
Suave is a decentralized project developed by Flashbots. It establishes a network with a TEE environment to solve the problem of key protection and multi -party mutual trust encountered in the MEV process.At the same time, the addition of Tee in the Suave project allows Suave to have more possibilities besides solving the MEV problem.
Suave related code library
The Suave project is based on Ethereum, so it is naturally compatible with EVM.Its related projects currently on GitHub include: Suave-Geth, Suave-Std, Suave-Examples, etc.
Among them, Suave-Geth is an extended execution layer code based on Geth. It mainly adds an encrypted computing environment on the basis of Geth, and some Precompile (pre-compilation) in the encryption computing environment.It is particularly worth mentioning that the Precompile, which adds standard HTTPS requests, allows developers to use the Tee environment to provide users with the function of accessing other networks.In addition, it contains a series of Precompiles based on Tee use functions, such as obtaining encryption parameters, storage and encryption information, and obtaining encryption information, which form a development infrastructure based on a trusted environment.
Suave-Std is a project established for developers to facilitate use, which can be understood as the development tool library.For example, it packaged how to use HTTP requests, and even packaged a code library using ChatGPT on this basis, which made developers not need to assemble the ChatGPT request message and analyze the return message of ChatGPT.Just replace your own API Key when you are a message.The TEE security environment guarantees the security of API Key because all this is carried out in the Tee environment.Initially, this ChatGPT standard library used the GPT-3.5-Turbo model by default, and the Temperator defaults to 0.7.Now adding flexible interfaces, you can also pass the models as parameters.
The Suave-EXAMPLES project is mainly to show some cases of application development, or it is more suitable for beginner tutorials.For developers who have just contacted SUAVE applications, they can learn and compare them through cases in this project.
Suave development practice
Since Suave is expanded by Ethereum (its executable environment is called MEVM, that is, the Modified Ethereum Virtual Machine), the development of smart contracts is compatible with EVM, and the official development documents are introduced by solidity.Therefore, for developers, Solidity’s development experience is completely available.In Suave application development, the development of smart contracts can be understood as Solidity development with encrypted computing functions in the Tee environment.
There are several key Suave Mevm Precompiles.The first is ConfidentialInpputs. This Precompile accepts encryption parameters from the application request. This parameter usually needs some private information that needs to be encrypted, such as private keys, API Key, etc.In the environment, in the application development, the information is obtained by this interface.Its transmission process is fully encrypted and safe and reliable, and we will talk about the principle later.The second is ConfidentialStore. Its role is to store private information. When we obtain private information from the parameters, they often do not need to participate in calculation at that time, so they are stored to prepare for subsequent use.The third is ConfidentialReTrieve. This interface is used when the TEE context is required to be requested when the private information is required to participate in the calculation.
SUAVE’s secure storage of private information allows developers to achieve such a scene: “Users upload the private key, and then the third party calculates the business. When the conditions are met, the third party can directly use the user’s private key for signature.The third party can use the user’s private key to sign the user under certain rules, but the third party cannot get the private key. “
Suave uses HTTPS request for cross -chain operations.There is a library called Gateway in the tool set to directly read cross -chain information. Its essence is that the user sets a chain RPC Node. More common is that users upload API Key information such as Infura, EtherScan, etc., and thenWhen you need to call, use the http directly to the corresponding node.When you need to make information on cross -chain, there is a transaction package in the tool set to help developers perform enabled on packets such as EIP1559, and finally trading the transaction through ETH_SENDRAWTRANSACTION interface.
Another use scenario is worth mentioning that the Bytecode compiled by Solidity is uploaded and stored and stored as a private parameter. When it meets the conditions, it is formed and called it, which forms a private library.This usage scenario can be extended to: private key + private bytecode library.In this case, when the third -party commission is called, it can achieve completely privacy transactions.
SUAVE characteristic
The final state of Suave is a chain, which we call the Suave chain.The Suave chain can regard it to achieve a chain of MEVM.Since it is an EVM compatible blockchain, then we can also build assets such as ERC20 and ERC721 on Suave. The operation on the chain is not different from the EVM series chain.However, its uniqueness is that the operation of the chain is added, such as sending transactions to the nodes of other chains. The operation result of the under -chain or the conditions of use can be stored on the Suave chain. The result of the storage is guaranteed.In this way, the consistency of the calculation and the state on the chain can be achieved.For example, developers can write a smart contract and record some conditions on the chain (can also be modified). When accessing a chain network node, the returned results meet the requirements, and the pre -set ERC20 asset transfer is performed.
The above are the characteristics of the credible computing of the Suave chain.We know that Suave was developed by the Flashbots team, and Suave was regarded by the Flashbots team as “The Future of MEV”, so the processing of Bundle’s transaction must be there. Based on the credible environment, the principle of MEV -related principles is very simple: assembly: assembly: assembly: assemblyBundle trading, sent to the Relay node of Flashbots.The private key can be stored secretly, and even the code is okay, which forms huge potential for use.For example, Builder can get some digital assets on the Suave chain in addition to the GAS reward on the target chain.For the MEV market, the business can be flexibly defined in the case of security guarantee, which is currently not available for MEV (currently only the traditional trust, contract, goodwill, etc.).
Suave development tool and infrastructure
For developers, a DAPP development, in addition to the development of smart contracts on the chain, is also an important part of tool sets such as Ether.JS in front -end development.In the development of Suave applications, because the Suave chain is based on EVM, ether.js, web3.js and other tools can also be used. These tools are not different from the smart contract interaction with the SUAVE chain and other EVM compatibility chains.But only the function of the non -Confidential environment can be called.A SUAVE chain smart contract is divided into chain (referring to the Suave chain) and under -chain (cross -chain operation is also this category) operation. The operation of the chain actually refers to the CONFIDENTIAL environment calculation.For the Confidential environment computing, the Flashbots team provides SDK (GO and TypeScript) in two languages, and the usage method is introduced in the Suave document.When sending the Flashbots team called Confidential Compute Request, it can be brought into ConfidentialInputs when the Flashbots team is called the Confidential Compute Request, which is a private parameter. This parameter will only appear in the Tee environment throughout the transmission process.
Finally, when it comes to the deployment of smart contracts, the name of the SUAVE chain test network is called regil, but now it has been upgraded to Toliman. The deployment method has been introduced in detail in the Suave document.The way of deployment, the way of deployment, etc. are not different from the deployment of the Ethereum smart contract.
Keptle
After the intelligent contract deployment, its actual operation method is different from Ethereum.One of the most important execution units of Suave is called Kettle.Kettle is the Tee operating environment of Suave (it includes a MEVM node and a Confidital Data Store).When the developer wrote a smart contract and deployed, the user sent the Confidential Compute Request (hereinafter referred to as CCR), and the smart contract needs to use the Confidential Compute, which is actually Kettle.
The composition of Kettle is as follows:
>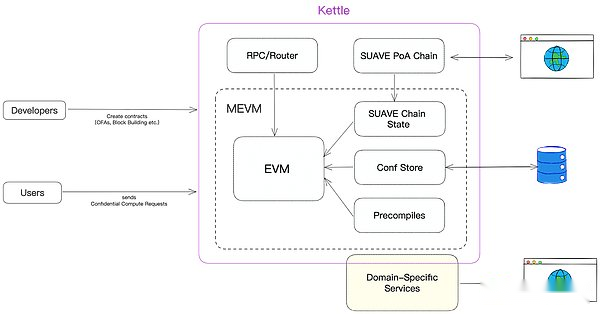
We can see that developers use Solidity language development and deployment applications. After finally requesting Kettle, they are all processed by MEVM. In addition to GetH functions in MEVM, some Precompiles can be added on it to store and retrieve private data.wait.In addition, it also processes the state on the Suave chain (including modification and retrieval).
The main work of Kettle is to receive and handle private computing, as well as handling private data storage and retrieval.Taking a private data as an example, the entire process is like this: the front end of the user uses SDK or Suave Geth tools to initiate a CCR request to a smart contract on the Suave chain.Data is encrypted. This data key will only appear in the environment of Kettle, and Suave’s RPC Node will only see cipher text.Is Kettle’s relationship with one -to -one relationship, this is not seen from the Suave document.In the same way, the detailed principles of Kettle itself, nodes, and key exchange are not introduced in the documentation.However, based on the known process of decryption, developers have reason to believe that private data can be guaranteed from the front end of the user from the front end of the user to the internal TEE environment of the Kettle.
Private data Kettle will be stored in the Confidital Data Store. When developing smart contracts, developers will specify the visitors and modifiers of the data. Kettle will publish it through its transport network.It must be sent to this Kettle, because the data storage of Kettle is not global.When the developer deploys the smart contract, the user accesses the corresponding Kettle (there is a parameter in the CCR request, which must specify the Kettle address), and its private data can be accessed.When the user sends a CCR and requests private data in a smart contract, the ID and key established when the corresponding data are stored are used to retrieve it. That is to say, the private data access is accessed and used through its key value.
Regarding HTTP requests, etc., they are also processed by Kettle.Obviously, these are jobs that belong to the Suave chain, which means that these tasks are running in a single node. Although Suave is a chain, its blockchain attributes are weak. When Kettle runs a CCR request, there will be no there will beMany nodes are running and then verified.The reason is very simple. The resources outside the chain must not guarantee that they will be equal.Therefore, these jobs that belong to the Suave chain are actually dependent nodes.Therefore, developers should pay attention to the Kettle address when deploying (this point, Kettle can be regarded as a special smart contract), follow -up user CCR requests to bring the corresponding key address.
In addition, there is a problem worthy of the attention of developers.On the current test network Toliman, Kettle does not guarantee running in the Tee environment.Therefore, when developing smart contracts on the test online, pay attention to protecting private data, and do not leak real private data.
Summarize
The Suave chain has brought enough capabilities to application development by introducing the Tee environment, and its potential application scenarios are very many.Its concise and convenient cross -chain operation also brings enough imagination to DAPP design.
The Kettle design of the Suave chain can handle the resources outside the chain, which brings the problem of verification and consensus.Disadvantages of Kettle are destroyed to the network.How to ensure that Kettle does not do evil, or do evil can be punished, or the cost of ensuring evil is high enough, which is a problem that needs to be solved.The POA mode adopted by the consensus of the Suave chain, whether it can stand the consideration of practice, is still waiting to be seen.







