
Source: Dengchain Community
In today’s article, we will look at solidityeventIt is called in more common Ethereum and EVMLOGSEssenceWe will see how to use them, their definitions, how to use the theme of the event and the signature to filter the log, and some suggestions on when.
We will also cover inspection-event-The interaction mode, this famous model is traditionally applied to the re -income of state variables, but we will see why this model should also be applied to trigger events and potential risks and security vulnerabilities involved.
How to define events in solidity?
Be availableeventThe keyword defines the event in Solidity, as shown below.
interface ilight {
event switchedon ();
Event switchedoff ();
Event Bulbreplaced ();
You can pass the name of the contract through a complete limited access, followed by followThen, thenTo access the event from another contract with the event name, as shown below:
Event dressUser)
The event signature is:
Event dressUser)
The theme of the event is:
bytes32 Topichash = uccessFully.selector;
Please note that only after Solidity V0.8.15, the incident will.selectorMembers can use it.
If you check any blockchain log, you will find the index of the theme of the log0(The first) The purpose corresponds to the theme of the event.Since the theme is the content that can be searched through a log, we canFilter with the theme of the event:
-
Search for specific events in the smart contract of a specific address.
-
Search for specific events in all contracts on the blockchain.
We will see it further below,
anonymousAnonymous event is the exception of this rule.anonymousKeywords make them unable to search, so use the term“anonymous”Essence
Based on this fact, we can also infer that the simplest event defined in Solidity has no parameters, such as the event defined aboveBulbreplacedorSwitchedon, Will be used at the bottomLog1The operating code trigger the theme in the log because the incident itself is searchable.
You can add more themes, other themes will be usedLog2,,Log3,,Log4andLog5As long as these parameters are marked asindexedEssenceLet’s take a look at the index parameter in the next section.
Event parameters and index parameters
Event can accept any type of parameters, including value type (UINTN,,bytesn,,bool,,address…),,struct,,enumAnd the value type defined by the user.
According to my research in this article, the only type that is not allowed is the internal function type.The external function type is allowed, but the internal function type is not allowed.For example, the following code will not be compiled.
// spdx-sLicense-IDentifier: UnlicenSed
Pragma solidity ^0.8.0;
Contract anonymousevents {
EEVENT 2 Secretpasswordhash) Anonymous;
}
If the event statement isanonymousIn the contract ABI, the incident is available"Anonymous"The field will be marked astrueEssence
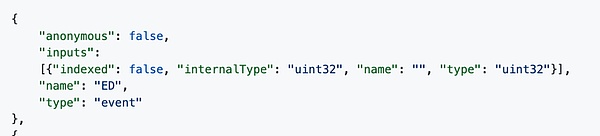
An anonymous advantage is that it makes your contract cheaper and cheaper, and GAS is cheaper when triggered.
A good case of anonymous event is a contract with only one event.All events in the negotiation contract are meaningful, because only this incident will appear in the event log.Subscribe to its name is irrelevant, because only one single event is defined to issue the contract.Therefore, you can define events anonymous, subscribe to all event logs from the contract, and confirm that they are the same events.
Check the use of anonymous use in the popular code library, such as DS-Note contract in DAPPPHUB[7]middle.
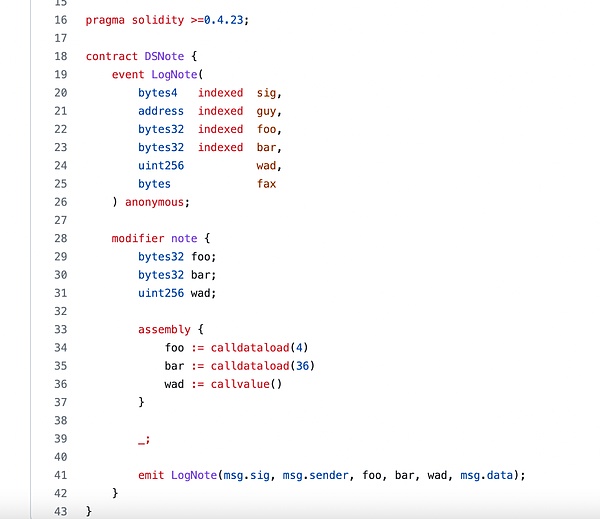
We can see in the above code fragment that because the event statement is anonymous, this can define the fourth “indexed” parameter.
Please note that because the anonymous event does not have the theme of Bytes32, the anonymous event does not support.selectormember.
Use the LOG operating code to trigger events in the assembly
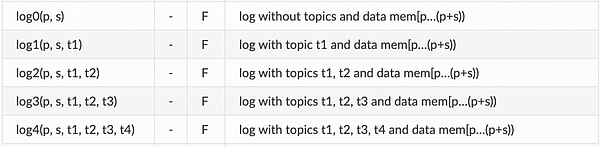
It is possible to trigger an event in the assembly, useLognInstruction, the instruction corresponds to the operation code concentrated by the EVM instruction.
To trigger an event in the assembly, you must store all the data issued by the incident inmemorySpecific position.
Once you will store data from the event in memory, and then you can specify the following parameters to the LOGN instruction:
-
P = Get the memory position of the data from it.Basically, this is a memory pointer, or a “offset” or “memory index”, depending on how you call it.
-
s = You want the number of bytes issued from P in the event.
-
All other parameters
T1As well asT2As well asT3andT4It is the event parameters you want to be indexed.Please note that there are two important things here: 1) These parameters should be the same as parameters defined in the same order as the definition of your events, 2) These parameters should be placed in memory to obtain data.
The following code fragment shows how to perform this operation in the assembly.
Event ExampleEventasm (bytes32 tokenid);
Function _ EmiteventaSSEMBL(Bytes32 tokenid) Internet {
Bytes32 Topichash = ExampleEventasm.Selector;
MSTORBR/> MSTORE (Add (FREEMEMORYPOINTER, 32), tokenid)
// emit the `ExampleEventasm` Event with 2 Topics
Log2 (
FreeMemorypointer, ///` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P` P`= Starting Offset in Memory
64, // `s` = Number of bytes in Memory from` P` to Include in the Event Data
Topic for Filtering The Event IT Self
tokenid // 1st indexed parameter
)
}
}
GAS cost of the event

All record operation code (Log0As well asLog1As well asLog2As well asLog3As well asLog4) You need to consume GAS.The more parameters (themes) they have, the more the GAS they consume.
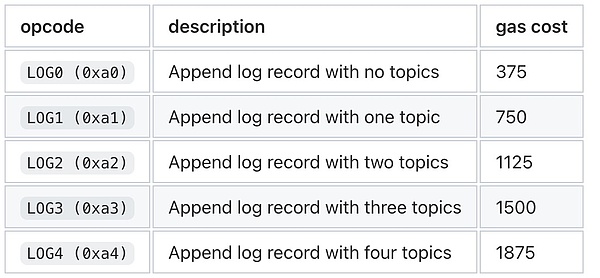
In addition, other factors such as indexes or data can also cause the event to consume more GAS.
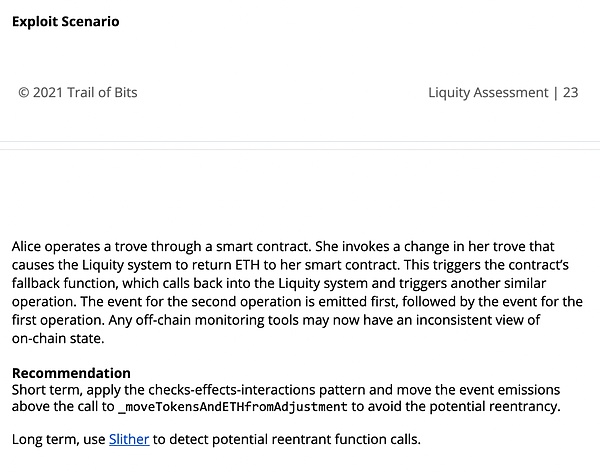
Check -event -interactive mode
Check-Effective-Interactive mode[9]It is also suitable for incidents.
One method to detect these modes is to use the Remix static analysis tool.
This model can also be detected by Slither.When a contract is running a contract with an external call, you will get a discovery to prompt the “re -entering event”.
Therefore, for DAPP, the order is very important, so that you can correctly check which incident first, next, and finally issued.This is particularly important when recursive or re -entered calls.If the event is triggered after external calls, and this external call is made of a repeated call, then:
-
The first incident was the second time after the call was completed.
-
The second event was issued after the initial transaction.
-
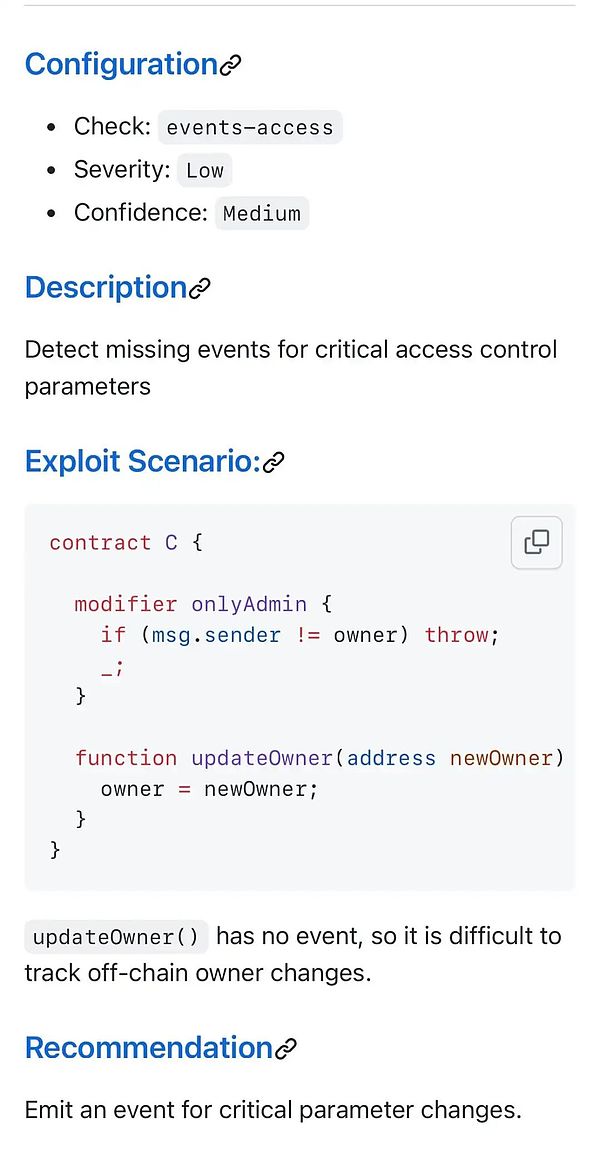
When restricted users and address execute certain operations (eg, owner or contract administrator).This includes such as popular ones
Transfer ownership (address)Function, this function can only be called by the owner to change the contract owner. -
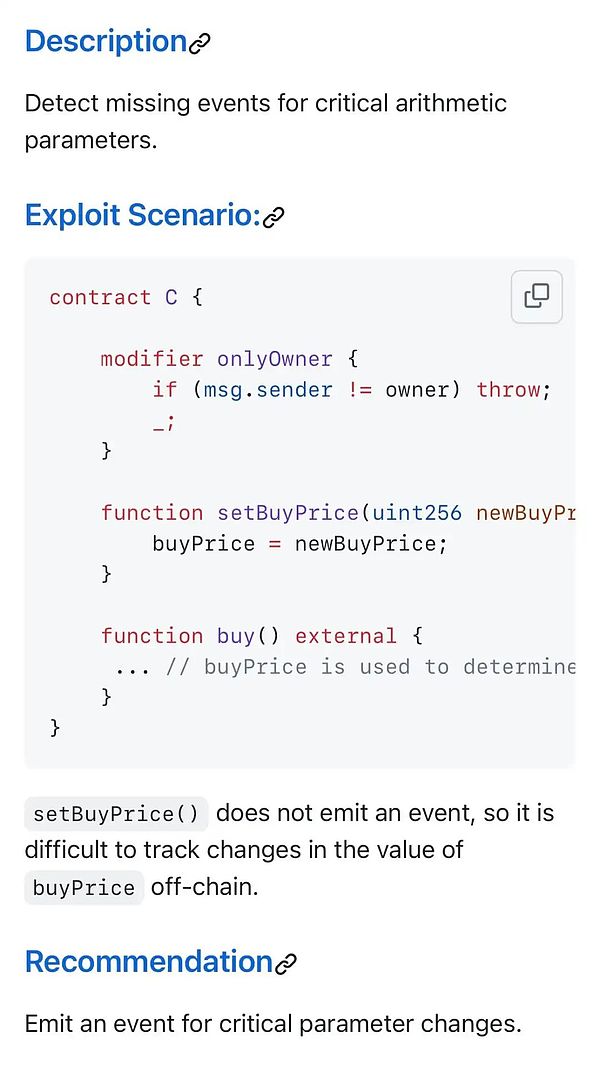
Change some key variables or arithmetic parameters, which are responsible for the core logic of the contract.It is particularly important in the background of the DEFI protocol.
-
Surveillance contracts deployed in production to detect abnormalities.
-
The missing document for the purpose of the use of anonymous event (know why)
[14] -
[Advantages of anonymous event]
Understanding this also allows clear audit tracking under the chain to monitor contract calls.You can see which functions are first and finally called, and the running order of each routine during the execution of the transaction.
slither detector documentation[10]-Stidity and Vyper’s static analyzers.
This potential vulnerability is also on the Trail of Bits[11]Found and report in the audit of smart contracts.

When should the incident be triggered?
There may be several cases in your contract that may be important and useful to trigger events.
Slither detector documentation[12]Describe more information about these situations.
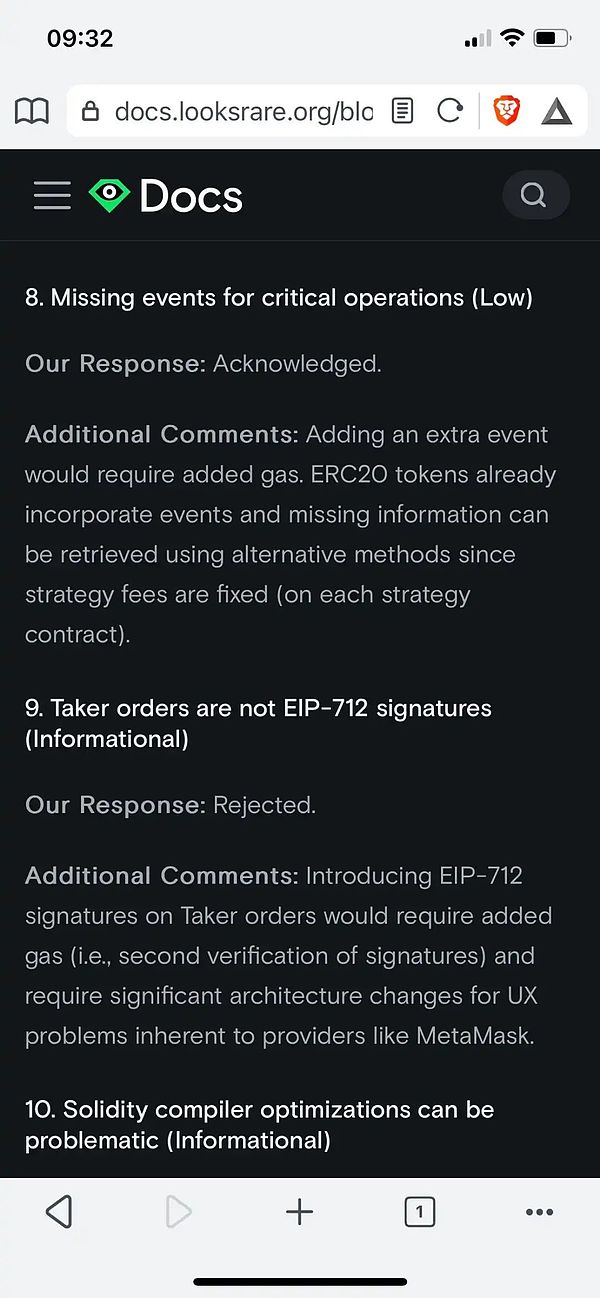
This is also described in the TRAIL audit report of looksrare.

View 0xprotocol[13]Details to understand the safety related issues related to the incident.







