
background
Some time ago, we discussed TON’s characteristics and user asset security issues in the first discussing Ton: account, token, transaction and asset security.Today, let’s learn another emerging high -performance blockchain platform, SUI, which has a number of innovative technologies and unique features, which has attracted the attention of developers and researchers.Sui focuses on providing a fast and safe trading experience, suitable for various application scenarios.This article will help readers understand SUI by explaining the Sui account model, token management, trading mechanism and asset security.
>
Account model
address
The SUI follows the extensive wallet specifications accepted in the cryptocurrency industry, including BIP-32 (and its variants SLIP-0010), BIP-44 and BIP-39 to provide users with key management.
>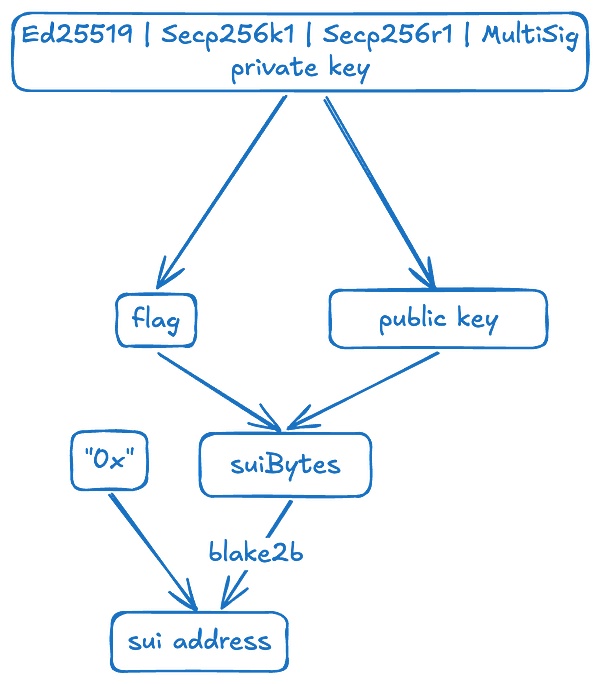
In order to assign a 32 -byte SUI address, SUI uses Blake2B (256 -bit output) hash function to connect the signature scheme (1 byte) with the public key byte.The SUI address currently supports pure ED25519, SECP256K1, SECP256R1, and Multisig. The corresponding logo bytes are 0x00, 0x01, 0x02 and 0x03, respectively.
Balance
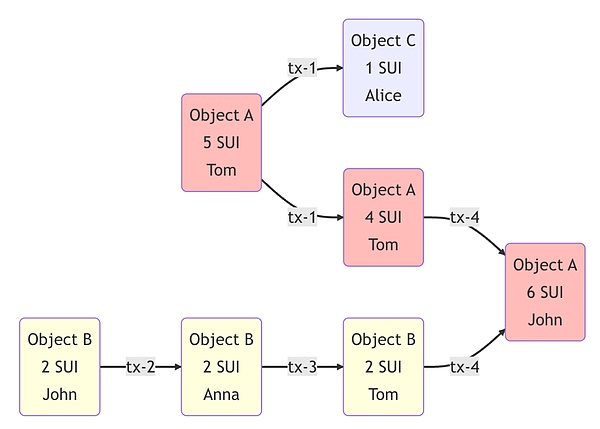
On the SUI, everything is an object, and the balance of the user is also the object.During the transfer process, if the balance contained in the object does not equal the required value, the object needs to be split or merged.For example, you have an object that contains 100 SUI, but you only want to transfer 30 SUI, so the system will divide this object into two objects: one contains 30 sui and the other contains 70 sui.You can transfer objects containing 30 SUI and retain the remaining objects.Conversely, if you need a larger amount, you can also merge multiple balance objects to form a larger amount.
>
Token management
Sui officially implements the standard code of Coin. Developers only need to call `use sui :: coin;` to use this standard library in the contract when issuing Coin.
Because the MOVE language is used, it is different from the programming language commonly used in other blockchain (such as solidity). Developers need to understand and pay attention to some unique functions or characteristics when using. Let’s look at a paragraph:
>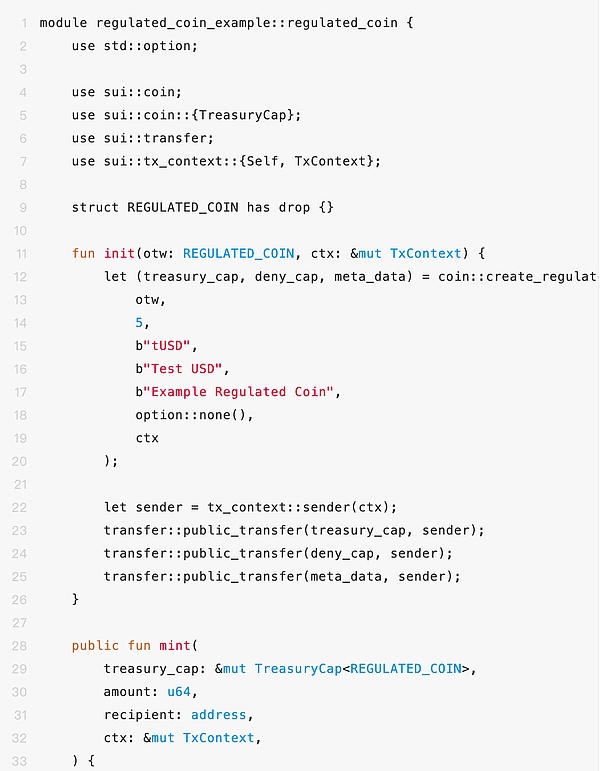
This is a complete Coin issuance contract. The smart contract design on the SUI is different from the blockchain platforms such as Ethereum or Solana. We cannot see the management of permissions in the source code.When using this function to create Coin (Coin :: Create_regulated_currency), the creator of the contract will receive a TreasuryCap object, which is necessary to cast a new Coin or destroy existing coin.Only by accessing the address of this object can the COIN distribution be maintained.
For users who received Coin, his account controlled the ownership of these tokens. When using these tokens to call smart contracts, these objects also needed to be passed in and signed the transaction.
Transaction mechanism
Trading is the concept of basic blockchain world, and it is a way to interact with blockchain.The transaction is used to change the state of the blockchain and is the only way.In the MOVE programming language used by SUI, transactions are used to call functions in the package, deploy new packages, and upgrade existing packages.
When constructing a transaction, you need to pay attention, and each transaction must clearly specify the object of its operation!This is similar to that of Solana’s transactions.
The content contained in the transaction:
-
Sendor -Sign the account of the transaction
-
Instruction list (or instruction chain) -The operation to be executed
-
Command input -command parameters: pure text -simple value, such as numbers or string, or object -transaction will access objects
-
GAS object -Coin object for payment transactions
-
GAS price and budget -transaction cost
Contract security
SUI uses MOVE as the programming language of smart contracts, which can solve the problem of vulnerabilities of Solidity’s high incidence to a certain extent, such as re -entered attacks, integer overflow, double flowers, DOS attacks and compilers.Error, so security audit is still necessary.Here are some matters that developers need to pay attention to during the development process:
1. permissions check:Analysis of the type of object received by external functions, for the privilege function involving sensitive operations, needs to ensure that the transmitted object is an object with privileges.If the function receives and uses the privilege object, the function caller must be the legal owner of the object.
2. External function check:Some functions should not be directly called by the outside. If there is a function interface that should not be released, the developer should propose that the function should not be disclosed.
3. Object analysis check:Because the objects in the SUI can be converted into public objects, developers should sort out the types of all objects used to confirm whether they are static or public, and whether there are errors.If the object of privatization should be converted into a public object, then anyone can use this object, which is a security risk.
4. Coin consumption check:SUI’s tokens are different from other chains. The design allows tokens to be included and held by other objects, and it can also be split, which derives several tokens consumption models:
-
Directly transfer to the token object to another object;
-
After adjusting the token objects, a new object is generated, and then transferred to the target object;
-
Demolition to the token object and transfer the partly split part to the new object.
Therefore, in the case of token consumption, developers need to check the following points:
-
Whether the amount of consumption is correct;
-
Whether the object has been transferred;
-
If there is a split, the amount of split is right.
5. Prices of prophecy machine price manipulation attack:If the contract on the SUI uses the prophetic machine to obtain the price, then you need to pay attention to the possibility of the price manipulated.Developers can introduce multiple data sources and consensus mechanisms to prevent the risk of being manipulated by a single data source.In addition, the average price of time can be used to prevent the risk of manipulating the prophecy machine.
6. Governance attack:In the contract on the SUI, if the voting rights design of the tokens are unreasonable, there is also the risk of encountering governance attacks. In this regard, you can refer to the logic of community governance of some mature decentralized organizations.
7. arbitrage attack:If logical design is unreasonable, the DEFI contracts on SUI also have the risk of arbitrage attacks.Developers should carefully review the logic in the contract when developing to avoid the use of attackers.
8. Fake recharge attack:When dealing with the SUI token recharge, the exchanges or developers also need to pay attention to check whether the transaction status is successful, whether the Package ID of the tokens is correct to prevent fake recharge attacks.
Summarize
In this article, we briefly discussed the design characteristics of SUI, including its account model, tokens management, trading mechanism, and contract security.Using MOVE programming language, SUI also introduced innovative data models and object storage methods while ensuring high performance and low latency, which significantly improves security and flexibility.Compared with other blockchain platforms, the MOVE language performed well in preventing common smart contract vulnerabilities (such as overflowing, heavy incoming attacks, etc.), which makes SUI more stable and reliable at the technical level.However, developers still need to pay attention to the security of the business logic level, especially in terms of authority management, the use of object types, and token consumption, beware of asset losses due to errors or improper designs in the code.
Reference link:
https://docs.sui.io/
https://docs.sui.io/standards/coin
https://move-book.com/







