
Author: duncan nevada, hack VC partner; Translation: Bitchain Vision Xiaozou
The transparent encrypted ledger fundamentally changed how we look at the trust system.As the old saying says: “DON’T TRUST, Verify (Non -verification, don’t believe it)”, and transparency is just allowed us to believe it.If everything is open, any fraud can be marked.However, this transparency has been proven to be one of the factors for usability.Of course, some things should be made public, such as settlement, reserves, and reputation (maybe there are identities), but we do not want everyone’s financial conditions and health files to be made public together with personal information.
1. Privacy needs of blockchain
Privacy is a basic human right.Without privacy, there is no freedom and democracy.
Just as early the Internet needs to be encrypted (or SSL) to achieve secure e -commerce and protect user data, blockchain requires strong privacy technology to give full play to its potential.SSL allows websites to encrypt the data in transmission to ensure that sensitive information such as credit card numbers will not be intercepted by malicious actors.Similarly, the blockchain requires privacy technology to protect transaction details and interaction, while maintaining the integrity and verification of the underlying system.
Privacy protection on the blockchain is not only to protect individual users, it is essential for enterprises to adopt, data protection compliance, and unlocking new design space.No company in the world wants each employee to see the salary of others, and no company hopes that competitors can understand the most valuable customers who sort them and dig them away.In addition, some industries such as healthcare and finance have strictly regulatory requirements for data privacy. Blockchain solutions must be a feasible tool, and these requirements must be met.
2. Map of Privacy Enhancement Technology (PET)
With the development of the blockchain ecology, several key PET technology has appeared, and each PET has its own advantages and weighing balances.These technologies -zero -knowledge proof (ZK), multi -party computing (MPC), full -state encryption (FHE), and trusted execution environment (Tee) -crossing six key attributes.
-
Universal:The solution is applied to extensive use cases and calculations.
-
Combined:This technology is combined with other technologies to reduce disadvantages or unlock the easy level of design space.
-
Computing efficiency:The system executes the efficiency of calculation.
-
Network efficiency:With the increase of participants or data scale, the scalability of the system is.
-
Decentralization:The degree of distribution of security models.
-
cost:The actual cost of privacy.
Just like the scalability, security and decentralization of the blockchain, it is challenging to achieve all six attributes at the same time.However, the recent development and progress and mixing methods are breaking through the possibility of possibility, making us get closer and closer to high -performance comprehensive privacy solutions.
Now we have a map in our hands. Let’s take a look at the whole picture and explore the future prospects of these PET technology.
3. PET landscape map
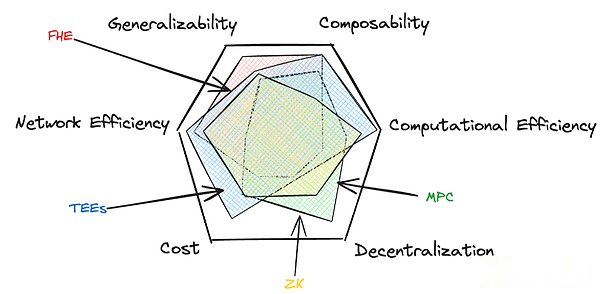
I think I need to add some definitions here.
(1) Zero knowledge certificate
Zero Knowledge (ZK) is a technology that allows verification to verify that a calculation does happen and achieve a result without disclosing the input information.
-
Universal:middle.The circuit is highly specific to the application, but it is inseparable from the hardware -based abstract layer, such as ULVATANA and IrReducible and general interpreters (such as Nil’s ZKllvm).
-
Combined:middle.It is independent of a credible Prover, but the proofer must see all the original data in the network settings.
-
Computing efficiency:middle.As the real ZK application (such as Leo Wallet) is launched, it proves that it is achieving index growth through novel deployment.With the increase of customers, we look forward to further development.
-
Network efficiency:high.Folding’s latest progress has brought great potential for parallelization.Folding is essentially a more effective method for constructing iterative proof, so its development and construction can be carried out based on the completed work.Nexus is a project worthy of attention.
-
Decentralization:middle.Theoretically, it proves that it can be generated on any hardware, but in fact, the GPU is more popular.Although hardware becomes more and more unified, at the economy level, further decentralization can be further decentralized through AVS (such as Aligned Layer).Input is privacy only when combined with other technologies (see below for details).
-
cost:middle.The initial deployment cost of circuit design and optimization is high.The operating cost is moderate, proves that the production cost is relatively high, but the verification efficiency is also high.One of the significant factor that caused this cost structure is to store storage on the Taigo, but this can be relieved by other methods, such as using data availability layers such as EIGENDA or AVS.
Take “Sand Dune” as an example: Imagine that Stilgar needs to prove to the Duke of Leto that he knows the location of a spice field, but does not want to disclose the exact location.Stilgar brought the eyes with his eyes on a fluttering machine, hovering over the spice field until the flavor of the cinnamon permeated the entire cabin, and then he returned to Arraken with Leto.Leto now knows that Stilgar can find spices, but he doesn’t know how he can get there.
(2) Multi -party calculation
Multi -party computing (MPC) means that multiple parties can calculate the results together without revealing their inputs to each other.
-
Universal:high.Given the particularity of MPC (such as secret sharing, etc.).
-
Combined:middle.MPC is safe, but the combination of combination is reduced as the complexity increases, because complexity will bring index -level network overhead.However, MPC has the ability to process privacy input from multiple users in the same calculation, which is a very common case.
-
Computing efficiency:middle.
-
Network efficiency:Low.The number of participants is rather than the must be completed.Nillion and other projects are trying to solve this problem.Erasure Coding/ Reed-Solomon Codes-or more loosely, divide the data into a piece (Shards), and then save these schks-it can also be used to reduce errors, althoughIt is not a traditional MPC technology.
-
Decentralization:high.But participants may also make a breath, endangering safety.
-
cost:high.The implementation cost is medium.Due to communication expenses and computing requirements, operating costs are high.
Taking “Sand Dunes” as an example: Considering Landsraad’s people to ensure that they have enough spice reserves, so they can help each other, but they don’t want to disclose the specific information of their personal reserves.The first one can send a message to the second one to add a large random number to their actual reserves.Then, plus the actual reserves of their actual reserves, and so on.When the first total number of the final number is received, you only need to minus the large random number they added before, and you can know the actual total spice reserves.
(3) All -in -one encryption
Full -state encryption (FHE) allows calculation of encrypted data execution without being decrypted in advance.
-
Universal:high.
-
Combined:A single user input is highly combined.It must be combined with other multi -user privacy input technology.
-
Computing efficiency:Low.However, it will be consistently optimized from the mathematical layer to the hardware layer, which will be a huge potential unlock.ZAMA and Fhenix have done a lot of outstanding jobs in this regard.
-
Network efficiency:high.
-
Decentralization:Low.Some reasons are because of calculating demand and complexity, but with the advancement of technology, the degree of decentralization of FHE may be close to the degree of decentralization of ZK.
-
cost:Very high.Due to complex encryption and strict hardware requirements, the deployment cost is high.Due to the large calculation volume, the operating cost is high.
Take “Sand Dunes” as an example: imagine a device similar to Holzman’s shield, but for numbers.You can enter digital data in this protective shield, activate it, and then give it to a Mentat.The MENTAT can be calculated without seeing the shielded numbers.After the calculation is completed, they will return the protective shield to you.Only you can restore the shield and see the calculation results.
(4) Trusty execution environment
The trusted execution environment (TEE) is a Secure Enclave or area in the computer processor. It is isolated from the rest of the system and can perform sensitive operations in it.The uniqueness of Tee is that they depend on silicon and metals, not polynomial and curves.Therefore, although they may be a powerful technology today, theoretically, due to the limitations of expensive hardware, their optimization speed should be slower.
-
Universal:middle.
-
Combined): HighEssenceBut because of the potential Side Channel Attacks, the safety is low.
-
Computing efficiency:high.The efficiency close to the server is that Nvidia’s latest H100 chipset series is equipped with Tee.
-
Network efficiency:high.
-
Decentralization:Low.But due to specific chipsets, such as Intel’s SGX, this means that it is easy to suffer bypass attacks.
-
cost:Low.If the existing Tee hardware is used, the deployment cost is low.Because it is close to native performance, the operating cost is low.
Take “Sandow” as an example: Imagine the HEIGHLLINER cabin of the Aerospace Association.Even the guild’s own pilot could not see or interfere with what happened inside during use.The pilot enters the cabin and performs the complex calculations required for folding space, and the cabin itself ensures that everything that is carried out in it is private and safe.The guild provides and maintains this cabin to ensure its safety, but they cannot see or interfere with the work of the carrier in the cabin.
4. Actual cases
Maybe we don’t need to compete with the spice giant, but only need to ensure that privilege data such as key spices maintain privileges.In our real world, some of the actual uses corresponding to each technology, such as below.
ZK is very suitable when we need to verify whether a certain process is generated.When combined with other technologies, it is an excellent privacy technology, but it will sacrifice trust alone and is more similar to compression.Usually we use it to verify that the two states are the same (that is, the L2 status of “uncomfortable” and the block header published to L1, or it proves that the user is over 18 years old and does not leak any actual personal identity information of the user).
MPC is usually used for key management, which can be a private key or a decryption key used with other technologies, but it is also used for distributed random number generation, (small) privacy computing operations and Oracle aggregation.In essence, any method that should not be colluded with each other to computing lightweight aggregation is very suitable for MPC.
When a simple general -purpose calculation is required when the computer cannot see the data (such as a credit score, a smart contract game of the Mandarin Party, or sorting transactions in the memory pool without disclosing the transaction content), FHE is a good choice.
Finally, if you are willing to trust hardware, Tee is very suitable for operations with higher complexity.For example, this is the only feasible solution for private equity models (LLM in enterprises or finance/medical care/national security institutions.The relevant advantages and disadvantages are that Tee is the only hardware -based solution. Theoretically, the speed of improvement of disadvantages should be slower than other technologies and higher costs.
5. Other solutions
Obviously, there is no perfect solution, and a technology is unlikely to grow into a perfect solution.Mixed solutions are exciting because they can use the advantages of one method to alleviate the shortcomings of another method.The following table shows that by combining different methods, you can unlock some new design space.The actual practice is completely different (for example, combining ZK and FHE may need to find the correct curve parameters, and combining MPC and ZK may need to find a certain type of setting parameters to reduce the final network RTT time.
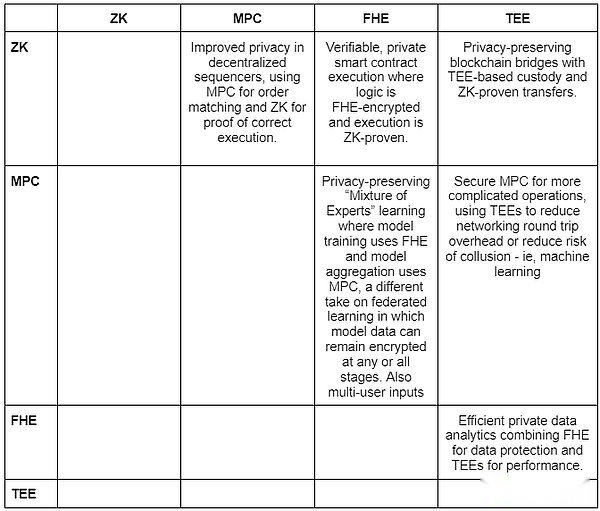
In short, high -performance general -purpose privacy solutions can unlock countless applications, which involve the life cycle, identity authentication, non -financial services, collaboration and coordination of games, governance, and fair trading life cycles.This can explain to a certain extent why we find that Nillion, LIT Protocol and ZAMA are so fascinating.
6. Conclusion
In short, we see huge potential, but we are still in the early stages of possibility exploration.Individual technologies may be almost mature to some extent, but Staking technology is still a field of exploration.PET will be tailored in this field. From the perspective of the industry, we still have a lot of things to do.







