determine is thatThe two parties will locked their respective BTCs into a multi -signal address in the future.
>
In the second step, the two sides continue to deduce the events and results that may happen in the future:For example, when the results of the game are announced, it may be a variety of possibilities such as the Alice winning BOB losses, Alice loses BOB wins, and drawing, which will cause different distribution results in the Bitcoin in the above -mentioned 2/2 more.
Different results need to be triggered by different transaction instructions. These“Perhaps the trading instruction may be on the future” is called CETAnd contract execution transaction.Alice and BOB have to launch all the CETs in advance to generate transaction data sets containing all CETs.
For example,According to several possible results of the aforementioned Alice and Bobs, Alice creates the following CET:
CET1:Alice can get 1.5 BTC from the multi -signal address, and the BOB can get 0.5 BTC;
CET2:Alice can get 0.5 BTC from the multi -signal address, and the BOB can get 1.5 BTC;
CET3:Both sides can get 1 BTC.
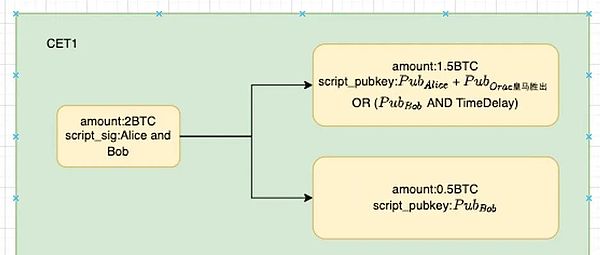
Let’s take CET1 as an example (Alice take 1.5 BTC and Bob with 0.5 BTC):
This transaction means that the 1.5 BTC in the multi -signal address is transferred to a Taproot address jointly triggered by the output result of the Alice and prophet output, and the other 0.5 BTC transferred to the BOB.The corresponding event at this time was: Real Madrid won, Alice won 0.5bTC, BOB lost 0.5bTC.
>
certainly,To spend this 1.5 BTC, Alice must get the signature of the “Real Madrid victory” results sent by the prophet machineEssenceIn other words, only when the prediction machine outputs “Real Madrid Victory”, Alice can transfer these 1.5 BTCs.As for the content of CET2 and CET3, we can use and so on, so I won’t go into details.
>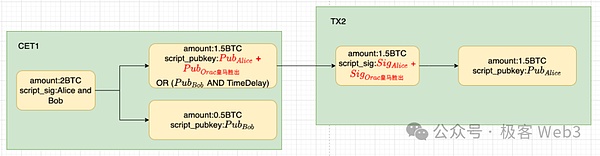
It should be noted that CET is essentially a transaction that is waiting to be effective.If Alice broadcasts CET1 in advance, or in the case of “Barcelona victory”, what will happen to the CET1 that can only be triggered by “Real Madrid”. What will happen?
In the previous schematic diagram, we mentioned that after the CET1 is on the chain, the 2 BTCs locked in the original multi -signal address will be transferred away, 0.5 BTC to BOB, and 1.5 BTCs to a Taproot address.After Real Madrid wins “, Alice can unlock the BTC locked by the Taproot address.The effect is shown in the figure below.
At the same time, this Taproot address is limited by time lock,If Alice cannot successfully take 1.5 BTCs during the window period of the time lock, BOB has the right to take the money directly.
Therefore, as long as the prophet machine is honest, Alice cannot take these 1.5 BTCs. The time limit for the time lock is exhausted, and BOB can take these 1.5 BTCs.The 0.5 BTC that is directly transferred to the BOB when CET1 is on the chain, and all the money will be owned by BOB in the end.
>
For Alice, no matter whether you are in the end or loss, the most favorable way is to put the correct CET on the chain, and the invalid CET chain will make you lose more money.
In fact, when the above CET was constructed, it improved the signature of Taproot’s Schnorr. It can be understood as the use of the public key+event results of the prophecy machine to construct each other’s independent address for different results.After that, the signature corresponding to a result of the prediction machine can cost the lock BTC corresponding to the address corresponding to the result.
Of course, there is an extra possibility in it.If Alice knows that he has lost, he simply does not put on the CET1 you built, what should I do at this time?This is easy to solve, becauseBOB can build a custom CET for the “Alice Losing, BOB Win”. The effect of this CET is basically the same as the CET built by Alice, but the specific details are different, but the results are the same.
The above is the most critical CET construction process.The third step of DLC is to communicate with both parties and BOB, check the CET transaction built by the other party, and bring themselves to the CET signature. After checking it correctly, you can trust each other.The mentioned Alice and BOB’s 2/2 -signing address, and then wait for a CET to be on the chain to trigger the follow -up process.
Finally, after the results of the prophecy machine are announced, after getting the signature of the results of the prophecy machine, any party can put the correct CET on the chain and let the two BTC locked in the multi -signal address are reuse.The chain will make yourself lose all the money. If the correct CET is on the chain, the loser can also recover 0.5bTC.
>
Someone may ask,What is the difference between DLC and ordinary 2/3 more?First of all, signed more 2/3, and any two sides can steal all assets. DLC can restrict the opponent by building the CET collection in advance.The loss caused by conspiracy is often limited.
Secondly, the multiple signatures require the signature of the specific parties to the on -chain transaction, andUnder the setting of DLC, the prophetic machine only needs to sign the results of specific events, do not need to know the content of CET/to be traded in the chain, or even no need to know that there are two people of Alice and BOB.Just interact with the user like the machine.
We can think,DLC is essentially to transform the trust of the number of participants into the trust machine.As long as the prediction machine does not participate in evil, it can ensure that the DLC protocol design is enough to trust.Theoretically,DLC can use a relatively mature and perfect third -party prophecy machine to avoid evilEssenceAnd DLC.LINK and Bitlayer took advantage of the characteristics of DLC to pass the trusted problem of the bridge to the third -party prophecy machine.
In addition, the Bitlayer’s DLC Bridge also supports self -built prophecy nodes. On this one, a layer of fraud proves are added. When the self -built prophecy machine comes to the chain of the invalid CET, it allows anyone to challenge it.For the principle of its OP-DLC bridge, we will start a brief description below.
OP-DLC Bridge: DLC channel+fraud certificate
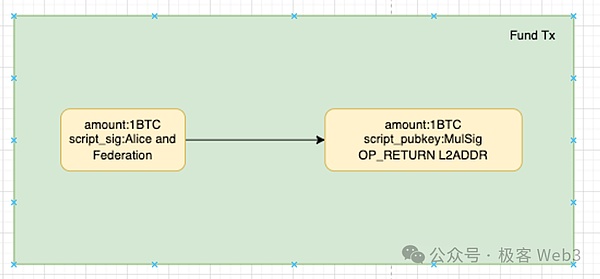
We explain the operating principle of the OP-DLC bridge from the full process of withdrawal.Suppose that now Alice has a BTC deposit to L2 through the OP-DLC bridge,According to the two-step trading mechanism, Mr. Alice forms a Pre-Fund transaction, As shown below:
>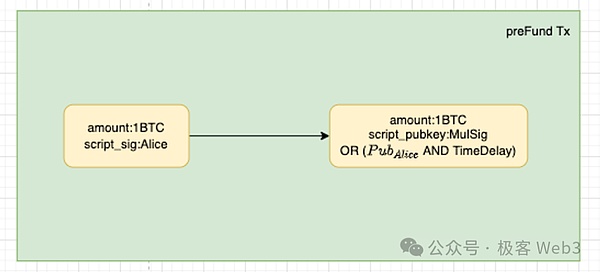
This is actuallyFirst transfer 1 BTC to the Taproot address controlled by the members of Alice and Bitvm Alliance, and then turn on a series of processes to create CET.If members of the Bitvm Bridge Alliance refuse to cooperate with Alice’s deposit request, Alice can wait for the time to lock, and immediately pull the money back.
If members of the Bitvm alliance are willing to cooperate with Alice, the two parties will form a formal Fund deposit transaction (not on the chain first) and all the CETs in the withdrawal of the withdrawal of the withdrawal of the withdrawal of the withdrawal.Submit the Fund transaction.
In the Witness/Signature Data of Fund transaction,Alice will specify your receipt address on Layer2;After the Fund transaction is on the chain, Alice can submit the above Fund transaction data to the bridge contract on Layer2 to prove that he has completed the deposit action on the Bitcoin chain and is eligible to release the L2 bridge contract to the designated receipt address to release token.
>
After the Fund transaction is triggered, the deposit is actually locked in the Taproot multi -signal address controlled by members of the Alice and Bitvm Alliance.However, it should be noted that CET can only unlock the address locking BTC through CET. The Bitvm alliance cannot turn the money away for no reason.
Next, let’s analyze the CET built by Alice and Bitvm alliances in advance.These CETs are used to meet the potential scenes of future withdrawals. For example, Alice may deposit 1 BTC, but when she first withdraws the withdrawal, only 0.3 BTCs are taken off, and the remaining 0.7 BTCs are submitted to the Public Fund Pool of the Bitvm AllianceCome to dominate, but you can only use the Bitvm bridge mentioned earlier;
Or simply use this 0.7 BTC to initiate a new Pre-Fund deposit as an asset that is newly charged into the DLC bridge. You can repeat the Fund transaction and CET construction process mentioned earlier.
>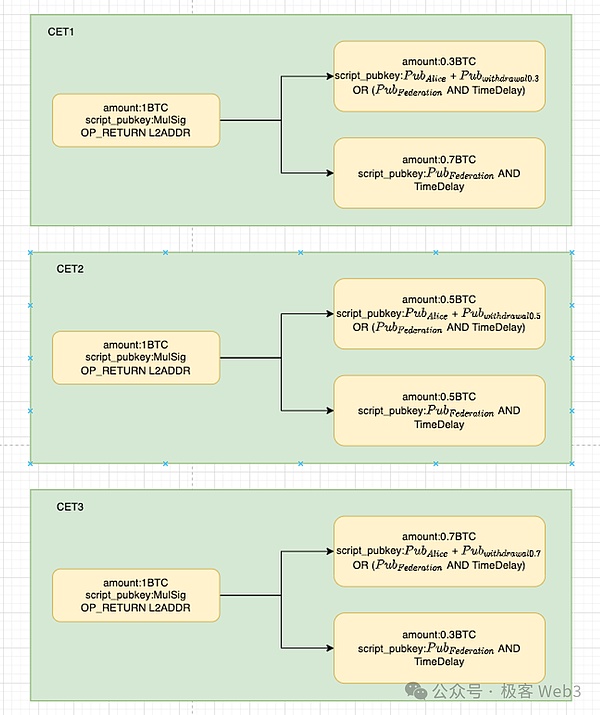
The above process is not difficult to understand. In fact, the depositer Alice and the Bitvm Alliance act as the opponent to create a CET for different amounts of withdrawal events, and then let the prophecy machine read the withdrawal statement initiated by Alice on Layer2 to determine which Alice wants to trigger which trigger trigger is triggered.A CET (how much does you want to mention).
The risk in it is that the prophetic machine may conspire with the Bitvm alliance, such as the Alice statement to withdraw 0.5 BTCs, but the prediction machine forged a withdrawal statement, and eventually made the “Alice recover 0.1BTC, BITVM Alliance received 0.9bTC”Error CET on the chain.
There are several solutions to this. First of all, you can use a relatively complete third -party prophecy machine.Prevent this kind of conspiracy (at this time the BITVM alliance is extremely difficult to win with the prophecy machine),Or let the prophet machine pledge,The prophecy machine needs to release the Commission on the Bitcoin chain on a regular basis to declare that he honestly handle the withdrawal request of the withdrawal of the withdrawal of the withdrawal.Anyone can challenge the Community through Bitvm’s fraudulent proof protocol. If the challenge is successful, SLASH is a evil prophetic machine.
>
Under the design of the OP-DLC bridge, users can always “take one hand” to their assets to prevent the assets from being misappropriated by the BITVM alliance, and this design scheme similar to the channel brings more autonomy to users, and alsoYou don’t need to let your funds be mixed with other people’s funds, more like a P2P point -to -point access scheme.
also,Considering that the BITVM solution can only be implemented for a while. Before its landing, compared with simple multi -sign schemes, the DLC bridge is a more reliable bridge processing model.This scheme can also be used as two major deposits to withdraw from the BITVM bridge. One of them can take the other entrance after one out of the failure, and it is also a good fault tolerance method.
Summarize
Bitlayer and Citrea’s Bitvm bridge solution, which is essentially the “advance payment-reimbursement” modeThere are special operator nodes to make money for the withdrawal users, and Operator can regularly apply for reimbursement from the public deposit address.If there is a false reimbursement application, anyone can be challenged and slash.
Bitvm2’s solution is introduced to the signature name, combining the passage of the channel, allowing users to limit the processing process after the execution of the deposit execution before the formal deposit, and do not give the cross -chain bridge official misappropriation of opportunities for user deposits.
This bridge does not have security problems in theory, but there is a problem of activity/availability, And it cannot meet the needs of specific users for capital independence and anti -money laundering (essentially the model of the capital pool), and it is also difficult to land.
为此,Bitlayer增设了名为OP-DLC的桥接方案,该方案类似于DLC.link,在通道和DLC的基础上引入欺诈证明,防止DLC桥的预言机作恶。
However, because the landing of BITVM is too difficult, the DLC Bridge will take the lead in landing and temporarily alternative.As long as you solve the risk of trust machines, integrate a more reliable and mature third -party prophecy,DLC Bridge can become a safer withdrawal of withdrawal verification programs than Duo Duo Bridge at this stage.