Author: Wallet Source: DWALLET LABS Translation: Shan Ouba, Bitchain Vision
The zero trust architecture is a security model that needs to be continuously verified by each operation to eliminate the inherent trust, thereby achieving the safety of the entire web3 and the interaction of the machine.
Zero Trust VS Castle and Hugu River
Zero trust structure is a modern network security method that emphasizes verification of everything and dislike everything.This model ensures that each operation, access request and interaction have been thoroughly verified and authorized to eliminate inherent trust.
Castle and moat models are older network security methods.In this model, a secure boundary (moat) is established around the trusted internal network (castle).Once you enter this boundary, the entity can obtain a wide range of access permissions without further review.Although this model is effective in a relatively simple network environment, it seems unswerving when dealing with today’s complex and interconnected digital environments.The main weakness of this method is that it depends on the irreplaceability of the “moat”, and assumes that the threat is always external, ignoring the possibility of internal vulnerabilities or being stolen vouchers.
The development of zero trust is to cope with the loopholes of the castle and moat models.In zero trust, regardless of every entity inside and outside the Internet, unless it is proven to be credible, it is considered unbelievable.This means that each operation, access request and interaction must go through strict authentication and authorization.
Zero trust in Web3’s natural fit
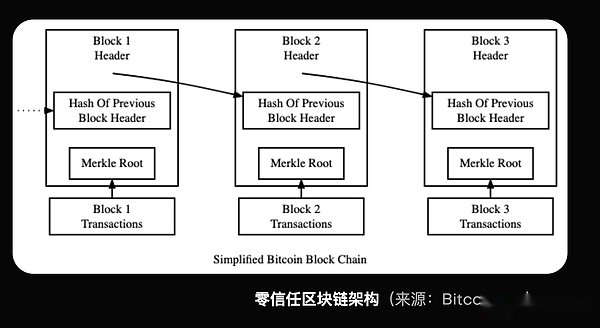
Zero trust is not new in Web3.Since the birth of Bitcoin, blockchain technology has been using zero trust methods.In the blockchain network, no entity is trusted.Instead, each user can independently verify each transaction, and ensure that the agreement is correct from beginning to end.This verification process eliminates the trust needs of any authority, including nodes that run the network.
>
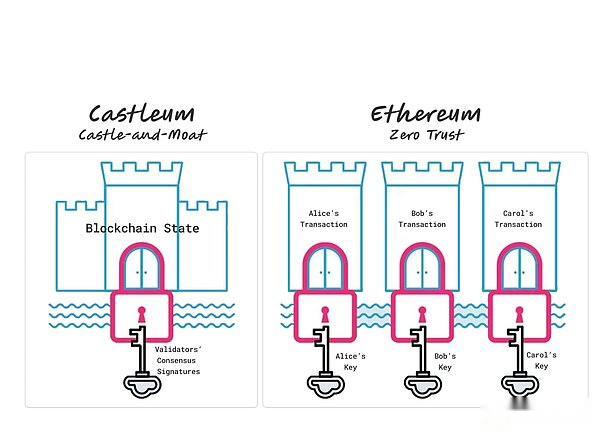
In a hypothetical scene, imagine a blockchain called Castleum, which uses a castle and moat model.Here, the verifier handles the transaction and updates the blockchain status without user verification. If the consensus mechanism is destroyed, potential loopholes will be generated.In contrast, the zero -trust architecture of Ethereum requires users to sign a transaction. The verifier will include it in the block after verifying its authenticity, and this authenticity is verified by each user.
>
Sovereign and honeypots
With the development of Web3, many blockchain networks came into being, and each network operates in its own field.Although these networks maintain zero trust within their boundaries, challenges will appear when they need interoperability between different blockchains.The traditional method of connecting these networks involves the principle of sacrificing zero trust, and returns to the castle and moat models.
The “sovereign issue” comes from the needs of connecting the independent blockchain network, and it is necessary to trust third parties to manage cross -chain interaction.This trusted entity (or entity) became a single -point failure and sacrificed the zero trust model.In addition, these solutions will become bait of attackers, called “honeypots”.The more controlled the assets, the greater the motivation for malicious actors to break through its defense.
Occible ZTPS
ZTPS (Zero Trust Agreement) is the web3 protocol using zero -trust architecture.They need to be continuously verified on each operation to ensure that no entity is inherently trusted.In an isolated network, ZTPS is the standard of Web3, maintaining a zero -trust model by ensuring that only native assets involved in the network.This means that in a single blockchain like Ethereum, it can maintain zero trust for trading of native assets involving the chain, thereby achieving “isolated ZTPS”.
Take UNISWAP as an example. This is a popular decentralized exchange on the Taifang.When users want to exchange two Ethereum native assets, such as UNI and ETH, Uniswap operates as a zero trust agreement.The agreement inherits the zero -trust architecture of Ethereum to ensure that each transaction can be verified by all users.
>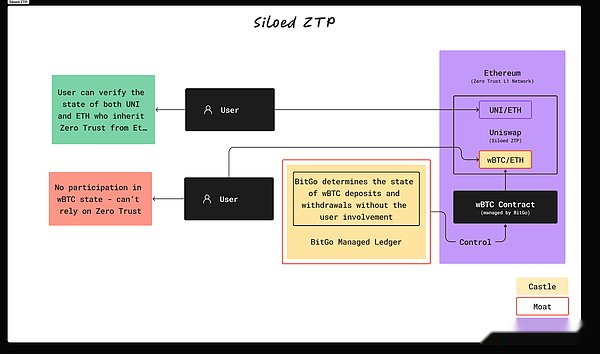
When interacting with WBTC, Siled ZTP (Uniswap) runs as CMP.WBTC/ETH is currently the largest mining pool on Uniswap.
However, if users want to exchange ETH and WBTC (Wrapped Bitcoin), the situation will change.WBTC is a BTC derivative that depends on centralized custodian (Bitgo).In this case, Uniswap lost its zero -trust nature, because WBTC’s security relies on Bitgo’s castle and moat architecture, and users need to trust Bitgo instead of independent verification transactions.This makes UNISWAP run as a castle and moat (or CMP).
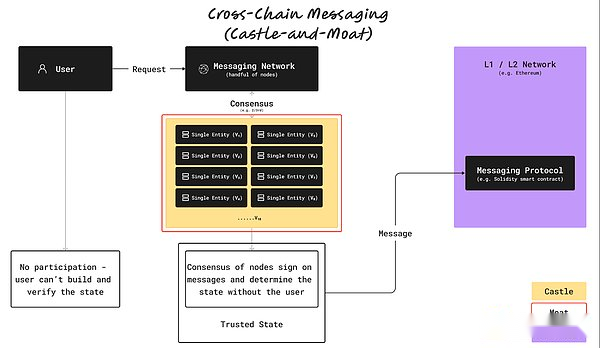
Since users cannot directly interact with other networks (such as BTC or SOL) to the UNISWAP, they must rely on derivative packaging assets that are derived from the castle and moat structure, making Uniswap a isolated ZTP.This usually includes traditional cross -chain solutions, such as bridge connection, cross -chain message transmission, and combined with MPC.
>
2PC-MPC: The future of ZTPS
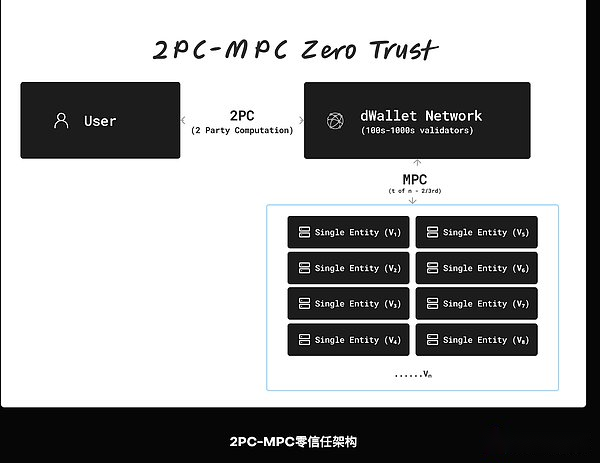
In order to create ZTPS that is not limited to its deployment network, the DWALLET network uses advanced encryption methods to maintain zero trust between different networks.The 2PC-MPC encryption protocol of the DWALLET network enables ZTPS to run in various blockchain ecosystem without compromising its zero trust principle.By encrypted, users are required to participate, Dwallet ensures that each operation is verified, and no entity is trusted.
2PC-MPC is an encrypted solution that allows the two parties (in this example for users and DWALLET networks) to generate signatures on any network, involving hundreds to thousands of decentralized nodes, forming a non-collusion and large scaleDecentralized system.The participation of users ensures zero trust, and the participation of the Dwallet network has created the infrastructure of ZTPS through the agreement through the agreement.
>
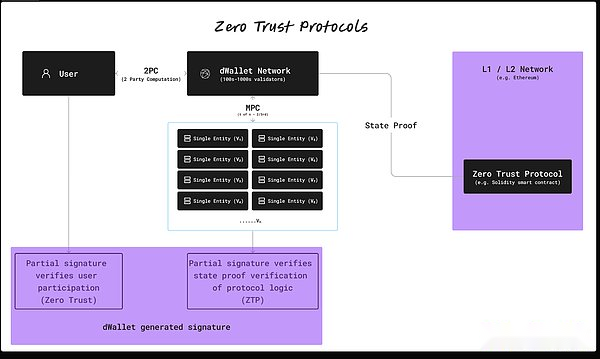
The working principle of ZTPS
-
User and Internet participation: Any transaction or operation must be verified, and the user and the DWALLET network must be involved.The participation of users is essential for the necessary encryption signature.
-
Decentralized verification: DWALLET network consists of a large number of nodes to jointly verify the user input and transaction details.This decentralized verification process ensures that no single entity can control or manipulate transactions.
-
Cross -chain interaction: ZTPS allows security interaction between different blockchain networks.For example, users can interact with assets on Ethereum and Bitcoin without compromising zero trust models.The DWALLET network ensures that all operations are verified and certified between these networks.
>
The actual application of ZTPS
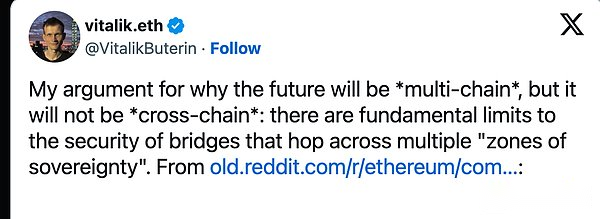
Vitalik Buterin has expressed doubts about cross -chain applications, mainly due to the inherent security restrictions in the bridge between blockchain, especially in the face of 51%attack on the weak security chain, emphasizing these connections, emphasizing these connections.The risks of the castle and moat structures, especially when facing 51%attack, endanger the native assets on the chain with strong security.
>
ZTPS is necessary for a multi -chain world that does not rely on the castle and moat architecture.Provide decentralized hosting, multi -chain DEFI and non -hosting wallet solutions.
in conclusion
The Zero Trust Agreement (ZTPS) is critical to maintaining the security and integrity of the multi -chain Web3.By being required to continue verifying and eliminating inherent trust, ZTPS ensures that interaction between different blockchain networks is safe and tough.It is possible to make the security interaction across any blockchain and pave the way for innovative decentralized applications.
As we continue to explore the potential of blockchain technology, hugging the zero -trust principle through ZTPS will be essential to build a safe and interactive Web3 ecosystem.