Source: Liandeng Community
What are zk-SNARKs and zk-STARKs?They are all zero-knowledge proofs, but what are their characteristics and how to compare them to each other.
Zero Knowledge Proof (ZKP) is an encryption protocol that allows one party (proverb) to convince the other party (verb) that a statement is true without revealing any information beyond the validity of the statement itself.ZKP is a revolutionary technology in the blockchain ecosystem, enabling blockchain scalability through layer two solutions and building privacy protection applications.The two most prominent ZKP types are zk-SNARKs and zk-STARKs, each with different characteristics and use cases.
In this article, we will discuss zk-SNARKs and zk-STARKs, their key properties, and their comparisons.
Prerequisites
Understanding ZKPs: You need to know what circuits, constraints, witnesses, validators and provers are.
What is zk-SNARK (concise non-interactive knowledge argumentation)
Zk-SNARKs are a broad class of ZKP systems that are non-interactive, meaning there is no back and forth communication between the prover and the validator after the initial proof is generated.They are known for their efficiency, providing short proof sizes and fast verification times that remain the same regardless of complexity.
Key Features of zk-SNARKs
-
Trusted Settings:SNARKs requires a trusted setup phase where an initial set of parameters is generated, commonly known as structured reference strings (SRS).This setup phase uses a secret that, if exposed, will undermine the security of all subsequent proofs created with the setup.This setup data is often referred to as “toxic waste”.Trusted settings are often seen as a disadvantage because they introduce a potential trust problem: the user must believe that the settings are executed correctly and that the secrets are destroyed later.
-
Elliptic Curve Encryption (ECC): Many SNARK constructs rely on elliptic curve encryption, depending on the difficulty of the discrete logarithmic problem (DLP).While this provides powerful security for classical computers, it makes SNARKs likely to be vulnerable to future quantum computers, which can efficiently solve DLP.
Popular zk-SNARK protocol
-
Groth16:Groth16 is one of the most widely used SNARK protocols.It requires trusted settings for a specific circuit and is very efficient, generating very small proofs and fast verification times.Due to its compact proof size, it is commonly used in blockchain projects such as Zcash.
-
PLONK(Performance argument based on Lagranghi’s universal non-interactive knowledge argument): PLONK is a more flexible SNARK protocol that usesGeneraland updateable SRS, which means it can be used for any circuit and can be modified to support larger circuits.Unlike Groth16, the PLONK setting is not specific to any particular circuit and multiple circuits can be reused.This reduces the need to repeat trusted settings and makes it easier to add new programs or circuits without re-making the entire setup.
Characteristics of zk-SNARKs
-
Proof size: Small, which makes SNARKs suitable for applications with limited bandwidth and storage.
-
Post-quantum security: Limited due to dependence on ECC.SNARKs are not quantum resistant, as a sufficiently powerful quantum computer may solve DLP.
-
Trusted Settings: This is required (in most SNARKs).The setup phase introduces a trust assumption that, if not managed properly, can pose potential security risks.
-
Scalability: Very efficient for applications that require compact proof and fast verification, although the need for trusted settings in highly dynamic environments can be a limitation.
What is zk-STARK (Extensible Transparent Knowledge Argument)
Zk-STARKs are another type of ZKP that aims to address the shortcomings of zk-SNARKs.They are designed to be scalable and “transparent”, meaning they do not require a trusted setup phase.Instead, zk-STARKs use hash functions and expose known randomness to build proofs, thereby enhancing their security and scalability.
Key Features of zk-STARKs
-
Transparent settings:STARKs do not depend on secret parameters.Instead, their proofs are generated using public randomness, meaning they have no “toxic waste” that can destroy the system and do not require a trusted setup.
-
Hash-based security:STARKs rely on hash functions such as SHA-256, rather than elliptic curve encryption.This makes them resistant to quantum attacks, because under the current encryption assumption, hash functions are considered safe in front of quantum computers.
Features of STARKs
-
Proof size: STARK proof may be several times larger than SNARK proof, which increases verification time and is a disadvantage in environments with limited bandwidth or storage.This is due to their transparency, the use of polynomial commitments, and the way to achieve scalability.
-
Post-quantum security:powerful.Since STARKs use hash functions instead of elliptic curve encryption, they are less vulnerable to quantum attacks under the current encryption assumption.
-
Trusted Settings:unnecessary.STARKs uses transparent settings to eliminate the trust requirement in the setup phase and enhance security.
-
Scalability: Highly scalable, especially for large computing, they show more obvious performance advantages when complexity increases.They are more flexible because trusted settings are not required, as settings do not need to be re-produced for each new application or use case.
Comparison between zk-SNARKs and zk-STARKs
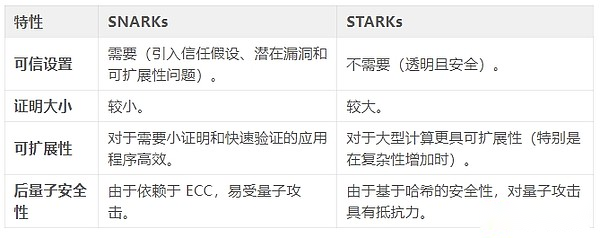
Summarize
Zk-SNARKsIt is a zero-knowledge proof system.They provide efficient proof size and fast verification times, but require trusted settings and use elliptic curve encryption to make them vulnerable to quantum attacks.
Zk-STARKsNo trusted settings are required.Instead, they rely on hash functions for security (making them quantum resistant) and are more scalable for large computing.However, their proof size is larger and is slower for smaller computational verification.
These two main ZKPs are crucial to building ZK protocols in the blockchain ecosystem, enabling blockchain scalability through layer two solutions and building privacy-protected applications.