
Author: shew & amp; faust, Geek web3, consultant: kevin he, bitvm Chinese community sponsor, ex web3 tech head@huobi
The current Bitcoin Layer2 track can be described as full of flowers, and various technical solutions have gathered in the BTC ecological melting furnace.Due to the fast iterations in the blockchain field, professional vocabulary or standards are constantly changing during research innovation and engineering landing.In this context, many projects will obtain differentiation and attention in the way many projects will use the “concept”/”concept of concept”, which has become the industry’s hidden rules.
For example, many modular blockchain projects that were originally active in Ethereum/CELESTIA ecosystem also took the Dongfeng to take the “Bitcoin Layer2” express, and they were self -proclaimed as “RollUP”, but their technical solutions often do not often doMet the standards of rollup.
However, vocabulary such as “Rollup” is highly recognized, and it is more conducive to publicity under the banner of “Rollup”.Many project parties are either stubborn (self -named Rollup) or the concept of rollUp, the mainstream of the fork (plus an ambiguous attribution, such as sovereign Rollup).
But at a glance, the work principle of many projects is still simply “client verification” or “side chain”, but it is only convenient to be convenient to themselves through the slogan of “XX Rollup”.Although this propaganda method is relatively common, it is often misleading. For the general public who pursue the truth, the disadvantages bring more.
(The Nazi Propaganda Minister Gobel’s summary of “lying propaganda”, which is common in many project parties)
So how can we identify the behavior of this kind of “rolup concept”?
Perhaps, starting from the principles of firstality, according to the widely recognized standards of the West and the industry, to define the scheme category and security level of different Layer2 projects, and functional completeness, so that we can open the pairs of “kaleidoscope writing in the fog to watch flowers in the fog.Wheel eyes.In other words, what kind of solution is not the most important. The core is whether the project can ensure whether Layer2 network security is reliable, and whether it can really empower the BTC main network.

Below, we plan to use the Bitcoin Layer2 made by the foreigner of Chainway as the case to analyze the “client verification” hidden in the “Rollup” promotional slogan.We can see more clearly, “sovereign rollup” and “client verification”, with the significantly different differences between the Rollup schemes such as smart contract implementation in the mainstream of the industry, or OPROLLUP.
Of course, this is not to say that sovereign Rollup or client verification is not as safe and reliable as ZK Rollup. Everything depends on its specific details.Although Chainway is a typical client verification Layer2, it proposes a anti -review transaction solution “in BTC trigger+verification under the chain”, and uses recursive ZK Proof similar to the MINA public chain, leading most Bitcoin Layer2Essence
We believe that the technical research on Chainway is relatively valuable, which is of important reference significance for the majority of Bitcoin Layer2 observer.

(Chainway’s promotional pictures are advertised as ZK Rollup, but its real solution is the client verification. At present, it has not yet realized the consensus between the client under the chain, or the reliable information exchange)
text:Chainway is a well -known Bitcoin Layer2 project in the Western community. Many KOLs directly call it “ZK Rollup” when promotingIn its technical documents, Chainway is also self -positioning as “sovereign rollup”.Recently, CHAINWAY also announced its new project Citrea, claiming to be Bitvm -based ZK Rollup.Since Citrea has not explained in detail how it is realized by Bitvm -based ZK verification scheme,This article will focus on the technical interpretation of the already planned solution.
We can summarize in one sentenceChainway’s currently disclosed technical solution: DA data is published through the Ordinals protocol,Use BTC as its DA layer,ZK Proof, which is state Diff + in LAYER1 for details of changing status changes.Equivalent on the release of complete, verified transaction data.
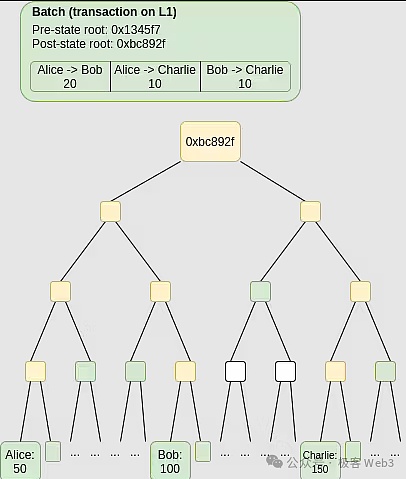
(State Diff is the change in account status)
However, because Layer1 does not directly verify the ZK Proof, the verification work is performed by the independent client/node under the chain, andChainway’s current code library has not achieved consensus between independent clients under the chain, and officials have not declared this problem on social media.Therefore, the current technical solution announced by Chainway is essentiallybelong“Client verification”Types, even more like an inscription index protocol that supports bridge assets.
The following will mainly introduce the specific technical implementation of Chainway and analyze its security model.
What is sovereignty Rollup: DA layer releases data + under -chain verification
In Chainway’s technical documents, Celestia’s sovereign Rollup (Sovereign Rollup) concept was used.andThe sovereign ROLLUP is actually different from the Ethereum community and even the industry’s mainstream Rollup concept (smart contract ROLLUP).EssenceSo what is the specific structure of sovereign Rollup?
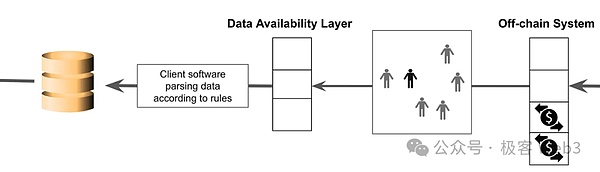
actuallyBitcoin -based sovereign Rollup is a bit similar to- “” Client group/side chain under the chain of DA data on the BTC chain “,The biggest feature is that the intelligent contract on Layer1 is required to verify the status conversion/cross -chain behavior of Layer2. In essence, the BTC is used as the DA layer. The security model and the “client size value” are largely large extent.near.
certainly,Some highly secure sovereign Rollup solutions will rely on the third -party settlement layer (similar to the side chain) under the BTC chain to complete the status conversion verification.And between different independent clients/full nodes, there is a layer of consensus or reliable message transmission, so as to achieve “consistency” to certain controversial behaviors.butSome sovereignty Rollup projects are naked “client verification”, and there is no reliable message transmission between independent client/nodes.
In order to better understand the unique concept of “sovereign rollup”,We can compare sovereignty Rollup with its corresponding smart contract ROLLUP.Layer2 on Ethereum is basically smart contract Rollup, such as Arbitrum and Starknet.The structure of the smart contract ROLLUP can refer to the figure below:
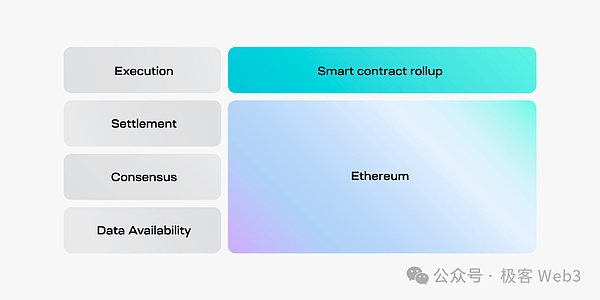
In the figure above, we can see several terms of modular blockchain narrative, as follows:
Execution execution layer:Execute user transactions, update the status of the blockchain, and submit data to the DA layer and the settlement layer
Settlement settlement layer:Verify the state conversion of the execution layer, solve disputes (such as fraud proof), and provide bridge modules to handle L1-L2 bridge receiving assets
DA layer:A large announcement board, receiving the status conversion data submitted by the execution layer, and providing this data to the trust to anyone
Consensus consensus layer:To ensure the final nature of transaction sorting, it seems to be closer to the function of the DA layer (the layered method of the Ethereum community on the modular blockchain does not include the consensus layer)
From the architecture of the smart contract Rollup, we see that except for the execution layer, the functions of the other three layers are borne by Ethereum.The figure below shows the role of Ethereum in the smart contract ROLLUP.
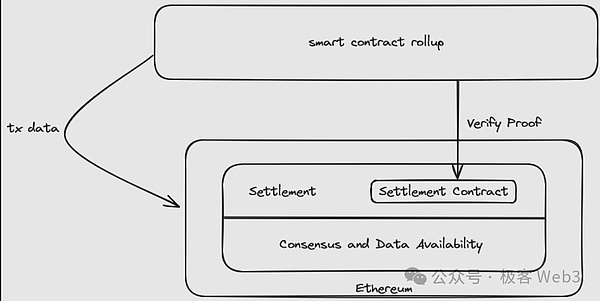
Rollup contracts on Ethereum will receive Validity Proof (validity proof) or Fraud Proof to verify the effectiveness of Layer2 status conversion.It is worth mentioning that the Rollup smart contract here is actually a settlement layer entity in the modular blockchain.The settlement layer contract often contains the bridge connection module to process the Ethereum bridge to receive the assets of Layer2.
For DA, the settlement layer contract can force the sorter Sequencer to put the latest transaction data/status change details on the chain. If the DA is not on the chain, the L2 state recorded on the Rollup contract can not be updated smoothly.
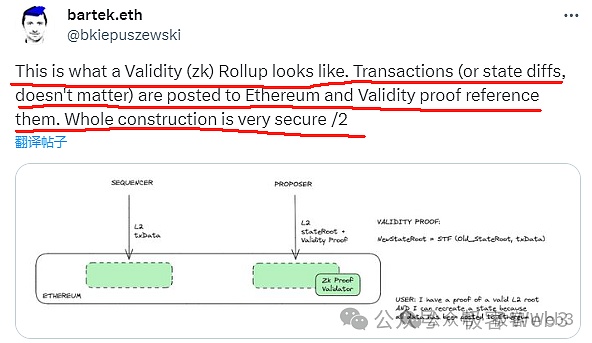
(ZK RollUp or OP Rollup, you can mandate DA data on the chain, and you cannot update the status of the settlement of the settlement layer)
We can see,Smart contract ROLLUP seriously relies on smart contracts on Layer1.For Layer1, which is difficult to support complex business logic, it is basically impossible to construct LAYER2, which is “aligned” to Rollup in Ethereum.
andThe sovereign ROLLUP scheme simply does not require the contract on Layer1 for status verification/bridge processing.The architecture is as follows:
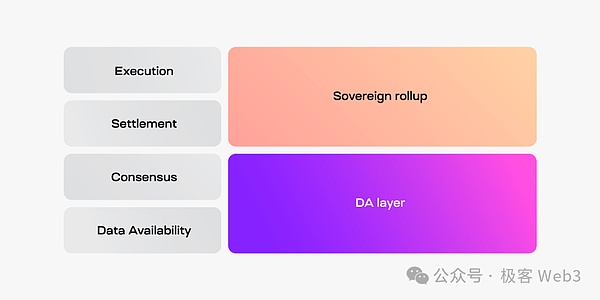
We can see,In the sovereign Rollup, node groups outside the DA layer as entities for transaction execution and settlement operations have higher degree of freedom.The specific workflow is as follows:
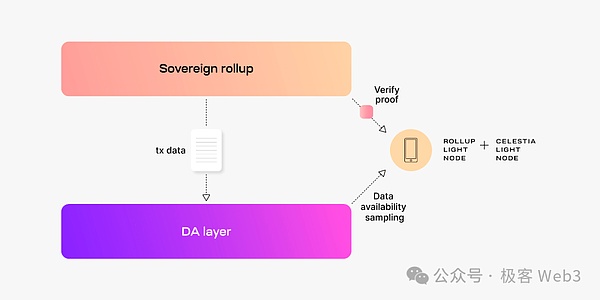
The execution layer node of the sovereign ROLLUP sends the details of transaction data/status change to the DA layer, and the settlement layer/client method is set to obtain data and verified.It is worth noting,Since the settlement layer module is not located on Layer1, the sovereign ROLLUP is theoretically unable to achieve a bridge that is equivalent to Layer1.It often depends on the notary bridge, or a third -party bridge.
At present, the sovereign Rollup/client verification scheme is less difficult to land. It only needs to implement data release on the BTC chain and adopt a form similar to the Ordinals protocol.As for the parts under the chain and the consensus under the chain, there is a lot of space for free.Even many side chains only need to publish DA data on the BTC, which basically become “BTC -based sovereign ROLLUP”, but specific security is doubtful.
But the problem is,Bitcoin’s data throughput is extremely low,The maximum 4MB per block, the average output time is 10 minutes, and the data throughput is only 6kb/s.Now the Layer2 solution that claims to be sovereignty Rollup may not be published on the BTC chain, and then adopt other compromises.: For example, publish DA data under the chain and store Datahash on the BTC chain as a “commitment”.Or find a way to compress DA data high (such as the State Diff+ZK Proof) claiming to be used by Chainway.
But obviously this model does not conform to the definition of “sovereign Rollup” or the definition of serious Rollup. It belongs to a variant, and its safety is open to question.We predict that in the future, most of the Layer2 project under the banner of “Rollup” will eventually be fully published on the BTC chain.Therefore, the practical solutions are “ZK ROLLUP” and “OP ROLLUP” on the white paper and the slogan of “ZK ROLLUP” and “OP Rollup” on the white paper.

Finally, let’s simply summarize the difference between sovereign Rollup and smart contract ROLLUP:
First, it can be upgraded.The update iterative iteration of smart contract ROLLUP involves the UPDATE of smart contracts, and the development team needs to use upgraded contracts.The upgrade permissions of this smart contract are generally controlled by the Rollup development team.The upgrade rules of sovereign ROLLUP are similar to the soft and hard fork of conventional blockchain. The node can choose to update the version by itself, and different clients can choose whether to accept the upgrade.From this point of view, sovereign rollup is superior to smart contract ROLLUP.
Second, bridge.The bridge of the smart contract ROLLUP is minimized under the ideal conditions, but the upgrades of the contract can affect its security.andUnder the sovereign ROLLUP scheme, the developer needs to construct a bridge to connect the component under the Layer1 chain. The constructed bridges will not be trusted like a smart contract bridge.
BTC DA structure
In the above, we mentioned it,To achieve BTC -based sovereign Rollup, the core is to use the Ordinals protocol to use the BTC as the DA layer.Chainway uses this solution.
We can observe a DA data submission from the chainway sorter. The trading hash is:
24ADD7CDCBFFCDA8D43509C8E27C5A72F4DF1731BE84BDBA727CD83AE0000,,The schematic diagram is as follows:
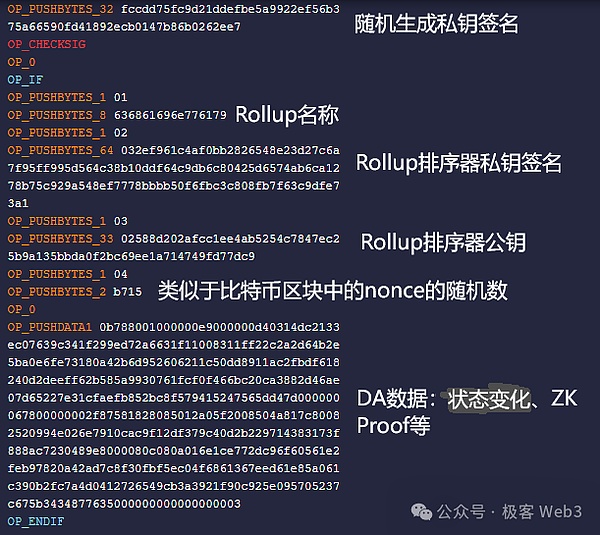
The script code of this transaction borrowed from the OP_0 OP_IF in Ordinals Protocol to implement data writing schemes, and write Rollup’s DA data into the BTC chain(Release status change+ZK PROOF, which is equal to the release of original transaction data in security, but the data size can be greatly compressed).
Of course, in addition to DA data, the sorter also writes some authority data in the transaction. The most important thing is that the Rollup sorter uses its own private key to sign the DA data to ensure that the DA data is submitted by the sorter is submitted by the sorter.Essence
We should pay attention here,In any transaction involving DA data, there are 16 binary 0 (that is, 0 consecutive bytes are 0 consecutive bytes).In the code, we can see this limit:
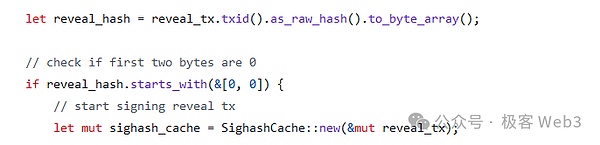
The random number B715 in the previous sample trading diagram is to adjust the value after the transaction takes the Hash, so that the tail is carried with specific 16 0, which makes a random number NONCE similar to Bitcoin mining, so that soThe front n bits of Hash are 0, which meets specific restrictions.
This design is to simplify the difficulty of obtaining DA data.When Layer2 is required to obtain DA data, just scan the BTC block, all the end set to 16 0 transactions,It is equivalent to the transaction initiated when the data sorter is submitted to the data, which is clearly distinguished from other transactions on the Bitcoin chain.In the later article, it is said that this contains DA data andThe transaction with 16 0 0 at the end is “CHainway standard trading.
Then the key points mentioned in the title of this article:How does Chainway achieve anti -censorship?Because the Layer2 sorter may deliberately reject a user’s transaction request, we must use a special solution to allow users to initiate anti -censorship transactions.
Faced with this problem, Chainway allows users to initiate“Mandatory transaction”, Forced Transaction.Once the user submits this transaction statement in the BTC block, the CHAINWAY sorter must handle the transaction request in Layer2, otherwise it will not be able to be out normally, or the block will not be recognized by the linked client.
The parameter structure of the mandatory transaction is as follows:
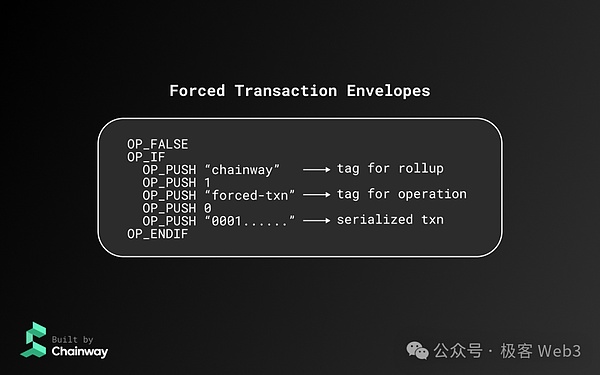
The transaction will be submitted to the Bitcoin chain as a “CHAINWAY standard transaction”, and 16 0 0 at the end of the trading hash.When the Chainway sorter generates the L2 block,The “Layer2 specification transaction” that has been disclosed on the BTC chain but not included in the L2 ledger,And the summary of a Merkle Tree writes its Merkle Root into the L2 block head.
Once the user directly initiates mandatory transactions on the BTC chain, the sorter must be processed, otherwise the next effective block cannot be generated.The Chainway client under the BTC chain can check the ZK proof first, determine the effectiveness of the L2 block submitted by the sorter, and check the Merkle ROOT at the L2 block head to determine whether the sorter contains the compulsory transaction request.
Its workflow can refer to the following flow chart.Note that, limited to space, in the figure below, Verify_relevant_tx_list lacks a conditional judgment:
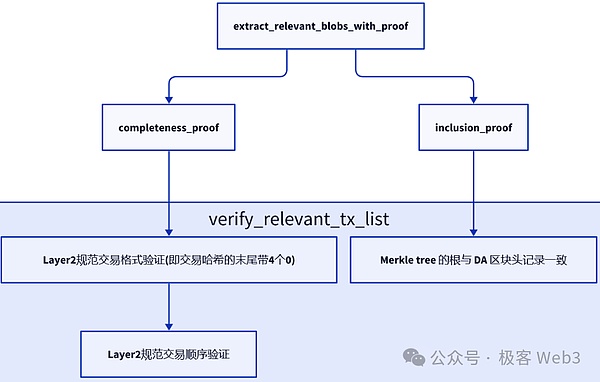
All in all, the Chainway client/node will synchronize the BTC main network block, and from it to scan the “DA data” released by the chainway sorter, confirm that the data is published by the specified sorter, and it does contain all submitted BTCs submitted to BTC”Chainway Standard Trading” on the chain.
It is not difficult to see,As long as the user can construct a “standard transaction” that meets the conditions and submits it to the BTC chain, this transaction will eventually be included in the local L2 ledger in the Chainway client, otherwise the L2 BLOCK released by the chainway sorter will be will be willClient refuses.
If it is reliableConsensus/alert message transmission under the chain,CHAINWAY’s anti -review transaction solution is approaching the ideal anti -review method of the ideal sovereign Rollup.For example, some sovereign Rollup schemes have clearly stated that encountering invalid blocks will broadcast Alert alert information between clients under the chain to enhance security. In particular, the light client that cannot synchronize the complete DA data also knows that the network status is abnormal.
If a block does not truthfully contain “mandatory transactions”, it will obviously trigger a warning broadcast under the chain.But now chainway has not yet achieved this piece(At least the current information and code library shows that it has not done this technology).
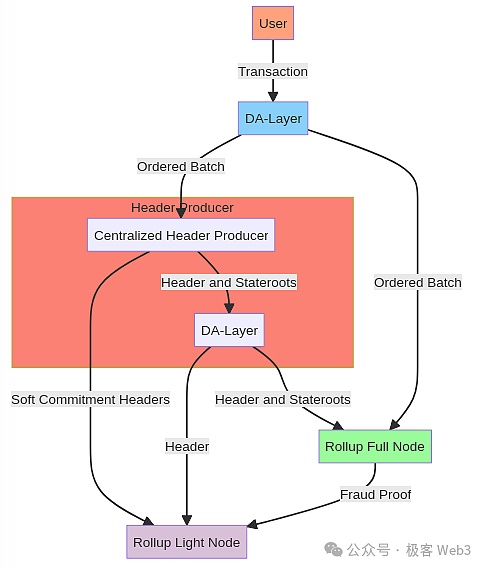
Even if the consensus between the client/node under the chain is implemented,The anti -review effect of the “compulsory transaction” of the “compulsory transaction” is not as good as the smart contract such as Arbitrum, because the Arbitrum One will eventually ensure that the “mandatory transaction” is included in the Layer2 ledger through the contract on Layer1, which fully inherits the resistance of Layer1.Obviously, sovereign ROLLUP cannot be aligned with the smart contract ROLLUP, and its anti -review finally depends on the bottom part.
This is also determined,The idea of ”sovereign rollup” and “client verification” scheme,BasicUnable toLike Arbitrum One or Loopring, DYDX and Degate,wholeInheriting Layer1’s anti -examination, because the mandatory transaction can be successfully included in the Layer2 ledger, it depends on the decision -making of the Layer2 -chain entities, which has nothing to do with Layer1 itself.
Obviously,ChainwayThis solution that is simply dependent on the client under the chain,It just inherited Layer1’s DA reliability and did not fully inherit its resistance.
Similar to MINA’s recursive ZK proof
In this section, we will further introduce other parts of the chainway. In addition to using BTC as the DA layer, it also achieves itSimilar to MINA’s recursive ZK proofEssenceThe overall structure is as follows:
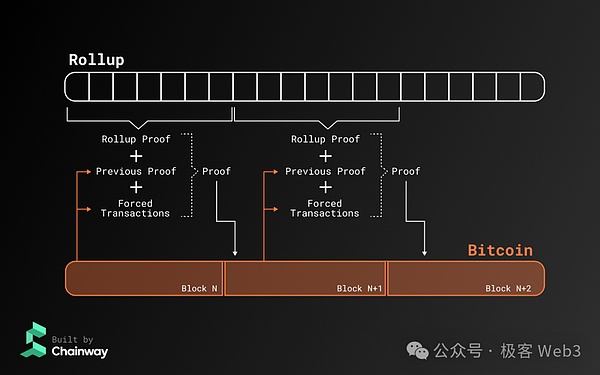
After processing the user transaction, the sorter of the CHAINWAY network generates the final ZK proof, and the state changes with different accounts are state Diff and published on the BTC chain.The whole node will synchronize all historical data released on the BTC.Each ZK proof must not only prove the status conversion process of the current block, but also ensure that the ZK certificate of the previous block is effective.
Based on the above plan, we can find that each new proof is generated. In fact, the previous proof was confirmed and recursive in order.The latest ZK certificate can ensure that all ZK certificates starting from the creation block are effective.This design is similar to MINA.
When a “light client” that only synchronizes the block head, that is, the light node is added to the network,Only the latest ZK Proof that is valid for the latest ZK Proof on the BTC can confirm the historical data of the entire chain and all status conversion.
If the sorter is evil, deliberately does not accept mandatory transactions, or does not use the previous ZK certification for recursive proof, the new ZK proof generated by it cannot be accepted by the client (generated or recognized), as shown below:
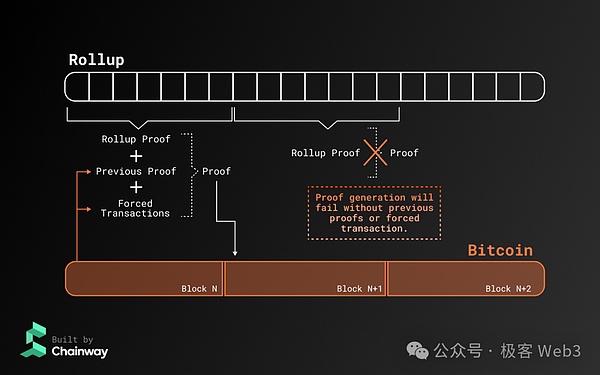
Summarize
As the summary of this article,Chainway is essentially a sovereign Rollup/client verification scheme using BTC as a DA layer.In order to improve Rollup’s anti -examination, Chainway introduced the concept of mandatory transactions.On the other hand, Chainway uses recursive ZK proof technology, so that the newly entered nodes can more trust the output of the sorter, and confirm that the entire chain’s historical data is correct at any time.
The current question of Chainway is how to trust the cross -chain bridge part,Because it adopts the sovereign ROLLUP scheme, it is not explained that on the cross -chain bridge scheme, it is difficult to judge how its final security is planned to solve the technical details.
today,Through in -depth analysis of the technical solution of Chainway, we found that the technical types promoted by the project community are not Rollup in the mainstream sense.Considering that the current Bitcoin LAYER2 project has reached dozens of (hundreds of years in half a year), in order to reduce the cognitive cost of everyone’s technical term, we will continue to classify the classification and security standards and functional assessment standards of Layer2 solutions, security standards, and functional complete evaluation standardsIn -depth research, so stay tuned!







