
Author: Dewhales Research Source: Substack Translation: Shan Oba, Bitchain Vision Realm
1. Introduction: What is FHE, its historical and applications
FHE represents a completely identical encryption, which is an encryption solution that allows the ciphertext to perform computing directly without decryption.This means that the encrypted data maintains the encryption state throughout the computing process, and the calculation result is also encrypted. No one can access explicit data at any time.FHE supports calculation of encrypted data, including machine learning and artificial intelligence analysis, so that scientists, researchers and data -driven enterprises can extract valuable insights without decrypting or leaking underlying data or models.Completely the same -state encryption is the most powerful form of encryption, but it has a great disadvantage and requires a lot of computing power.
In fact, there are many types of FHE: BGV, BFV, CKKS, FHEW, NUFHE, and TFHE.After being proposed in 1978, the same -state encryption (HE) initially developed slowly in the first thirty years.The current form of FHE came out in 2009. At that time, Craig Gentry proposed a method of fulfilling a completely homogeneous encryption, although the system would introduce noise every time it operated.Later, some people proposed a modified version with a small ciphertext, but the most popular solution was proposed by ZVIKA Brakerski and his team. Compared with the early FHE method, it provided better security and performanceEssenceAfter several continuous iterations -BGV, BFV, and CKKS -GSW were born, and it was developed to develop FHEW (launched in 2014) and TFHE (launched in 2016).Chillotti, GAMA, Georgieva, and Izabachene shortened the delay of each door guidance operation to less than 0.1 seconds.Since then, the program has included programming guidance into its process, accelerating FHE, and making it applicable to most use cases, including web2 and web3 applications.
>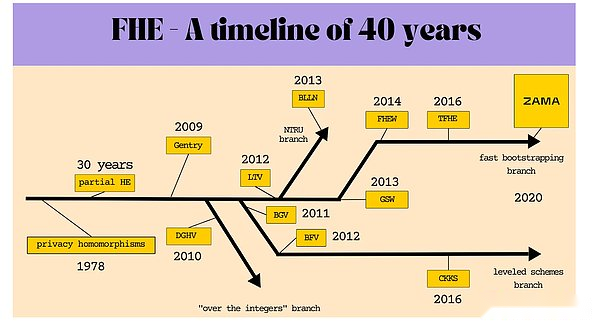
So far, the final result is ZAMA’s TFHE-RS, which has extended the original TFHE function to support integer programming guidance.Moreover, the current Privasea implementation is TFHE-RS.
FHE use case:
-
cloud computing:FHE allows users to store and process data on remote servers in a remote server to bring huge benefits to cloud computing.This means that users can use the powerful computing capabilities of the cloud while ensuring the security and privacy of data.This is a win -win situation for all participants.
-
Financial services:Financial services can also use FHE’s function.Through securely processing financial data, FHE allows financial institutions to analyze complex encrypted data.The best part is that customer privacyIt remains unchanged throughout the process.
-
Machine learning:By training the model on encryption data, FHE can greatly promote machine learning.This enables the organization to use the power of machine learning while ensuring data security.
2. Privea Overview
PRIVASEA AI network provides solutions for the privacy related to artificial intelligence data.This network represents a cutting -edge architecture that combines full -state encryption (FHE) with a blockchain -based incentive to solve the increasing concern of data privacy, and meets the growing demand for cooperation AI computing.EssenceThe PRIVASEA AI network divides FHE from theory to application into the following four levels: application layer, optimization layer, arithmetic layer, and original layer.The network provides general and customized solutions to meet the gap between user privacy and distributed computing resources in AI processing, covering all four levels of FHE.
A key goal of the PRIVASEA AI network is to ensure compliance with data protection regulations, including the EU’s strict “General Data Protection Regulations” (GDPR).These regulations put forward strict requirements for collecting, processing and storage of personal data.
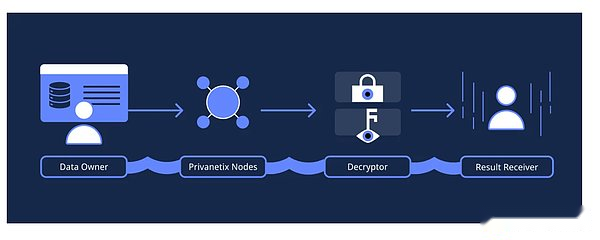
2.1 Network participants:
>
-
Network users (data owners, result receivers): initiated machine learning tasks, provided data securely, and interacted with the Internet to obtain decryption results.
-
Privnetix Node (Calculating Node): As a service provider in the Privasea AI network, it provides computing resources for privacy protection machine learning tasks.
-
Decryptor: Make sure that the encryption results generated by the PrivaNetix node are specially decrypted by special participants.They collaborate with network users to decrypt and explain the final result of machine learning tasks to ensure the privacy and integrity of decryption results.
2.2 Privasea architecture:
>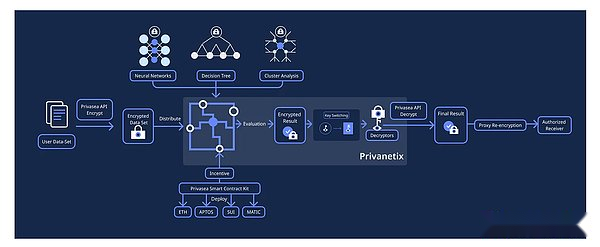
The PRIVASEA AI network consists of four main components: Hesea library, Privasea API, PrivaNetix, and Privasea smart contract kits.
-
Hesea library: This component constitutes the basis of the Privasea AI network. It custody the efficient implementation of a series of popular all -state encryption solutions, such as TFHE, CKKS, BGV, BFV, etc.Hesea library provides developers with permissions to access various functions.
-
Privasea API: A set of comprehensive protocols and tools based on Hesea library.Privasea API allows developers to easily integrate advanced privacy protection functions into their AI applications.
-
PrivaNetix: A computing node network, which can be calculated securely on encrypted data.By distributing calculations on multiple nodes, PrivaNetix ensures the scalability and efficiency of the Privasea AI network.
-
PRIVASEA Smart Contract Set: This kit includes a series of carefully designed smart contracts to handle all aspects of network management.
In addition, according to GitHub, Privasea also contains several other components of ZAMA AI, which can provide the most advanced FHE solution for blockchain and AI:
-
Concrete: An open source FHE compiler (updated as TFHE-RS), which can simplify the use of full-state encryption (FHE).It allows the Python program to convert it to its FHE equivalent program.For developers who want to create a high -level application who accepts encryption input and generate encrypted output, Concrete is very useful.
-
TFHE-RS: TFHE’s pure RUST implementation is used to perform Bur and integer operations on encrypted data.TFHE-RS is designed for developers and researchers who want to fully control the TFHE function without having to worry about the details of the bottom layer.
-
Concrete ML: ZAMA is an open source tool for privacy protection machine learning (PPML) based on Concrete.It aims to simplify the use of data scientists for the use of omnidirectional encryption (FHE) to help them automatically convert machine learning models into homogenous equivalent models.
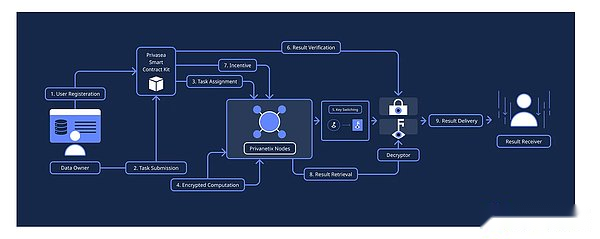
2.3 PRIVASEA workflow:
>
-
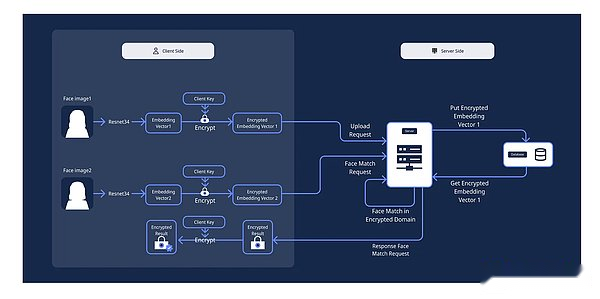
Users create accounts, set up machine learning tasks, encrypt the vectors locally through the API interface applied by machine learning, and generate the exchange key locally.
-
Users can then submit encryption tasks to Privenix network and pay service fees through blockchain.
-
The Privenix node receives and executes the encryption task in the user’s encryption domain, and then uses the user’s previous switching key to transmit the encryption result to the encryption domain of the decrypted person.
-
Once the work is completed, PrivaNetix will send the result to the decryptor and get paid
-
Next, the decryptor uses their client key to decrypt the results, and use the agent encryption (Pre) solution to send the decryption result to the network users.
-
Mining/pledge (45%)-In the assignment to the pledge node provided in the project with a complete homogeneous encryption (FHE) and other privacy services.
-
Team allocation (10%)
-
Supportr (20%)
-
Marketing and community development distribution (15 %)-This currency will be used for marketing and community development plans.
-
Reserve (6%)——The this category is mainly applicable to projects that cannot be planned, such as future regulations that need to be satisfied or licenses that need to be applied.
-
Liquidity (4%)——This liquidity is critical, because it can ensure that participants can enter or exit their positions without causing large fluctuations in prices, thereby promoting market growth.
2.4 Safety KYC case case workflow:
>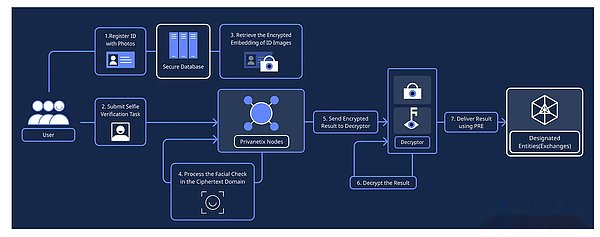
1. Register ID card with photos: Users provide ID cards, including photos.Client use feature extraction algorithm extract facial features from the ID card photo
2. Submit a selfie verification task: Users use the camera or mobile device for selfie, the client uses the same feature extraction algorithm as the ID card registration, and extracts the face features from the selfie image.
3. Reto the encryption embedding of ID image: The specified PrivaNetix node retrieves the encrypted ID -related encryption ID from the security database.
4. Handle face face check in the ciphertext: Using FHE function, the PrivaNetix node is calculated on the encrypted ID and self -timer embedded, such as calculating the distance between them.The PrivaNetix node compares the distance from the predefined threshold to determine the similarity.The result is retained in the ciphertevy.
5. Send the encrypted result to the decryrator: the PrivaNetix node will send the encrypted Burlier results to the decryrator for further processing.
6. Decryption and extraction results: The decryptor has a private key, and decrypt the received results to obtain the final check result (such as or not).
7. Result transmission: The decryptor uses proxy re -encryption (Pre) or other appropriate methods to pass the final result safely to the designated mechanism or entity that needs it.
3. github
Above we have checked some of the zama AI repository. Now let’s take a look at some proprietary partsPRIVASEA repositoryEssenceThe first thing that attracts your attention is that the last update of the PrivaseA repository was in July 2023.This may be because the current competition around the FHE and AI/ML tasks is very fierce, so the team will not release updates to maintain their development vitality.
Privasea-GeneralIt is the main PrivaseA repository with multiple open source software packages.These software packages include Hesea_lib, which is a high -level full -level encryption (FHE) library, providing developers with strong, flexible and easy -to -use security computing tools.Or Privasea-Miscellaneous, which contains source data that can be used for other Privatesea repository.
Hesea_lib-Hesea is a cutting -edge full -state encryption (FHE) library, providing developers with strong, flexible and easy -to -use security computing tools.Hesea is built with the most advanced encrypted technology and optimized high performance. It is an ideal choice for various cases.Hesea provides a variety of FHE solutions, including TFHE, CKKS, BGV, BFV, etc., and the use of encryption data can be calculated without decryption.This ensures that sensitive data is kept safe and avoids privacy leakage and security threats.
Comparison_demo-This is a demonstration using the Hesea library for ciphertext sorting.This demonstration program will encrypt the explicit sequences to be sorted to the corresponding ciphertext sequence, and sort the sequence through a comparative ciphertext sequence.Then, the program will decompose the dense text sequence and output the explicit sequence after sorting.
dinn_demo-This is a demonstration using the Hesea library for security handwriting digital recognition.It represents a privacy protection deep learning method using the TFHE encryption scheme.The main advantage of Dinn is that it has the accuracy of competitiveness while using discrete neural networks to maintain normal operational efficiency while maintaining normal operational efficiency.These networks quantitative weights and offsets reduce the complexity of the underlying calculation and simplify the initial TFHE guide program.Therefore, the same state estimation has been further improved, thereby improving efficiency.
4. Tokens
PRVA tokens are a practical tokens in the PRIVASEA AL network. They play a vital role in promoting transactions, motivating participants, and realizing chain governance.It also acts as an exchange medium, and users can access privacy AL services and unlock various functions in the ecosystem.The value of the PRVA tokens is mainly driven by the demand for network services, including machine learning to protect privacy and other AL -based functions.
Specifically, the PRVA token plays the following role in the ecosystem:
-The transaction facilitation
-Cope and reward
-Apirate and voting
-Pamel and Network Security
-The exclusive features
Token distribution:
5. Team
LinkedinCEO David JiaoHe is an experienced entrepreneur with a strong background in the development of complex systems. In 2010, he served as a software engineer in Simplight NanoElectronics, and then joined Cybercom Group.From 2015 to 2020, David served as co-founder and chief product officer of Golden Ridge Robotic AB. This is a start-up research and development company that mainly focuses on the Cyber-Physical home robot system.At the same time, he also participated in Volvo’s software development -as a system designer of Volvo, I was responsible for designing and designing the system function of vehicle configuration in the new SpA2 architecture of Volvo.In 2021, he launched Nulink to provide PRE+ZK technology for decentralized applications through API.In addition, David’s experience in Volvo enables Privasea to participate in joint projects carried out by RISE (a Swedish research institution) and Alkit Communications AB for the automotive industry.
Ting gao, LingyingChief Research Scientist-The background with deep applied mathematics and mathematics modeling: Since 2010, he has been a researcher at the Illinois Institute of Technology. Since 2015, he has served as M3’s data analysts and data scientists, and then served as Twitter’s ML engineer.Since 2021, he has served as an assistant professor of applied mathematics, random modeling, deep learning, and its application in mathematics finance
Alex (R) Gaidarski, LinkedInGrowth Manager-has rich experience in system administrators since 2006, which has made him a technical marketing personnel.Before joining Privasea, he was a member of the marketing team with Nuilink and David Jiao.
Zean Darren, community development and management, LinkedIn-With rich experience in community management, he has served as the hosts and assistants of Manta, Polyhedra, Tansi Network, and as hosts and assistants in Arcomia and Story Chain.
6. Cooperation, integration and application
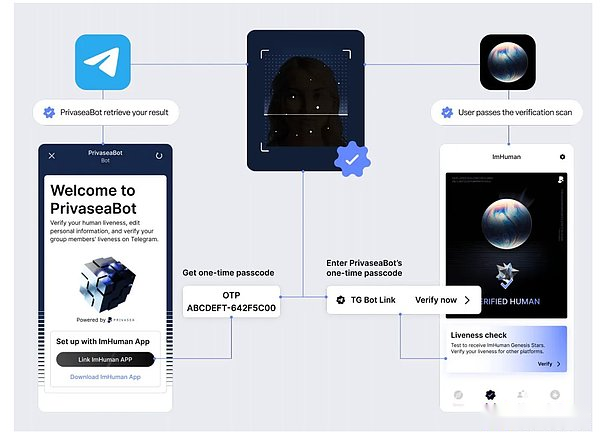
Privasea’s current main actual application is imhuman, and this application has been launched on Google Play and AppStore.It is a implementation of the POH (human certificate) technology that can confirm human identity and protect your number of violations from robots and artificial intelligence imitation.In this application, confirmation of identity through facial biometric technology is a proof of human identity through NFT.Bio -characteristic data is network through the encryption vector on the user device.Then use the user’s client key to encrypt these vectors and send them to PRIVASEA’s security network server.Privasea is currently planning to implement its POH solution in Linea, Movement, and Gate, and integrates with Telegra,/Discord/Reddit.
Example with TG robot integration:
>
>
Mind Network is the pioneer of decentralized zero trust data lake.Privasea is currently building a fine -tuning library that optimizes the core operation of completely homogenic encryption to provide high -efficiency and convenient solutions for Web2 and Web3 customers.On the other hand, Mind Network focuses on secure data -driven smart contracts and encrypted data AI.One of the key aspects of this cooperation is that Mind Network integrated the FHE data of Mind Network into the AI network of Privasea.
BNB GRIENFIELD -combine data management with decentralized finance (DEFI) potential in BNB Smart Chain (BSC).Privasea AI Network and BNB Greenfield joined forces to change the pattern of data storage and privacy.PRIVASEA’s FHE technology will achieve durable encryption of user data on the network.In addition, developers on the BNB Greenfield platform can seamlessly use encrypted data to perform calculations, covering operations such as data statistics, logical analysis, and machine learning model evaluation.Essence
Ton Network -PRIVASEA has launched Secure Livenesscheck Bot, which is a Ton Network solution to redefine user identity verification by using advanced facial recognition technology combined with the same -state encryption [FHE].
Pri-Auto is a sustainable automotive industry project. Sweden Vinnova Fordonsstrategisk Forskning Och Innovation (FFI) has chosen to provide funds in 2023.Under the PRI-Auto project, PRIVASEA will build infrastructure to create security data sources for the automotive industry, and realize data sharing between OEM, MAAS and insurance companies through intelligent access permissions.For this project, Privasea is working with Rise (a Swedish research institution) and Alkit Communications AB (a supplier providing data collection services for OEMs such as Volvo Group and Volvo Automobile).
7. Supportr
Privasea has been supported from Dewhales Capital, Binance Labs, Gate Labs, OKX Ventures, MH Ventures, K300 Ventures, QB Ventures, Crypto Times, Basic Capital, DuckDao and other supporters, as well as some business businessmen from the industry. Industry Angel (such as Zakaria (Zak) Aves and LukeSheng (from Chainlink) to get a $ 5 million investment commitment.
8. Conclusion
By solving the problem of efficiency and focusing on improving the existing algorithm, Privasea has paved the road for FHE’s widely used, ensuring that data security and privacy can coexist in this data -driven world.Their solutions allow users to use a variety of distributed computing resources provided by the blockchain, while maintaining complete control of data and models when processing AI.Today’s world is becoming more and more complicated, and the connection between Web3 and AI is getting closer.







