
Too long to read the version:
Zero Knowledge Proof (ZKP) is obviously useful for improving scalability and privacy in web3, but is hampered by relying on third parties to process unencrypted data.
Fully homomorphic encryption (FHE) brings breakthroughs that allow for simultaneous shared and separate private state without the need for third-party trust requirements.
FHE can directly calculate encrypted data, thus supporting applications such as dark pool AMMs and private lending pools whose global status information is never leaked.
Benefits include trustless operations and permissionless on-chain state transitions on encrypted data, with challenges focused on computational latency and integrity.
Major players in the emerging FHE cryptocurrency space focus on the development of private smart contracts and dedicated hardware acceleration for scaling.
Future FHE crypto architecture includes the potential to integrate FHE rollups directly on Ethereum.
“One of the biggest challenges left in the Ethereum ecosystem is privacy (…), using a complete set of Ethereum applications involves bringing a large part of your life to be viewed and analyzed by anyone.” – Vitalik
Zero Knowledge Proof (ZKP) has been a darling in the field of cryptography for at least the past year, but it also has its limitations.They are valuable for privacy, proving information knowledge without revealing information, and scalability, especially in zk-rollups, but they currently face at least some major limitations:
(1) Hidden information is usually stored and computed off-chain by trusted third parties, limiting the permissionless composability of other applications that need to access these off-chain data.This server-side proves to be similar to systems like web2 cloud computing.
(2) The state transition must be done in plain text, which means that the user must trust third-party certifiers who have unencrypted data.
(3) ZKP is not suitable for applications that require knowledge of shared private states to generate proofs about local private states.
However, any multi-person use case (e.g. dark pool AMM, private lending pool) requires shared private state on-chain, which means using ZK requires some kind of centralized/off-chain coordinator to implement shared private state, which makes it cumbersomeAnd introduce the trust assumption.
Input full homomorphic encryption
Fully homomorphic encryption (FHE) is an encryption scheme that allows calculations to be performed on data without prior decryption.It allows users to encrypt plaintext as ciphertext and send it to a third party to process it without decryption.
What does this mean?End-to-end encryption.FHE allows sharing of private state.
For example, in AMM, the decentralized market maker account interacts with each transaction, but does not belong to any single user.When someone exchanges Token A for Token B, they must understand the existing amount of the two tokens in the shared market maker account to generate a valid proof of exchange details.However, if the global state is hidden through the ZKP scheme, generating the proof will no longer be feasible.Conversely, if global status information is publicly accessible, other users can infer details about the personal exchange.
With FHE, the shared and personal states can be hidden in theory, as proofs can be calculated by encrypting data.
In addition to FHE, another key technology to implement the Holy Grail of Privacy is multi-party computing (MPC), which solves the problem of performing calculations on private inputs and only discloses the results of these calculations while retaining the confidentiality of the inputs.However, we leave it for another discussion.Our focus here is FHE – its pros and cons, current market and use cases.
It is worth noting that FHE is still in its early stages of development, which is not a tribalist issue with FHE with ZKP or FHE with MPC, but an additional feature unlocked when combined with the currently available technology.For example, a privacy-focused blockchain could use FHE to enable confidential smart contracts, use MPC to distribute shards of decryption keys between validators, and use ZKP to verify the integrity of FHE calculations.
Pros and Cons
At this point: The benefits of FHE include:
1. No third-party trust requirements.Data can be kept secure and private in an untrusted environment.
2. Composability by sharing private state.
3. Data availability while maintaining data privacy.
4. (Ring) Quantum Resistance of LWE.
5. Ability to perform on-chain state transitions on encrypted data without permission.
6. There is no need for hardware and centralized supply chains as vulnerable to side-channel attacks like Intel SGX.
7. In the context of fully homomorphic EVM (fhEVM), there is no need to learn to perform repetitive mathematical multiplication (e.g., multiscalar multiplication) or use unfamiliar ZK tools.
The disadvantages include:
Lurking.Computation-intensive means that most solutions are currently not commercially viable for computing-intensive applications.It is worth noting that given the hardware acceleration is under active development, this is a short-term bottleneck, and at this point Zama’s fhEVM can already achieve about 2 TPS on hardware at about $2,000 a month.
Accuracy issues.The FHE scheme requires noise management to prevent ciphertext from invalidating or corruption.However, TFHE is more accurate because it does not require approximation (unlike CKKS for some operations).
Early.There are very few production-ready FHE projects launched in the web3 space, which means a lot of combat testing is required.
Market Overview
Current FHE x cryptocurrency landscape
emphasize
Zama provides a range of open source FHE tools for encrypted and non-encrypted use cases.Its fhEVM library supports private smart contracts to ensure on-chain confidentiality and composability.
Fhenix uses Zama’s fhEVM library to implement end-to-end encryption aggregation.Their goal is to simplify the process of integrating FHE into any EVM smart contract with minimal modification to existing contracts.The founding team consists of Secret Network founder and former head of Intel FHE bizdev.Fhenix recently raised $7 million in seed funding.
Inco Network is an EVM-compatible L1 powered by FHE, which integrates Zama’s fhEVM encryption technology to introduce the computing of encrypted data into smart contracts.Founder Remi Gai is one of the founding members of Parallel Finance and has worked with several Cosmos engineers to realize this vision.
hardware.Some entities are building hardware acceleration to solve the latency problem.Notably, Intel, Cornami, Fabric, Optaanalysis, KU Leuven, Niobium, Chain Reaction and some ZK ASIC/FPGA teams.This surge was driven by DARPA’s grant of ASIC-based FHE accelerated grants about three years ago.That said, this specialized hardware acceleration may not be necessary for some blockchain applications with a GPU that may reach 20+ TPS.FHE ASIC can increase performance to 100+ TPS while significantly reducing the operating costs of the validator.
Notable mention.Google, Intel, and OpenFHE have all made significant contributions to the overall progress of FHE, but the specificity in the field of encryption is not so specific.
Use Cases
The key advantage is to achieve shared private state and personal private state.What does this mean?
Private smart contracts: The traditional blockchain architecture exposes user data to web3 applications.Each user’s assets and transactions are visible to every other user.This is useful for trust and auditability, but it is also a major obstacle to enterprise adoption.Many companies are reluctant or simply refuse to disclose this information.FHE changed that.
In addition to end-to-end crypto transactions, FHE also supports encrypted memory pools, encrypted blocks and confidential state transitions.
This unlocks a variety of novel use cases:
DeFi: Dark Pool, eliminates malicious MEVs through encrypted memory pools, untrackable wallets, and confidential payments (such as employee salaries for on-chain organizations).
Game: Encrypted state multiplayer strategy game, supporting various new game mechanisms, such as secret alliances, resource hiding, destruction, spy, bluffing, etc.
DAO: Private voting.
DID: Encrypt credit scores and other identifiers on the chain.
Data: Compliant on-chain data management.
So what will the future of FHE encryption architecture look like?
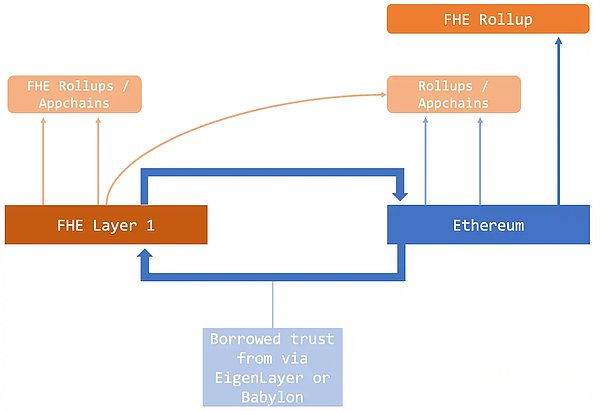
We should elaborate on three core components:
Layer 1: This layer is the basis for developers (a) to launch applications locally on the network or (b) to interface with the existing Ethereum ecosystem (input and output models), including the Ethereum mainnet and its L2s/sidechains.
The flexibility of L1 is key here, as it caters to new projects seeking native platforms with FHE capabilities, while also adapting to existing applications that are more willing to stay on the current chain.
Rollup/Application Chain: Applications can launch their own Rollup or Application Chain on top of these FHE-enabled L1s.To this end, Zama is committed to the optimistic stack of fhEVM L1 and the ZK FHE summary stack to expand privacy-focused solutions.
FHE Rollup on Ethereum: Launching FHE Rollup on Ethereum itself can significantly enhance local privacy on Ethereum, but face some technical challenges:
Data storage cost: Even if the plaintext entries are small, the FHE ciphertext data is quite large (over 8 kb each).Storing such a large amount of data on Ethereum for data availability (DA) purposes would be very expensive in terms of gas charges.
Sequencer Centralization: A centralized sequencer sorts transactions and controls global FHE keys is a major privacy and security issue that first violates the purpose of fhEVM.While MPC is a potential solution to decentralize control of global FHE keys, maintaining multi-party networks to perform computations increases operational costs and leads to potential inefficiencies.
Generating valid ZKP: Generating ZKP for FHE operations is a complex task that is still under development.While companies like Sunscreen are making progress, it may take several years for such technology to be widely used for commercial purposes.
EVM Integration: FHE operations need to be merged into EVM as precompilers, so consensus votes are required for multiple issues involving computational overhead and security issues.
Validator hardware requirements: Ethereum validators need to upgrade their hardware to run the FHE library, which raises concerns about centralization and cost.
We expect FHE to initially find its position in specific areas where less liquid environments and privacy is critical.Ultimately, deeper liquidity may occur on FHE L1 as throughput increases.In the long run, once the above problem is solved, we may see FHE rollup on Ethereum, which can make more smooth use of the mainnet’s liquidity and users.The challenge now is finding killer use cases for FHE, maintaining compliance and bringing technologies that can be put into production right away.
Meanwhile, any developer who wants to make money by hand or through bounty hunting can try Fherma’s FHE challenge and earn several 4-figure bounties.
Acknowledgements: Thank you very much to Gurgen Arakelov (founder of Yasha Labs/Fherma), Rand Hindi (founder of Zama), Remi Gai (founder of Inco Network), and Hiroki Kotabe (head of research at Inception Capital) for their contributions.








