
Source: Shenzhen Zero -time Technology
background
On February 25, 2024, we monitored a attack event on Ethereum: https://etherscan.io/tx/0xf0464 Lueberryprotocol, the loss of about 455 ETH 1.4m USD.Fortunately, the attack was intercepted by an ID of a C0FFEEBABE white hat (0XC0FFEEBABABABE5D496B2DDE509F9FA189C25CF29671 [C0Ffeebabe.eth]), and finally returned 366.5 ETH 1.2 M USD.
Blueberryprotocol is a COMPOUND FORK -based DEFI project, providing borrowing, mortgage and other services.The specific operation mode is shown below:
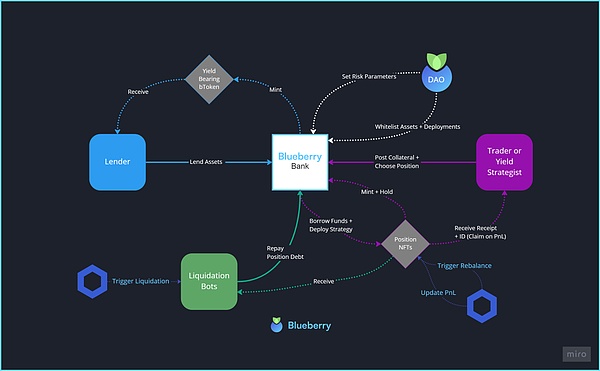
Attack analysis
The attacker first borrowed 1 WETH through lightning loan from Balancer.
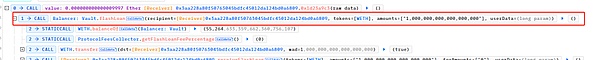
Subsequently, the attacker mortgaged 1 Weth to Blueberryprotocol and Mint made 1 BWETH.Then, the attacker used 1 BWETH mortgaged as a mortgage, and used Borrow to borrow 8616 OHM (Decimal = 9), 913262 USDC (decimal = 6), and 6.86 WBTC (decimal = 8).
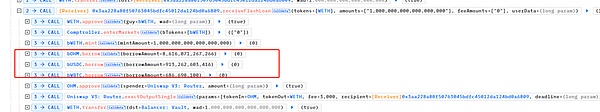
Finally, the attacker replaced the OHM, USDC, and WBTC to 457 ETH through Uniswap.
Vulnerability analysis
The root cause of the problem is that when the code processs different assets, the tail number is processed errors.The decimal of Weth is 18, OHM’s decimal is 9, USDC’s decimal is 6, and the decimal of WBTC is 8.
However, the Price Oracle of Blueberryprotocol, when processing the price of token, is scal at the price of Decimal = 18.
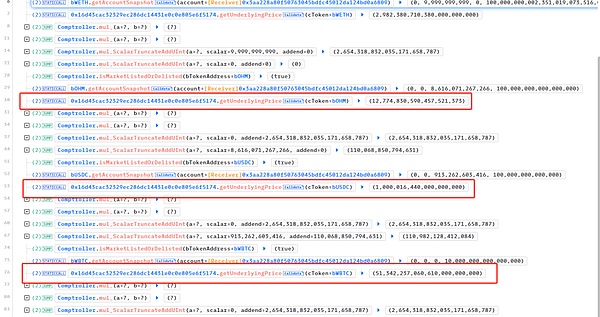
As a result, the value of OHM shrinks by 1e9, USDC value shrinks by 1e12, and WBTC value shrinks by 1E10.As a result, the attacker picked up assets worth 460 ETH through only 1 ETH mortgage.
Summarize
The vulnerability is that the project party uses the same code to handle different tokens, and does not take into account the different Decimal of different token.Asset caused a large amount of assets of Decimal, and the attacker was borrowed at a very low price as a mortgage.It is recommended that the project party conducts full audit and cross -audit for smart contracts before the contract is launched to avoid such security issues.







