Author: Zack Pokorny, Assistant Researcher at Galaxy Digital; Translation: Bitcoin Vision xiaozou
A mysterious high-powered operator passed3738sending address to39423Sent to receiving address41523stripOP_RETURNMessages, these addresses hold a total of230Thousands of Bitcoins.What does this person want?
1,introduction
This summer, an unknown operator carried out a “dust attack” on thousands of Bitcoin wallets – sending tiny amounts of Bitcoin to these wallets and embedding cryptic messages in the OP_RETURN field.The OP_RETURN function is similar to the memo field of a check, but with one key difference: its contents can be viewed on the blockchain by anyone, not just the payee.
These messages typically contain a warning in all capital letters (such as “Legal Notice”) and a link to a page on the Salomon Brothers website.The reference here is not the legendary Wall Street investment bank where Lewis Ranieri pioneered mortgage securitization in the 1980s (the institution is now part of Citigroup), but an unknown institution with the same name.The page notifies users who receive the message that their wallet “appears to be lost or abandoned” and claims that an unnamed Salomon customer has (somehow) obtained “constructive possession” of the wallet.Cornell Law School’s Legal Information Institute defines constructive possession as “the legal possession of something that is not under the direct physical control of the party… For example, a person who holds the key to a safe may have constructive possession of the contents of the box.”
Wallet owners were given a 90-day response period to either prove possession of the private keys by transferring tokens on-chain or send proof of ownership documents to Salomon Brothers.Salomon Brothers warned that those who failed to take action by the deadline risked losing their “legal rights” to their wallets.
Although the information was posted publicly on-chain for everyone to see, it didn’t gain widespread attention until early July.At the time, a long-dormant wallet belonging to an early holder transferred 80,000 Bitcoins shortly after receiving one of the messages.The dust attack subsequently became the focus of debate and speculation.
Is it a hacker group that somehow obtained the user’s private key and started looking for justification for their attacks?Worse yet, has anyone discovered a quantum vulnerability in the Bitcoin protocol?No one knew what to make of it all.
To shed light on this shrouded story, Galaxy Research conducted a detailed analysis of thousands of transactions sent by Salomon customers over the summer.As this report will reveal, the majority of attacks target P2PKH (“Pay to Public Key Hash” script) addresses, which are considered less vulnerable to quantum attacks than other address types.Salomon Brothers, for its part, claimed that its client was “not a hacker or a phisher.”Therefore, we do not believe that this information indicates a vulnerability in Bitcoin or that private keys have been stolen.
While the intent of Salomon’s clients remains elusive, our analysis shows that the campaign, while crude in some aspects, was executed through a complex maze of on-chain transactions.Given the size of this OP_RETURN campaign, the content of the message, and the notification it linked to, one reasonable explanation is that the people behind it may have attempted to pursue legal claims against non-responding wallets under the unclaimed property laws of some jurisdictions after the deadline.However, even if he obtains a favorable court ruling, it remains unclear how Solomon’s clients will take over these allegedly abandoned wallets without access to the private keys.
2, main findings
Scope and structure:
Passed in total3,738sending address to39,423Sent to receiving address41,523OP_RETURN messages.
The total number of addresses that received the message at the time the message was senthold2,334,482.52Bitcoin.
The campaign was divided into two phases: an initial test message (June 30) that did not contain a link or mention of Salomon Brothers, and a subsequent phase (July to August) in which messages containing links to the Salomon website were sent in batches.
Target image:
The vast majority of destination addresses (98.82% of all receiving message addresses) areTraditionP2PKHaddress.
The average adjusted dormancy period (i.e., the length of inactivity) of an address receiving notifications is2,171sky(approximately 5.95 years).
98.1%The informed addressBefore the dust attack, since first receiving tokensNo transfer has ever been made.
Execution process:
The first message related to Solomon contained an incorrect URL; the sender later sent a corrected version.
There is an obvious cycle pattern of “testing→batch sending→monitoring→adjustment”: test transactions are conducted before each round of main message sending; the common characteristics of the receiving wallets and the number of messages sent in each batch of activities are adjusted.
Legal recourse possibilities:
The attack’s methods, such as targeting addresses that have been dormant for longer than a certain period and setting a response grace period, are consistent with the requirements of unclaimed property laws in some U.S. states.
While Salomon’s clients have questions about the legal viability and scope of potential claims for abandoned property, the dust attack should not be dismissed as a purely behavioral experiment.
3, Who is Salomon Brothers?
Salomon Brothers in the original sense was an investment bank founded in 1910 by Arthur Solomon, Herbert Solomon and Percy Solomon.Originally a private partnership, the company went public in 1981 through a reverse merger with Fibo.Salomon Brothers, a giant in U.S. Treasury trading during its heyday, is best known for its arrogant portrayal in Michael Lewis’s book “Liar’s Poker.”
In 1997, Travelers Group, led by Sandy Weill, acquired Salomon Brothers, which at that time mainly served institutional clients, and merged it with Travelers’ retail brokerage business to form Salomon Smith Barney.The following year, Travelers Group merged with Citigroup to form Citigroup, which became the prototype of a modern “financial supermarket.”In April 2003, Citigroup discontinued the name Salomon Smith Barney and reorganized its investment banking business into Citigroup Global Markets.
In 2022, a group of people who claimed to be old employees of Salomon Brothers, including R. Adam Smith, set out to restart the investment bank several years after purchasing the trademark rights to the name.The customer who sent the OP_RETURN message on the Bitcoin network between July and August this year seems to be the reborn Salomon Brothers.
The corporate information and team information disclosed on the official website of Salomon Brothers is extremely limited.However, by using a combination of website time machine, web crawler technology and industrial and commercial registration directory query, and tracking the limited clues on the website, we discovered more details that cannot be obtained from the landing page alone.These findings include insights into corporate entities, their online footprint, and published information notices.
The company is a legal entity registered in New York. It submitted its application on June 5, 2020, and is currently registered with the New York State Government as existing.The company’s main office address is located on the 16th floor of 733 Third Avenue in Manhattan (virtual office rental services are available on this floor).C. Daniels (full name Christopher “Chip” Daniels) has been confirmed as CEO.On his LinkedIn page, Chip Daniels is listed as the executive chairman of State Stox, which appears to be affiliated with Salomon Brothers.It is worth noting that the State Stox website and the official website of Salomon Brothers adopt a similar design style, and the same Third Avenue address is displayed at the bottom of the page.Public records show the two companies were involved in a deal in which Salomon Brothers served as sole underwriter to help take a company called Ownet public.According to his LinkedIn profile, Daniels also serves as a director of Ownet.
4, Salomon Brothers website and social media
Salomon Brothers conducts online promotions and activities through its official website, LinkedIn account and X platform account.
Company official website
The website was registered on January 6, 2023, and includes the company’s service introduction, development history and many details.It is worth noting that part of the website refers to the company as “Salomon Encore”. This name only appears in the fine print of the website and does not appear in the on-chain notification.The company claims that its service scope covers investment banking/mergers and acquisitions, asset management/consulting, real estate financing and research and other fields.Except for the research button, which will jump back to the official homepage, other categories will lead to new web pages.There are many invalid buttons and expired links on the website: for example, the “Solomon Sisters” button on the homepage claims to provide “specialized services for female entrepreneurs and investors,” but the details button still jumps back to the main site; the bridge financing details link leads to the domain name registrar GoDaddy’s page.
At first glance, the transaction case button on the investment banking/M&A page looks like the company’s past performance (including financing and M&A projects), but the transactions listed all occurred decades ago, long before the company obtained the Salomon trademark.For example, Home Shopping Network acquired Ticketmaster Group equity in 1997, Fred Meyer merged with Quality Food Centers in 1999, Northrop Grumman acquired Logicon and other merger and acquisition cases; Loehmann’s went public twice in 1964 and 1996, and Abercrombie & Fitch went public in 1996 and other financing cases.The website clearly states: “These are not transactions completed by Salomon Encore and its affiliates”, but “transactions that Salomon Encore related personnel have participated in or occurred at previous institutions.”Another page on the website notes: “References to Salomon Brothers on this website are historical references unless otherwise stated.”
In addition to assisting Ownet in listing, Contemporary Salomon Brothers did not disclose other transactions involved.His LinkedIn account has posted investment invitation posts, but the specific level of participation and transaction status are unknown.
Company social media account updates
The company’s X (formerly Twitter) account has not been updated since Christmas 2023, and has mainly published research reports and holiday greetings.Its introduction claims to be “returning by popular demand” and states that Salomon Brothers was founded in 1910 and will resume operations in 2022.The account mentioned Ownet, a social media network whose parent company worked with Salomon Brothers on an initial public offering.
The LinkedIn account is also sparsely updated, but the profile contains a jump link to “salomonencore”, which redirects to the main website “salomonbros” mentioned above.The account had posted an update about sending an OP_RETURN message to a Bitcoin address, linking to an official press release issued by the company.
5, Salomon BrothersOP_RETURNWhat does the message say?
Salomon Brothers issued two public statements regarding messages sent to more than 39,400 Bitcoin addresses.The first is a press release issued on August 7 (nearly a week after the final news was sent), and the second is published on the official website of Salomon Brothers.Its homepage displays a TV news marquee-style scrolling display with the all-capital title “Solomon Client Takes Over Abandoned Wallet.” Clicking on it will jump to the “Statement on Wallet Notifications,” which involves the OP_RETURN news that received widespread attention in July and August.
The statement said the company represented a client who identified a batch of digital wallets that appeared to be abandoned and vulnerable to attack, and emphasized that the message was not sent directly by the company (the client’s identity has not been disclosed).The notice emphasized that the client was not trying to “adversely impact the crypto market,” but was taking action “at his own expense” to “reduce the risks posed by abandoned wallets.”Users who still control the private key are required to prove ownership by initiating small transactions, while those who have lost access can contact the customer through a designated form.The page also states that “customers do not claim any rights and interests in wallets that are not truly abandoned.”In addition, Salomon Brothers announced that customers have established a “Keyless Wallet Recovery Fund” aimed at returning assets to users who can prove legal ownership of inaccessible wallets. The fund will be managed by Salomon Brothers, with specific details to be announced in a few months.
This is not the first time the website has made announcements about on-chain news.Between July 9 (a week after the first message was sent) and August 5, the same link led to another announcement that was retroactively available through the Internet Archive.The announcement is more informal in tone, using an FAQ format rather than a legal statement, and qualitatively defines abandoned wallets and explains their risks and customer objectives (consistent with the current announcement).It is worth noting that this early announcement responded to media speculation about on-chain messages sent by its customers: “We regret that the information provided by Salomon Brothers has not been included in the reports to date. Some unsubstantiated reports have claimed that customers are ‘hackers’ (implying malicious intent) or conducted phishing attacks targeting specific wallets – such accusations are untrue.”
The press release on August 7 basically restated the content of the website announcement from the perspective of the risks of abandoned wallets and how users can prove ownership.The key detail is the statement “provide wallet owners with at least a 90-day response period.”While most wallets have at least a 90-day response period since receiving the message, 3,203 addresses received no more than 88.4 days of notification based on on-chain transaction timestamps.This detail will be spelled out in the Chain Analysis chapter – this time lag will be critical if the client does plan to take legal action after the notice period has expired.
passOP_RETURNLink content for message distribution
Salomon Brothers customers distributed two types of links with different functions through the OP_RETURN message. Neither link can be directly accessed through the company’s website homepage.
Both pages state that Salomon Brothers customers have sent notifications to a series of suspected “abandoned” Bitcoin wallet addresses, advising wallet owners to contact Salomon Brothers and/or perform cryptographic ownership verification via signed transactions.The notice warns that if the address owner fails to respond before the specified deadline, his address will be considered abandoned and the customer may take remedial measures including claiming ownership of the relevant currency through “constructive possession”.It is important to note that although the two notices have different names (labeled “Legal Notice” and “Owner Notice” respectively) and have different deadlines (the owner notice deadline is October 10 and the legal notice deadline is November 5), the content and wording are exactly the same.This operation used multiple links and different notification titles, most likely to track the 90-day response window of message recipients (since the notifications were sent over a one-month period).
A contact form at the bottom of the notice page allows users claiming to have “details and supporting documentation of a valid claim of ownership” to contact Salomon Brothers directly and indicate that the individual or his or her representative may use this form to remain anonymous.It’s worth noting that the form requires submitters to fill in geographic location information (country, state and zip code or province), and these fields are marked with an asterisk next to them to indicate they are required.
6,OP_RETURNWhat is it?
OP_RETURN is an opcode (i.e. instruction) for Bitcoin Script that allows users to embed up to 80 bytes of arbitrary data in transactions.Although the funds associated with the OP_RETURN output cannot be spent (and therefore will not be added to the “unspent transaction output set”), the data payload is permanently recorded on the blockchain and broadcast to the entire network.This makes OP_RETURN a “public bulletin board” on the Bitcoin network.Its uses cover a variety of scenarios such as homogeneous token protocols (such as Runes), timestamps and even spam messages.Because OP_RETURN has both low cost and permanent characteristics, it is often used for on-chain messaging between addresses.
7, Salomon customer dust attack range
The client campaign was divided into two phases: the first messages did not mention Salomon Brothers, and subsequent messages included links to the company’s website.The chain data strongly indicates that the two sending subjects are the same entity.The first messages can be considered a test run for Phase 2, which is broader and more thoroughly implemented.Much of the social media discussion focused on the second batch of messages (specifically the “Notice to Owners…”), which was received by the ancient whale who liquidated Bitcoin in mid-July.Few observers at the time noticed the early linkless messages and subsequent messages pointing to Solomon’s website.The lack of background information may be the main reason for widespread panic interpretations (such as “Bitcoin is broken by quantum computing”).
The message content and some of its details are shown in the table below.

8, attack details and timeline
We sort out the important events related to the Salomon Brothers dust news in chronological order, as well as key high-level details related to the two attacks.
(1) specific details
This operation involved 3,738 independent sending addresses and 39,423 receiving addresses (at least 5 of which may be controlled by the dust attack perpetrators themselves).The two sending addresses of the Solomon message appear in the receiving address list at the same time, indicating that the operator also implemented a dust attack on its own wallet.This activity shows a high degree of complexity at both the funding organization and dust distribution levels, and mainly targets addresses with one of the following three characteristics:
P2PKH address (earlier address type);
Addresses that have received tokens but never transferred them out (38,754 out of 39,423 addresses);
Addresses with an average dormancy time of 1,890 days.
It is worth noting that the complete visible transaction history of 5,097 addresses only includes receiving messages related to Salomon Brothers; if these addresses are excluded, the average dormancy time of the remaining 34,326 target addresses is 2,171 days, of which the number of target addresses that have received tokens but never transferred them is 33,657.The oldest address has been dormant for 5,991 days, the latest address has been dormant for 58 days, and 34,307 addresses have been dormant for at least three years.Overall, dust attack perpetrators paid at least0.49831883 BTChandling fee(approximately $60,246, based on October 7 exchange rate), spent on OP_RETURN messages0.22768359 BTCDust Tokens (approximately $27,516.29) and at the end of the eventRecycled at least0.00878853 BTCremaining balance(Approximately $1,062.52).
This entity built a complex fund flow network: before initiating a dust transaction, the tokens were dispersed to thousands of addresses, circulated repeatedly among subsequent addresses for multiple message types, and the change output was manually distributed instead of returned to the sending wallet (“change” in Bitcoin refers to the remaining part of the input amount returned to the sender or the designated address after the transaction is completed).This mode of operation initially increases the difficulty of tracking.This activity, which is both complex (covering 41,523 OP_RETURN messages) and large-scale, requires an in-depth understanding of the Bitcoin protocol and a large amount of preparation and resource investment.
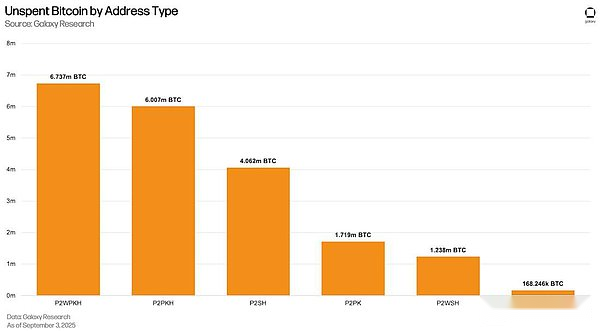
Destination address type:
Pay-to-Public-Key-Hash (P2PKH) addresses are the main targets in this round of messaging activities, accounting for 98.82% of the total addresses receiving notifications.Why is it important to emphasize the type of address receiving the message?Because certain Bitcoin address types are considered more vulnerable to emerging technology attacks than others, Salomon Brothers’ official communication regarding the OP_RETURN message also hinted at this risk: “Rogue states and criminal organizations with deep resources pose a credible threat to hackers of abandoned digital wallet assets.””Old encryption protocols are vulnerable to new technologies, which means malicious actors could illegally gain access to abandoned wallets – because these wallets cannot be upgraded to more secure versions.”This statement seems to point to the possible quantum computing threat to Bitcoin, which has become an important topic of community discussion and debate this year.
Quantum computing is a computing method that uses quantum mechanical principles (such as superposition and entangled states) to process information. The computing power for specific problems can exponentially exceed that of classical computers.At present, the risk remains theoretical: some experts believe that practical quantum computers may appear in the late 2020s or early 2030s, continue to increase computing power in the 2030s, and achieve full reliability in the 2040s or later.
One of the concerns about attacks on Bitcoin by quantum computing or related technologies is the technology’s potential ability to match public and private key pairs, which would allow a theoretical attacker to gain unauthorized control of user funds.Pay-to-Public-Key (P2PK) addresses (used in Bitcoin’s earliest blocks) embed the original public key directly into the output script, making it a script type more vulnerable to theoretical quantum or similar attacks than other address types.In theory, quantum computers or other technologies could derive private keys directly from exposed public keys and hijack funds.In contrast, P2PKH addresses (the main target of this round of attacks) and subsequent address formats lock coins to the hash of the public key (i.e., the result of cryptographic obfuscation), which means that the original public key is only exposed after the address spends the coins.Therefore, for an attacker to exploit these addresses, the victim would have to have spent tokens before this hypothetical attack occurred and reused the spending address.As mentioned before, the vast majority of target addresses seem to never transfer funds, so their public keys are never exposed and are theoretically less vulnerable to attacks than P2PK addresses.
Our analysis found no evidence that the addresses receiving the Salomon Brothers dust messages in this round of activity were of the P2PK type.All identified targets are of late address type, primarily P2PKH.While a P2PK output dust attack is technically possible by sending tokens directly to the original public key, we have found no evidence of Salomon Brothers clients carrying out such an operation.In practice, original P2PK usage has been largely phased out: modern Bitcoin software no longer supports the format, and neither wallets nor exchange front-ends allow users to paste bare public keys as receiving addresses.Galaxy Research tried to send BTC to the P2PK output through centralized and decentralized front-ends but failed. In the end, it could only verify the conclusion by manually constructing a partially signed Bitcoin transaction (PSBT) containing the original P2PK output and broadcasting it independently.This operation requires custom script assembly because the standard interface forces the use of modern address formats.The difficulty of the experiment highlights that P2PK has been completely deprecated – although sending funds to such addresses is still technically possible.This raises an important question: If Salomon’s client stated that the goal was to protect abandoned addresses from technical exploitation, why did it ignore arguably the most vulnerable address type and most likely to be abandoned (P2PK), and instead send messages to a less vulnerable format?
As of September 2, P2PK addresses held 1.719 million BTC, accounting for 8.63% of the circulating supply and 8.18% of the maximum supply.This huge amount of BTC is widely considered to be the most vulnerable to attacks when quantum computing is implemented, but according to our observation, Salomon customers did not send notifications to any such address.
(2) Fund preparation and testing of important addresses——4moon7Solstice6moontwenty fourday
The earliest traces of the two-stage attack date back to April 7, when a funds transaction arrived at a Bitcoin addressbc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99.As shown in the following analysis, this address has become the core hub of non-Solomon activities and Solomon activities: it not only serves as the earliest source of funds for dust addresses, but also serves as a dust sending address. It is also the target address for most dust addresses to collect the remaining balance after sending OP_RETURN messages.Before the full-scale operation began, the address was used on June 24 to send a transaction containing the following message: “This is an 80-byte OP_RETURN test message and must be accurate.”The next day, the address received two further OP_RETURN messages “MESSAGE_1” and “MESSAGE_2”.Together, these messages indicate that the Dust attack entity is testing Bitcoin’s OP_RETURN function in preparation for large-scale activity.
First test transaction reveals key addressbc1qgh3jg9pqrjyawwernal2u7kuhezrxelgp72z0t——This address received funds through bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99 test funds as a manually allocated change address.bc1qgh3jg9pqrjyawwernal2u7kuhezrxelgp72z0t subsequently becamebc1qfefxhstqphwx6rkkxwlup9uufahx0enwm2x5adThe fund source address (this address participates in non-Solomon activities and providesbc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lhFunding – the latter is another important address that funds the Dust address and connects the two campaigns), while also funding an additional 180 addresses that send non-Solomon messages.Therefore, bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99 plays a gateway role: both providing funds to addresses in non-Solomon activities, and as a direct source of funds for Solomon-related activities.
(3) No link or Solomon associated message——6moon30day
Immediately following these test transactions, the groundwork of the first round of large-scale dust activity appeared through two notices: 1) “Not abandoned? Please initiate on-chain transaction proof through the private key before September 30th”; 2) “Legal notice: We have taken over the wallet and its contents.”These messages appeared on June 25 and circulated among random combinations of the same four addresses. The complete activity began on June 30 between Bitcoin network blocks 903447 and 903448.In the initial transaction on June 25,bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99Plays a central role: 1) sending a “not discarded?” message to itself; 2) sendingbc1qkq47hh2xv0ehvh44ec9z6pvy2856m5w66a3gw8(who provided funds the day before) sends a “Legal Notice” message; 3) receives the same “Legal Notice” message from the same address.The campaign on June 30 was subsequently expanded to an additional 90 addresses (covering two types of messages), 87 of which would subsequently receive communications related to Salomon Brothers.The group of addresses that received these messages included an ancient whale—whose involvement sparked widespread concern about the event.In other words, the address associated with the whale received two types of dust attacks with non-Solomon Brothers messages as early as June 30.
(4) The first Solomon-related message is sent——7moon2day
On July 2, the Dust attack entity sent a message related to Salomon Brothers for the first time after the June 30 event: “Notice to owner…”.This marks the first appearance of the three main Solomon message types that month.Similar to previous non-Solomon activities,bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99Appears in test transaction (this transaction is at block height903659, only 15 blocks away from the main event).Crucially, this test comes frombc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lhaddress, which has dual characteristics: 1) it was used for “abandoned” message sending on June 30; 2) it was funded by an address that participated in the June 30 dust event.also,bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lhandbc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99Fund multiple addresses sending Solomon-related messages.This overlap strongly suggests a direct connection between the two campaigns.
The reuse of addresses from earlier messaging stages, as well as the provision of test funds for Salomon Brothers operations from addresses involved in non-Solomon activity, may be operational oversights.These actions left conclusive evidence that the non-Solomon messages and the Solomon Brothers-related messages were actually coordinated and continuous actions carried out by the same subject.
More importantly, the link provided in the message failed because it contained an underscore instead of a hyphen (the dust entity may have accidentally hit the shift key when inserting the hyphen).Anyone trying to access the page will receive a 404 error and a “File not found” prompt.In addition, 20 addresses (excluding addresses potentially controlled by Dust entities) held a total of 106,602.06 BTC balances at the time of receiving the incorrect link, and these addresses either never received the post-correction message or had transferred tokens before the correction notification was sent.This distinction is critical: if a dust entity attempts to assert legal rights over so-called abandoned addresses, this particular group of addresses may not be legally notified.This address group includes the ancient whale that liquidated 80,000 BTC—which means that even if the whale sees the message, there is no accessible web page at all.
(5) correct errors——7moon9Solstice7moon14day
The whale’s behavior of transferring tokens on July 4th attracted widespread attention, and some people believed that there was a vulnerability in Bitcoin or at least that the P2PKH address type was risky.Discussions continued when whales began dumping tokens in mid-month.Around this time (July 9), the Dust attack entity began sending messages containing corrected URLs on a large scale.The campaign for this particular URL was split into two main waves: the first on July 9, and the second on July 13-14 – each wave of messages contained updated links but with slightly different wording.
Similar to the first three batches of messages, two obvious test transactions appeared on July 8 (i.e., a few hours before the first wave of correction messages were sent): the first test only contained an update link without additional text, and the second test contained a complete update message (with the corrected URL indicated).The two tests were sent in different blocks. The first one was 73 blocks in advance from the start of the correction notification activity, and the second one was 27 blocks in advance.
It is worth noting that the test transaction that only received the updated URL had the dual characteristics of 1) being funded by a manually updated change output from a transaction containing the old version of the wrong link message; 2) itself containing a manually inserted change output to the address bc1q2dskr0y97vzlpvkhr44tagdh906w48y6mu29mf (This address subsequently cleared its balance via an OP_RETURN message that may have a German spelling error, which translated to “Thank you for giving birth to me. Now you will be rewarded with real money”).The funding transaction occurred on July 8, five days after the “Webpage Correction” message campaign ended (the old link was last sent on July 3, and the test was received on July 8).The transaction also contains the receiving addressbc1qmak4853pysqmqlvmdcs3hwpz928dqqc5v6gnzw, that address then becomes the recipient of a link-only test transaction.This address also received an abnormal OP_RETURN message with the content “This wallet will be deleted in October 2025” on July 8, further indicating that it is an experimental address of the Dust Attack entity.It is worth noting that this address initially received 0.81162432 BTC funds on November 28, 2023, and most of the funds were not fully transferred out until July 30 (after receiving multiple messages from the Salomon Brothers dust sender).
Of the 1,940 addresses that received the wrong link, the majority (1,919) also received the corrected notification (another 285 addresses did not receive the original wrong link but received the corrected notification, which may be an operational error by the dust attack entity).It is worth noting thatAddresses that received the invalid owner notification link but had transferred their tokens before the correction notification was sent did not receive the correction link notification.; This indicates that the Dust attack entity is monitoring the address from which it sent the original notification and ensuring that messages are not re-delivered (this may be intentional, or because the filter applied to the target address excludes blank or recently active addresses).
The second round of dust attacks with updated links was launched on July 13, using the message format: “Notification to Owners…”.There are also obvious test transactions in this round of attacks: as early as two days before the main body of the activity (July 11),bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99The message was sent to the address.This message was sent to a total of 3,204 addresses, none of which received the original incorrect link or the “Webpage Correction” message.In addition to test transaction recipients,All addresses in this groupDeadline for link-based associations (October 10, 2025)None are complete90days notice period: The address that received the dust on July 13 was only given about 88.4 days of notification period, and the recipient on July 14 was only given about 87.5 days of notification period (from the time of confirmation on the OP_RETURN transaction chain).This detail is crucial because the written notice accompanying the message claims to give the recipient at least 90 days to respond.These addresses held a combined 251,606.5217 BTC at the time of receiving the notification.It is worth noting that 107 of the addresses that received this message did not have any traces of activity other than receiving behavior – these addresses may be falsifying the scale of the activity by increasing the number of addresses receiving messages, creating the illusion that there are a large number of vulnerable addresses.
The whale’s move of tokens continued to make headlines until July 25, a timeline that coincides with the third (and final) version of the Salomon Brothers message sent on July 23.The message reads: “Legal Notice to Wallet Owners: Please visit the webpage…”.Consistent with the previous pattern, obvious test transactions appeared in the first 22 blocks of the activity.It is worth noting that none of the 33,987 addresses that received the message had received any messages sent in June or July.This message, the largest in terms of number of recipients, was sent in two separate batches: the first between July 23 and 24, and the second between July 28 and August 4.Among them, 6,000 messages were sent from July 23 to 24; 27,987 messages were sent from July 29 to August 1; and a single message was sent on August 4.
Key differences between the “Legal Notice” message and all previous messages include the large number of target addresses, the long duration of the campaign, and the small average balance of the target addresses.The message was sent to 33,987 addresses over 13 days, its duration was 2.17 times longer than the next largest campaign, and it had 6.28 times more recipients than the next largest campaign.In addition, the average balance of the target address of this type of message (1.37 BTC) is significantly smaller than other types: the average balance of the “owner-notification” category address is 400.52 BTC, the “owner-notification” category is 980.52 BTC, and the target address of the “abandonment” and “takeover” category messages both reach 8,400 BTC.
Interestingly, 4,990 of the addresses that received this final notification had no transaction history other than receiving this OP_RETURN message.This phenomenon also exists in the “owner-notification” message, which may be deliberately done to inflate the scale of the activity.
(6) closing stage
When the dust attack entity gradually terminates various message activities, it will withdraw the remaining funds to its own address in batches to clear the address used to send a specific OP_RETURN message set.In some cases, a transaction that clears the active address of a certain message also becomes a source of funds for sending new messages to a new address.Presumably the entity added all these jumps in order to mask the connection to previous messages, ensuring that the owner of the address attacked by the dust could not easily identify the connection between the different sets of messages through a block explorer.Supporting this interpretation is the fact that of the 3,738 addresses used to send messages, 3,734 addresses delivered only one message type, while the four addresses that participated in multiple message types all appeared in apparent test transactions.
addressbc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99Acts as an intermediary in multiple scenarios to circulate funds between addresses with adjacent message activities.In addition, the addressbc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lhServes as a gateway address to redeploy remaining funds from non-Solomon activity to the first batch of Solomon-related messages.When the use of the address is completely terminated, the remaining BTC recovered through the clearing operation are sent to a new address that is not associated with the OP_RETURN message.Some transactions are large and costly, with a single transaction requiring up to 68.2kvb (kilovirtual bytes) of data and paying a handling fee of up to US$1,300.
(7) clue association
Two specific addresses strongly suggest that the entities behind the Solomon-related activity were likely also the operators of earlier non-Solomon activity—bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99andbc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh.As the earliest news of the testing foreshadowed, the same addresses that pioneered the initial experiments have reappeared as key bridges between non-Solomon and Solomon activities.
The covert connection between the two campaigns stems from the three following characteristics of the two addresses: 1) apparently conducting test dust attacks on each other during the Solomon brand campaign; 2) each sending at least one transaction containing non-Solomon messages; and 3) jointly funding the addresses used in the Solomon-related campaign.Additionally, bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh is provided bybc1qfefxhstqphwx6rkkxwlup9uufahx0enwm2x5adwas funded (the address was used to test the June 30 message set), which in turn was funded by bc1qgh3jg9pqrjyawwernal2u7kuhezrxelgp72z0t (the address itself was funded as change output by bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99).
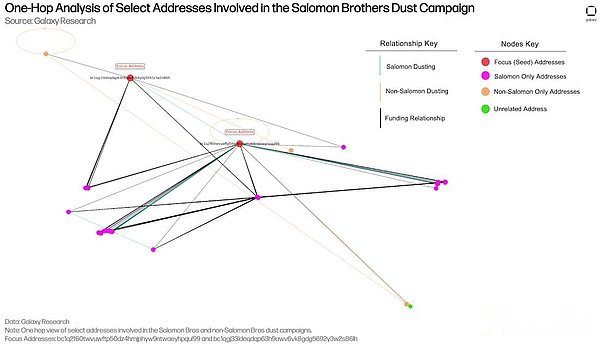
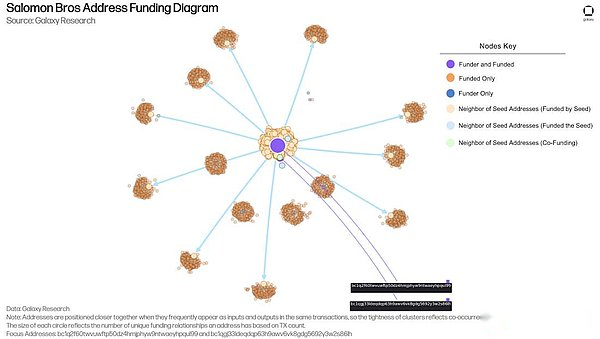
The image below is a graph visualization created from single-hop network analysis.This analysis maps all addresses directly connected to the seed address (labeled “Focus Address”), and the data source includes both Salomon Brothers-related capital flows, message flows, and non-Solomon message flows.The arrangement of nodes and edges in the graph is determined by the Kamada-Kawai layout algorithm, which optimizes spacing to bring more closely connected nodes closer to each other and minimize line intersections to enhance readability – but in dense areas it may cause nodes to overlap, making visual counting difficult.
Contains two relationship types:
blackFund flow(Line): Represents a fund supply transaction between addresses (e.g. address X provides funds to address Y).
Orange and green two colorsdust attack(Line): Represents dust messaging (e.g. address A performs a dust attack on address B).Color distinguishes activity types: cyan is Solomon-related activities, and orange is non-Solomon activities.
In addition, the self-cyclic relationship of an address performing a dust attack on itself is retained in the analysis and is represented by an arc returning to the same node (as shown in the figure for a focus address).
The visual graph shows that the two seed addresses are directly connected through the Solomon Brothers related message activities, and each has implemented dust attacks on addresses not in the Solomon Brothers activity.The two also provided funds for addresses that were subsequently used for Salomon Brothers activities, creating an overlap between the flow of funds and the Dust attack.It is particularly noteworthy that bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99 had dusted itself in the initial message, which appears as a self-looping structure in the middle of the chart.
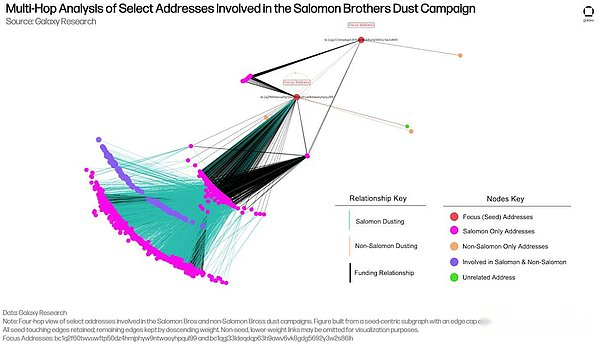
From a macro perspective, it can be clearly seen: Addressbc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99andbc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lhBoth fund and send messages to active addresses in Solomon and non-Solomon campaigns.The address bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99 played an important role in the preparation of funds for the Salomon Brothers active address, serving as an input address for more than 750 such address funding transactions.The chart below highlights the breadth of addresses that were funded through transactions from this address, and how these addresses further funded other addresses involved in Salomon Brothers-linked activity.It is worth noting that the two focus addresses also provided initial capital flows to the earliest wallets in the Salomon Brothers activity, enabling them to have operational capabilities and promote the subsequent expansion of the activity.
What is particularly critical is that there was a transaction that simultaneously funded 51 output addresses by two addresses connecting the two activities. These output addresses were subsequently used to execute and further fund the Solomon Brothers activities.The remaining funds recovered from non-Solomon messages were distributed in this transaction after being funneled through bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh – a flow of funds explained in detail below.
The image below further highlights the importance of these two addresses in funding addresses used in the Salomon Brothers messaging campaign.Unlike traditional edge plots, this visualization relies on spatial closeness rather than visible links: clusters form when specific addresses co-occur in the same funding transaction.Since Bitcoin transactions can involve multiple inputs and multiple outputs, this diagram captures joint participation relationships in capital flows rather than exclusive one-to-one capital relationships.Therefore, a seed address should be interpreted as a participating core hub rather than the unique point of origin for every funded address in its cluster.
This figure shows that the target address is at the core of the funding cluster and directly or indirectly touches most of the dust attack addresses in the Salomon Brothers activity.They also serve as funding co-participants to other addresses (which act as secondary hubs), each radiating out independent clusters of funding recipients (highlighted by a hub-and-spoke structure built around a core cluster).This model emphasizes that the target address is not only a core participant itself, but also closely connected to other influential funding providers, thus reinforcing their key role in the Salomon Brothers message funding network.
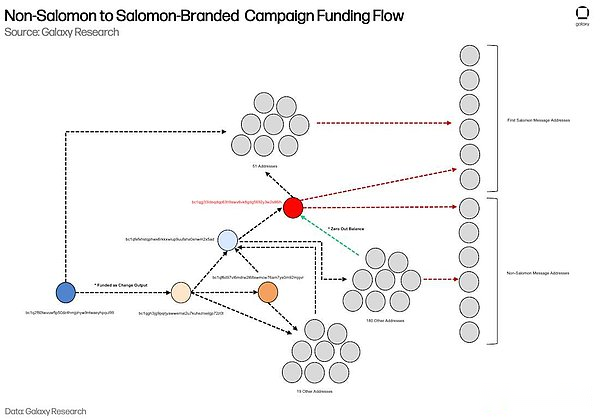
Finally, a key flow of funds confirmed the connection between the two activities.addressbc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lhIt plays a dual role: it is both a fund collection address for sending non-Solomon message addresses, and a fund source for sending the first round of Solomon-related message addresses.The figure below visually demonstrates this capital flow, which is simplified compared to the previous complex diagram to highlight the role bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh plays in connecting non-Solomon and Salomon brand activities.
The key part of this funding flow began at 16:00:35 Beijing time on June 30 (EST), with bc1qfefxhstqphwx6rkkxwlup9uufahx0enwm2x5ad providing funds to 181 addresses, including bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh.These 181 addresses were subsequently used to send non-Solomon messages.After the non-Solomon messages were sent, these addresses zeroed out their remaining balances to bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh at 21:23:02 on June 30, 2025 (approximately three hours after the last non-Solomon branded message was sent).Two days later, the address bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh, together with bc1q2f60twvuwftp50dz4hmjphyw9ntwaeyhpqul99, contributed funds to 51 addresses that were subsequently used in the first round of Solomon campaigns (i.e., the campaign containing the faulty link).This indicates that bc1qgj33ldeqdqp63h9awv6vk8gdg5692y3w2s86lh is a gateway hub that facilitates the flow of funds between the two events.
(8) Overall analysis of the impact of dust attacks
The dust attack entity sent a total of messages to 39,418 independent addresses that we determined were not under its control, and these addresses collectively held a maximum of 2,334,482.52 BTC.
Since the attacker sent multiple messages to some addresses, this statistic uses the maximum balance of each independent address when receiving any message for superposition calculation.All addresses that we identified as belonging to the dust attack entity itself have been excluded from this analysis.
One of the purposes of the dust attack activity is to observe whether users will transfer tokens as a result.So how effective is the attacking entity’s success in prompting users to take action?The following analysis data is as of 8:30 a.m. ET on September 29.
6moon30Sent on day“abandoned“and“take over“information:
These two types of messages were sent to 94 independent addresses, 4 of which we identified as test transactions sent by the attacking entity.During this event and the first round of Solomon message sending, no token transfer occurred to addresses that were not suspected to belong to attackers, indicating that the success rate of the June 30 message was 0%.The total holdings of the targeted wallets at the time these messages were sent were 789,565 BTC.
Salomon Brothers news analysis:
Analysis of Solomon-related messages is slightly more complicated because there are three message categories and in some cases are sent to different combinations of the same address.The following data analyzes the success rate of Solomon attacks, taking into account unique combinations of message types and dust addresses.
7moon2Wrong link sent
The first Salomon-branded message with the incorrect link was sent to1,939independent address(Excluding addresses that may be controlled by dust attack entities), the nominal holdings of these addresses are1,902,210.5 BTC.in10addressesBefore the correction notice is sent on July 8Transferred out86,161.15 BTC.This batch of transferred addresses includes the ancient whale that controls 8 of the addresses and transferred 80,009.44 BTC.Calculate the success rate of the message based on the number of addresses0.52%,press dustBTCThe value is calculated as4.53%.This statistic assumes that the wallet owner took action after seeing the message, but subsequent analysis suggests that at least some of the transfer behavior may be due to chance.
7moon9Hiyo7moon13Correction link message sent on
The correction link was sent in two separate batches of messages: one marked as a correction message and sent to addresses that had previously received the incorrect link (and some addresses that had not received it); the other was sent to a completely new address group.A distinction must be made between these two types of messages to assess the specific success rate of such messages.
After receiving the correction notification, a total of 109 addresses (excluding known dust attack addresses) transferred 55,161.62 BTC.The specific breakdown is as follows:
share32address forwarding42,510.35 BTC, these addresses received both the correction notification and the original Solomon notification but had not previously taken action.This batch of addressesTotal holdings1,795,607.63 BTC(involving1,918address), the success rate is calculated based on the number of addresses as1.67%, calculated based on the value of BTC held2.37%.One of the addresses only transferred a small amount of BTC after receiving the correction notification, and currently still holds 1,105.13 BTC; the other address retains 0.1 BTC.
share8address forwarding2,714.12 BTC, these addresses only receive correction notifications and not original notifications.This batch of addressesTotal holdings118,489.25 BTC(involving284address), the success rate is calculated based on the number of addresses as2.82%, calculated based on the value of BTC held2.29%.One of the addresses only transferred a small amount of BTC after receiving the message, and currently still holds 424.59 BTC.
share69address forwarding9,937.13 BTC, these addresses received the correction link as new notification objects.This batch of addressesTotal holdings251,606.54 BTC(involving3,203address), the success rate is calculated based on the number of addresses as2.15%, calculated based on the value of BTC held3.95%.However, these addresses did not receive the full 90-day grace period promised by the notification (message receipt time was July 13-14, and the deadline was October 10).A wrong notification timeframe could shield these tokens from any legal recourse.
Overall, the success rate of this correction to the linked messageCalculated by the number of addresses2.02%,according toBTCValue calculated as2.55%.
7moontwenty threeSolstice8moon4Sent on day“legal notice“information
Evaluating the success rate of a “Legal Notice” message is straightforward because the address group for its dust attack has not received any previous Solomon or non-Solomon messages.exist33,986addresses, there are3addresses were transferred114.99 BTC(The total holdings of this group of addresses is46,693.66 BTC).Calculate the success rate based on the number of addresses0.009%, calculated in BTC value as0.25%.The only addresses in this group that transferred tokens had their balances cleared to zero.
Overall impact:
After the dust attack event is over,share122Addresses transferred out cumulatively141,437.76 BTC.Assuming that the total value of the addresses affected by the dust attack is 2,334,482.52 BTC, calculated based on the BTC balance6.06%Transfer occurs, calculated based on the number of addresses0.31%A token transfer occurs.After excluding addresses that transferred tokens but retained non-zero balances,still valuable2,188,604.9 BTCof dust attack balance (equivalent to the circulating supply10.98%, the maximum supply of10.42%) no transfer occurred, and may therefore face legal follow-up actions triggered by these messages.Note: These values only count on-chain token movement and do not include wallets that may have contacted Salomon Brothers via the notification link form.
If further exclusions do not obtain complete90addresses with a grace period of 3 days, addresses that only receive initial error notifications, and addresses that have been dormant for less than three years(Important deadlines in the legal context of abandoned and unclaimed property),Then there are approximately1,920,124.4 BTCPotential legal recourse that may face notification.This is equivalent tocirculating supply9.64%, the maximum supply (2100Thousands of pieces)9.14%.
The transfer of tokens after receiving the message could be purely coincidental:
There is evidence that some addresses transferring tokens following the dust attack were purely coincidental and their owners may have never seen the message.A case in point is address 16P6cMXdmiiZR5d4L5aa793HwWZ5MomMKu: it transferred 1,219.99 BTC reserves 80 minutes before receiving the Solomon message.This suggests that the Dust attack entity may have compiled the batch of addresses in advance before sending the message – during which tokens were transferred to that specific address.The overall active whale activity on the chain over the past few months further supports the interpretation that these token transfers are purely coincidental.
9, What are the real goals of Salomon’s customers?
According to a statement on Salomon Brothers’ website, its clients are engaging in acts of altruism.The company stated that “our clients do not knowingly take any actions that adversely affect the crypto market” and that it “claims no interest in wallets that are not actually abandoned.”Solomon claims that the client also intends to create a “keyless wallet recovery fund to assist those who have lost access to their wallets but can prove legal ownership.”
It’s possible that Salomon clients are simply trying to move abandoned tokens over to government custody in order to protect the network from hostile entities (protecting the network is a goal clearly stated in its multiple communications).However, this in itself will not mitigate such risks: nationalized wallets are just as vulnerable as private wallets if existing encryption protections are breached; if the government sells these tokens, they could flow back into the market and end up in the very custody arrangements that customers claim to be trying to protect against.But customers may believe that once the token is under government regulation, malicious entities will be less willing to attack even if they have the ability to do so.
But another, more pessimistic interpretation cannot be ruled out either.Consider the following factors:
There are contradictions between Salomon Brothers’ public statements and on-chain notifications.The company’s public statements frame customer behavior as altruistic, emphasizing that the campaign is intended to protect the network and holders who lose access to their tokens.But these assurances are difficult to reconcile with the wording of the notice itself, which claims that the customer has acquired “constructive possession” of the receiving address and warns that failure to act could result in “loss of all right, title and interest.”Solomon sent mixed signals: In the most accessible communications, customers are portrayed as benevolent protectors; but in the fine print, the notice reserves the right to claim ownership of the tokens that customers may not have access to (unless they have private keys or a quantum computer, both of which we consider extremely unlikely).This contradiction raises the question: If the real goal is to protect the network from the threat of technological vulnerabilities, why assert personal possession?
Characteristic portrait of the target address.Despite Solomon’s allusions to quantum risks, its clients bypassed the most vulnerable address type (P2PK) and instead focused on P2PKH wallets that had been dormant for nearly six years without ever transferring tokens—significantly exceeding the three-year dormancy threshold set out in multiple states’ digital asset abandoned property regulations (as detailed below).
90days deadline.This echoes the 60 to 120 day notice window common in unclaimed property laws.
Customer’s precision operation capabilities.As mentioned above, the operator behind the message appears to have a deep understanding of Bitcoin’s technical architecture and social dynamics (the notice mentions the network’s quantum fragility, a long-standing niche topic in the Bitcoin community).The combination of technical capabilities and social insights gives clients the extraordinary ability to both roll out on-chain actions at scale (sending messages to nearly 40,000 addresses) and to frame message content by leveraging community fears and social tensions.This makes the event more of an opinion-shaping and dormant holder pressure exercise than a public service announcement.
Behavioral test mode.The client did not adopt a single method of sending notifications, but started on a small scale and continued to expand the scope of operations within a month as public attention increased.If the intention is to warn Bitcoin users of an impending threat, there is no reason to send out the leak in batches and gradually increase coverage – it would be more efficient to send all notifications at once, rather than taking an entire month.
Combining these factors, one could be forgiven for speculating that Salomon clients intended to take legal action under unclaimed or lost property laws to assert ownership of so-called “abandoned” tokens or to force a state trusteeship.
Looking at the big picture, U.S. property law rarely applies the folk principle of “who finds it to whom it belongs” – and this is especially true in the cryptocurrency field.The “found things” principle has traditionally only applied to tangible personal property, not intangible assets such as BTC.The latter must be declared to the government.
Although state unclaimed property laws vary, they generally provide that when a virtual currency account remains dormant for the legal period, the “holder” must first perform due diligence to contact the “owner”.Statutory due diligence notices are typically sent by the holder via first-class mail (including email if agreed) to the owner’s last known address within the state-mandated window (generally 60-120 days prior to filing).If this fails, the holder is legally required to declare the assets to the state government and subsequently transfer them to state custody.The state then acts as custodian of the funds on behalf of the original owners, while the holders are released from liability.This allows the owner or his heirs to apply to the state at any time to recover the value of the property.
The number of states that have incorporated, or are in the process of incorporating, digital assets into their abandoned property laws may reveal the paths Salomon’s clients take and the restrictions they may face.
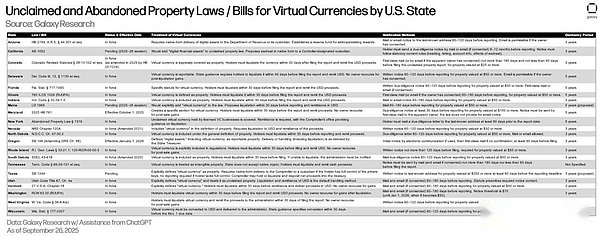
Sending electronic abandonment notices via an OP_RETURN transaction (in lieu of an unobtainable street address or email) may be consistent with the spirit of some state-level unclaimed property laws in the United States.However, certain definitions and the applicability of these laws may limit a customer’s ability to operate, including:
what for“holder“?These laws consistently define “holder” as a business, corporation or other legal entity that is obligated to hold, deliver or pay property to the “owner”.An owner is defined as a person with legal rights to a suspected abandoned property.In the context of cryptocurrency,Holder categoryThis may include centralized exchanges, custodial wallets and fintech applications, qualified custodians and trust companies, and cryptocurrency-enabled brokers and investment platforms.Such entities can track account inactive status, owner information (such as name and home address), perform due diligence and transfer funds to the state.And for self-hostedwallet, the user is the only one with access to the funds, and the developers of these solutions cannot trace the user’s identity or send funds on behalf of the owner.There are therefore no third parties to report or transfer the assets, and it is impossible to move these funds without access to the corresponding private keys – so the “holder” definition likely does not apply.This is also fundamentally unworkable: if a holder is also the owner and refuses to respond to the abandonment notice, but subsequently uses the tokens themselves, the tokens were never truly lost or abandoned.
What happens to unclaimed property?When the holder fails to find the owner through due diligence, the property must be turned over to the state.After a business transfers property to the state, the state acts as a custodian and holds the funds on behalf of the owner indefinitely.State governments may liquidate assets such as stocks or virtual currencies into cash for management purposes.The original owner or his or her heirs may petition the state to recover the value of the property at any time.
Do one state’s unclaimed property laws automatically apply to other states?Not so.Jurisdiction follows the Supreme Court’s “Texas v. New Jersey” priority rule: 1) declaration to the state where the owner’s last known address is; 2) transfer to the state where the holder is registered if the address is unknown or the state does not provide that the specific property is owned by the state.The key is that the holder can only transfer the property if that type of property is covered by the receiving state’s statutes (sometimes through an “intangible property” catch-all provision or a requirement to be liquidated into cash); if neither state covers it or the statutes specifically exclude it, there is no right to devolution.More broadly, BTC is a global asset, and unclaimed property regulations are the product of geographically bounded laws and do not have international effect—meaning they cannot force foreign holders or entities outside the jurisdiction to declare or transfer them.
As a result, Salomon customers’ operational capabilities may be limited by:
Jurisdictional precedence rules(The owner’s last known address takes precedence, followed by the holder’s registered address): OP_RETURN “grace period” is likely to have no legal effect, and it is difficult to force the transfer of funds by itself.Even if the inactivity status of the notified address has exceeded the standard dormancy period, if there is no legal “holder”, this inactivity status itself does not create a reporting obligation.If the assets are subsequently deposited into a centralized custodian, any obligations will generally be accrued from that point in time based on the custodian’s records—although some state statutes may raise factual disputes regarding prior abandonment status and jurisdiction.
legal“holder“exists(Centralized custodian) vs. self-custody model (usually no holders): While the notice is likely not legally binding on self-custodial assets, its intent may be to create factual premises for future claims.If the tokens from the address attacked by the dust are subsequently deposited in a centralized custody institution, Salomon customers may use the previous notification to claim rights, which will cause the owner and the custodian to get into a legal dispute over the ownership of the tokens.
Territorial scope of effect of regulations: Because BTC is a global asset and U.S. unclaimed property laws do not have international or interstate enforcement force, any attempt to maximize coverage will require evaluating whether local regulations recognize digital assets as requitable property on a state-by-state basis and asserting rights only in areas where a viable legal framework exists.This all assumes that the OP_RETURN notification is recognized as a legally valid form of contact or due diligence by specific unclaimed property regulations in some jurisdictions, and that the tokens can be moved on behalf of the owner.This further assumes that both the holder and the owner are located in those jurisdictions – without this geographical nexus, the regulations would not apply.
Self-hostedBTCenforcement gaps: Legal issues aside, self-custody tokens cannot be moved without the corresponding private key under any circumstances.Even if there were legal avenues to deem self-custody tokens public property, there is no way to enforce the transfer of funds without access to the private keys.While a court cannot force the transfer of the Bitcoin itself, it can order a known individual (if the owner can be identified) to hand over the private keys.But this remedy presupposes the existence of an identifiable and reachable individual; for most long-dormant or anonymous addresses, no such connection exists, making the token effectively beyond the reach of any court order.Unlike a wallet that can be picked up on the sidewalk and kept for collection, Bitcoin cannot be “possessed” at all without access to the corresponding private key (or someday, a quantum computer).Any attempt to circumvent this framework and convert abandoned wallets into private ownership via on-chain notifications would lack precedent and be legally suspect if the private keys are inaccessible.
However, this legal gray area may be the value proposition perceived by the customer: by establishing an on-chain notification record through a dust attack, he may believe that he can attempt to initiate a new type of claim based on newly introduced regulations and thereby seize ownership of the “abandoned” tokens.
Recent litigation highlights the fragility of such theories.In Battle Born Investments v. Department of Justice, the U.S. Supreme Court rejected speculative ownership claims for seized Bitcoin wallets and instead sought concrete evidence of control—that is, the ability to conduct transactions or demonstrate access to private keys.By analogy, an OP_RETURN notification alone is unlikely to establish ownership or expropriate an owner’s interest.Such notices amount to speculative claims at best and lack the legal force required by the existing unclaimed property regime.But they may be designed to induce self-selection, prompting dormant holders to either identify themselves or move their tokens to a more legally binding custody venue.
In short: a notice is unlikely to immediately create a valid claim, but a subsequent transfer into a custodial environment may create a fact pattern that could lead to litigation in the jurisdiction where Salomon customers assert their rights.
10,in conclusion
Based on the analysis of all on-chain details and legal elements, Salomon Brothers’ OP_RETURN dust attack should not be simply regarded as a pure behavioral experiment.Rather, this is more of an attempt to establish an on-chain record of notifications to prepare evidence for potential litigation.
However, the operation itself has outstanding contradictions: broken links in early messages; possible insufficient notification of certain addresses by the sender’s self-declared standards; claiming to protect the network from technical attacks without notifying address types that are theoretically more vulnerable to technical attacks; and sending messages to addresses that have been dormant for less than the time limit specified by the Unclaimed Property Act.
Despite these missteps, the operators clearly had a deep technical understanding of the Bitcoin network and took sophisticated measures to cover their tracks and deliver messages to a large number of addresses.While still puzzling in many ways, the Solomon case deserves continued attention from the global Bitcoin and crypto community given the new legal theories this mystery client may ultimately test.Please pay close attention to the two key time points of October 10th and November 5th – when the 90-day period set by Salomon customers will expire.