
Author: Arweave Oasis Chinese, Source: Author Twitter Twitter
In front
For about a month, Bitcoin will start to be halved in the next round.But the author believes that Nakamoto’s vision -everyone can use the consensus of CPU participation, and has never been realized.At this point, Arweave’s mechanism iteration may be more faithful to the vision of Satoshi Nakamoto, andVersion 2.6 makes the Arweave network truly meet the expectations of Satoshi NakamotoEssenceIt has made great improvements than the previous version, just to achieve:
-
Limit hardware acceleration, general -level CPU + mechanical hard disk can participate in the system’s consensus maintenance, thereby reducing the storage cost;
-
Call the consensus cost to effective data as much as possible, rather than high -energy -consuming hash arms competitions;
-
Stimulate miners to build their own complete Arweave dataset copies, allowing data to routing faster and more distributed storage.
Consensus mechanism
Based on the above goals, the mechanism of version 2.6 is roughly as follows:
-
A new component is added to the Hash Chain in the original SPORA mechanism. It is the previously mentioned encrypted algorithm clock, which will generate a SHA-256 mining hash.
-
Miners select a partition index in their own data partitions, and start mining with mining hash, and mining address as mining input information.
-
A retrospective range 1 is generated in the partition selected by the miner, and a random position in the weaving network is regenerated into a retrospective range 2.
-
Calculate the retrospective data block (Chunk) within the retrospective range 1 to try whether it is a block solution.If the calculation result is greater than the current network difficulty, the miner obtains the right of block; if it is not successful, calculate the next retrospective block in the retrospective range.
-
The retrospective data block in range 2 may also be calculated and verified, but the solution there requires hash in the range 1.
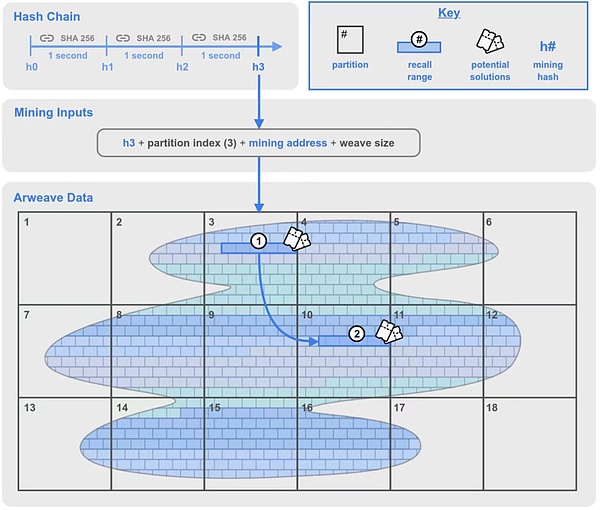
Figure 1: 2.6 version of the consensus mechanism diagram of the consensus mechanism
Let’s get to know the concepts of nouns that appear in this mechanism:
-
Arweave data:Also known as “weaving”.All the data in the network are divided into data blocks one by one, and the English name chunk (the blocks like “brick walls” in the figure above are chunk).These blocks can be evenly distributed in the Arweave network, and through the method of Merkel Tree to establish a addressing solution for each data block (also known as Global Office global offset) to identify any position in the weaving networkData block.
-
Data block (chunk):The size of each data block is usually 256 KB.To win the right of block, the miner must pack and haveh processing of the corresponding data blocks, and proves that they have stored data copy during the SPORA mining process.
-
Partition: “Partition” is a new concept in version 2.6.Every 3.6TB is a partition.The partition has been numbered from the beginning of the weaving network (index 0) to the number of partitions that cover the entire weaving network.
-
Recall Range: The retrospective range is also a new concept in version 2.6.It is a series of continuous data blocks (CHUNK) with a length of 100MB from a specific offset and a length of 100MB.Calculated by a data block of 256 KB, it includes 400 data blocks in a retrospective range.In this mechanism, there will be two retrospective scope, which will be explained in detail below.
-
Potential solution:Each 256KB data block within the retrospective range will be a potential solution to obtain the right to get out of the block.As part of the mining process, each data block will be handled by hash to test whether it meets the difficulty requirements of the network.If you are satisfied, the miners will win the right to get out and get mining rewards.If it is not satisfied, the miners will continue to try the next 256kb block within the retrospective range.
-
Hash Chain:The hash chain is a key update of version 2.6. It has a encrypted clock added to the previous SPORA, which plays a speed limit of limiting the maximum hash.The hash chain generates a section of data continuously by using the SHA-256 function.This process cannot be calculated parallel (consumer CPU can be easily done), and the hash chain can achieve a delayed 1 second effect by performing a certain number of continuous hash processing.
-
Mining hash (mining hash): After a sufficient number of continuous hash (that is, after 1 second delay), the hash chain output is a hash value that is considered to be effective for mining.It is worth noting that mining hash is consistent between all miners, and all miners can be verified.
After introducing all the necessary noun concepts, we can better understand how the 2.6 version operates through how to obtain the best strategy.
Best strategy
Arweave’s overall goal has been introduced many times before, that is, the number of data storage copies on the network.But what do you save?How to save?There are also many requirements and doorway.Here we will discuss how to take the best strategy.
Replicas and Copies
Since version 2.6, the author has frequently seen two words in various technical materials, replicas and Copies.Both concepts translate into Chinese can mean a copy, but in fact, there are very big differences between them, which also causes a lot of obstacles to me when I understand the mechanism.To facilitate understanding, I tend to translate replicas into “copies” and translate Copies into “backup”.
Copies backup means that there is no difference between the data of the same data.
The meaning of the replicas copy is to pay attention to its uniqueness, and it is to store the data after a unique processing of the data.Arweave network encourages the storage of the copy, not simply backup storage.
Note: The consensus mechanism in version 2.7 has become Spores, which is the simple replication certificate for the SUCCCINCT PROOFS of Replications, which is stored in a copy, and I will interpret it in the future.
Packing the unique copy (Packing Unique Replicas)
The only copy is very important in the Arweave mechanism. Miners who want to obtain the right of block must be packed in a specific format to form their own unique copy. This is prerequisite.
If you want to run a new node, it is not possible to copy data that other miners have packed directly.You first need to download the original data in the arweave weaving network (of course you don’t want to download all, only the download part can be set, you can also set your own data policy, filter out risk data), and then pack these through the RandomX function to package these.Each data block of the original data makes it a potential mining solution.
The packaging process includes a Packing Key packing key to the RandomX function, which allows it to pack the original data block through multiple operations.The process of unzip the packaging data block is the same. It provides the packaging key and unzip the packaged data block with the results generated by multiple operations.
In version 2.5, the Packing Key backup is a SHA256 hash has a SHA256 hash has been associated with the position parameters of the data block as the position parameter of the data block) and the TX_ROOT (transaction root) associated with.This ensures that each mining solution comes from the only copy of the data block in a specific block.If a data block has multiple backups in different locations in the network, each backup needs to be backup into a unique copy.
In version 2.6, this backup key is extended to Chunk_offset, TX_ROOT, and Miner_address (miner address).This means that each copy is also unique to each mining address.
The advantage of storing the complete copy
The algorithm recommends that the miner is to build a unique complete copy, rather than a part of the copy that is copied multiple times, which makes the data in the network evenly distributed.
How do you understand this part?We understand through the comparison of the following two pictures.
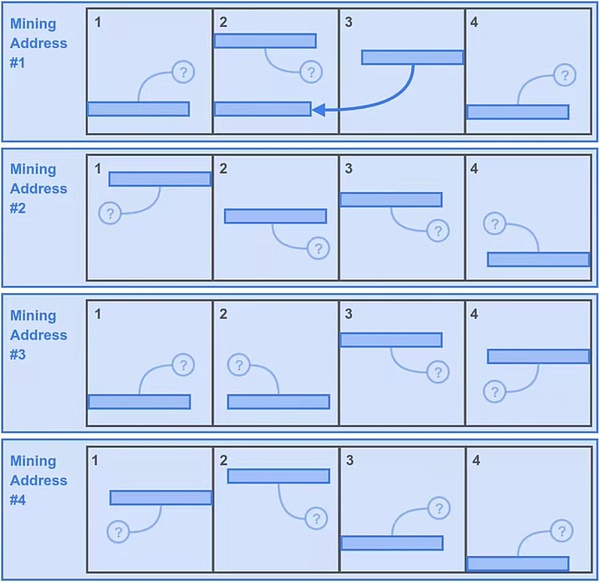
First of all, let’s assume that the entire ArWEAVE broken network generates a total of 16 data partitions.
The first case:
-
Miner Bob is too time -consuming to download the data, so only the data of the first 4 partitions that destroy the network.
-
In order to maximize the mining copy of these 4 districts, Bob’s clever machine moved 4 copies of the data of these 4 divisions, and used different 4 mining addresses to form them with 4 unique copy resources to fill them.It has its own storage space, so there are 16 partitions in the storage space of BOB.There is no problem in this way, which is in line with the rules of the only copy.
-
Next, when BOB can get mining hash every second, the data block of the data block of a retrospective substance is for each of the partitions for the aggression test.This makes BOB get 400* 16 = 6400 potential mining solutions in one second.
-
But Bob is also the second price for his little cleverness, because he must lose a mining opportunity to trace a retrospective range. Did you see these “small question numbers”?They represented the relevant second retrospective range in the hard disk of BOB, because they marked the data partition that BOB did not store.Of course, good luck, and there are relatively low indicator lights that symbolize the four districts of BOB storage. This is 25%of this, that is, 1600 potential solutions.
-
So this strategy allows BOB to have 6400+1600 = 8000 potential solutions per second.
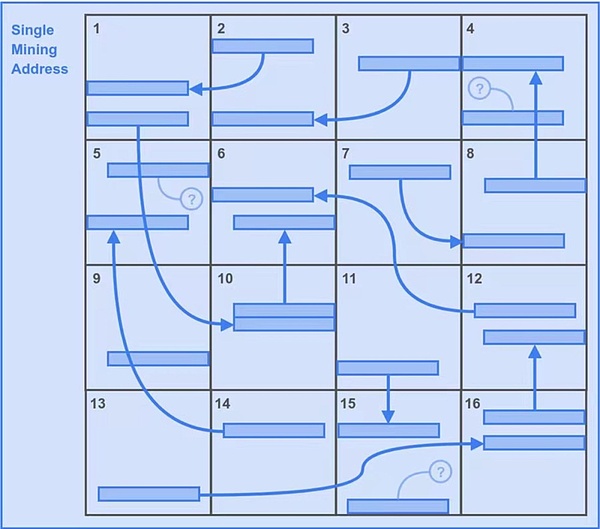
The second case:
Then let’s look at the second situation.Due to the arrangement of two retrospective mechanisms, a better strategy is the only copy of the storage problem.As shown in Figure 3.
-
The miner Alice is not as “smart” as Bob. She has downloaded the partition data of all 16 partitions in this division, and only uses one mining address to form a unique copy of 16 backups.
-
Because Alice is also 16 partitions, the first potential solution of the first traceable range is consistent with the BOB, and it is also 6,400.
-
But in this case, Alice has gained all the second traceable solutions.That is the extra 6400.
-
So this allows the Alice strategy to have 6400+6400 = 12800 potential solutions per second.The advantage is self -evident.
The role of the retrospective range
Maybe you will be weird. Before version 2.5, the offset of a single back retrospective block through the function hash will give the miners find and give the storage certificate again. Why is there a back traceable range?
The reason is actually very well understood. The retrospective range is composed of continuous data blocks. This structure is not anything else. The purpose is to minimize the movement of the readable head (HDD) of the mechanical hard disk (HDD).The physical optimization brought by this method enables the reading performance of HDD to be placed with the more expensive SSD hard disk (SSD).This is like tie a hand and one foot for SSD. Of course, it can transmit four retrospective range per second to have expensive SSDs, and it still has a little speed advantage.But compared to cheaper HDDs, the count will be a key indicator for miners’ choice.
Verification of hash chain
Now let’s discuss the verification of the next new block.
To accept a new block, the verifier needs to verify the new blocks that block producers synchronize. The method is to use the mining hash it to verify the mining hash hash.
If the verification is not at the current head of the hash chain, each mining hash includes 25 40 millisecond checkpoints.These checkpoints are the result of a continuous hash 40 milliseconds. They combine together represents the one -second interval of the starting hash from the previous mining.
Before the authentication of the newly received block to other nodes, the verification will quickly complete the first 25 checkpoints within 40 milliseconds. If the verification is successful, it will cause the dissemination block and continue to complete the verification of the remaining checkpoints.The complete checkpoint is completed by all verification of the remaining checkpoints.The first 25 checkpoints are 500 verified checkpoints, and then 500 verified checkpoints. The interval between the 500 checkpoints of each group in each group is doubled.
When the hash chain generates a mining hash, it must be performed in order.However, the verification of the verification can be verified when the inspection point can be verified, which can make the time of the verification block shorter and improve efficiency.
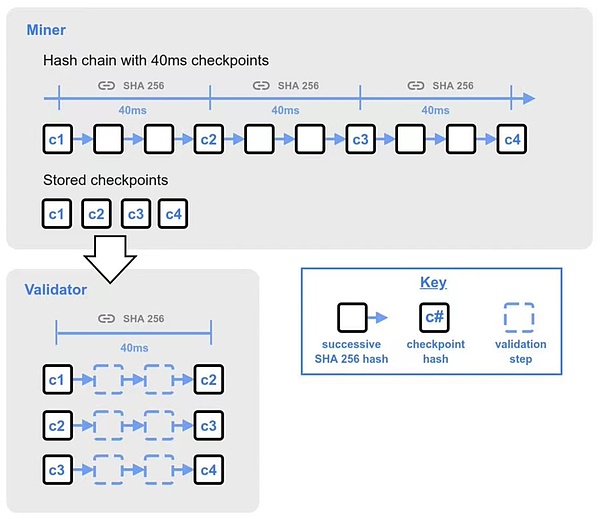
Figure 4: The verification process of the hash chain
Hash chain seeds
If the miner or mining pool has a faster SHA256 hash computing power, their hash chain may lead other nodes in the network.Over time, the advantages of this block speed may accumulate a huge hash chain offset, and the mining hash has not synchronized with the rest of the verification.This may lead to a series of uncontrollable forks and reorganization phenomena.
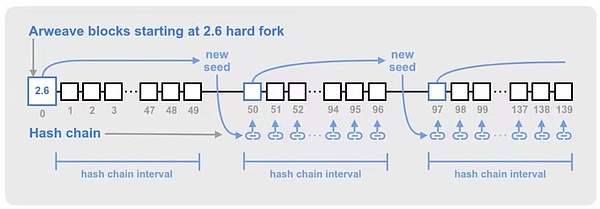
In order to reduce the possibility of this hash chain offset, Arweave simultaneously synchronizes the global hash chain by using tokens from historical blocks on a fixed interval.This will regularly provide new seeds for hash chains, so that the hash chain of each miner will synchronize with a verified block.
The interval between the hash chain seeds is every 50 * 120 mining hash (50 represents the number of blocks, and 120 represents the number of mining hash in a block production cycle 2 minutes) to choose a new seed block.This makes the seed block appear about 50 arweave blocks once, but due to some changes in the block time, the seed block may appear earlier and later than 50 blocks.
The above is the content selected from the 2.6 specifications. From these, it can be seen that Arweave has achieved low power consumption since 2.6. Below, more decentralized ideological mechanism to run the entire network.Nakamoto’s vision was practiced in Arweave.
Arweave 2.6:
https://2-6-spec.arweave.dev/https://2-6-dec.arweave.dev








