
The first “thief” in the bull market is here.
近段时间的加密市场,除了比特币,MEME无疑是最大的赢家。AI, Politifi, and Desci are hyping one after another. Driven by hot spots and emotions, phenomenal MEMEs such as GOAT, PUNT, and BAN have made the dream of benefiting a hundred times again. Fighting the “Golden Dog” has also become an indispensable part of MEME people.Daily activities.
赌场规模初现,围绕MEME的市场化工具也随之增加。今天的主角——DEXX,正是日前MEME市场活跃的链上交易终端之一。
11月16日凌晨,DEXX遭遇攻击,多名用户代币被转移,截至目前损失高达2000万美元。I thought it was just an ordinary hacker attack, but under the constant slash of the community, more information also surfaced. The private key plain text and mnemonic words were out of bounds, and the boss was suspected to have a Rug history..
Is it insufficient prevention or directing and acting?Fake Rug or is it really stolen?DEXX让中文MEME圈再度蒙上了一层阴霾。
According to official reports, DEXX is a full-chain trading platform focusing on Memecoin, supporting multi-chain asset trading such as SOL, ETH, TRX, BASE, BSC, etc., and provides on-chain mobile stop-profit and stop-loss, hotspot push, order-following trading and other functions.In short, the core of DEXX function lies in on-chain aggregation, and user experience is the key. In its early publicity, “On-chain Binance” is mostly used as a selling point. According to people familiar with the matter, the daily transaction volume of the platform exceeds 50 million., daily profit exceeds $300,000.可以看出,尽管并不如Banana Gun、Unibot等成熟平台知名度高,但该平台也已初具规模,在MEME圈具备一定影响力。
但就在11月16日,刚刚声名鹊起的DEXX就给了MEME市场迎头痛击。当日凌晨,DEXX遭遇攻击,多名用户发现账户代币不翼而飞,Banana、LUCE等多个MEME遭遇波及大幅度下挫,LUCE跌幅超过41%。Community panic is about to break out, and it has caused widespread heated discussion on the public platform.At that time, rumors were flying in the market, and the rights protection group quickly increased to 3,000 people, more than 9,000 stolen transactions were reported, and even the amount involved was rumored to exceed 500 million US dollars.
However, in the subsequent investigation, the asset loss did not reach this level. According to the 821 stolen users who have been counted by Slow Fog, the total loss is close to US$20 million, of which one exceeds US$1 million and two are between 50-100The range of 10,000 US dollars, and the range of 28 is between 100,000 and 500,000 US dollars.But at present, hackers have not converged and transfer assets are still increasing.
On the day of the incident, DEXX responded quickly, saying that there was no Rug, and the problem is being investigated with all efforts.Its founder Roy (@honza204) also followed suit and responded, “I will pay for it and quarantine some users. I don’t have RUGs and I’m in the process of troubleshooting. I can’t reply one by one, don’t worry.”
Despite repeated statements that there is no Rug, the battle-hardened community clearly has some doubts.The subsequent preliminary investigation of slow fog and bit jungle has further aggravated the suspicion of platform Rug.The survey shows that the DEXX platform has major security issues. Not only does it store user private keys in the official server as a non-hosted platform, but no encryption measures are taken when the user exports the private keys, resulting in the private keys being in plain text during transmission.Exposed.
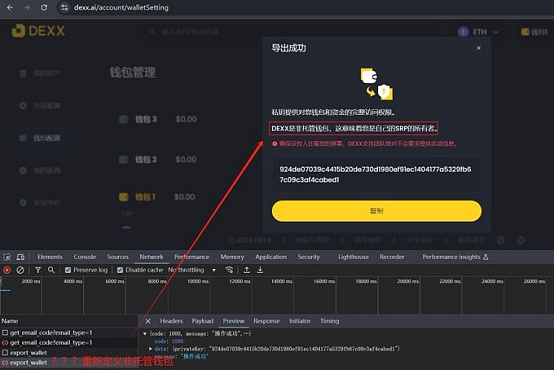
In addition to the taboo of plain text transmission, the clipboard permissions are also extremely unreasonable.The DEXX platform was found to repeatedly request user clipboard permissions. If the user has copied private keys or mnemonics in the clipboard, the information is most likely to be accidentally transmitted to the platform, increasing the risk of sensitive information leakage.
In terms of attack methods, there is no trace of intrusion on the front end of DEXX, but downloads private keys from the remote server to realize theft.Moreover, the hackers have obviously planned for a long time. Not only did they choose the relatively nervous time point in the early morning, but after the attack, the hackers adopted the strategy of creating new wallets one-to-one batches to transfer stolen assets and achieve anti-tracking to the greatest extent..
Promote yourself as a full-chain trading platform, but in fact it is more centralized than centralization. The private key is stored openly and you can also copy mnemonic words on the clipboard.The platform ignores such obvious security risks until the so-called “hacker” attacks. Can’t this hacker be the platform itself?
After the news was disclosed, the market was in an uproar, and the community continued to condemn, and the theory of self-stealing and money-running continued to ferment. The market spontaneously tracked DEXX, and more details also surfaced.
Although according to the registration information, the DEXX subjects are quite scattered, and companies are registered in the United States, the Bahamas, Singapore, Tokyo, Japan, Hong Kong and the Marshall Islands.But at present, the company is located in Xihu District, Hangzhou, and the company is named Hangzhou Chengdao Technology Co., Ltd.
With the opening of the netizen, the founder’s information was also completely disclosed.The real name of the founder is Lou Yulinfeng, a native of Jinhua, Zhejiang, at the age of 30. It is said that he has been engaged in online gambling..According to Encrypted Intelligence Orange, the so-called “text” boss actually has only a junior high school education.Some netizens also disclosed their positioning in the circle of friends, saying that they are currently in Thailand.What’s more, it is mentioned that the boss of the building had a previous record of soft rugs, and the project he had participated in Opendao is a precedent.Coincidentally, the day before the theft incident, Roy also posted a post saying “It’s great to have money”, which made various conspiracy theories rampant.
Rug public opinion is fermenting, market anger is also heating up, and KOLs that have promoted the platform are also being slutty.In fact,The main way of DEXX promotion is to promote batches of well-known KOLs in the form of rebates, and obtain traffic through the influence of KOLs.This method is also quite common in the currency circle, but it is worth noting that compared with other platforms, the Dexx commission rebate ratio is very high, with the highest reaching 50%-60% of the handling fee.In the connection between official personnel and KOLs, it was mentioned that the top KOLs can receive more than 40,000 US dollars through commission rebates alone.
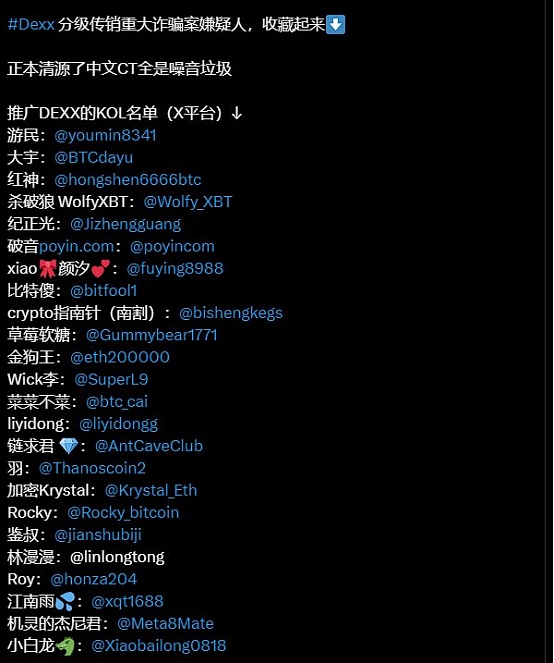
Under the temptation of interests, there are many KOLs, especially Chinese KOLs. More than 25 well-known KOLs such as Youren, Daewoo, Hongshen, Shapolang, etc. have promoted DEXX, and some KOLs have even failed to do so in private domain traffic.Bottom line promotion is also the reason why most of the victims are Chinese users this time.After the incident, the market also launched a series of criticisms against the KOLs, believing that KOLs are suspected of abuse of their influence and not reporting on cutting leeks.The KOLs also performed differently in their accusation.
Cutting the mat immediately is a necessary operation.Some KOLs directly deleted previous publicity copy to smooth out market memories; KOLs, which are more fond of feathers, will apologize and pay a certain amount of compensation from the perspective of maintaining long-term profits, but there are not many KOLs in this part, only single digits;Most KOLs seem to be planning to be invisible to wait for the storm to subside.
Of course, remediation is second, and the most urgent task is to recover the stolen assets.Although Roy said he would pay the full amount, it remains to be seen whether he could take out enough amounts. If he directed and acted by himself, then the amount could be recovered and he could resort to judicial means. However, if it was really a hacker invasion, he would be in the chain of unknown identity authentication.When you go to the exchange, protecting your rights seems even more distant.
Quoting the claims of lawyers Guo Zhihao and Shao Shiwei, DEXX, as a project operated by domestic institutions, is equivalent to engaging in virtual currency-related business activities in China in disguise, and should be considered illegal financial activities. The minimum principle is to ban and order business closure in accordance with the law.Specifically for this incident,If the platform is really stolen by hackers, the platform illegally collects user’s private keys, which is suspected of infringing on citizens’ personal information; if the platform directs and acts by itself, it is highly likely to be classified as a stricter crime of fraud, and the sentence is sentenced to a maximum ofDelivered life imprisonment.KOLs who want to be invisible may not escape their responsibility. Since KOLs are suspected of earning platform commissions through information networks, they are suspected of illegally using information networks, and there is certain joint and several liability. Although the probability of filing this crime is not high, the threshold for conviction isVery low, if users insist on climbing, they may not let KOL lose its skin.
Yesterday, DEXX posted a letter to hackers on X platform, saying that it has received strong support from security agencies, partners and exchanges to find the stolen tokens, and is also continuously monitoring the hacker’s address in order to freeze the stolen in a timely manner.Funds, now require the resolution of the incident within the next 24 hours, otherwise it will continue to cooperate with local police, security agencies and exchanges to conduct investigations and take enforcement actions to protect user assets, no matter how long it takes.平台表示,正在标记黑客地址,并请求Solana基金会提供帮助被标记后,黑客将无法通过任何方法充值进交易所/兑换成法币。
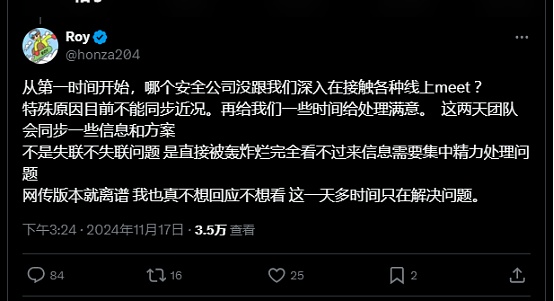
The founder also spoke out again to refute the rumors of missing contact, saying, “For special reasons, we cannot synchronize the current situation. Give us some time to handle it with satisfaction. In the past two days, the team will synchronize some information and solutions, not whether it is missing or not.”
It is not uncommon to talk about theft only in the crypto industry. DEXX is not the first one, and it will inevitably not be the last one.In essence, there is no absolutely secure custodial and non-custodial wallet. In addition to the enhanced transparency of open source on the contract chain, it can only rely on a stronger background and a stronger amount of funds, otherwise it is only based on external trust transmission and auditing, etc.The method does not rule out the possibility of major dangers.Taking DEXX as an example, the platform has also been audited by CertiK, but the final response to this incident is that the incident occurs on the Solana chain, which is not within the audit coverage.
Back to the user itself, the improvement of security awareness is imminent.In addition to not believing in anyone’s promotion, when it comes to the use of funds, a platform with a complete security mechanism and sufficient endorsement should be given priority.In terms of fund security management, we should try to use completely independent equipment to operate under the premise of diversified and placing assets. It is recommended to use decentralized authentication and inconvenient convenience as the core, avoid setting up password-free and live-action authentication, and use plug-ins with caution.Large assets, stored using hardware wallets.Users should remember that safety is the priority of operations, otherwise the first pot of gold earned in the bull market may become someone else’s.
On the other hand, if it is a platform Rug, even if the founder runs away, he may not be able to rest assured. After all, as a guarantee person who has been opened and may have over 100 million yuan on his body, no matter where he is, he has no safety.where to go.








