Introduce Full -State Encryption (FHE): Exploring its exciting application, limitations, and recent promotion of its popular development.
>
When I first heard that “FHE” (FHE), I was curious about the name of the fashion concept of fashion.Over the years, we have encountered many fashionable vocabulary that swept the entire industry. The nearest one is the “zero knowledge certificate” (ZKPS).
After some investigations and exploration new companies that are using FHE to build products, I noticed a prospect full of new tools.In the next few months and years, FHE may become the next major technology that sweeps the entire industry like ZKPS.The company is using the latest progress in various fields of cryptography and cloud computing to pave the way to a powerful future for protection of data privacy.The question is not whether we can realize this, but when it is realized, I believe that FHE may be a key promotion factor for promoting data privacy and progress in ownership.
In the next few weeks, I will thoroughly learn more about FHE and study its limitations, potential and applications.I will share my research results in a series of articles to explore different aspects of dialogue around FHE.This week, I will introduce this technology and discuss why it has attracted a lot of attention recently.People in many industries are talking about it, including Kyle Samani from Multicoin Capital[4]He said:
“FHE is the holy grail of cryptography. Over time, FHE will reshape all the computing structures, whether in web2 or web3.”
What is homorsphism?
The key to solving the problem is to understand the meaning of “the same state”.Tracing the root of its roots, the same state originated from mathematics and is defined[5]The mapping of the core components is retained between the two same algebolic structures.
If you prefer a more practical definition, a basic principle behind mathematics is that the two groups do not need to be exactly the same to have the same core attributes.For example, imagine two fruit boxes:
Box A contains small fruits.
Box B contains large fruits.
>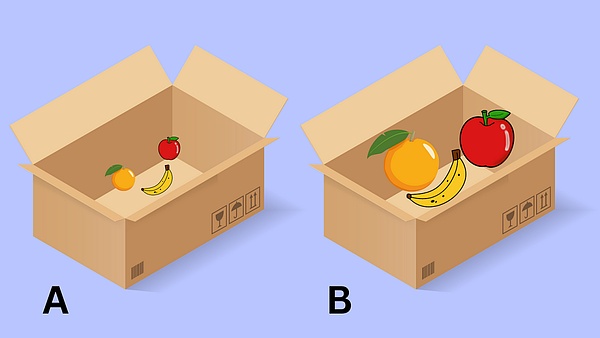
Although the size of individual fruits is different, squeezing a small apple and a small orange in the box A will produce a mixed juice with the same flavor of a large apple as a big orange in the box B.Squeeze juice to produce the same flavor similar to the core component between two boxes.Assuming our main concern is the same taste, then which box we squeeze fruit juice is not important, because the size of the juice is not the focus of our attention.Two boxes (taste) are equivalent in the place where they are concerned, so the differences (size and quantity) between them have no effect on their main functions (producing specific juice flavors).
Compared with the same state, we captured the two main characteristics of it:
-
Map: We have established a connection between two boxes, and each small fruit in the box A corresponds to a large version in the box B.Therefore, the small apple in the box A corresponds to the big apple in Box B, which is pushed according to this.
-
Reserved operation: If two small fruits are squeezed in box A, they will produce specific flavors of fruit juice, then squeeze their corresponding large versions in box B should produce the same taste.Although the size and quantity of fruit juice are different, the “taste features” are retained.
What is a full -state encryption?
Link all this to the central theme of this article and encrypted in the same state[6](FHE) is a specific data encryption method,Enable people to perform calculations on encryption data without leaking original data.Theoretically, the analysis and calculation of encrypted data execution should produce the same results as the execution of the original dataEssenceThrough FHE, we have established a relationship corresponding to the data of the encrypted data set to the data of the original data set.In this case, the retention of the core component is the ability to perform any calculations and generate the same results on any data set.
In this context, many companies have taken preventive measures to protect user data and maintain differentiated privacy.The company rarely stores data in the cloud or its database in the form of primitive, unlike.Therefore, even if the attacker controls the company’s server, they still have to bypass encryption to read and access data.However, when the data is only encrypted and idle, the data is no longer interesting.When the company wants to analyze the data to obtain valuable insights, they have no choice but to fix the data.Once decrypted, the data will become fragile.However, through end -to -end encryption, FHE becomes very useful because we no longer need to decrypt data for analysis; this is just the tip of the iceberg that reveals the possibility.
A key consideration is whether the company should be allowed to read and store our personal information.Many people respond to this standard that the company needs to view our data to provide us with better services.
If YouTube does not store data such as watching and searching history, the algorithm cannot give full play to and show me the video I am interested in.Therefore, many people think that it is worth a trade -off between data privacy and gaining better services.However, through FHE, we no longer need to make such a weighing.Companies like YouTube can train their algorithms on encryption data and produce the same results for end users without infringing data privacy.Specifically, they can encrypt the information such as my viewing and search history, analyze it without checking it, and then show me the video I am interested in according to analysis.
FHE is an important step towards a future. Among them, our data is no longer a valuable product that we voluntarily provides by the organization.
Application of full -state encryption
Correct application of full -state encryption (FHE) is a breakthrough in all storage user data departments.We are watching a technology that may change our overall attitude towards data privacy and the company’s acceptable violations.
Let’s study how to reshape the health care industry from FHE[7]Data practice begins.Many hospitals preserve private records of patients stored in their databases. For moral and legal reasons, they must keep confidential.However, this information is valuable for external medical researchers, and they can analyze these data to infer the important opinions of diseases and potential treatment methods.A main obstacle to slowing research progress is to keep the patient’s data absolute confidential when outsourcing data outsourcing.There are many ways to anonymous or pseudo -anonymous patient records.But they are not perfect, and they may reveal that there are too many information to identify, or it is not enough to reveal enough information about their cases, making it difficult to obtain accurate opinions on the disease.Using full -state encryption (FHE), the hospital can encrypt patient data to more easily protect the privacy of patients in the cloud.Medical researchers can perform computing and running analysis functions on encryption data without damage the privacy of patients.Because there is a one -to -one mapping between the encrypted dataset and the original data, the results obtained from the encrypted data set provides true insights that can be applied to actual cases.FHE can quickly promote the development of the health care industry.
Another exciting application of FHE is artificial intelligence (AI) training.At present, the field of artificial intelligence is facing privacy issues, which hinders the company’s access to many wide data sets for improving AI algorithms.The company that train AI must make choices between using limited public data sets, paying a lot of funds to purchase private datasets or creating data sets, which is challenging for small companies with fewer users.FHE should solve the privacy problems that prevent many data set providers from entering the market.Therefore, the improvement of FHE may lead to an increase in the number of data sets that can be used to train AI.This will make AI training more financially and refined, because the diversification of available data sets can be increased.
The past limit of the same state encryption
If FHE can indeed change modern big data, why haven’t we seen more practical applications?
Although people have been discussing and studying FHE for many years, it is actually very difficult to achieve FHE in practice.The core challenge is to perform the computing power required for FHE.Full -state security data set can produce the same analysis results as the original data form.This is a challenging feat that requires a lot of calculation speed and ability, and many of them are unrealistic about the implementation of existing computers.It usually takes a few seconds to operate in the original data, and it may take a few hours or even a few days on the same -state encryption dataset.This calculation challenge has caused a loop of self -continuation. Many engineers have postponed the FHE project, which slows down its development and limits the realization of all its advantages.
A specific example of the calculation problem faced by engineers in FHE is how to solve the “noise error[8]“When calculating the same -state encryption dataset, many engineers produce excess noise or errors every time they calculate. When only a few calculations are required, this can be tolerated, but after multiple analysis, after multiple analysisThe noise may become so obvious that the original data becomes difficult to understand.
Why is it now?
It’s like generating artificial intelligence[9]It was once considered limited and primitive, and then became the mainstream. Full -state encryption (FHE) is developing in similar progress.Many industry leaders, even leaders in the blockchain field, have gathered and organized a large number of FHE research and development.This has promoted the development of several industries in recent times and promoted the striking narrative of the progress of this technology.
DPRIVE Plan
In March 2021, Microsoft, Intel, and National Defense Advanced Research Program (DARPA) agreed to launch an many years of plans[10], To accelerate the development of all -state encryption (FHE).This plan called data protection (DPRIVE) in the virtual environment marks the major progress of FHE.It shows two industry giants specializing in cloud computing and computer hardware to jointly solve the problem of data privacy.They initiated this plan to establish computers and software that can manage FHE computing speed, and formulate a guidance policy for accurate implementation of FHE to prevent data leaks that may be generated due to incorrect use.
As part of the DPRIVE program, engineers have proceeded to solve the “noise errors” mentioned earlier, and explore the way to reduce noise levels to retain the original data.A promising solution is the design of the design of the big calculation[11](LAWS) Data representation.Although traditional computer processors (CPU) usually use 64 -bit characters, engineers are developing new types of hardware that can handle 1024 or more lengths, and use LAWS.This method is effective, because research shows that the longer words directly affect the signal -to -noise ratio.Simply put, the longer word grows less noise in each additional calculation of FHE, allowing more calculations before reaching the data loss threshold.By constructing new hardware to solve these challenges, engineers participating in the DPRIVE plan have greatly reduced the calculation load required to perform FHE.
In order to speed up the calculation speed and close to the goal of 100,000 times FHE, the DPRIVE team started to carry out a continuous journey, designing a new data processing system to surpass the ability of traditional processing and graphics units.They developed a new multiple instructions and more data[12](MIMD) system can manage multiple instructions and data sets at the same time.MIMD is similar to building a new highway instead of using the roads with insufficient existing equipment to accommodate FHE’s fast real -time calculations required.
The interesting thing about the DPRIVE plan is that it is widely used in computer mathematics computing “parallelism[13]“This allows developers to perform multiple large -scale calculations at the same time. You can treat parallelism as a different part of a group of mathematicians to deal with huge mathematical problems at the same time, rather than let them complete their respective work one by one.Although performing multiple calculations at the same time helps to solve problems quickly, the computer must cool down to prevent overheating.
In September 2022, after starting the plan for a year and a half, Microsoft, Intel and DARPA announced[14]They have successfully completed the first stage of the DPRIVE plan.They are currently undergoing the second stage of DPRIVE.Intel also launch[15]It has its own all -state encryption toolkit and provide tools for developers to promote faster all -in -state encryption in the cloud.Intel designed this toolkit to ensure that it is compatible with the latest data processing and calculation.It includes special functions dedicated to the customization, seamlessly running with Microsoft Seal, samples of all -state encryption schemes, and technical documents that guide users.
Google’s Private Join and Compute[16]The open source library provides developers with a multi -party calculation (MPC) tool.This calculation method allows all parties to obtain sharing insights through different data sets without exposing the original data to each other.Private Join and Compute combines the encryption technology from FHE with the private collection intersection (PSI) to optimize data confidentiality practice.PSI is another encryption method that allows all parties with different data sets to identify common elements or data points without disclosing its data.Google’s method of promoting data privacy is not only concentrated in FHE; it integrates FHE and other influential data practice, and gives priority to a wider range of MPC concepts.
The increasing availability of the highly respected full -state encryption library is worth noting.However, when the highly respected companies try these libraries in their operations, the situation becomes more noticeable.In April 2021, Nasdaq, a famous stock exchange and global capital market technology entity, will[17]FHE is included in its operation.Nasdaq uses Intel’s FHE tools and high -speed processors to identify valuable insights and potential illegal activities through full -state encryption to identify data sets containing sensitive information, so as to deal with financial crimes through anti -money laundering work and fraud testingEssence
Recent financing
In addition to the research and development of the company mentioned earlier, there are several other companies who have recently received a lot of financial support to focus on the integrity encryption (FHE) initiative.
Cornami[18]A large technology company has highly praised the pioneering development of scalable cloud computing technology for full -state encryption design.They are engaged in many efforts to create a more effective computing system that supports FHE than traditional CPUs.They also guide to protect the initiative of quantum computing threats.In May 2022, Cornami announced[19]A round of C -series financing was successfully carried out, led by SoftBank, raised $ 68 million, so that its total funding reached 150 million US dollars.
Zama[20]It is another company in the blockchain industry that is building an open source and omnidirectional encryption tool. Developers can use these tools to build an exciting application using FHE, blockchain and artificial intelligence.ZAMA has developed a full -state Ethereum virtual machine (FHEVM) as one of its products.This smart contract agreement keeps the transaction data on the chain and keeps encrypted during processing.Developers who explore various applications using the ZAMA library are impressed by their performance, even in complex use cases.ZAMA in February 2022[twenty one]The $ 42 million round A financing was successfully completed, led by Protocol Labs, making its total funding of $ 50 million.
Fhenix[twenty two]It is also an emerging project that introduces FHE into the blockchain.Their goal is to extend FHE applications to areas except confidential payment, and for FHE in the field of decentralized finance (DEFI), bridge, governance voting, and web3 games[twenty three]Open the door.In September 2023, Fhenix announced[twenty four]The 7 million US dollars of seed round financing was successfully completed, led by Multicoin Capital and Collider Ventures.
What will happen next?
Over the years, Full Crypto Crypto (FHE) has been a concept of promising strong end -to -end encryption, which indicates the future of strong data privacy.Recent development has begun to transform FHE from theoretical dreams to actual reality.Although each company competes to become the first pioneer to achieve a strong and complete function, many companies are cooperating with the complexity of this powerful technology.By implementing the open source library of various cross -team plans and development with other libraries, this spirit of cooperation is obvious.
According to my survey, the discussion around FHE seems far -reaching.In the next few weeks, I am glad to study in depth and share my more insights in FHE research.Specifically, I can’t wait to explore the theme:
FHE’s emerging application.
The interaction between zero knowledge proof (ZKPS) and FHE.
Integrate FHE and Private Collection (PSI) to promote the multi -party calculation (MPC).
New companies like ZAAA and FHENIX have developed in the field of FHE.
>
Reference quotation:
Arampatzis, Anastasios. “The latest development of full -state encryption.”VENAFIOn February 1, 2022, venafi.com/blog/what-alre-latest-developments-homorphic-encryption-sk-experts/.
Arampatzis, Anastasios. “What is the same -state encryption and how to use it.”VENAFI, April 28, 2023, Venafi.com/blog/homorphic-encryption-IT-And- IT- Use/.
“Build hardware to achieve continuous data protection.”DarpaOn March 2, 2020, www.darpa.mil/news-Events/2020-03-02.[25]
Cristobal, SAMUEL. “Full of the same state encryption: the holy grail of cryptography.”DataScience.aeroOn January 7, 2021, DataScience.aero/fully-homomorphic-entryption-the-holy-grail-of-coreraphy/.
“Full of the same state encryption: What is it, why is it important?”Internet associationOn March 9, 2023, www.internetsociety.org/resources/doc/2023/homomorphic-encryption/.[26]
Hunt, James. “Fhenix raised $ 7 million through the seed wheel financing led by Multicoin Capital.”The block, The Block, September 26, 2023, www.theblock.co/post/252931/fhenix-seed-multicoin-capital.[27]
“Intel® full -state encryption tool package.”Infel, www.intel.com/content/www/us/en/developer/tools/homorphic-encryption/overw.html#gs.fu55im.[28]The visit date is October 8, 2023.
“Intel cooperated with Microsoft to participate in the DARPA project.”Infel, March 8, 2021, www.intel.com/content/www/us/en/newsroom/news/intel-collaboraate-Microsoft-darpa-html#gs.ftusxq.[29]“Intel to NASDAQ’s same -state encryption research and development has brought progress.”InfelOn April 6, 2021, www.intel.com/content/www/us/en/newsroom/news/xeon-dvances-nasdaqs-homomorphic-rd.html#gs.6mpgme.[30]
Johnson, Rick. “Intel completed the first milestone of DARPA DPRIVE, it realized the full -state encryption platform.”Infel, 2022 年 9 月 14 日, community.intel.com/t5/Blogs/Products-and-Solutions/HPC/Intel-Completes-DARPA-DPRIVE-Phase-One-Milestone-for-a-Fully/post/1411021.
“Microsoft Seal: Quick and easy to use the same -state encryption library.”Microsoft Research, January 4, 2023, www.microsoft.com/en-s/research/project/microsoft- seal/.[31]
Paillier, Dr. Pascal.Business Age, March 9, 2023, www.businessage.com/post/fully-homorphic-encryption-the-HOLY-GRAIL-OF-CRYPTOGRAPHY[32]
Samani, kyle. “Dawn on the chain.”Multicoin Capital, September 26, 2023, https://multicoin.capital/2023/09/26/the-dawn-on-chain-fhe/
“What is a full -state encryption?”Inpha, April 11, 2021, https://inpher.io/technology/what-s-fully-homorphic- entryption/







