
Author: Gimer Cervera, Ethereum Smart Contract Developer Translation: Shan Ouba, Bitchain Vision World
introduce
This article explores in -depth Ethereum virtual machines (EVM) and Solidity Assembly to achieve smart contract optimization and security.
Ethereum virtual machine (EVM) is the core component of the Ethereum network.EVM is a software that allows deployment and execution of smart contracts written in advanced language (such as Solidity).After writing the contract, compile it into bytecode and deploy it to EVM.EVM runs on each node of the Ethereum network.
Solidity Assembly is a low -level programming language that allows developers to write code at the level closer to EVM itself.It provides more detailed control over the execution of smart contracts, allowing optimization and customization that cannot be achieved through the higher -level Solidity code.
The language used in Solidity for the inner joint compilation is called yul.The programming language is compiled as an intermediary of the EVM bytecode.It is designed as a low -level language that enables developers to control the execution of smart contracts more finely.It can be used in independent mode, or in SolidityInternal Union CompilationEssenceYul is designed as a low -level stack language, allowing developers to write more optimized and more efficient code.Before explaining Solidity assembly, we need to understand how EVM components work.
EVM is a准 图 灵 灵 灵State machine.In this case, the term“allow”It means that the execution of the process is limited to the calculation steps of the limited number, depending on any of the GAS quantities that can be executed by any given smart contract.This is the way to deal with the suspension of stopping and the possibility of execution (malicious or accident) forever.In this way, the Ethereum platform is avoided.
GAS is a concept of calculating the calculation required to complete the transaction in Ethereum.The transaction cost is paid by Ethereum and is related to the price of GAS and GAS.Our goal in this process is to learn how to minimize the total amount of GAS consumed without affecting security.
Code optimization problem
The internal joint assembly is a method to access EVM at a lower level.It bypasses several important security functions and inspections of Solidity.The correct use of the inner joint assembly can significantly reduce the implementation cost.However, you should only use it to need its task, and only when you know what you are doing.Using the inner Lianhui Optimization code may bring new security problems to your code.To master the internal assembly, we need to understand the working principles of EVM and its components.
In EVM, you must pay for each time you visit any storage variable for the first time. This is called“cold”Visits, it takes 2100 GAS.The second or consecutive times is called“hot”Access, it takes 100 gas.
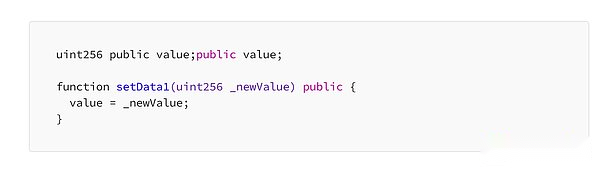
The following code is an example of how we optimize the code with yul.functionSetdata1Use solidity in traditional way as a global variableSet the new value.We need to spend 22,514 GAS when it first allocates this new value.The second cost is much less, that is, 5414 GAS.
>
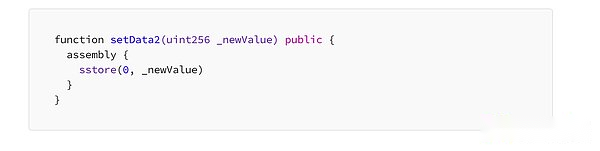
functionsetdata2Realize internal assembly.The inner foreign exchange block is marked by Assembly {…}, where the code in the bracket is the code of yul language.There is no need to understand the source code at this time, just remember that the software is accessing the storage space at a lower level.Therefore, the cost of execution will be lower.
In our example, the first modification of this value will cost 22,484 GAS.Several times in a row, the cost is 5384 GAS.The difference may not seem significant, but we should consider that this code may be executed thousands of times.
>
Why is it so expensive?Remember, we are in a decentralized world. Data are not only stored in one place, but are stored on tens of thousands of nodes.If future transactions need to be accessed or changed, it must also be easily used for each node in the network.The overall cost of the data is equal to the storage space it consumed and the sum of the calculation of the data on the entire network.
EVM stack, storage and memory
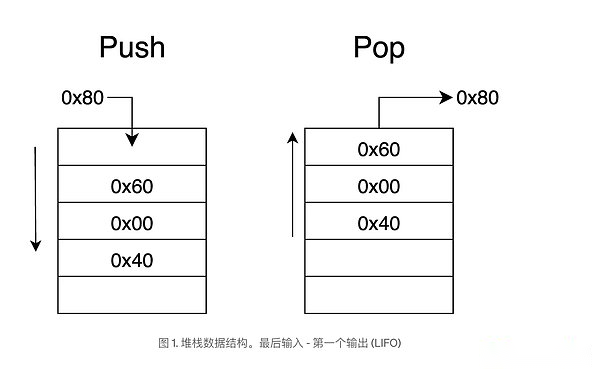
EVM is a stack -based machine that runs on the data structure called stack, which saves the value and executes operation.EVM has its own set of instructions (referred to as operating codes) to perform tasks such as reading and writing storage, calling other contracts, and performing mathematical operations.Stack according toLater, first out (lifo)Run the way, see Figure 1, which means that the recently inserted item is stored at the top of the stack, and it is the first item to be deleted.
>
When executing smart contracts, EVM creates an execution context containing various data structures and state variables.After the execution is completed, the context will be discarded and prepare for the next contract.During the execution, EVM will maintain a temporary memory, and there will be no continuous existence between the existence of transactions.EVM executes a stack machine with a depth of 1024 items.Each project is a 256 -bit word. The choice of this size is to facilitate the use of 256 -bit hash and oval curve encryption.
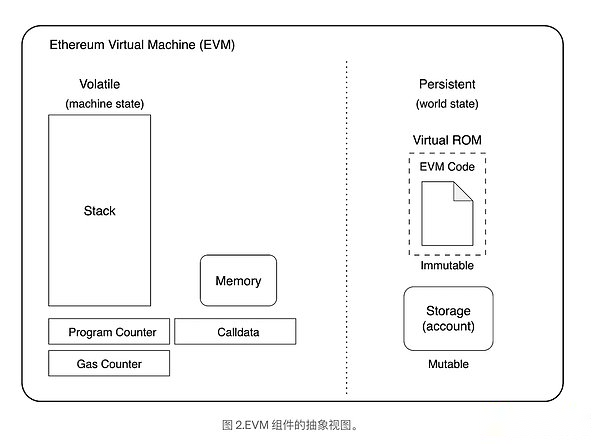
EVM has the following components, as shown in Figure 2:
-
Stack: The stack of EVM is a data structure running (LIFO) running (LIFO) in the way, which is used to store temporary values during the execution of smart contracts.
-
Storage: Permanent storage is part of the state of Ethereum, which is only initialized to zero for the first time.
-
Memory: Easy to lose, dynamic -sized byte array, is used to store intermediate data during the execution of contracts.Each time you create a new execution context, the memory is initialized to zero.
-
CallData: This is also an easy -to -loss data storage area, similar to memory.However, it stores unable variable data.It aims to save data sent as a part of a smart contract transaction.
-
Program counter: Program counter (PC) points to the next instructions to be executed by EVM.PC usually adds a byte after the execution of a instruction.
-
Virtual ROM: Smart contracts are stored in the area as bytecode.Virtual ROM is read only.
>
EVM stack
In this architecture, the instructions and data of the program are stored in memory, and the execution of the program isStack pointer control.The stack pointer tracking the next value or instruction will be saved or retrieved on the stack.When the program is running, it adds the value to the stack and performs the existing value.When the code wants to add the two numbers, it presss the number into the stack, and then performs the two values on the top.Then return to the stack.
>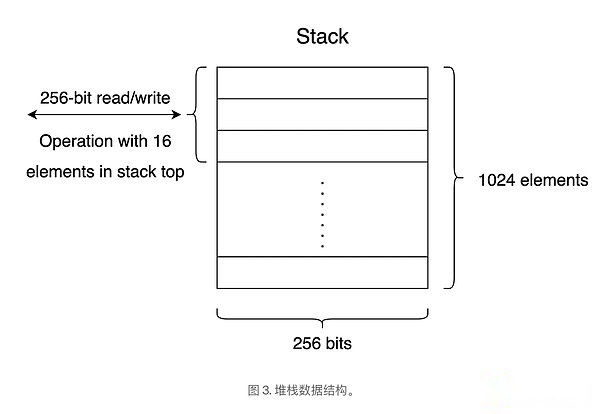
One of the most important features based on stack architecture is that it allows highly simple and efficient operation execution.Because the stack is a LIFO data structure, data and instructions can be easily processing data and instructions.
EVM has its own set of instructions, called the operating code.The operation code is used to perform tasks such as reading and writing storage, calling other contracts, and execution of mathematical operations.EVM instruction set provides most of the operations you may expect, including:
-
Stack operation: POP, Push, DUP, SWAP
-
Arithmetic/comparison/prescription: ADD, SUB, GT, LT, AND, OR
-
Environment: Caller, Callvalue, Number
-
Memory operation: MLOAD, MSTORE, MSTORE8, MSIZE
-
Storage operation: SLOAD, SSTORE
-
Program counter -related operating code: JUMP, JUMPI, PC, JUMPDEST
-
Stop operating code: Stop, Return, REVERT, Invalid, Selfdestruct
EVM storage
EVM storage is a non -prone space, saving 256 -bit -& gt; 256 -bit key value pair.The total number of storage slots in the contract is 2, which is a very large number of slots.Each smart contract on the blockchain has its own storage space.
During the function call, storage is used for data that needs to be remembered between function calls.It is used to store available variables and data structures that can be available even after the execution of smart contracts.
>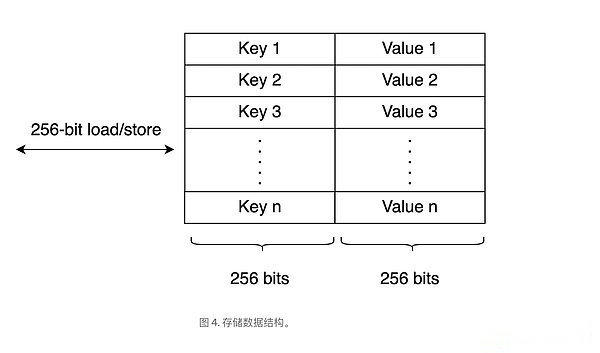
The operating code for accessing storage is: SLOAD and SSTORE
This account storage is permanent data storage, which is only used by smart contracts.The account (EOA) has no code and the storage space is empty.
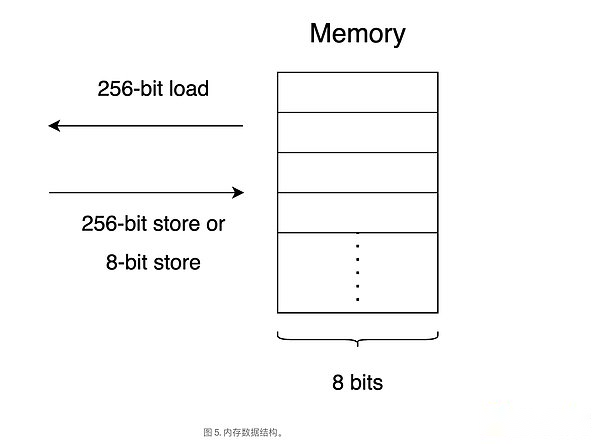
EVM memory
Memory is an easy -to -loss memory in the architecture, and its data is not lasting in the blockchain.Memory is a random access data structure that stores temporary data during the execution of smart contracts.
>
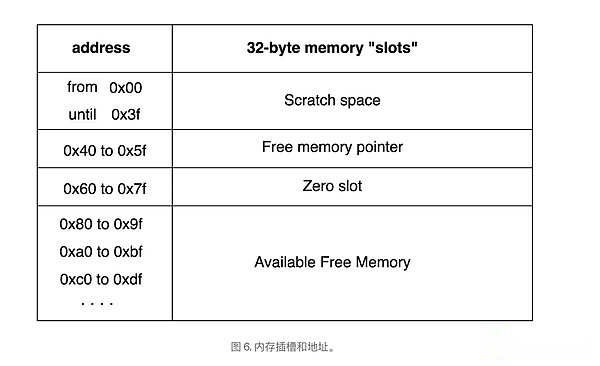
Memory is divided into four parts: 2 grooves are used for temporary storage space, 1 slot is used for free memory pointers, 0 grooves and 1 slot point to available free memory.The first 64th byte space will be used by the laidity method. The distribution method needs to be temporary space to store intermediate output before the final output is finally returned.
Free memory pointer is only a pointer to the start of the free memory.It ensures which memory positions are tracked in smart contracts and which are still available.This prevents contract coverage from certain memory that has been assigned to another variable.Figure 6 shows how the memory is divided:
>
Memory is used to store variables and data structures that do not need to be stored in memory.The memory size can be adjusted during the execution of the smart contract, but the access speed is slower and the cost is higher than the stack.
Considering that memory is zero -initialization, the operating code for access to memory is: MLOAD, MSTORE, MSTORE8
Sum up
In this article, we review some basic concepts related to the Ethereum virtual machine (EVM).To realize the internal assembly code, you need to understand EVM in -depth.This is because we are interacting with some components of EVM.In future courses, we will analyze other EVM elements in detail, such as: storage, memory and callData.In addition, we will review the important concepts such as bytecode, GAS, and Application Binary Interface (ABI).Finally, we will discuss the working principle of the operating code and more internal and foreign exchange examples to securely optimize the execution of smart contracts.







