
Author of this chapter: Beosin Research Team Eaton
1. A summary of the security trend of Web3 blockchain in the first half of 2024
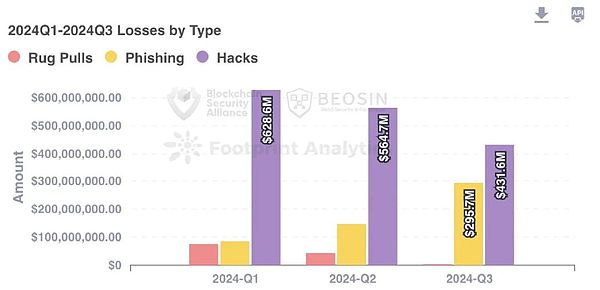
According to Beosin Alert monitoring and early warning,Q3 2024 The total losses caused by hackers, phishing scams and project party Rug Pull have reached$730 million.Among them, there were 23 major attacks, with a total loss of about US$430 million; there were 3 Rug Pull incidents, with a total loss of about US$4.24 million; and the total loss of phishing fraud was about US$295 million.

The losses caused by phishing in Q3 2024 increased significantly, and the attack continued to decline in the first half of the year compared with Rug Pull.
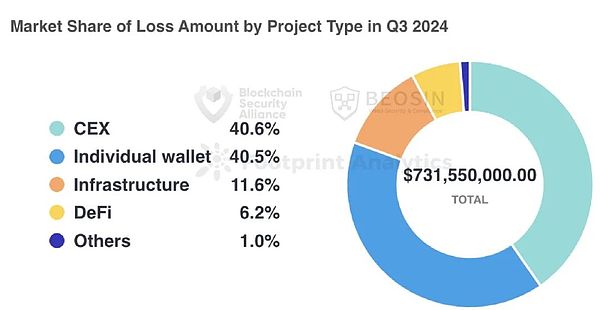
Judging from the types of attacked projects, the type of project with the highest losses is CEX. Three attacks against CEX caused a total loss of approximately US$297 million, accounting for about 40.6% of all attacks.
Judging from the loss amount of each chain, Ethereum is still the chain with the highest loss amount and the most attacks.The 21 attacks and phishing incidents on Ethereum caused $348 million in losses, accounting for about 47.6% of the total losses.
Judging from the attack methods, there were 5 private key leakage incidents in Q3, causing losses of US$305 million, accounting for about 41.7% of the total attack loss, which is the highest proportion of attack type.
Judging from the flow of funds, only about $16.9 million of the stolen funds were frozen or recovered.The vast majority (about 78.9%) of the stolen funds are still stored in the attack
on-chain address of the person.
Judging from the audit situation, among the attacked projects, the proportion of audited projects has increased.
2. Types of attacked items
CEX is the type of item with the highest loss
In Q3 2024, the project type with the highest losses was CEX, and three attacks against CEX caused a total of approximately US$297 million in losses, accounting for 40.6% of all attack losses.Although the number of CEX security incidents is not many, the amount of money is stolen every time is huge, highlighting the current security situation of the exchange ecosystem is not optimistic.
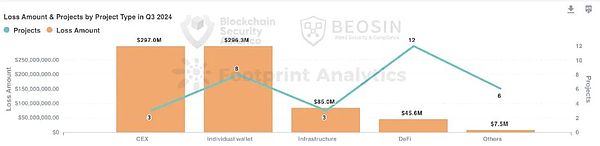
The victim type that follows the second place in the loss is the user wallet.Eight phishing and social engineering attacks on user wallets caused approximately US$295 million in losses to ordinary users, accounting for about 40.3%.Compared with the first half of 2024, the attacks and losses caused by Q3 against ordinary users have increased significantly.
Among the 23 hacking incidents, a total of 12 incidents occurred in the DeFi field, accounting for about 52.1%, making it the type of project with the most attacks. These 12 DeFi attacks caused a total of more than US$45.6 million in losses, ranking among all projects.The fourth place in the type.
Other types of projects that are attacked include: infrastructure, tokens, etc.Among them, the amount of losses caused by attacks on public chains and cross-chain bridges reached US$85 million, ranking third among all project types.
3. Loss amount of each chain
Ethereum is the chain with the highest loss and the most attacksSimilar to the first half of 2024, in Q3, Ethereum is still the public chain with the highest loss.21 attacks and phishing incidents on Ethereum caused $348 million in losses, accounting for 47.6% of the total losses.
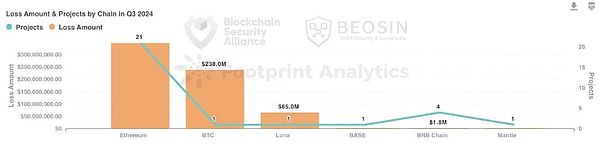
The public chain with the second largest loss amount is BTC, with a total loss of US$238 million, accounting for about 32.5% of the total loss.The amount of BTC lost comes from a social engineering attack on a giant whale address.
The third-ranked public chain for the loss is Luna ($65 million), and the attacker exploited a reentry vulnerability in the ibc-hooks timeout callback to attack Luna.
According to the number of security incidents, the top two are Ethereum (21 times) and BNB Chain (4 times).The number of security incidents in each chain ecosystem has decreased compared with the first half of the year.
4. Analysis of attack methods
About 41.7% of the loss comes from private key leakage incidents
In Q3 2024, there were 5 private key leakage incidents, causing losses of US$305 million, accounting for about 41.7% of the total attack losses.Like in the first half of the year, the losses caused by the private key leakage incident are still the first among all types of attacks.Private key leakage incidents that caused major losses include: WazirX (US$230 million), BingX (US$45 million), and Indodax (US$22 million).
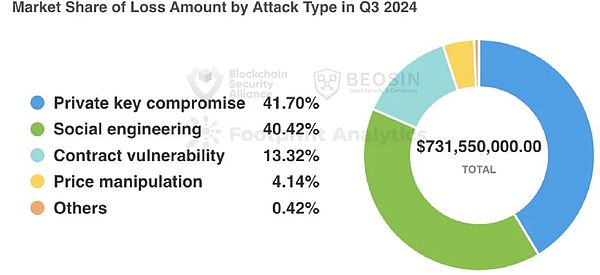
The second-ranked attack method is a social engineering attack, with one social engineering attack causing a loss of US$238 million.
Among the 23 attacks, 18 of them were exploited from contract vulnerabilities, accounting for about 78%.The total loss of contract exploitation reached US$128 million, ranking third.
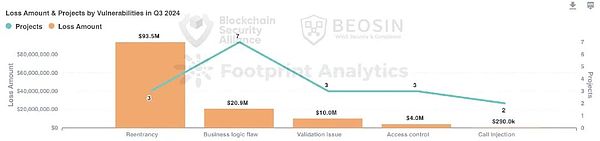
According to the vulnerability segmentation, the top three vulnerabilities that caused losses are: reentry vulnerabilities (US$93.46 million), business logic vulnerabilities (about US$2.09 million), and verification vulnerabilities (US$10.01 million).The most common vulnerability is a business logic vulnerability, and 7 of the 18 contract vulnerability attacks were business logic vulnerabilities.
5. Review of typical anti-money laundering events
5.1 Beosin Trace Tracks and Analysis of LI.FI Events
On July 16, according to Beosin Alert surveillance, it was discovered that the cross-chain protocol LI.FI was attacked. The attacker used the call injection vulnerability in the project contract to steal user assets authorized to the contract.
There is a depositToGasZipERC20 function in the LI.FI project contract, which can convert the specified token into platform coins and deposit it into the GasZip contract. However, the code at the redemption logic does not restrict the data called, resulting in an attacker using this function to call.Inject an attack and extract assets to the contract authorized users.
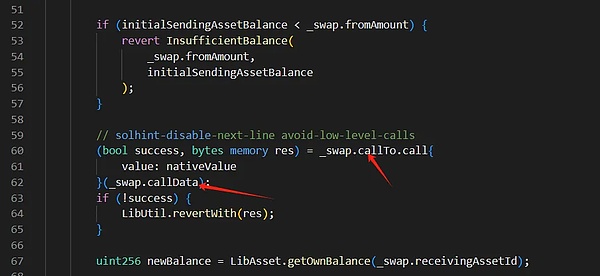
In addition to the contract vulnerability in the call, this incident has another noteworthy point, namely the configuration problem of Facet contract in Diamond mode.Further analysis found that the GasZipFacet contract was deployed 5 days before the attack and registered by the project’s multi-signed administrator on the LI.FI main contract more than ten hours before the attack.
Therefore, through this incident, we can find that the security of new functional contracts needs to be paid close attention to the upgradeable modes such as Diamond.
Beosin Trace tracked the stolen funds and found that the losses included USDT 6.3359 million, USD 3.1919 million, USD 169,500 DAI, about USD 10 million.
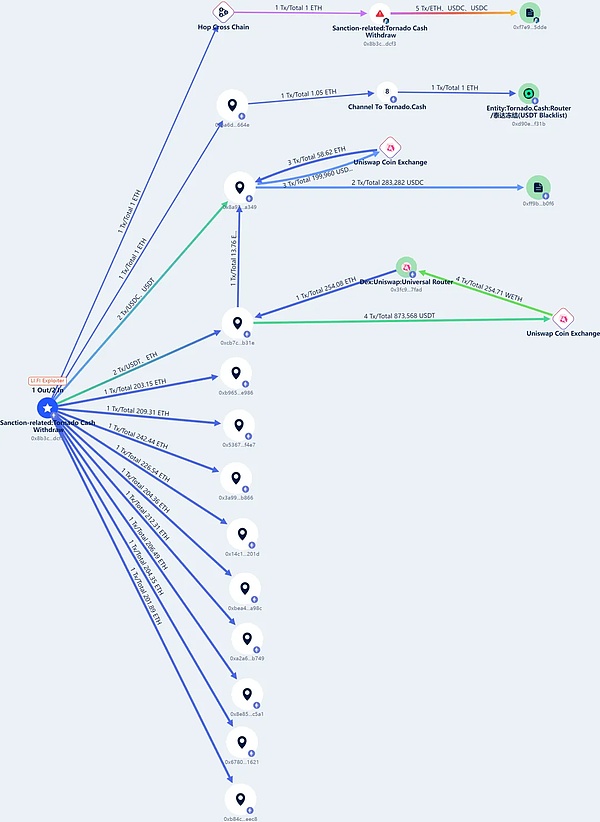 Beosin Trace: The flow of stolen funds
Beosin Trace: The flow of stolen funds
5.2 Analysis of the stolen US$235 million event on Indian exchange WazirX
On July 18, according to Beosin Alert surveillance warning, it was discovered that the Indian exchange WazirX was attacked. The attacker obtained the signature data of the exchange’s multiple signing wallet administrator, modified the wallet’s logical contract, and let the wallet execute the wrong logic to steal assets., involving more than US$230 million.
Beosin Trace tracks the stolen funds, and the streamlined chart of the stolen funds. At present, the hacker has transferred some funds to the Changenow and Binance exchanges, among which 0xf92949ab576ac2f8dc9e4650e73db083f1f9cd9f is the hacker’s coin recharge address in Binance.
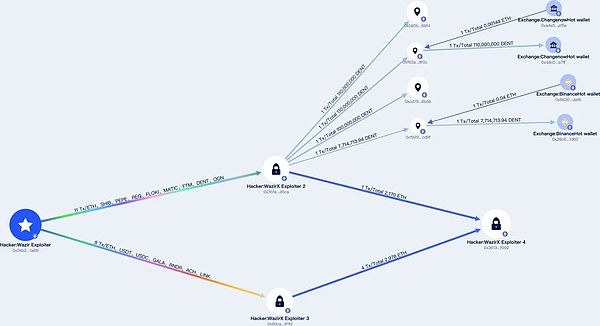
Beosin Trace: The flow chart of stolen funds
On the other hand, the hacker transferred 801 billion SHIBs to the address 0x35fe…745CA, worth up to US$14.02 million, and sold them in batches.
6. Analysis of the flow of funds of stolen assets
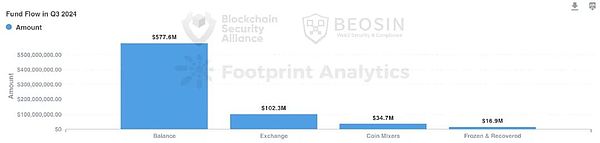
According to analysis by Beosin KYT anti-money laundering platform, only US$16.9 million of the stolen funds were frozen or recovered in Q3 2024.This proportion has dropped significantly compared with the first half of the year.
About $577 million (about 78.9%) of the stolen funds remain at the hacker’s address.As global regulators increase their anti-money laundering efforts, it becomes more difficult for hackers to clean up stolen money, so a considerable number of hackers choose to temporarily retain the stolen funds at the on-chain address.
About US$102 million of stolen funds have been transferred to various exchanges, accounting for about 13.9%, which is higher than in the first half of 2024.
A total of US$34.713 million (5.4%) were transferred to the currency mixer.Compared with the first half of the year, the stolen funds that were cleaned through the coin mixer in Q3 2024 have been significantly reduced again.
7. Analysis of project audit situation
The proportion of audited project parties has increased
In Q3 2024, among the 23 attacks, the project parties in 4 incidents were not audited, and the project parties in 16 incidents were audited.The proportion of audited project parties is higher than in the first half of the year, which shows that the overall Web3 industry project parties have increased their importance to security.
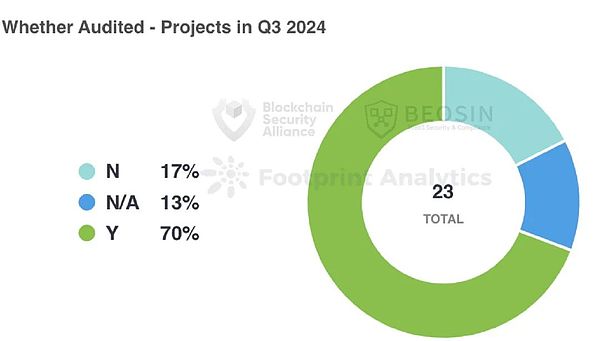
Among the 4 unaudited projects, contract vulnerabilities accounted for 3 (75%).Among the 16 audited projects, contract vulnerabilities accounted for 11 (68.75%).The overall proportion of the two is roughly the same.Compared with the first half of the year, the overall safety audit quality declined in 2024.
8. Summary of the security trend of Web3 blockchain in the first half of 2024
Compared with the same period in 2023, the total losses caused by hacker attacks, phishing scams, and project party Rug Pull fell slightly in Q3 2024, reaching US$730 million (the figure was US$889 million in Q3 2023).Factors such as the decline in the price of currency in Q3 in 2024 have a certain impact on the reduction of the total amount, but overall, the situation in the Web3 security field is still not optimistic.
Like the first half of the year, the type of attack that caused the most harm in Q3 of 2024 is still private key leakage.About 41.7% of the loss comes from private key leakage incidents.From the perspective of project types, private key leakage incidents are spread across all areas of Web3: game platforms, token contracts, personal wallets, infrastructure, exchanges, etc.All Web3 project parties/individual users need to be vigilant, store private keys offline, use multiple signatures, use third-party services carefully, and provide regular security training for privileged employees.
In Q3, only 5.4% of the stolen assets were transferred to various coin mixers, and another 78.9% of the assets were still retained at the hacker’s address, which further illustrates the increasing difficulty of hackers in cleaning up stolen money.
In Q3, 13.9% of the stolen funds were still transferred to various exchanges, which required the exchange to identify hacking behavior in a timely manner and actively cooperate with law enforcement agencies and project parties to freeze funds and conduct certification adjustments.At present, the cooperation between the exchange and law enforcement agencies, project parties, and security teams has achieved relatively obvious results. I believe that more stolen funds will be recovered in the future.
Among the 23 attacks in Q3, 18 of them were still exploited by contract vulnerabilities. It is recommended that the project party seek professional security companies for auditing before going online.








